Encryption Evolution: From Classical Ciphers to Quantum Security
 Utkarsh Kumar
Utkarsh Kumar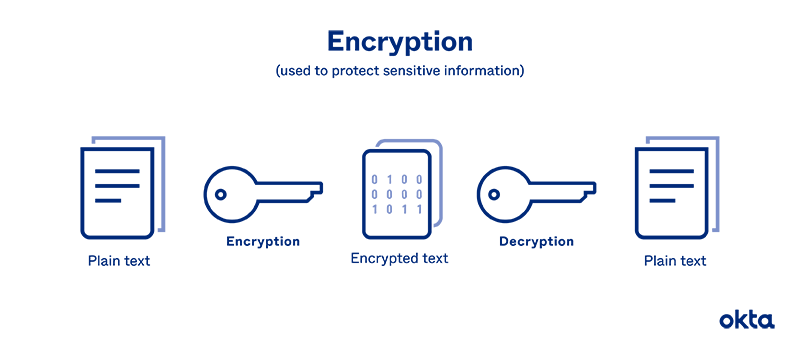
In today’s interconnected world, securing digital information is paramount. Encryption, the cornerstone of data protection, has evolved dramatically from its rudimentary beginnings to the sophisticated algorithms safeguarding our modern communications. This guide explores the journey of encryption—from classical ciphers to quantum-resistant technologies—while providing practical insights for implementing robust encryption in today’s applications.
What is Encryption?
Encryption is the process of converting plain text into coded text to prevent unauthorized access. It ensures that only those with the correct decryption key can access the original information. Encryption is vital for protecting sensitive data, securing communications, and maintaining privacy in both personal and professional realms.
Core Principles of Encryption
Confidentiality: Ensures that information is accessible only to those authorized to view it.
Integrity: Guarantees that the data has not been altered or tampered with.
Authentication: Verifies the identities of the parties involved in communication.
Non-repudiation: Prevents parties from denying their actions related to the data.
Historical Overview: From Classical Ciphers to Modern Algorithms
Classical Ciphers
Caesar Cipher: One of the oldest known encryption techniques, where each letter in the plaintext is shifted a certain number of places down the alphabet. While simple, it offers minimal security against modern attacks.
Vigenère Cipher: Uses a keyword to shift letters, providing better security than the Caesar Cipher. However, it is still vulnerable to frequency analysis and other cryptanalysis methods.
Modern Encryption Standards
Data Encryption Standard (DES): Developed in the 1970s, DES uses a 56-bit key to encrypt data. While groundbreaking at its inception, DES is now considered insecure due to its short key length.
Advanced Encryption Standard (AES): Adopted in 2001, AES is widely used today for its strong security and efficiency. It supports key lengths of 128, 192, and 256 bits, making it resistant to brute-force attacks.
RSA (Rivest-Shamir-Adleman): A public-key cryptosystem used for secure data transmission. RSA relies on the computational difficulty of factoring large prime numbers, providing both encryption and digital signatures.
Elliptic Curve Cryptography (ECC)
ECC offers similar security to RSA but with shorter key lengths, resulting in faster computations and reduced storage requirements. This makes ECC particularly suitable for mobile devices and environments with limited resources.
The Quantum Computing Threat
Quantum computing represents a significant advancement in computational power, capable of solving complex problems exponentially faster than classical computers. While this has numerous beneficial applications, it poses a severe threat to current encryption methods.
Why Quantum Computing Matters for Encryption
Shor’s Algorithm: Capable of efficiently factoring large numbers, potentially breaking RSA and ECC by rendering them insecure.
Grover’s Algorithm: Reduces the time required to perform brute-force attacks on symmetric key algorithms, effectively halving their key lengths’ security.
Quantum-Resistant Cryptography
In response to the quantum threat, the cryptographic community is developing post-quantum algorithms designed to withstand quantum attacks. These include:
Lattice-Based Cryptography: Utilizes mathematical lattices, believed to be resistant to both classical and quantum attacks.
Hash-Based Cryptography: Relies on the security of hash functions, offering simplicity and robustness.
Code-Based Cryptography: Uses error-correcting codes to create secure cryptographic systems.
Multivariate Quadratic Equations: Based on the difficulty of solving systems of multivariate quadratic equations.
The National Institute of Standards and Technology (NIST) is actively working on standardizing post-quantum cryptographic algorithms to ensure a smooth transition once quantum computers become mainstream.
Practical Implementation: Securing Modern Applications
Implementing strong encryption practices is essential for safeguarding data in today’s applications. Here’s how you can integrate encryption effectively:
1. Implementing SSL/TLS for Secure Data Transmission
Secure Sockets Layer (SSL) and its successor, Transport Layer Security (TLS), are protocols that encrypt data transmitted between clients and servers. Implementing SSL/TLS ensures that sensitive information, such as login credentials and payment details, remains confidential.
Steps to Implement SSL/TLS:
Obtain an SSL Certificate: Purchase from a trusted Certificate Authority (CA) or use free options like Let’s Encrypt.
Configure Your Server: Install the certificate on your web server (e.g., Apache, Nginx) and enable HTTPS.
Enforce HTTPS: Redirect all HTTP traffic to HTTPS to ensure all communications are encrypted.
2. Encrypting Data at Rest
Protecting data stored on servers, databases, and storage devices is crucial. Encryption at rest ensures that even if data is accessed without authorization, it remains unreadable.
Best Practices:
Use Strong Encryption Algorithms: AES-256 is recommended for encrypting sensitive data.
Key Management: Securely manage encryption keys using services like AWS Key Management Service (KMS) or Azure Key Vault.
Encrypt Backups: Ensure that backup data is also encrypted to prevent unauthorized access.
3. Secure Password Storage
Storing passwords securely is fundamental to protecting user accounts. Instead of storing plain-text passwords, use hashing algorithms to store derived values.
Best Practices:
Use Salted Hashes: Add a unique salt to each password before hashing to prevent rainbow table attacks.
Choose Strong Hashing Algorithms: Utilize bcrypt, Argon2, or PBKDF2, which are designed to be computationally intensive and resist brute-force attacks.
Regularly Update Hashing Methods: Stay informed about advancements in hashing algorithms and update your practices accordingly.
4. Utilizing Cryptographic Libraries
Leverage established cryptographic libraries to implement encryption correctly and securely, avoiding common pitfalls associated with custom implementations.
Recommended Libraries:
OpenSSL: A robust, widely-used library for SSL/TLS and general-purpose cryptography.
libsodium: A user-friendly library that provides high-level cryptographic functions.
Bouncy Castle: A comprehensive library supporting a wide range of cryptographic algorithms for various programming languages.
5. Securing APIs with Cryptography
APIs are critical for modern applications but can be vulnerable if not properly secured. Implement encryption to protect data exchanged through APIs.
Best Practices:
Use HTTPS for API Communication: Ensure all API traffic is encrypted.
Implement OAuth 2.0: Use OAuth for secure and standardized authorization.
Encrypt Sensitive API Parameters: Protect sensitive data within API requests and responses.
Best Practices for Encryption
Adhering to best practices ensures that encryption is implemented effectively and securely:
1. Choose the Right Encryption Algorithm
Select encryption algorithms that are widely recognized and have withstood extensive cryptanalysis. AES, RSA, and ECC are industry standards, while emerging post-quantum algorithms should be monitored for future adoption.
2. Secure Key Management
Encryption is only as strong as the security of its keys. Implement robust key management practices to prevent unauthorized access and ensure keys are rotated regularly.
Key Management Tips:
Use Hardware Security Modules (HSMs): Store keys in HSMs for enhanced security.
Implement Key Rotation: Regularly update encryption keys to minimize the impact of a potential key compromise.
Restrict Key Access: Limit access to encryption keys to only those systems and personnel that absolutely need it.
3. Regularly Update and Patch Systems
Ensure that all systems and software used for encryption are kept up-to-date with the latest security patches to protect against vulnerabilities that could compromise encryption.
4. Educate and Train Your Team
Promote awareness and understanding of encryption principles among your team members. Proper training ensures that encryption is implemented correctly and that security policies are followed consistently.
Future-Proofing Security: Preparing for Quantum Computing
As quantum computing advances, organizations must prepare to transition to quantum-resistant encryption methods to maintain data security.
Steps to Prepare:
Stay Informed: Keep up-to-date with developments in quantum computing and post-quantum cryptography.
Assess Current Encryption: Evaluate the encryption methods currently in use and identify which are vulnerable to quantum attacks.
Plan for Transition: Develop a roadmap for migrating to post-quantum cryptographic algorithms once they are standardized and available.
Engage with Standards Bodies: Participate in initiatives and discussions led by organizations like NIST to stay ahead in the adoption of quantum-resistant standards.
Conclusion
Encryption has come a long way from its classical origins, evolving into a sophisticated and essential component of modern cybersecurity. Understanding the historical context and current advancements in encryption equips organizations and individuals to implement robust security measures effectively. As we stand on the brink of the quantum computing era, embracing both current best practices and preparing for future challenges ensures that our digital communications and data remain secure.
By integrating strong encryption practices, staying informed about emerging threats, and adopting forward-looking cryptographic solutions, you can safeguard your applications and data against both present and future cyber threats. Encryption is not just a tool but a fundamental aspect of maintaining trust and integrity in our increasingly digital world.
Subscribe to my newsletter
Read articles from Utkarsh Kumar directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by
