eBPF Observability: Revolutionizing System Monitoring in Modern Infrastructure
 DurgaSaran
DurgaSaran
In today's complex cloud-native environments, obtaining deep insights into system behavior without impacting performance has become increasingly challenging. Enter eBPF (extended Berkeley Packet Filter) - a revolutionary technology that's transforming how we approach system observability. Let’s dive into how eBPF is changing the game and how organizations can leverage it for better monitoring and performance insights.
What is eBPF and Why Does it Matter?
eBPF is a technology built into the Linux kernel that allows sandboxed programs to run in privileged kernel space. Unlike traditional monitoring solutions that rely on resource-heavy agents, eBPF provides deep system visibility with minimal overhead. Think of it as having a microscope that examines your system's internals without disturbing its normal operation.
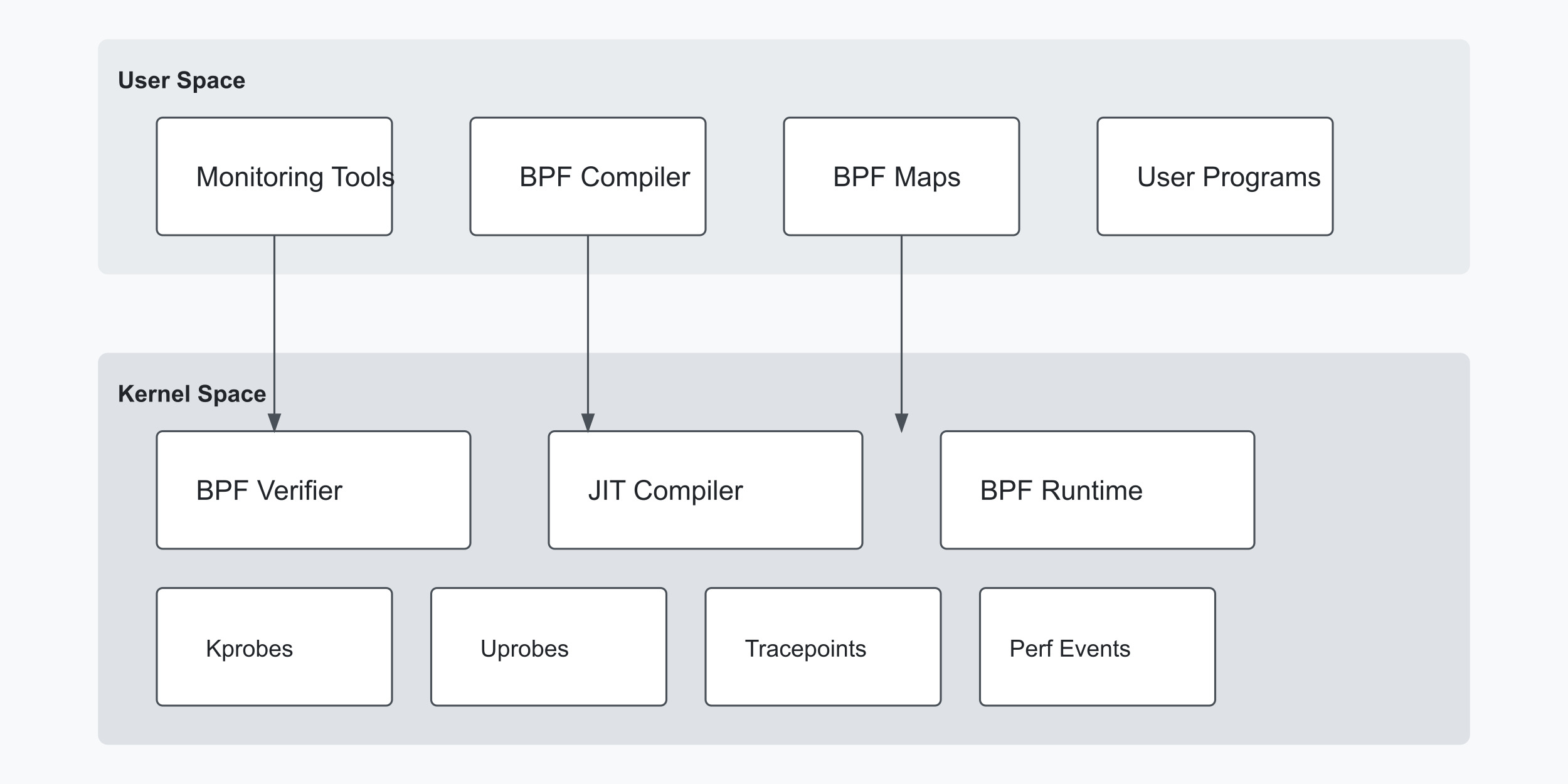
eBPF Architecture Overview
The eBPF architecture consists of several key components that work together to provide efficient system observability:
User Space Components
Monitoring Tools: Interface for collecting and visualizing data, offering real-time insights into system metrics.
BPF Compiler: Converts eBPF programs to bytecode, ensuring compatibility with the Linux kernel.
BPF Maps: Data structures that facilitate data sharing between kernel and user space for real-time observability.
User Programs: Custom applications leveraging eBPF functionality for specialized monitoring needs.
Kernel Space Components
BPF Verifier: Ensures the safety and correctness of eBPF programs, validating code before execution.
JIT Compiler: Converts eBPF bytecode to native machine code, optimizing performance and resource efficiency.
BPF Runtime: Manages and executes eBPF programs within the kernel.
Event Sources: Various attachment points (such as tracepoints, kprobes) for eBPF programs to monitor system events.
Key Benefits of eBPF Observability
Minimal Resource Impact
Lightweight Operation: Consumes as little as 2-3% of system resources, a significant improvement over traditional agents.
Kernel-Space Execution: Runs directly in kernel space, eliminating the need for user-space agents and reducing latency.
Agentless Approach: No additional frameworks or kernel modifications are necessary, keeping the setup minimal.
Enhanced Security
Sandboxed Programs: Ensures eBPF programs run in isolated environments, maintaining kernel security.
Built-In Verification: Kernel verifies eBPF program safety before execution, preventing potential harm.
Root-Level Access Control: Programs require root permissions, safeguarding system integrity.
Comprehensive Visibility
Network Traffic Monitoring (L3, L4, and L7): Provides insights into various network layers without impacting performance.
Process-Level Resource Utilization: Monitors process resource usage and kernel interactions.
Application Performance Metrics: Captures in-depth metrics, from application behavior to system calls.
Use Cases for eBPF Observability
1. Network Observability
Traffic Flow Analysis:
Real-time packet inspection without affecting performance.
Connection tracking across containers and pods.
Protocol-specific analytics (HTTP, DNS, etc.).
Bandwidth utilization per application.
Network Security Monitoring:
Detection and mitigation of DDoS attacks.
Identification of suspicious traffic patterns.
Alerts for network policy violations.
Telemetry for service mesh monitoring.
2. Kubernetes Infrastructure Monitoring
Control Plane Insights:
API server request tracking.
Scheduler decision monitoring for better resource planning.
Latency of etcd operations, providing insights into performance.
Monitoring of controller manager activities.
Data Plane Observability:
Container network performance monitoring.
Inter-pod communication patterns for efficient troubleshooting.
Service discovery metrics.
Assessment of load balancer effectiveness.
Resource Optimization:
Trends in pod resource utilization.
Node capacity planning metrics.
Horizontal scaling insights.
Resource request and limit accuracy analysis.
3. Application Performance Monitoring
Latency Analysis:
Function call latency tracking, optimizing application performance.
System call performance insights.
Timing for I/O operations.
Request path tracing for enhanced troubleshooting.
Resource Usage Patterns:
Tracking of memory allocation patterns.
CPU utilization per thread, identifying performance bottlenecks.
File descriptor usage, a key indicator of application health.
Network socket statistics for communication efficiency.
4. Security Monitoring
Process Behavior Analysis:
Monitoring of system call patterns, providing insight into process behaviors.
File access tracking for security and compliance.
Network connection tracking.
Privilege escalation detection.
Runtime Security:
Detection of container escape attempts.
Unauthorized access alerts.
Filesystem integrity checks.
Monitoring of executable files for security compliance.
5. Infrastructure Performance
Storage Performance:
I/O latency monitoring.
Block device utilization insights.
Cache hit ratio analysis.
File system performance, helping optimize storage efficiency.
System Resource Analysis:
CPU scheduling pattern insights for load balancing.
Memory pressure detection, critical for resource planning.
Network buffer utilization analysis.
Interrupt handling metrics for troubleshooting.
Leveraging eBPF for Observability: Tools and Best Practices
To fully leverage eBPF, organizations can either use standalone eBPF tools or opt for an observability platform with integrated eBPF support. BCC and bpftrace are popular tools for command-line monitoring, while observability platforms like groundcover provide built-in eBPF capabilities for streamlined data collection and visualization.
Best Practices for Using eBPF:
Avoid Unprivileged Mode: Running eBPF with limited permissions is tempting but can limit functionality and security. Stick with root privileges.
Consistent Kernel Versions: Maintain the same kernel versions across systems to avoid inconsistencies.
Targeted Programs: Write eBPF programs designed for specific observability tasks, enhancing efficiency.
Implementing eBPF Observability: A Practical Guide
Step 1: Assessment
Before implementation, verify the prerequisites:
Linux Kernel Version: Ensure it’s 4.4 or higher.
Root Access: Necessary for deploying eBPF programs.
Cloud-Native Architecture: Ideal for leveraging eBPF to its fullest potential.
Step 2: Choose Your Implementation Approach
- Standalone Tools Approach: Ideal for customizations and specific use cases.
# Install BCC toolkit on Ubuntu
apt-get install bcc-tools
# Example: Track new processes
execsnoop-bpf
Integrated Platform Approach: Opt for platforms like groundcover that offer built-in eBPF support, providing:
Pre-built dashboards for easy visualization.
Automated data collection to minimize setup.
Compatibility with existing monitoring tools, enhancing your observability stack.
Step 3: Best Practices for Implementation
Security Considerations:
Avoid unprivileged mode for critical applications.
Enforce strict access controls for eBPF programs.
Regular kernel updates to ensure security patches.
Performance Optimization:
Write focused programs for specific tasks to avoid resource bloat.
Monitor resource usage during deployment.
Regular benchmarking to ensure consistent performance.
Maintenance:
Consistent kernel versions across systems.
Frequent program updates for performance and security.
Document custom implementations for future reference.
Conclusion
eBPF represents a paradigm shift in system observability, offering organizations unprecedented visibility into their systems with minimal overhead. While implementation requires careful planning and expertise, the benefits far outweigh the initial investment. As cloud-native architectures become more complex, eBPF-based observability will likely become the standard for modern infrastructure monitoring.
Subscribe to my newsletter
Read articles from DurgaSaran directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

DurgaSaran
DurgaSaran
Enthusiastic Technical Consultant specializing in DevOps, Data Engineering, and Security. Adept at designing and implementing Observability solutions for real-time insights for Enterprises. Proven track record in optimizing cloud infrastructure for enhanced performance and security.