How to Edit Security Policies & Apply them to Security Groups with PowerNSX
 Dave Davis
Dave DavisTable of contents
Text Guide
In the previous post found here, we discussed how to create security policies with PowerNSX. In this post, I’ll demonstrate how to edit existing security policy firewall rules then apply security policies to security groups with PowerNSX.
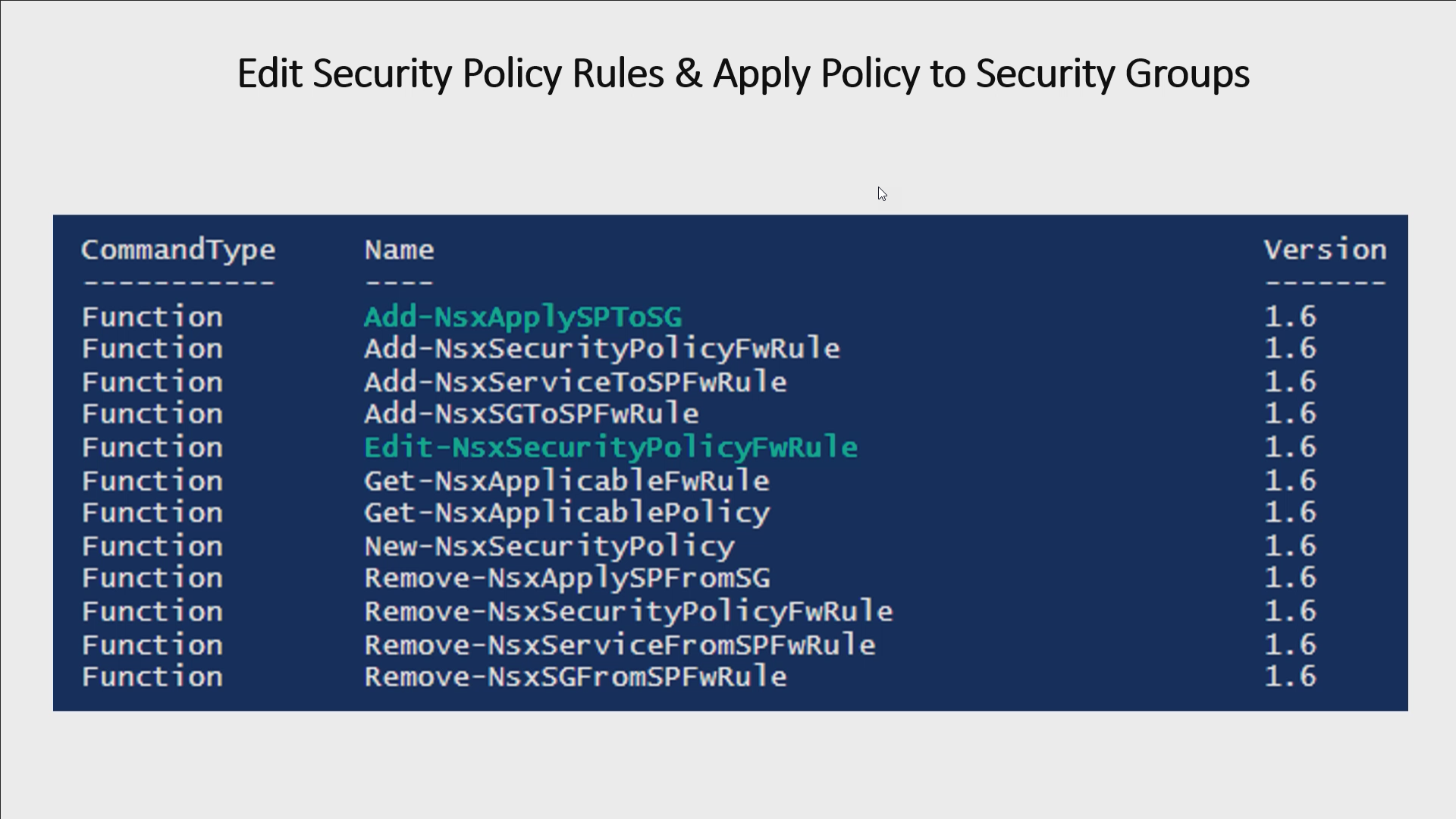
Edit-NsxSecurityPolicyFwRule:
Edit existing Security Policy firewall rules- Parameters: SecurityPolicy, FirewallRule, ExecutionOrder, ReturnObjectIdOnly
Add-NsxApplySpToSg:
Apply security policy to security group(s)- Parameters: SecurityPolicy, SecurityGroup[], ReturnObjectIdOnly
Video Guide
The video below demonstrates the cmdlets discussed in this post.
Disclaimer: The code shown in the video is not included in the PowerNSX module. There is still work to be done as I need to write Pester tests for these cmdlets to ensure everything works as expected and doesn’t break anything else. That said all code has been used in a production environment without issue.
All code used in this demo can be found in my Github repository here.
That it! This is a short and sweet post. Stay tuned for the last post in this series where we’ll discuss how to remove NSX security policy objects using PowerNSX:
Remove a specific NSX security policy rule (Remove-NsxSecurityPolicyFwRule)
Remove a security group(s) from an NSX security policy rule (Remove-NsxSgFromSpFwRule)
Remove a service from an NSX security policy rule (Remove-NsxServiceFromSPFwRule)
Remove an applied security policy from a security group(s) (Remove-NsxApplySpFromSg)
Remove entire NSX security policy (a native PowerNSX cmdlet: Remove-NsxSecurityPolicy)
As well as how to properly decommission NSX Security Groups in order to prevent sync issues.
Subscribe to my newsletter
Read articles from Dave Davis directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by
