Exploitation Basics: Introduction (TryHackMe)
 Jebitok
Jebitok
In this article, I will write a write-up for Metasploit: Introduction that covers the Introduction to Metasploit, Main Components of Metasploit, Msfonsole, and Working with modules.
What is the name of the code taking advantage of a flaw on the target system?
ExploitWhat is the name of the code that runs on the target system to achieve the attacker's goal?
PayloadWhat are self-contained payloads called?
SinglesIs "windows/x64/pingback_reverse_tcp" among singles or staged payload?
SinglesHow would you search for a module related to Apache?
search apacheWho provided the auxiliary/scanner/ssh/ssh_login module?
todb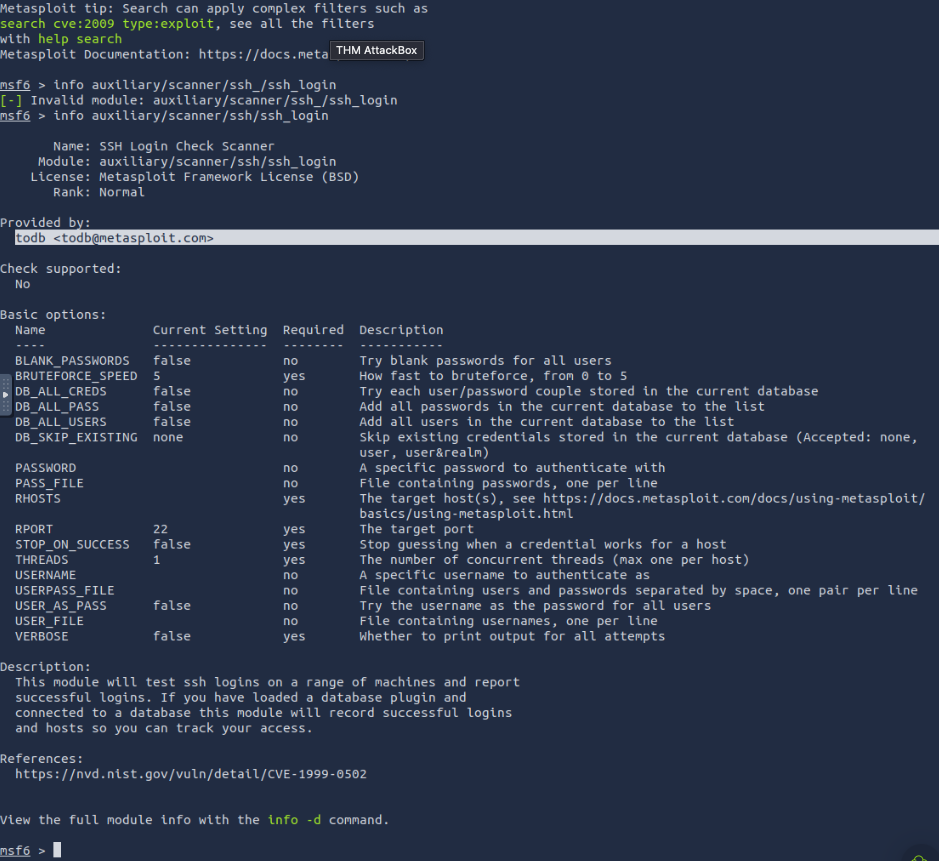
How would you set the LPORT value to 6666?
set LPORT 6666How would you set the global value for RHOSTS to 10.10.19.23 ?
setg RHOSTS 10.10.19.23What command would you use to clear a set payload?
unset PAYLOADWhat command do you use to proceed with the exploitation phase?
exploit
Thank you for reading my article. Please leave any questions or comments on improving my learning journey and the THM challenges.
Subscribe to my newsletter
Read articles from Jebitok directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Jebitok
Jebitok
Software Developer | Learning Cybersecurity | Open for roles * If you're in the early stages of your career in software development (student or still looking for an entry-level role) and in need of mentorship, you can reach out to me.