Supply Chain Attacks: Securing Your Software from Third-Party Code
 Abhiram
Abhiram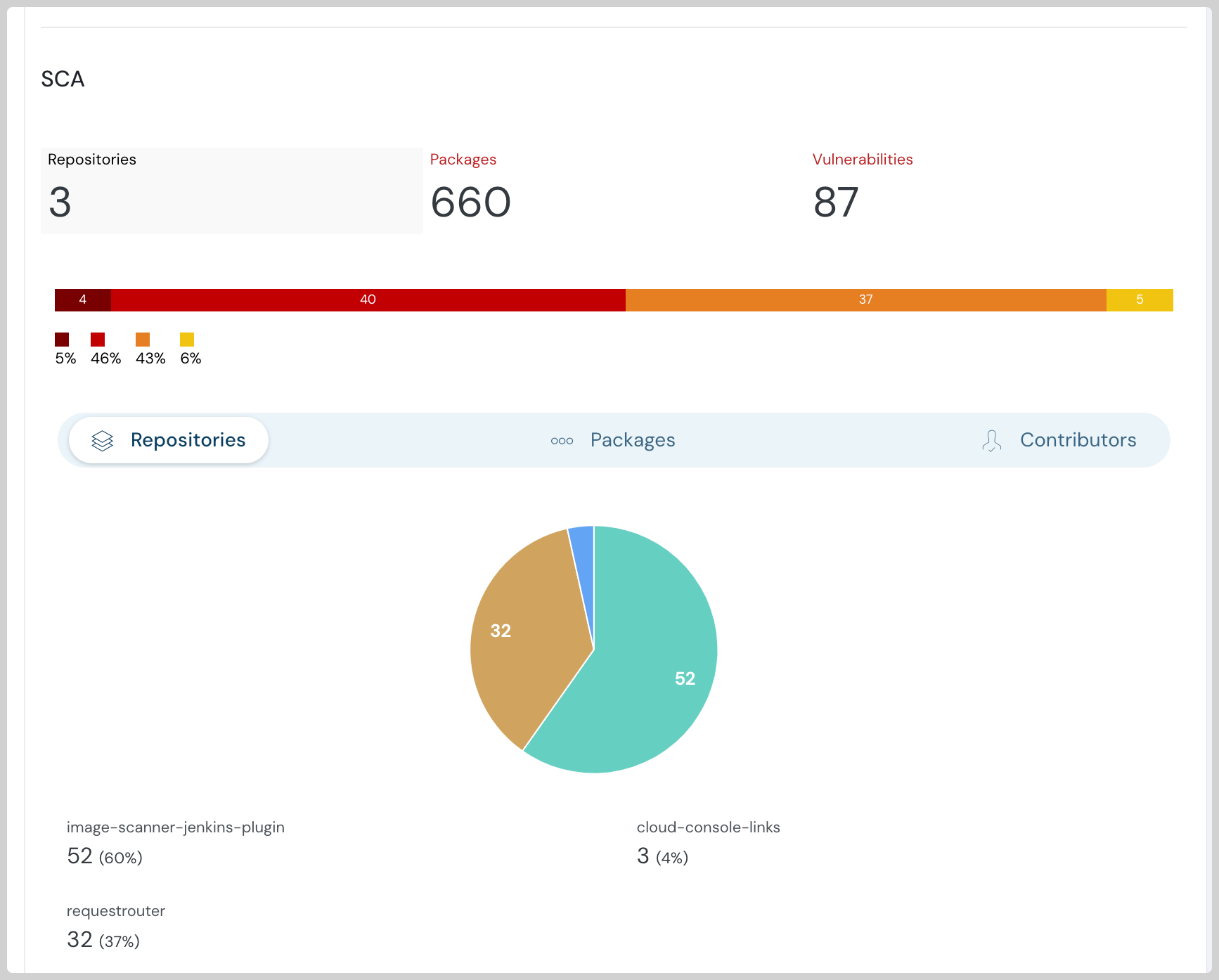
In today's interconnected world, software applications increasingly rely on third-party components. While these components can accelerate development and provide valuable functionality, they also introduce new security risks. Supply chain attacks, which target vulnerabilities in third-party software, have become a major concern for organizations of all sizes.
Understanding Supply Chain Attacks
A supply chain attack occurs when an attacker compromises a third-party component or supplier and uses it to gain access to a target organization's systems or data. These attacks can be difficult to detect and mitigate, as they often exploit vulnerabilities that are not directly related to the target organization's code.
The Risks of Supply Chain Attacks
Supply chain attacks can have serious consequences for organizations, including:
Data breaches: Attackers can use compromised third-party components to steal sensitive data, such as customer information or intellectual property.
Disruption of services: Supply chain attacks can disrupt critical business processes and lead to financial losses.
Reputation damage: A successful supply chain attack can damage an organization's reputation and erode customer trust.
Securing Your Software from Supply Chain Attacks
To protect your software from supply chain attacks, it is essential to implement a comprehensive security strategy. This includes:
Vendor Due Diligence: Carefully evaluate the security practices of third-party vendors and suppliers.
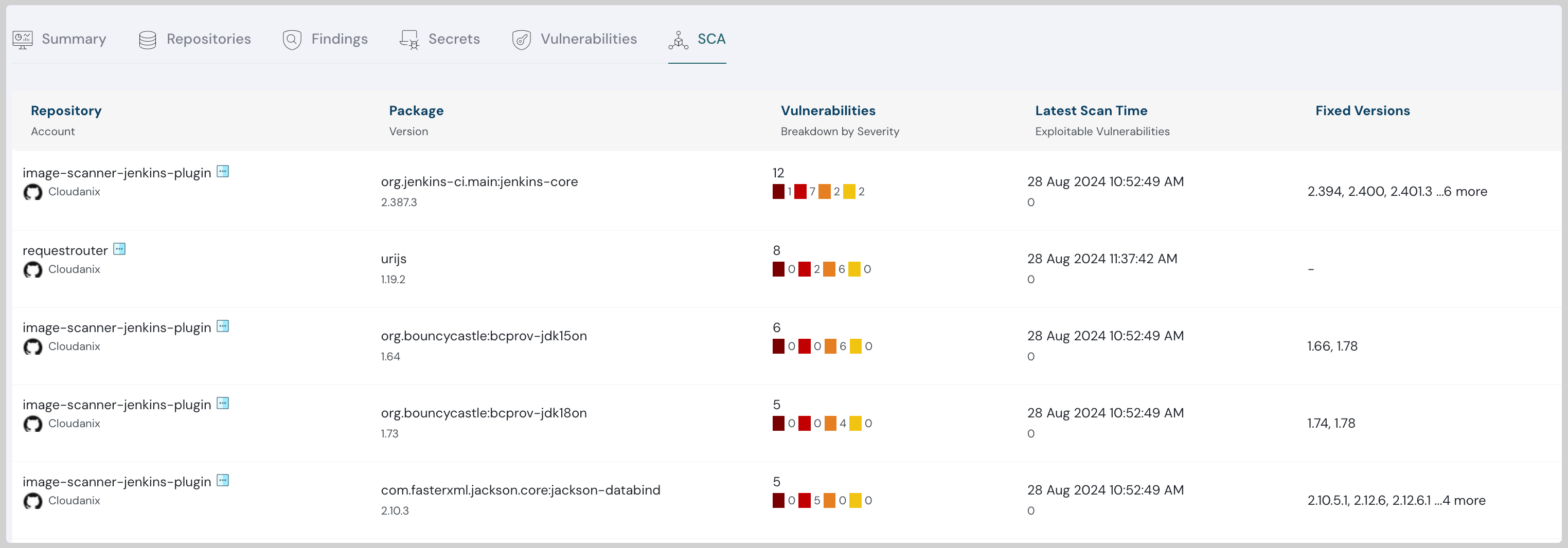
Software Composition Analysis (SCA): Use SCA tools to identify and assess vulnerabilities in third-party components.
Patch Management: Keep all third-party components up-to-date with the latest security patches.
Dependency Management: Use dependency management tools to track and manage the use of third-party components in your applications.
Secure Coding Practices: Ensure that your developers are following secure coding practices to avoid introducing vulnerabilities into your own code.
Incident Response Planning: Develop a plan for responding to supply chain attacks and test it regularly.
Best Practices for Securing Third-Party Components
Prioritize High-Risk Components: Focus on securing third-party components that are critical to your applications or that handle sensitive data.
Regularly Update Components: Keep third-party components up-to-date with the latest security patches.
Use Trusted Repositories: Obtain third-party components from trusted repositories, such as the npm registry or PyPI.
Scan for Vulnerabilities: Regularly scan third-party components for vulnerabilities using SCA tools.
Monitor for Indicators of Compromise (IOCs): Monitor your systems for IOCs that may indicate a supply chain attack.
Emerging Trends in Supply Chain Security
Open-Source Software (OSS): OSS components are widely used in modern applications, making them a prime target for attackers.
DevSecOps: Integrating security into the development process (DevSecOps) can help to prevent vulnerabilities from being introduced into applications in the first place.
Supply Chain Security Standards: Several standards and frameworks, such as NIST 800-171 and the Open Web Application Security Project (OWASP), provide guidance for securing supply chains.
Conclusion
Supply chain attacks are a growing threat to organizations of all sizes. By implementing a comprehensive security strategy and following the best practices outlined in this blog post, organizations can significantly reduce their risk of being targeted by supply chain attacks.
Subscribe to my newsletter
Read articles from Abhiram directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by