Is your Data really Private? You need to know the Truth about End-To-End Encryption
 Anusha
Anusha
You hear it everywhere: "End-to-End Encryption", E2EE – the holy grail of secure messaging. But here’s the big question: Is it actually as private as companies claim, or are you only getting half the story? Let’s dive into what this really means for your privacy.
So, what’s the deal with Encryption?
Let’s cover the basics. We all obviously agree that every conversation we have with out friends/family needs to be a private secure conversation without anyone being able to access it. You don’t want a snoopy hacker reading and smirking at your texts, right?
Right??
And this is essentially the core of encryption. Encryption transforms the data you send into a coded/encrypted format, accessible only to you and the intended recipient. But how does that work?
Encryption Keys: The Backbone of Secure Communication
For secure exchanges, Encryption is carried out using two pivotal keys: A Public Key (shared openly) and a Private Key (confidential and accessible only on your device). Think of the private key as your personal phone’s “key” – plug it in, unlock the message, and voilà, the text is decrypted and readable again.
But how does this work on our smartphones?
Scenario 1: Let’s look at regular encryption in a crude format
Say there’s a person X trying to send a message to person Y over a messaging platform we’ll call “M”. The Messaging platform runs a server called “S”, which facilitates communication between X and Y.
Here, Server also stores the encryption key through which it can decrypt the message.
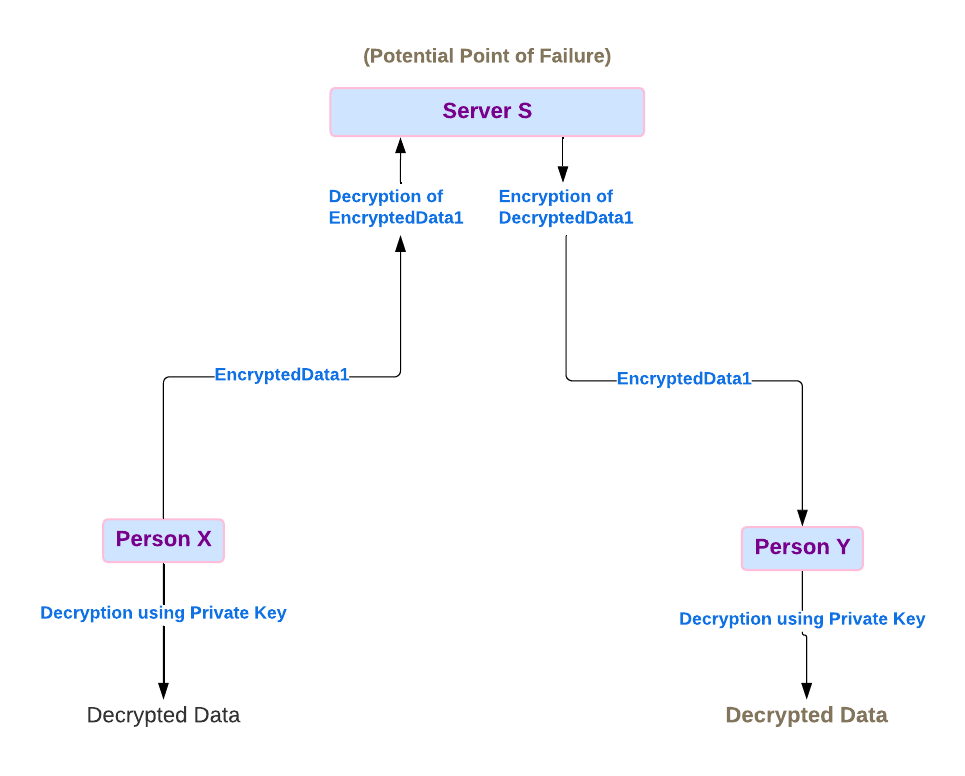
The message sent from Person X is encrypted and sent to the Server S.
Server S decrypts the message, re-encrypts it and sends it to Person Y.
When Person Y receives the message, it's decrypted on their device, making it readable.
Sounds secure, right? Well, let’s take a closer look.
The Catch: Data at Rest vs. Data in Transit
Here, the data in transit (meaning while it's on its way) is encrypted but data at rest (meaning when it sits on devices or the server) is decrypted.
If the server is hacked, then this becomes a single point of failure and all the decrypted data could be exposed, giving hackers full access to the private data. This could open doors for some serious security breach in such scenarios.
Scenario 2: Actual End-To-End Encryption
We’ll be looking at the same example.
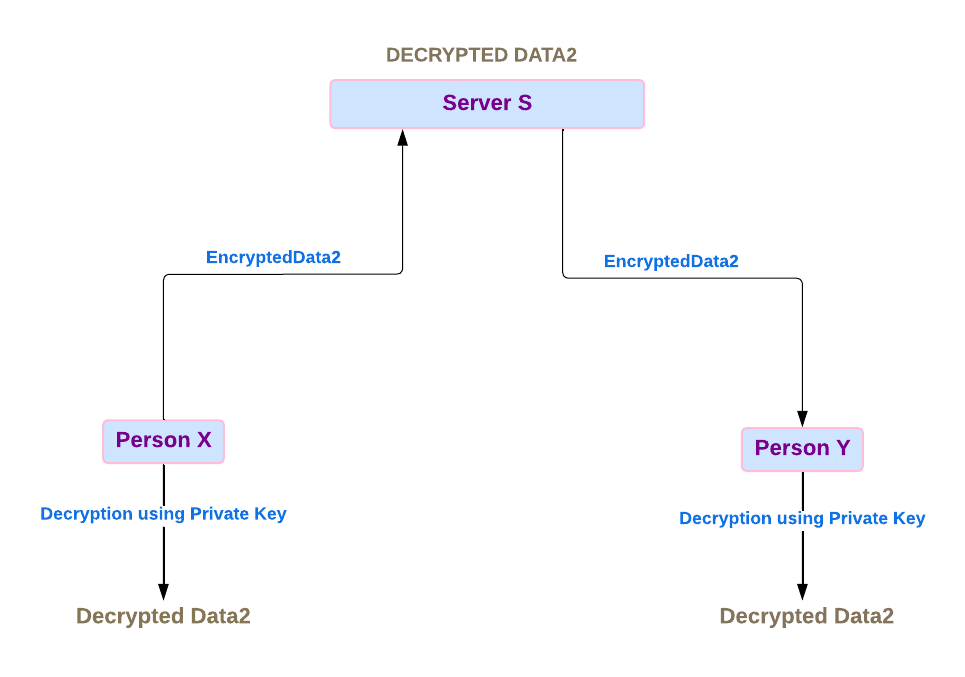
The message sent from Person X is encrypted and sent to the Server S.
Server S cannot decrypt the message as it lacks the key, sends the encrypted message to Person Y.
When Person Y receives the message, it's decrypted on their device, making it readable.
Here, the communication is secure, as both the data in transit and the data at rest are encrypted. Only the sender and the recipient can decrypt the message; no one else, not even the server, can access or steal your data.
So, how is all this encrypted magic possible? Person X and Person Y use a shared key that rotates frequently, boosting security even further. The key exchange itself uses the Diffie-Hellman protocol – but that’s a story for another day.
End-to-End Encryption sounds like the ultimate security guarantee, but there’s more to consider. Even with E2EE, if your credentials are hacked or misplaced, any decrypted data could still be exposed.
Think of it this way: With regular encryption, losing your password doesn’t mean losing access – you can still recover your data. But with true client-side E2EE, if you lose your password, the data is essentially gone for good. That’s both the power and the risk of robust encryption.
And here’s where it gets tricky: many companies today toss around buzzwords like E2EE, but not all actually deliver. Some hold the encryption keys themselves, even serving the encryption software, which could compromise security.
Hence, you NEED to check twice when a company claims they are secure before trusting them with your data.
EXTRA MASALA: Why Are Governments So Eager to Ban End-to-End Encryption?
End-to-End Encryption (E2EE) is the Fort Knox of digital security. But, ironically, that’s the very reason governments are uneasy about it. Here’s the crux: E2EE is so secure that it could potentially allow illegal activities, from terrorism to other crimes, to go unnoticed. Since encrypted messages can’t be accessed by anyone other than the intended recipient, any evidence of illegal activity becomes nearly impossible to obtain.
This lack of access is why some governments are wary of E2EE. With standard encryption, authorities can access server-stored data when necessary. But with E2EE, governments lose that control – and it’s causing quite a stir.
Some governments are even pressurizing the messaging apps to provide “backdoor access” to the E2EE systems .In theory, this backdoor would allow officials to intercept data if there’s a suspicion of illegal activity.
But is this feasible?
Well, you’re absolutely right to think it sounds impossible. If any middle-point decryption were to occur, E2EE’s entire purpose would be compromised. And even if a secure backdoor were created, it wouldn’t be long before hackers discovered this vulnerability and exploited it.
Take Telegram, for example. You may have heard about the French authorities arresting Telegram CEO Pavel Durov (aka “Russia’s Mark Zuckerberg”) for refusing to cooperate with law enforcement. Durov, who has multiple citizenships, was a French citizen too. While the government’s discontent with Telegram has many roots, one of the big reasons is its lack of control over user data.
Telegram uses End-To-End Encryption for private chats. For everything else, data is encrypted on Telegram’s servers. And it goes even further with decentralization: this data is scattered across the globe, making it nearly impossible for governments to access or control. No wonder Telegram and certain governments are currently at loggerheads.
So, this all comes down to a classic dilemma: Personal Privacy or National Security?
Where tech will lead us on this front, we’ll have to wait and see.
Here’s hoping no one ever cracks the code to read all those memes I send to myself,
Anu
Good luck deciphering these links for more:
https://www.youtube.com/watch?v=jkV1KEJGKRA
https://www.youtube.com/watch?v=NmM9HA2MQGI
Subscribe to my newsletter
Read articles from Anusha directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by
