WordPress TakeOver Investigation
 arzu
arzu
Lab link: https://learn.cyberexam.io/challenges/blue-team/incident-response/wordpress-takeover-investigation
Mission Statement
An advesary attacked a web server. The logs from the server after the attack are given to us. Analyze the data collected and solve the incident by gathering information about the attacker and the attack.
Log file is in Desktop after connected lab machine.
Lab Solution
Which platform under attack?
The targeted platform name is given in incident.log file.
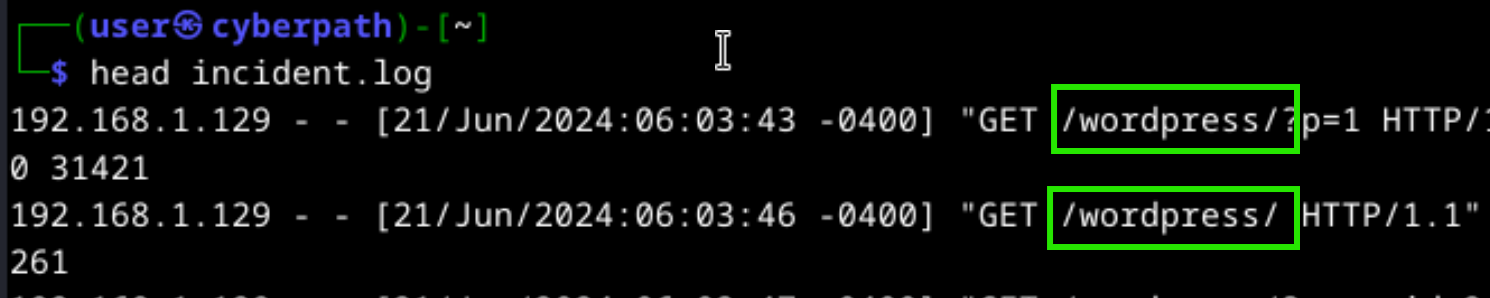
Which tool was used for attack? (First letter is uppercase)
To find the used tool for the attack, we can check for the user-agent value in the captured network packets incident.pcapng file since most of the attack tools is recognized by this method if user agent values doesnt be specifically modified by the attacker to reduce own visibility in the system.
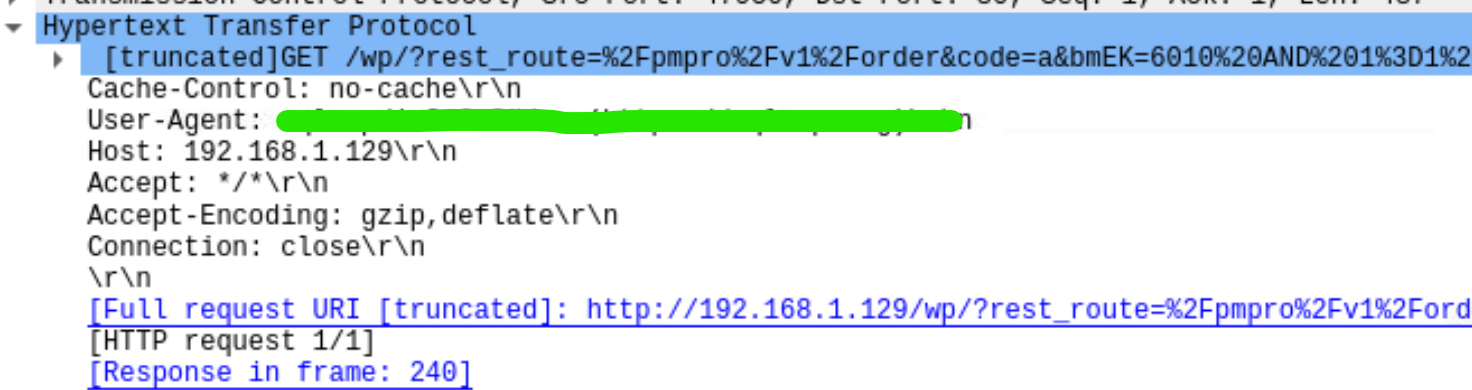
Who performed attack? (IP address)
We can see the IP address that is performed attack after the open network traffic pcapng file with Wireshark tool applying filter http.user_agent.
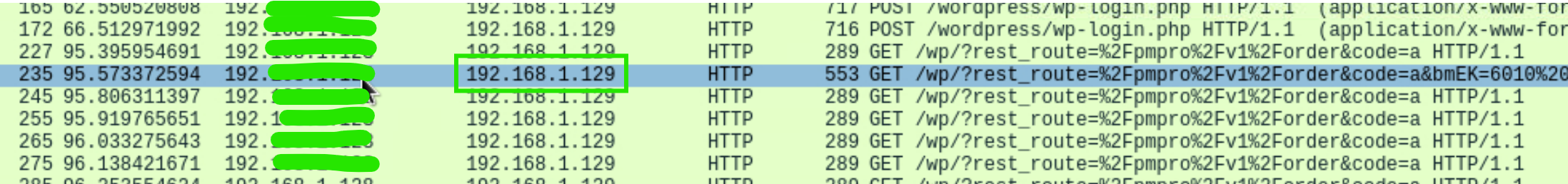
According to the picture abovee, the first IP represents source IP address which is the attacker IP address. Second is the destination address which gives the our victim machine IP.
What is the password of the admin panel?
The attacker requested with SQL payload for credentials wp admin panel. We can observe in both log and pcap file. Apply the http.request.method=="POST" filter to list POST HTTP requests. Then examine the packets.
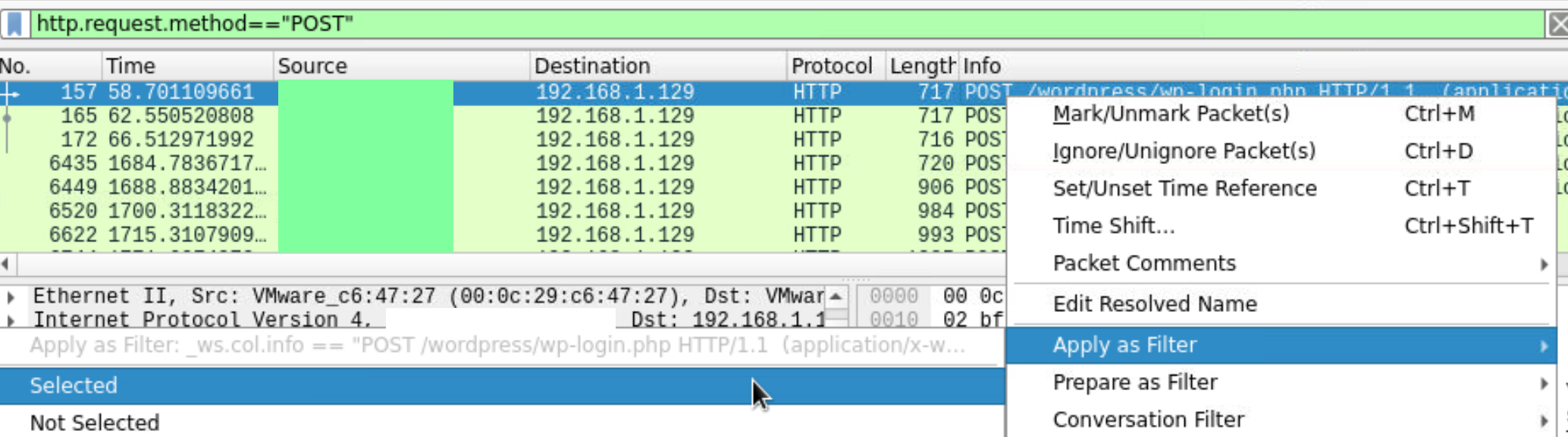
For the more detailed filter, we can do right click and select apply as a filter option.
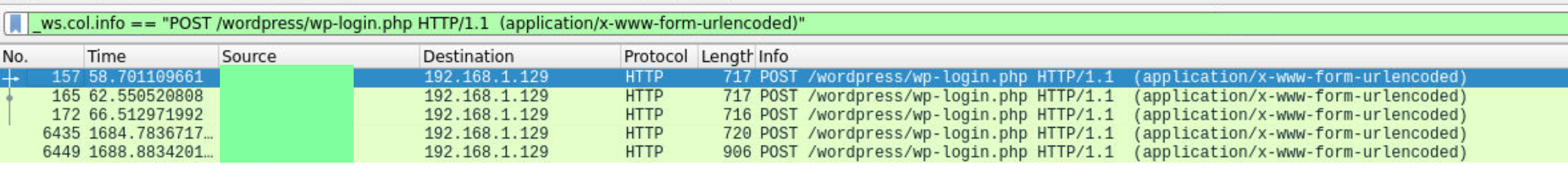
To see hte response of these requests, right click and select the Follow > HTTP Stream option. The response code for the right password value will be 302 Found status but this may not always be the case.
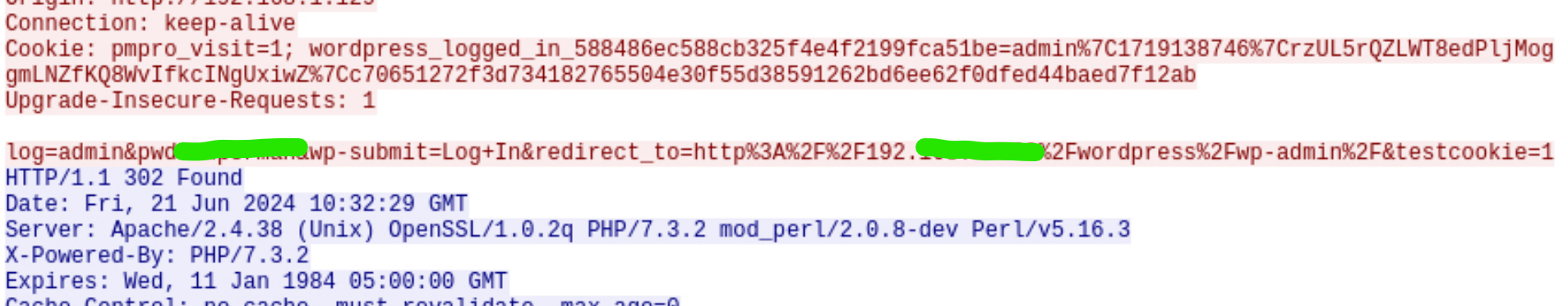
What is the password of the alex?
The attacker got a reverse shell by exploiting the SQL injection vulnerability that was found in the wordpress plugin used. The SQL queries were injected rest_route parameter with GET request and content type of the response was JSON format. Apply filter http.content_type contains "application/json"
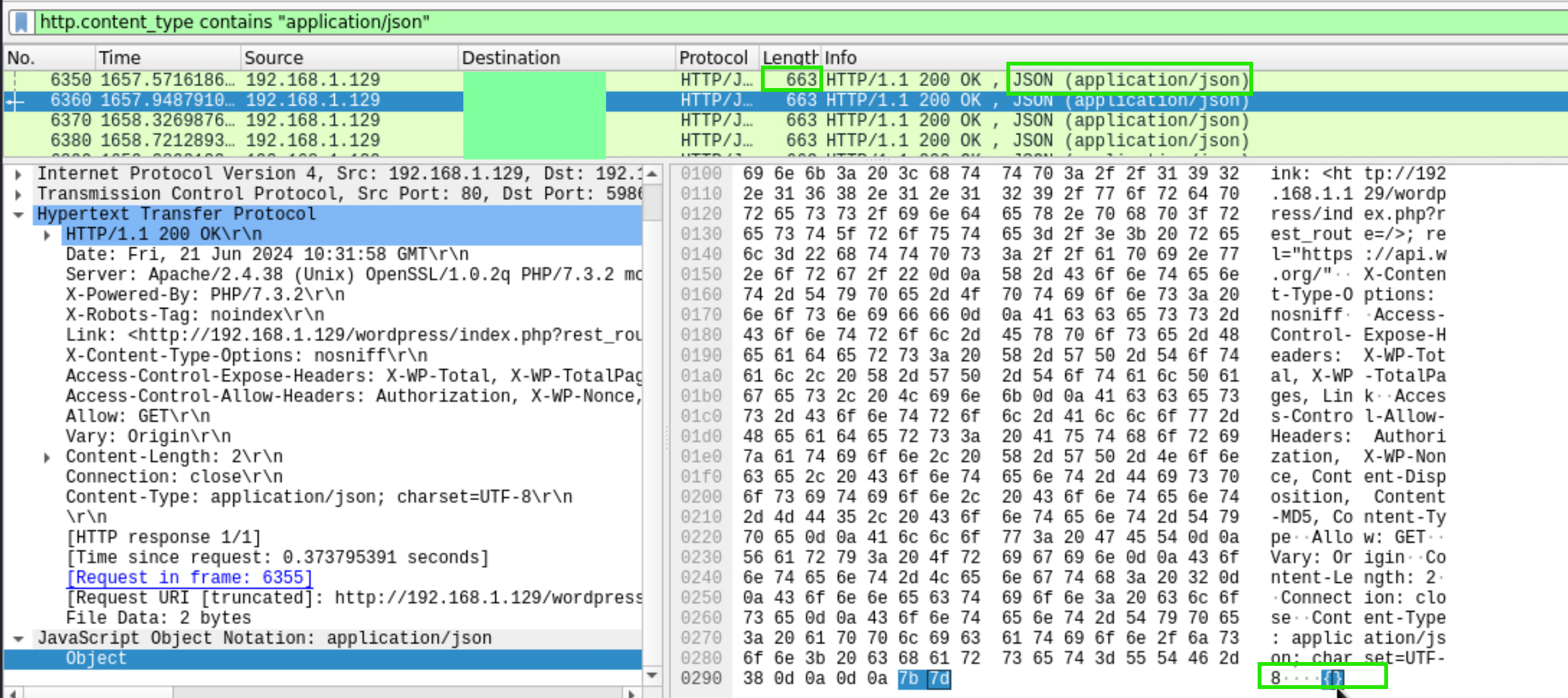
Filter the empty response by adding frame.len > 663 since the response packet length is that value.
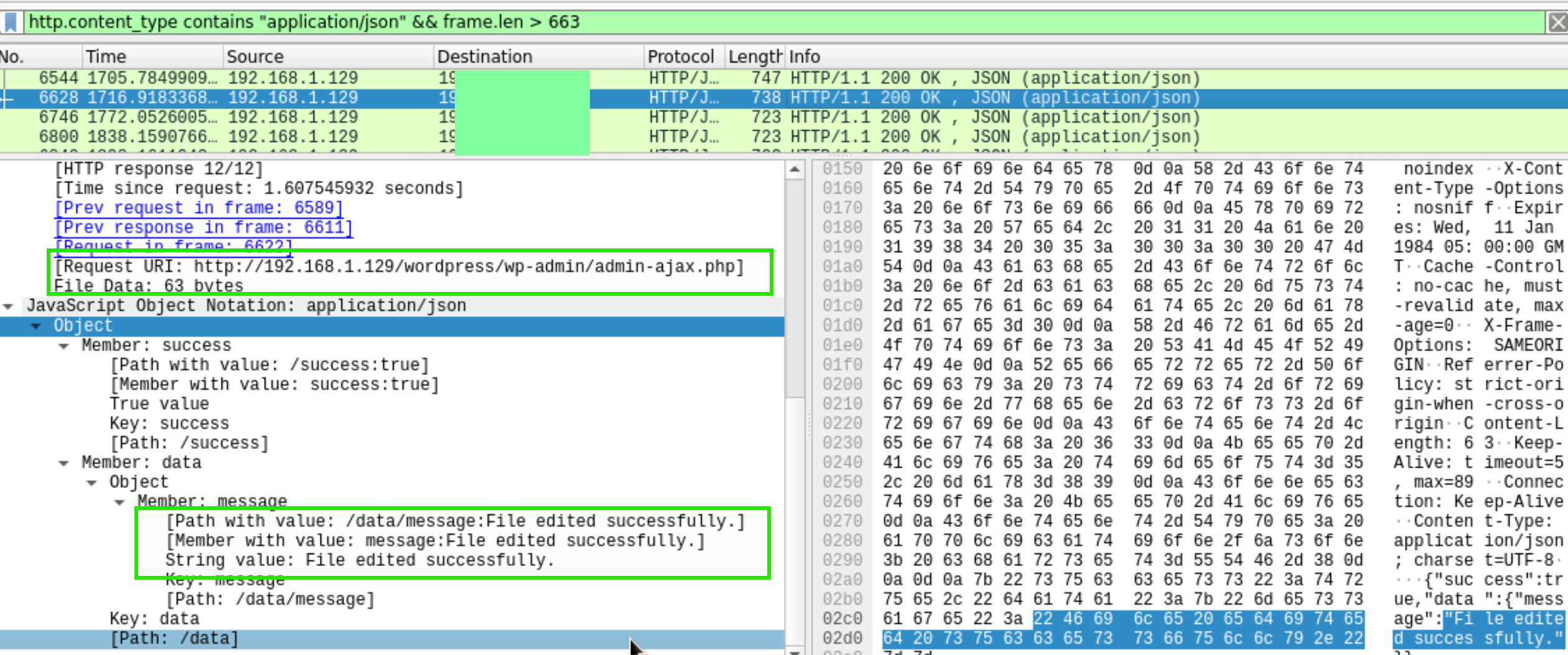
Notice that a file was modified. Right click the response and Follow > HTTP Stream. We can see the attacker had a reverse shell from 1234 port number by editing 404.php file.
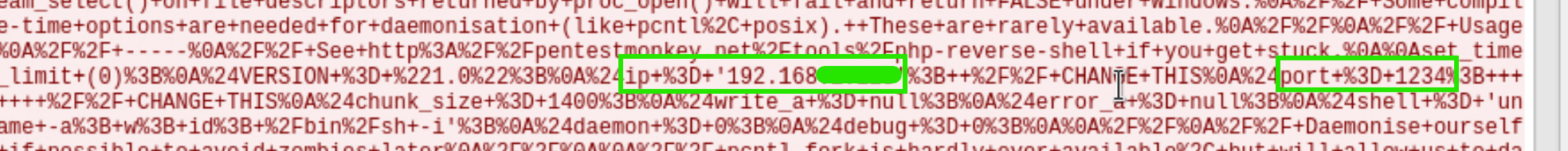
In a basic way, it might be detected by filtering POST request http.request.method == "POST"
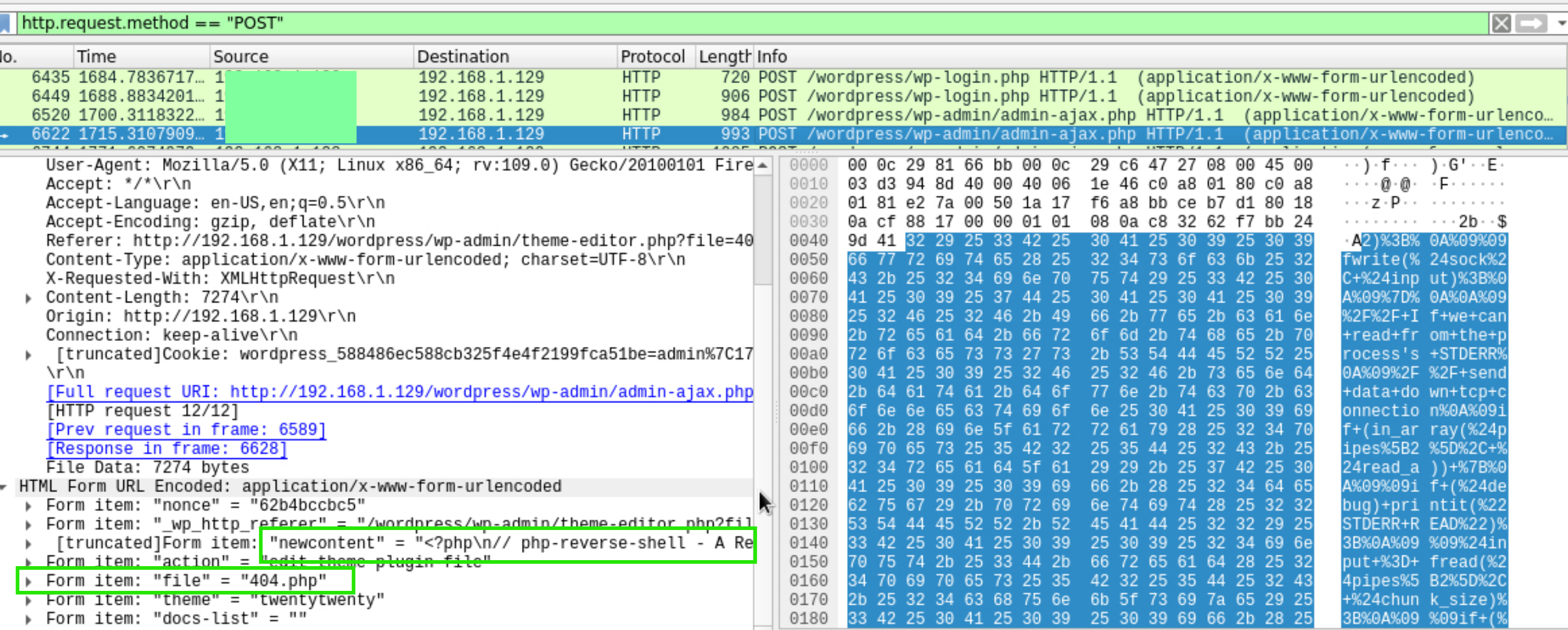
We found the port number that was connected. Apply filter tcp.port==1234 && data contains "alex"
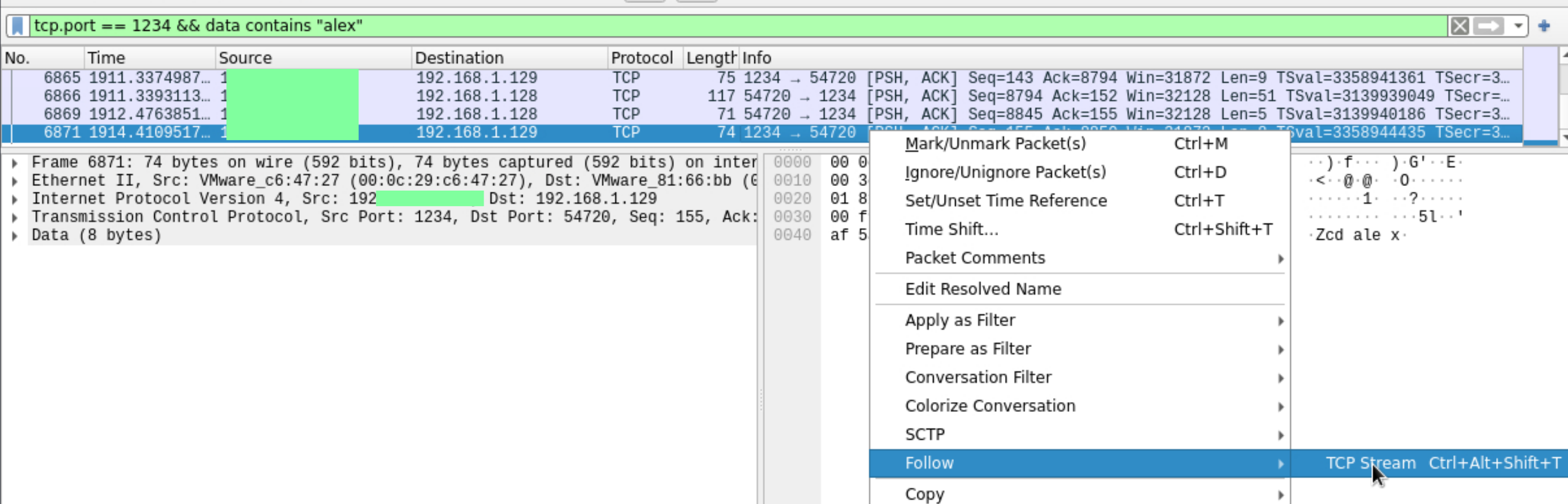
Right click the packet and select Follow > TCP Stream option to see whole conversation.

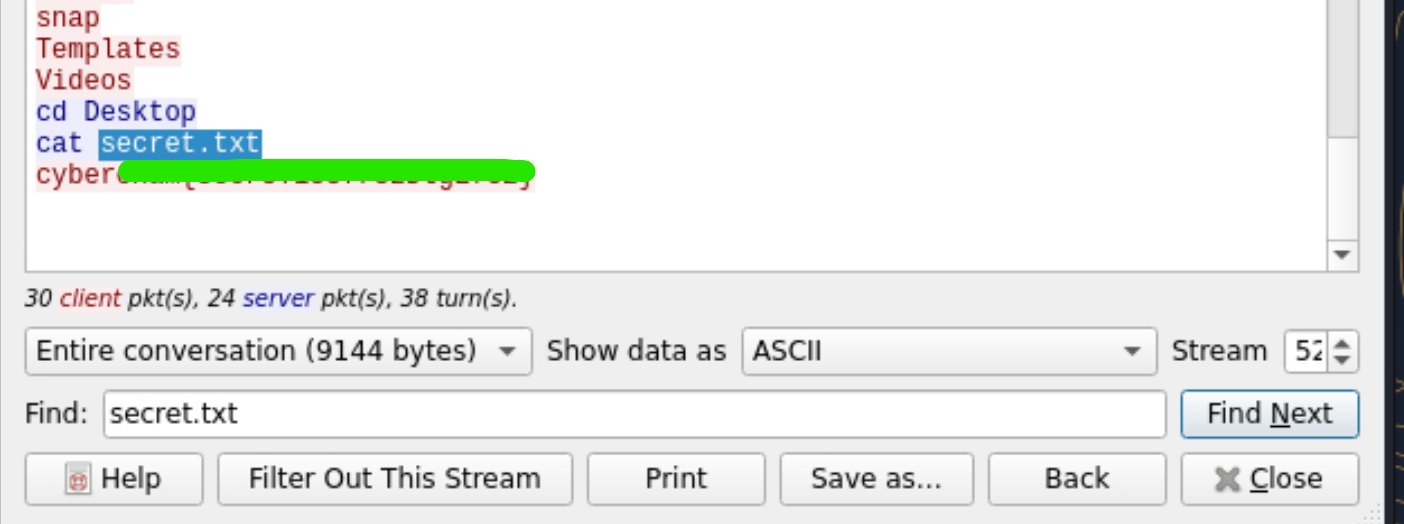
What is the content of the secret.txt?
The content of the secret file is included in the TCP stream.
Which attack technique used? (***e-b**** ***** ****) (lowercase)
The attacker used many attack technique in fact. Exploiting SQLi vulnerability to find wordpress admin panel credentials and having reverse shell with modified 404.php file. Otherwise when we consider the attack type, we can come to the solution. It may be useful to examine the used SQLi payloads to identify the attack type.
HTTP requests can be displayed Statistics > HTTP > Requests
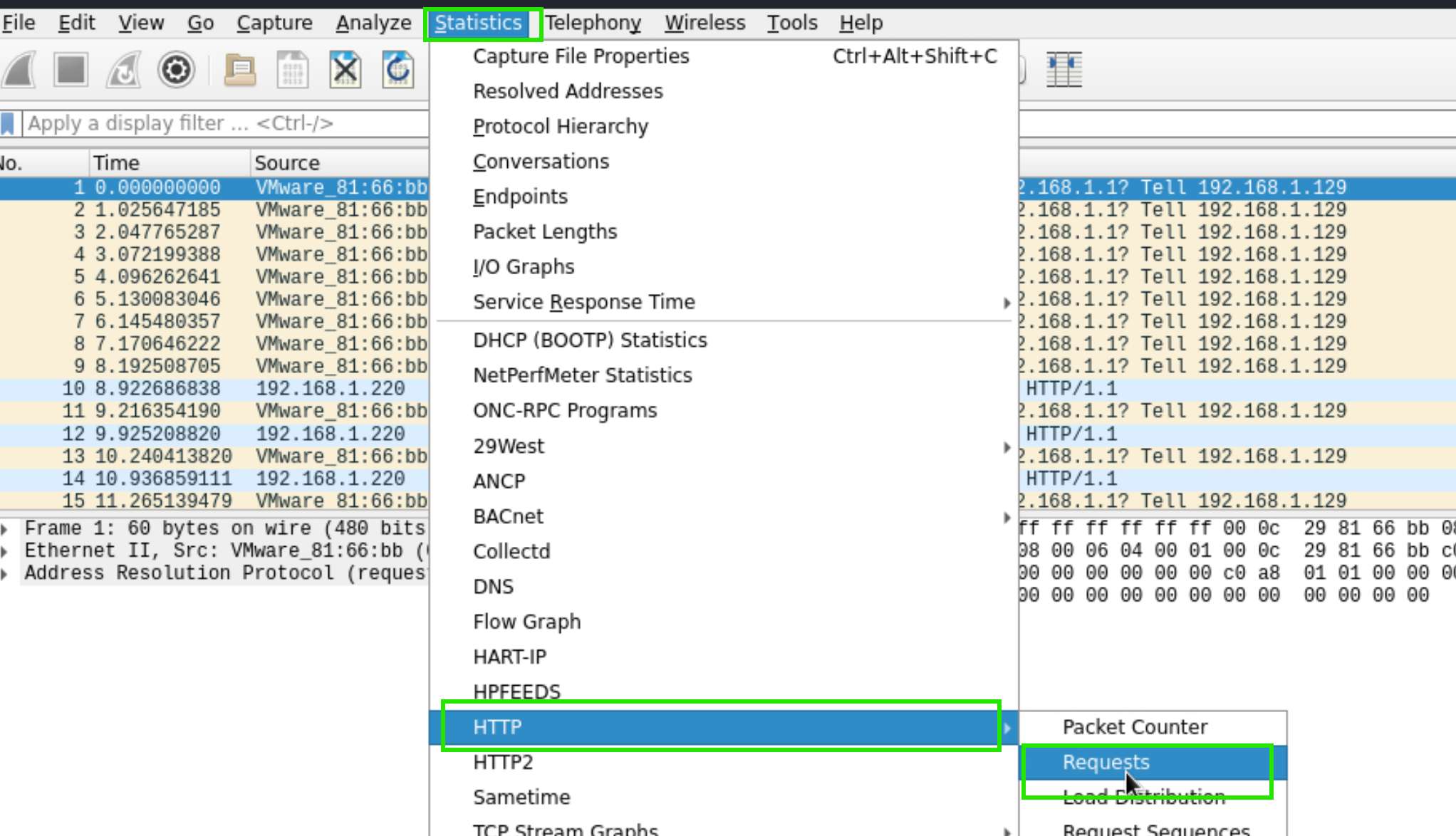
There are many requests to review manually.
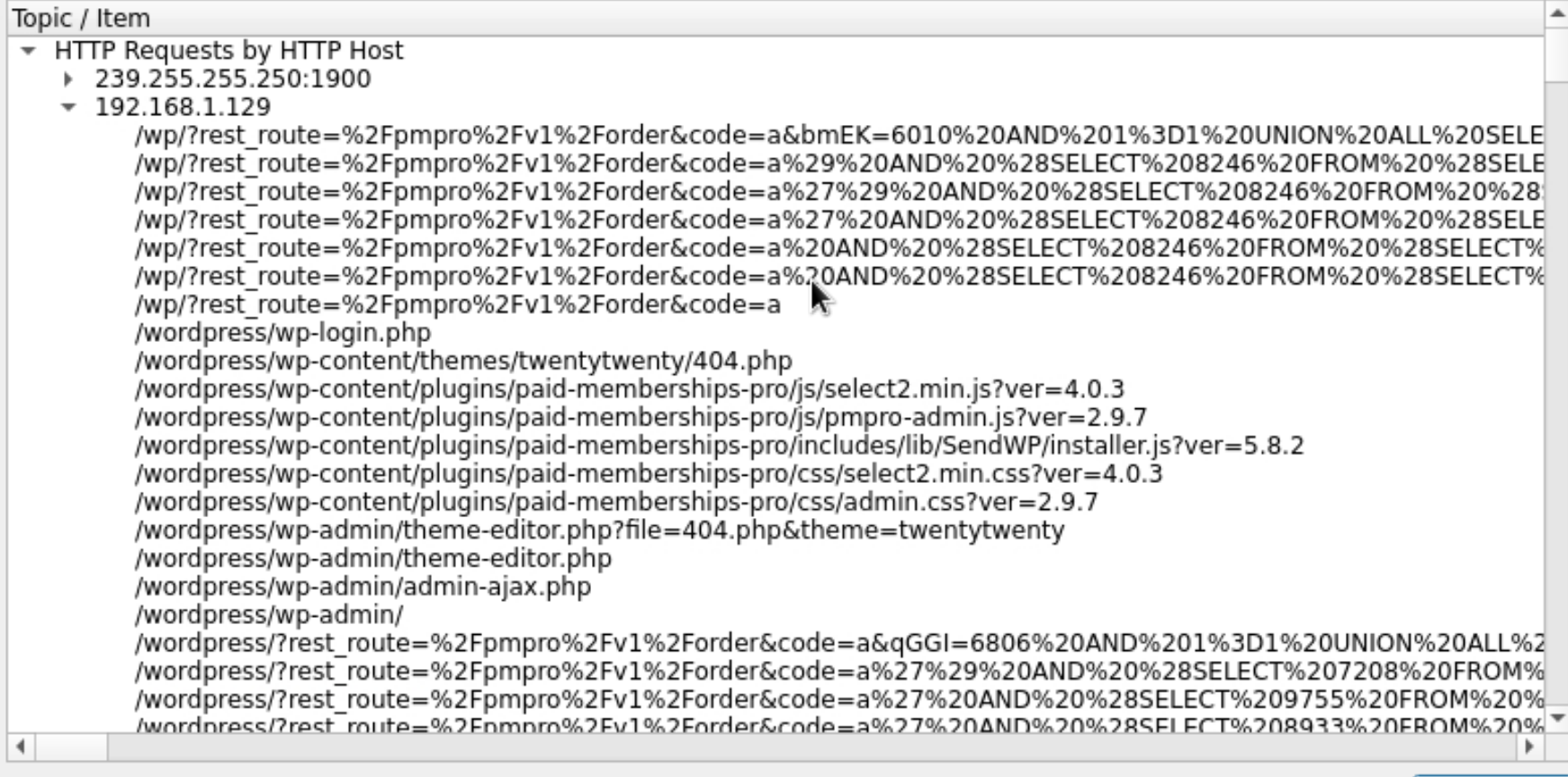
Apply filter the response code is not 500 and request path contains sqli payload http.request.uri contains "SELECT" && !(http.response.code == 500) .After that select a random packet and follow TCP stream.
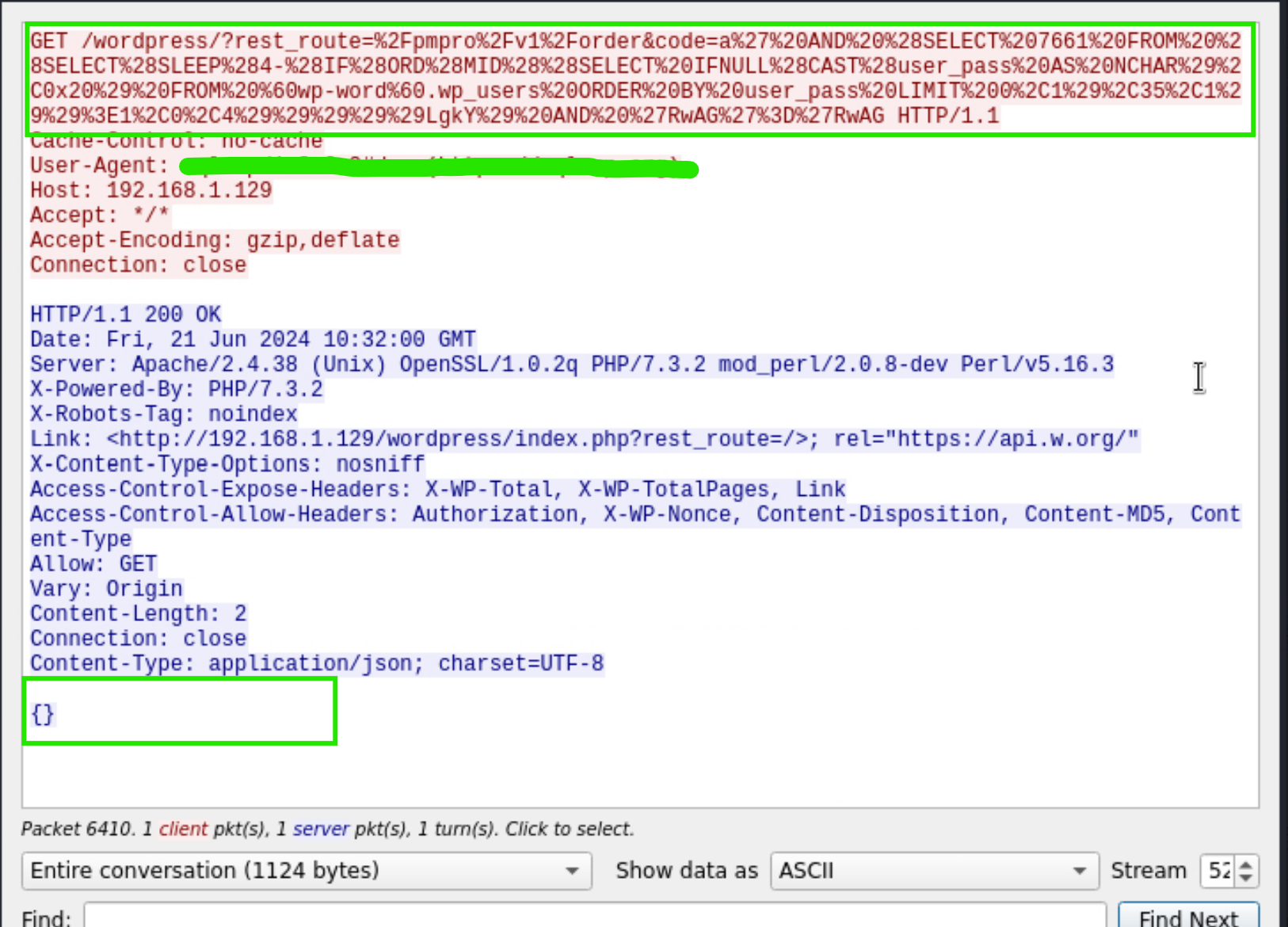
The payload gives the information about type of the exploited vulnerability.
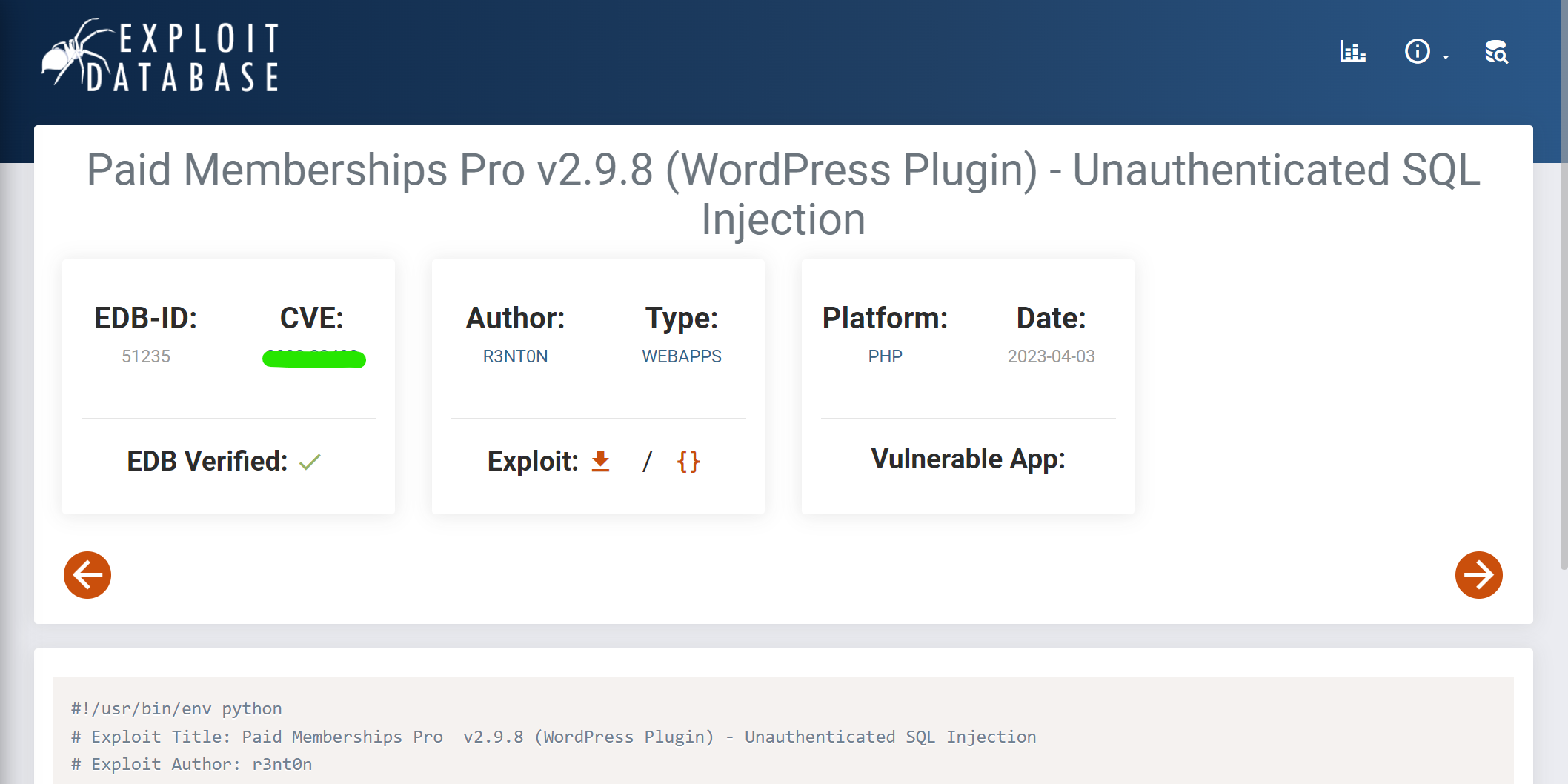
What is the CVE number for these attack?
The attacker used rest_route parameter to inject SQL queries with the tool to find admin panel credentials. We can check for the version or used plugins to identify the vulnerability. Filter incident.log file with grep tool. Run the command cat incident.log | grep -i -E "plugin|version" to list plugins.
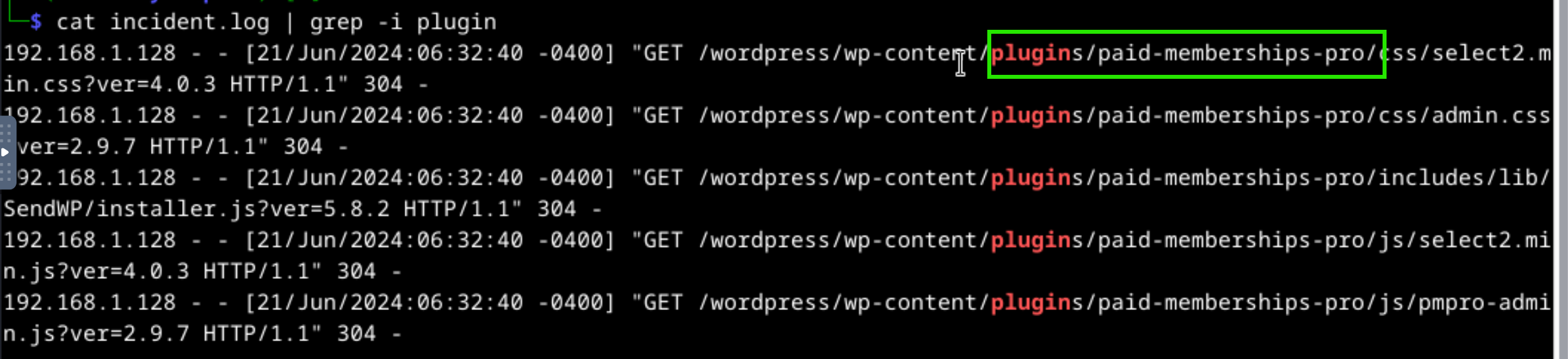
Then search with keywords like wordpress paid-memberships-pro plugin sqli or wordpress rest_route sqli for the vulnerability.
Subscribe to my newsletter
Read articles from arzu directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by
