Web Hacking: Web Application Basics (TryHackMe)
 Jebitok
Jebitok
In this article, I will write a write-up for Web Hacking: Web Application Basics that covers the Web Application Overview, Uniform Resource Locator, HTPP Messages, HTTP Request: Request Line and Methods, HTTP Request: Headers and Body, HTTP Response: Status Line and Status Codes, Security Headers, and a Practical Task: Making HTTP Requests.
Which component on a computer is responsible for hosting and delivering content for web applications?
web serverWhich tool is used to access and interact with web applications?
web browserWhich component acts as a protective layer, filtering incoming traffic to block malicious attacks, and ensuring the security of the the web application?
web application firewallWhich protocol provides encrypted communication to ensure secure data transmission between a web browser and a web server?
HTTPSWhat term describes the practice of registering domain names that are misspelt variations of popular websites to exploit user errors and potentially engage in fraudulent activities?
TyposquattingWhat part of a URL is used to pass additional information, such as search terms or form inputs, to the web server?
Query StringWhich HTTP message is returned by the web server after processing a client's request?
HTTP responseWhat follows the headers in an HTTP message?
Empty LineWhich HTTP protocol version became widely adopted and remains the most commonly used version for web communication, known for introducing features like persistent connections and chunked transfer encoding?
HTTP/1.1Which HTTP request method describes the communication options for the target resource, allowing clients to determine which HTTP methods are supported by the web server?
OPTIONSIn an HTTP request, which component specifies the specific resource or endpoint on the web server that the client is requesting, typically appearing after the domain name in the URL?
URL PathWhich HTTP request header specifies the domain name of the web server to which the request is being sent?
HostWhat is the default content type for form submissions in an HTTP request where the data is encoded as key=value pairs in a query string format?
application/x-www-form-urlencodedWhich part of an HTTP request contains additional information like host, user agent, and content type, guiding how the web server should process the request?
Request HeadersWhat part of an HTTP response provides the HTTP version, status code, and a brief explanation of the response's outcome?
Status LineWhich category of HTTP response codes indicates that the web server encountered an internal issue or is unable to fulfil the client's request?
Server Error ResponsesWhich HTTP status code indicates that the requested resource could not be found on the web server?
404Which HTTP response header can reveal information about the web server's software and version, potentially exposing it to security risks if not removed?
ServerWhich flag should be added to cookies in the Set-Cookie HTTP response header to ensure they are only transmitted over HTTPS, protecting them from being exposed during unencrypted transmissions?
SecureWhich flag should be added to cookies in the Set-Cookie HTTP response header to prevent them from being accessed via JavaScript, thereby enhancing security against XSS attacks?
HttpOnlyIn a Content Security Policy (CSP) configuration, which property can be set to define where scripts can be loaded from?
script-srcWhen configuring the Strict-Transport-Security (HSTS) header to ensure that all subdomains of a site also use HTTPS, which directive should be included to apply the security policy to both the main domain and its subdomains?
includeSubDomainsWhich HTTP header directive is used to prevent browsers from interpreting files as a different MIME type than what is specified by the server, thereby mitigating content type sniffing attacks?
nosniffMake a GET request to
/api/users. What is the flag?THM{YOU_HAVE_JUST_FOUND_THE_USER_LIST}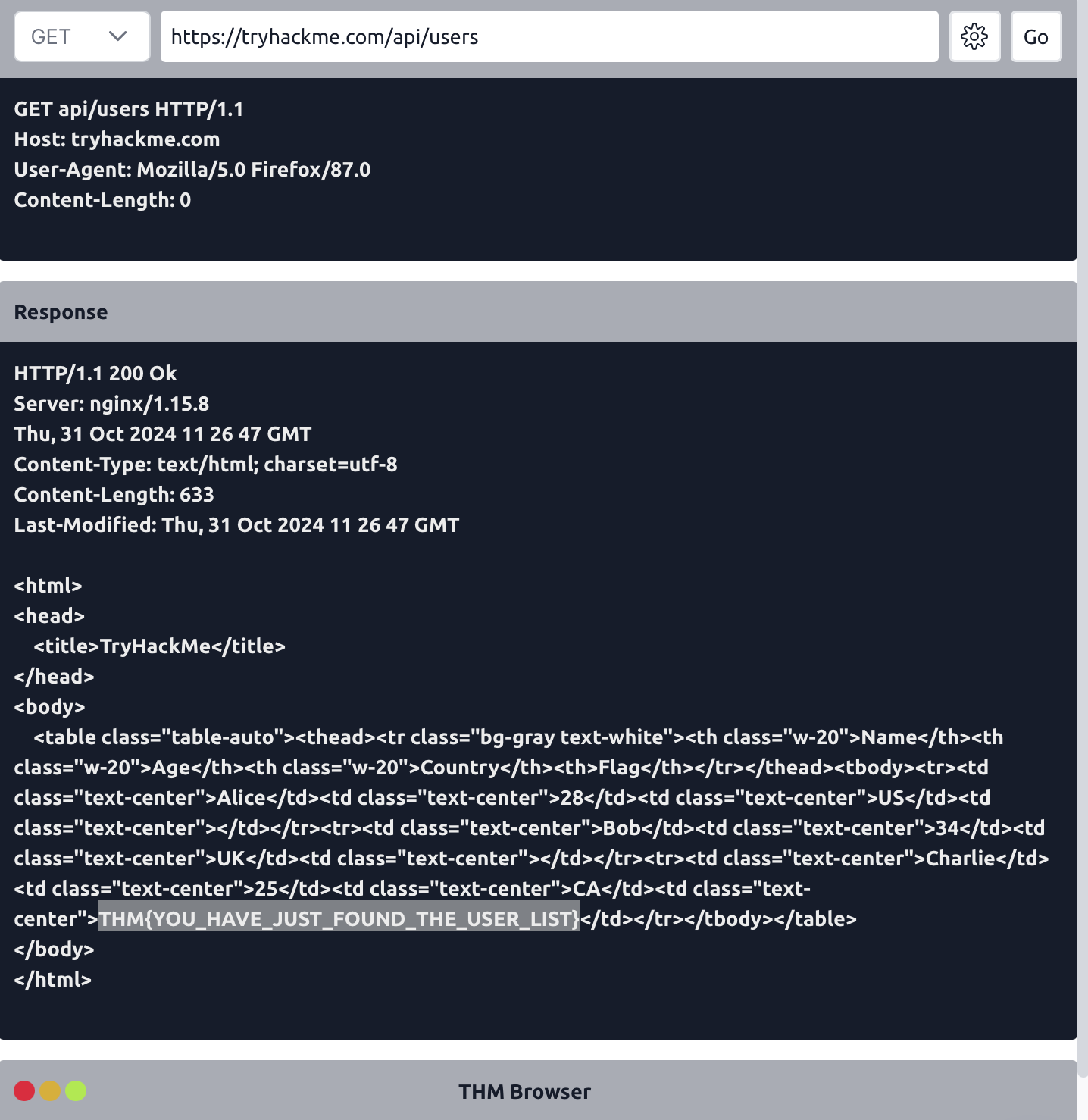
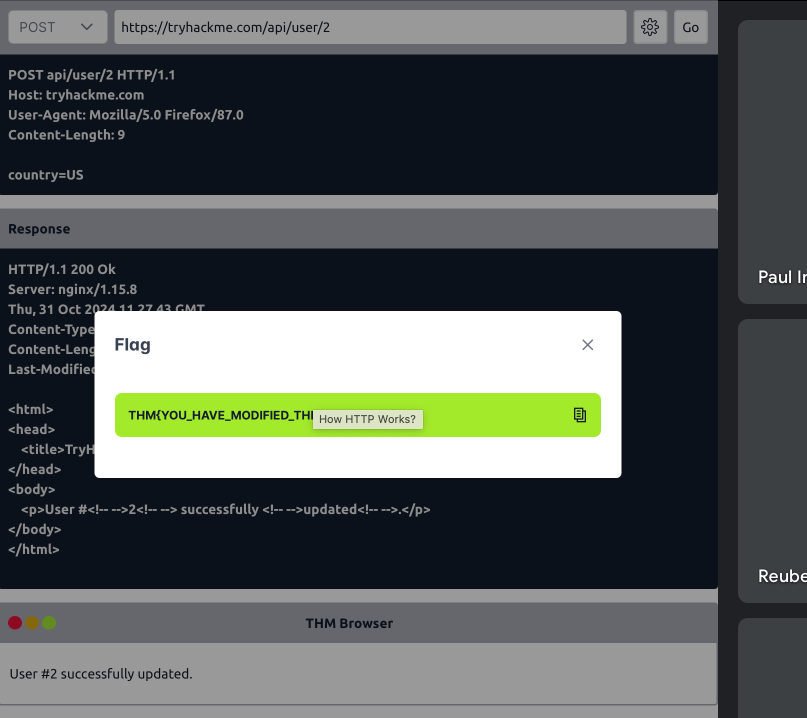
Make a POST request to
/api/user/2and update the country of Bob from UK to US. What is the flag?THM{YOU_HAVE_MODIFIED_THE_USER_DATA}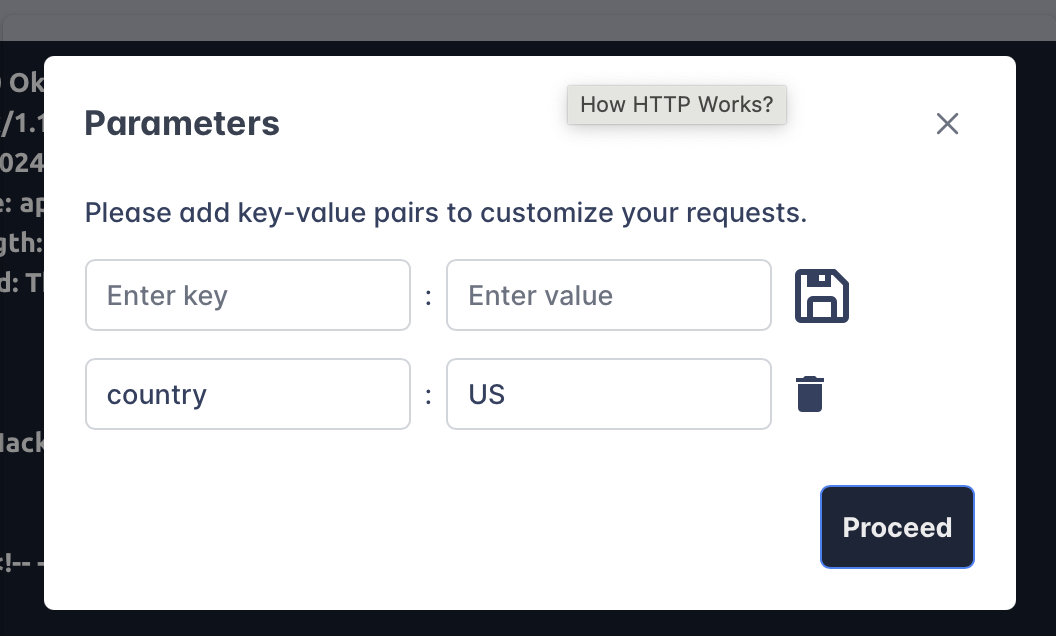
Make a DELETE request to
/api/user/1to delete the user. What is the flag?THM{YOU_HAVE_JUST_DELETED_A_USER}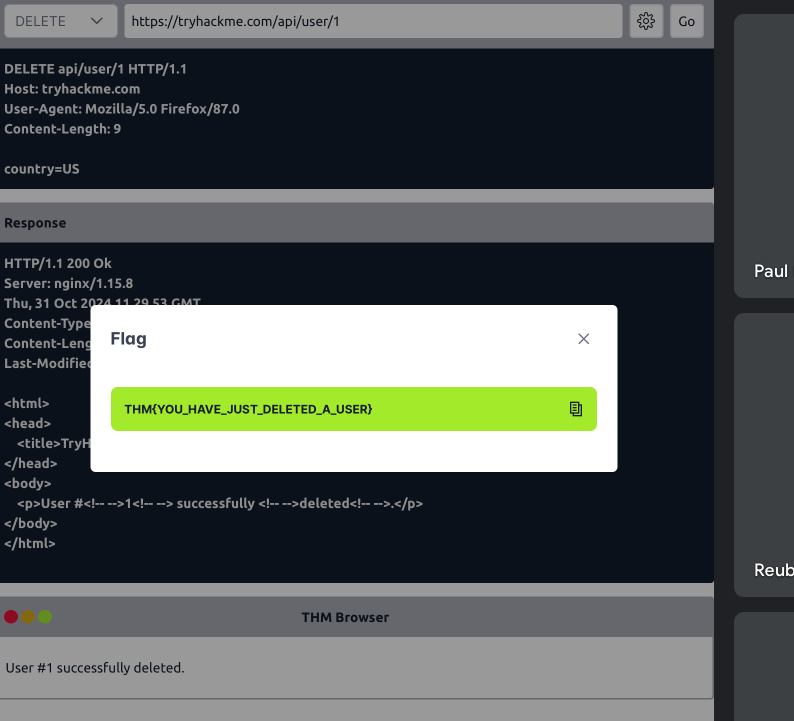
Thank you for reading my article. Please leave any questions or comments on improving my learning journey and the THM challenges.
Subscribe to my newsletter
Read articles from Jebitok directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Jebitok
Jebitok
Software Developer | Learning Cybersecurity | Open for roles * If you're in the early stages of your career in software development (student or still looking for an entry-level role) and in need of mentorship, you can reach out to me.