Modern Cybersecurity Threats
 Yuva Shankar Narayana Dhaipullay
Yuva Shankar Narayana Dhaipullay
what is the role of cybersecurity in this world !
As the internet is growing and it is more accessible to people , people use internet for both good and bad. As a coin has two sides internet has two sides too , where these bad guys pursue malpractices and set damage top normal users or higher business firms.To protect ourselves and have control of our data within us then the cybersecurity comes into play .

Cybersecurity is more of self awareness than looking for help
Lets see some of the threats here
These are the threats which are frequently occuring in day to day life ;
Malwares
Insider threats
Social engineering
Distributed denial of service (DDoS)
Advanced persistent threats (APTs)
Man-in-the-middle (MitM) attacks
Injections
Supply chain attacks and IoT attacks
Lets see in detail !!

Malware
This a most common way where a person is prone for a cyber attack!
A malware contains trojans and viruses where these smartly seek through your device when you download a file from an unauthorised sources.
In Viruses these replicate themselves and corrupt the files and these are hard to identify. They highly exploit your systems vulnerabilities
Ransomware
Where attacker encrypt your files and demand for financial favours.
Cryptojacking
where a infected device is used for crypto mining , unlike the remaining malware where they black mail you with your data , here they use your device for mining crypto currencies which at some point can definitely harm your system.
Social Engineering
This itself a has many inner types of threats in it , here even a well educated person can fall for these. As the fuel for these threats modern AI gives it the boost and hekps the hackers to make these attacks more realistic !!
These are some types of attacks
Spear phishing
Vishing (Voice phishing)
Smishing(SMS phishing)
Business Email Compromise (BEC)

Phishing or Spear Phishing
Here a specific user is targeted and a highly tailored message where it is purely related to the user itself. A user can easily fall into these.
Vishing (Voice Phishing)
As Ai is cruising forward with day to day advancements it is easy to replicate a person’s voice or imitate him/her , a voice note is sent to targeted user which contains a environment where user closer one is in threat and asks for financial or any other favour. As a human is a emotional creature he fall into scam without cross checking.
Smishing(SMS phishing)
A SMS is sent to user with a malicious link where it replicates someone’s identity usually it contains Bank related messages , any free stuff giveaway message ; Where it asks us to follow up through a malicious link.
Business Email Compromise (BEC)
This is a threat where usually happens between business firms , where a false invoice is generated and even sometimes can be asked to do payment through replicate of original payment gate!!
Insider Threats
Kind Of backstabbing other threats can be managed , we can find it out but this one we can’t find out easily. Here a official can misuse his power or can be said breach policies. This can be lead to serious data breaches , financial loss to the firm.
Distributed denial of service (DDoS)
This a technique is used many times in the history of internet , where certain malware attacked computer networks are taken in control and these are known as “BOTNETS” . These Botnets are further used in these DDos attack where a particular website gets access requests from these botnets and make website to crash , it’s server can’t handle these many requests ; some use this for financial benefits and some for personal gains.
Advanced persistent threats (APTs)
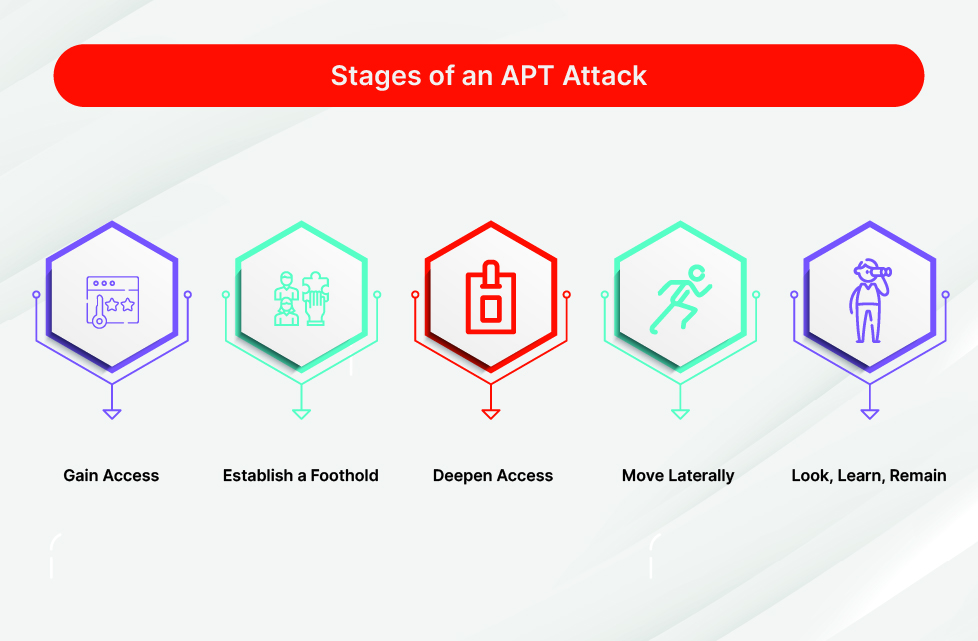
This is a type of threat where a intruder has gained access and sustaining his activities for longer period in search for sensitive data , in this process it is undetected.
Man-in-the-middle (MitM) attacks
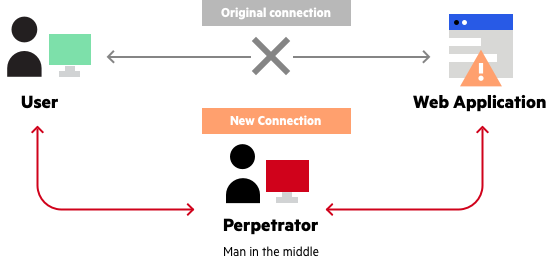
As you can see in pictorial depiction where the hacker set up a middle man role for himself between user and service provider, Most commonly these are occured between E-commerce sites and gateways are also targeted.
This can lead data breach and financial loss.
Injections
There as types of injections
SQL injections
OS command injection
Code injections
SQL INJECTIONS
SQL is the strongest tool ever made to manage data , the whole world’s data is managed under SQL , SQL injections states adding of malicious queries in Database , at end of the day it would definitely cause data and financial loss.
OS command injection
In this attack where attacker has a ability to execute shell commands , which would end up helping him to take over the system.
Code injections
A malicious block of code is injected into the actual web application or application’s code , and exploit its vulnerabilities.
Supply chain and IoT attacks
Supply chain attacks
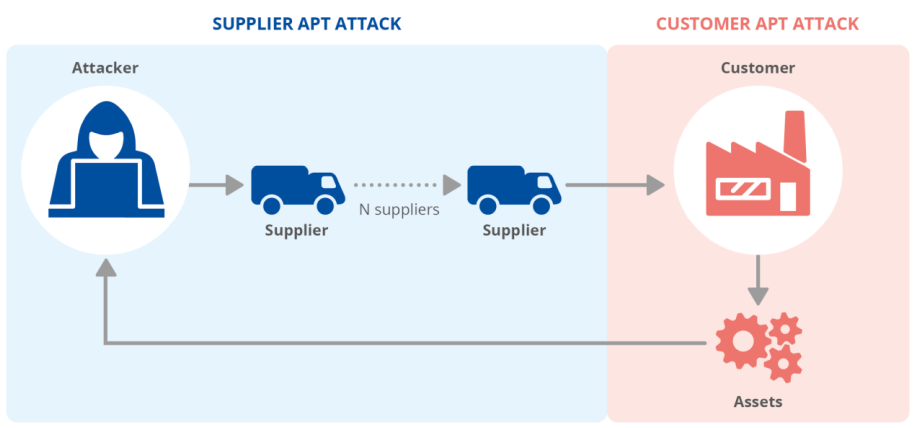
where a trusted supply chain’s relationship is intervened by the attacker , for an example we can see a chain between a reputed mobile company , its products , its customers.
A attacker sends a update patch which contains trojans , here in next scene the attacker gains the benefit of vulnerability and so that relationship between supplier and customer is also ruined.
IoT attacks
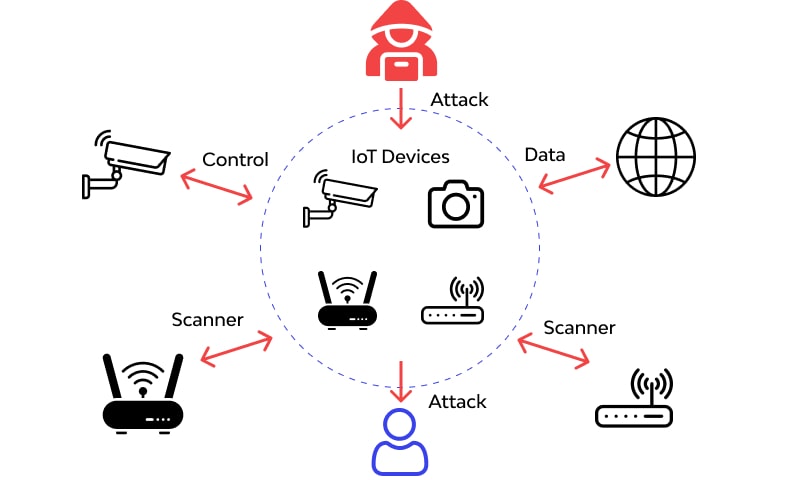
IoT attacks are deadliest attack for a user in this world as the most of the world is connected to internet , these IoT can be CCTV’s , personal assistants like alexa ,etc
Attacker use the vulnerabilities in these kind off device and again access of user’s sensitive data such as voice , face and many more!!
Thanks for referring my article!
Hope you learned something new!!
Yuva Shankar Narayana
Subscribe to my newsletter
Read articles from Yuva Shankar Narayana Dhaipullay directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Yuva Shankar Narayana Dhaipullay
Yuva Shankar Narayana Dhaipullay
A aspiring student pursuing his Bachelors in AI/ML , with passion of 'Cybersecurity'. Here i post my own take on these modern day technologies !!