Cryptography: John the Ripper: The Basics (TryHackMe)
 Jebitok
Jebitok
In this article, I will write a write-up for John the Ripper: The Basics that the Basic Terms, Setting Up John on Your System, Cracking Basic Hashes, Cracking Windows Authentication Hashes, Cracking /etc/shadow Hashes, Single Crack Mode, Custom Rules, Cracking Password Protected Zip Files, Cracking Password Protected Zip Files, Cracking Password-Protected RAR Archives, and Cracking SSH Keys with John.
What is the most popular extended version of John the Ripper?
Jumbo JohnWhich website’s breach was the
rockyou.txtwordlist created from?rockyou.com
the image below shows how to achieve the next questions form 3 to 10.
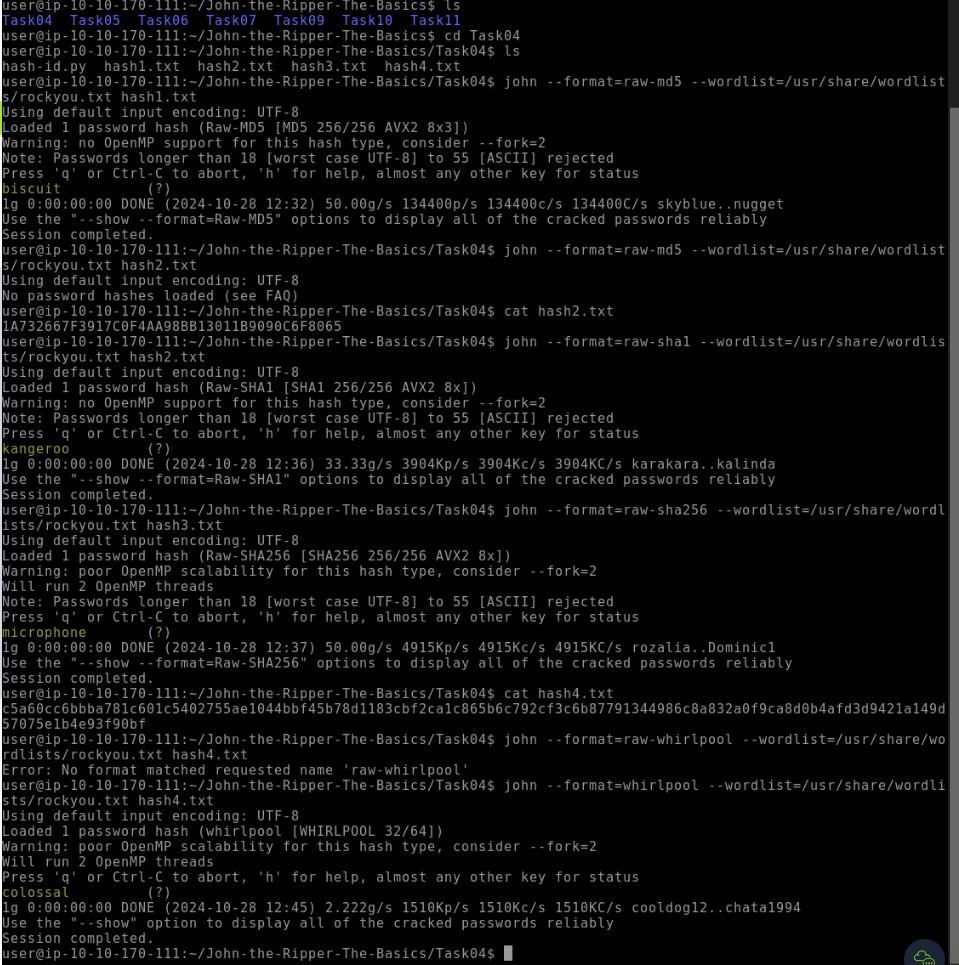
What type of hash is hash1.txt?
md5What is the cracked value of hash1.txt?
biscuitWhat type of hash is hash2.txt?
sha1What is the cracked value of hash2.txt?
kangerooWhat type of hash is hash3.txt?
sha256What is the cracked value of hash3.txt?
microphoneWhat type of hash is hash4.txt?
whirlpool
to identify the hash I used the rainbow table, Crackstation then continued to use Johnriper to crack the value using the command john —-format=whirlpool —-wordlist=/usr/share/wordlists/rockyou.txt hash4.txt
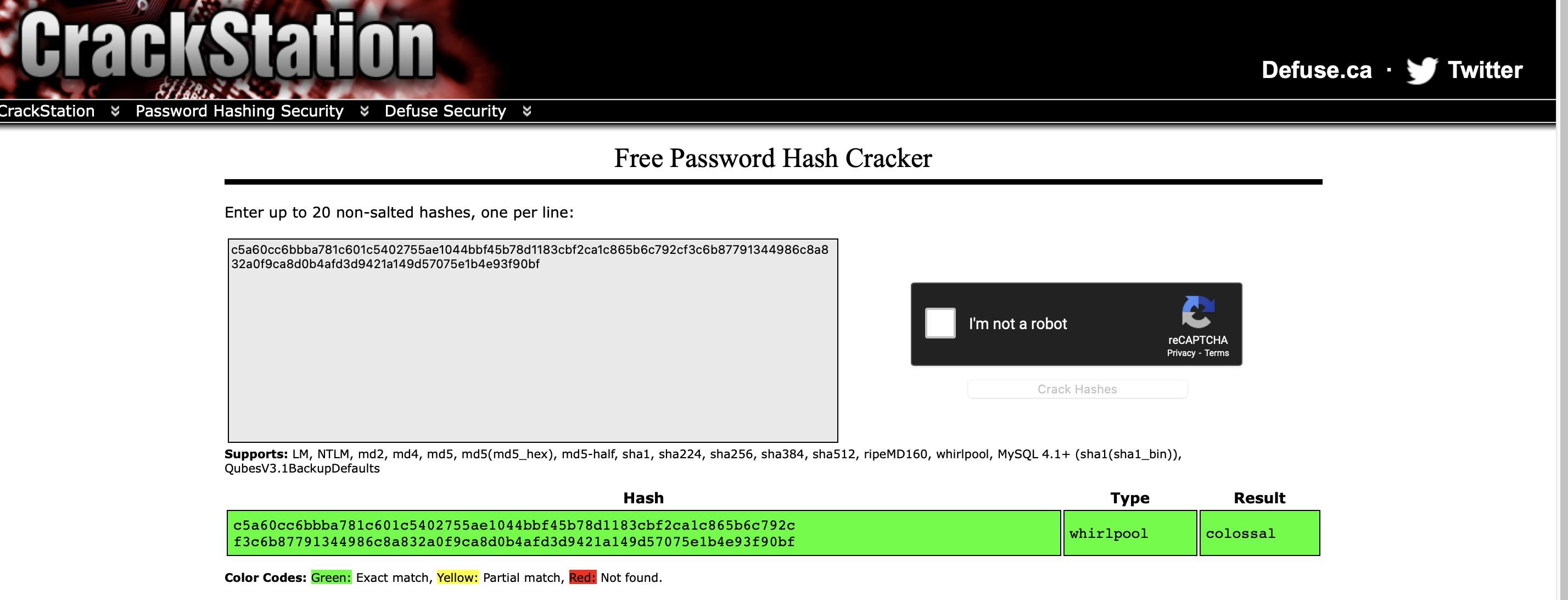
What is the cracked value of hash4.txt?
colossalWhat do we need to set the
--formatflag to in order to crack this hash?ntWhat is the cracked value of this password?
mushroom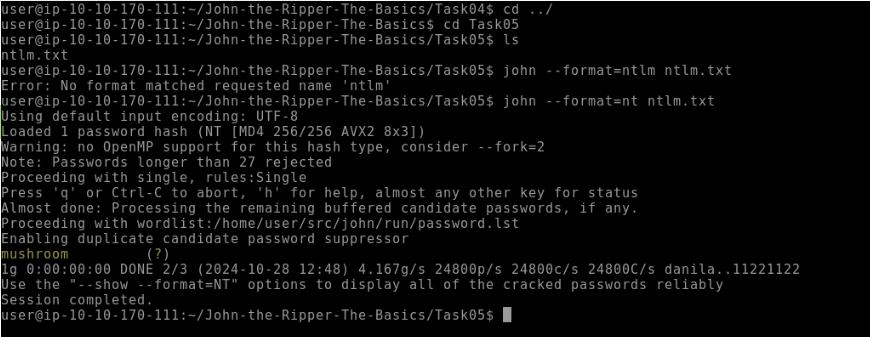
What is the root password?
1234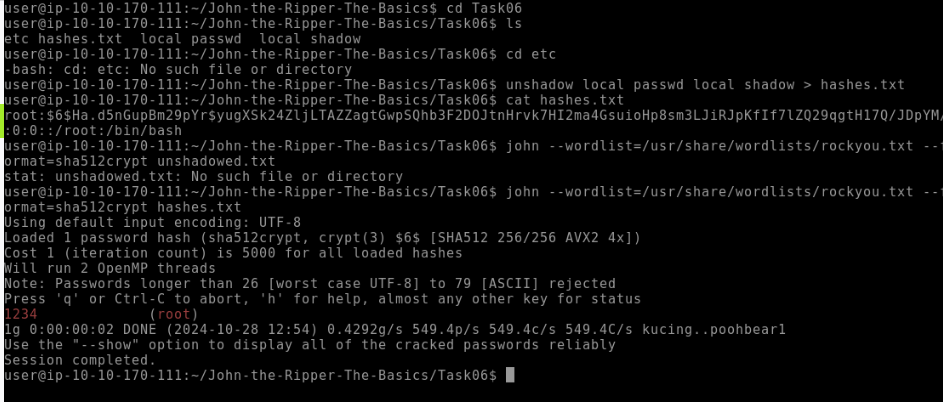
Example Usage:
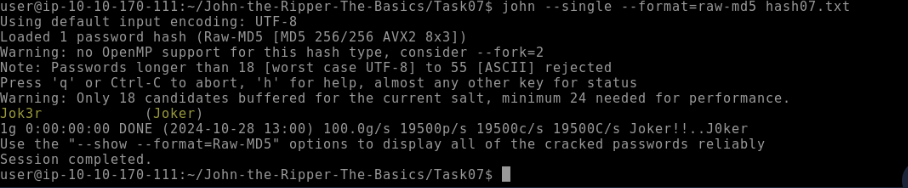
What is Joker’s password?
Jok3rafter finding the hash remember to edit the file with nano then add the name before the hash you’ve found
Joker:{hash}
What do custom rules allow us to exploit?
Password complexity predictabilityWhat rule would we use to add all capital letters to the end of the word?
Az"[A-Z]”What flag would we use to call a custom rule called
THMRules?--rule=THMRulesWhat is the password for the secure.zip file?
pass123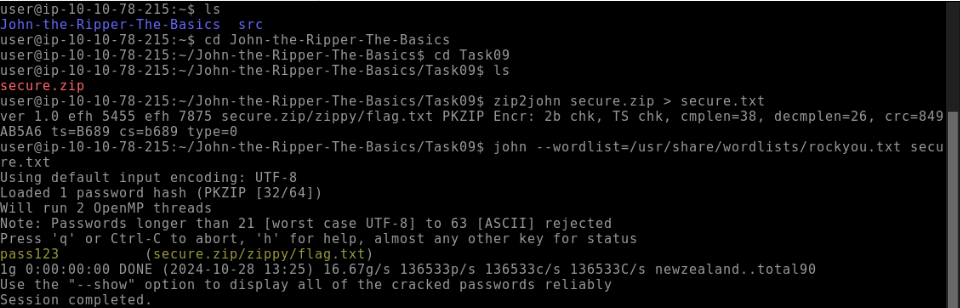
What is the contents of the flag inside the zip file?
THM{w3ll_d0n3_h4sh_r0y4l}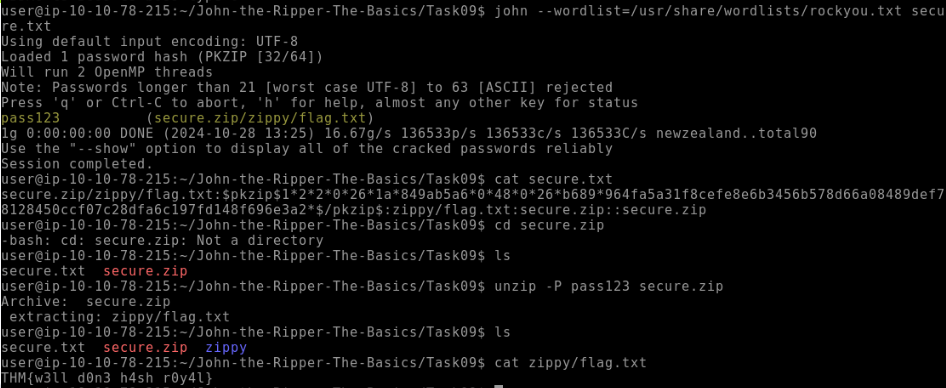
What is the password for the secure.rar file?
passwordWhat are the contents of the flag inside the zip file?
THM{r4r_4rch1ve5_th15_t1m3}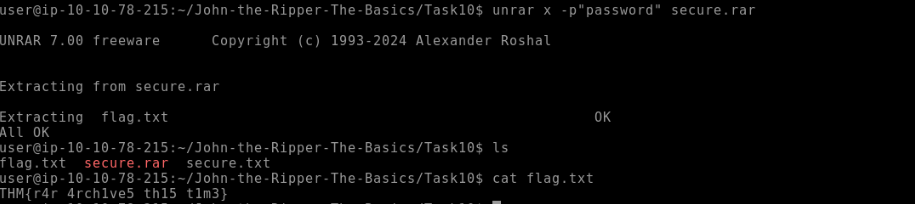
/opt/john/ssh2john.py id_rsa > id_rsa_hash.txt
Cracking
For the final time, we’re feeding the file we output from ssh2john, which in our example use case is called id_rsa_hash.txt and, as we did with rar2john, we can use this seamlessly with John: **`john --wordlist=/usr/share/wordlists/rockyou.txt id_rsa_hash.txt`**
Practical
Now, I’d like you to crack the hash of the **`id_rsa`** file relevant to this task! The file is located in **`~/John-the-Ripper-The-Basics/Task11/`**.
What is the SSH private key password?
mango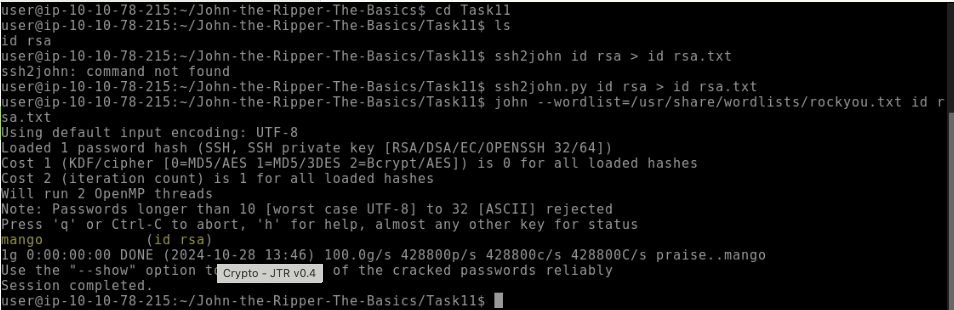
Thank you for reading my article. Please leave any questions or comments on improving my learning journey and the THM challenges.
Subscribe to my newsletter
Read articles from Jebitok directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Jebitok
Jebitok
Software Developer | Learning Cybersecurity | Open for roles * If you're in the early stages of your career in software development (student or still looking for an entry-level role) and in need of mentorship, you can reach out to me.