Defensive Security: SOC Fundamentals (TryHackMe)
 Jebitok
Jebitok
In this article, I will write a write-up for SOC Fundamentals that covers Introduction to SOC, Purpose and Components, and People, Process, and Technology.
What does the term SOC stand for?
Security Operations CenterThe SOC team discovers an unauthorized user is trying to log in to an account. Which capability of SOC is this?
DetectionWhat are the three pillars of a SOC?
People, Process, TechnologyAlert triage and reporting is the responsibility of?
SOC Analyst (Level 1)Which role in the SOC team allows you to work dedicatedly on establishing rules for alerting security solutions?
Detection EngineerAt the end of the investigation, the SOC team found that John had attempted to steal the system's data. Which 'W' from the 5 Ws does this answer?
WhoThe SOC team detected a large amount of data exfiltration. Which 'W' from the 5 Ws does this answer?
WhatWhich security solution monitors the incoming and outgoing traffic of the network?
FirewallDo SIEM solutions primarily focus on detecting and alerting about security incidents? (yea/nay)
yeaThis practical exercise uses People, Processes, and Technology and gives you a practical walkthrough of the role of a Level 1 Analyst in the SOC team.
Click on the View Site button below to display the lab on the right side of the screen.
View Site
Scenario
You are the Level 1 Analyst of your organization’s SOC team. You receive an alert that a port scanning activity has been observed on one of the hosts in the network. You have access to the SIEM solution, where you can see all the associated logs for this alert. You are tasked to view the logs individually and answer the question to the 5 Ws given below.
Note: The vulnerability assessment team notified the SOC team that they were running a port scan activity inside the network from the host:
10.0.0.8What: Activity that triggered the alert?
Port ScanWhen: Time of the activity?
June 12, 2024 17:24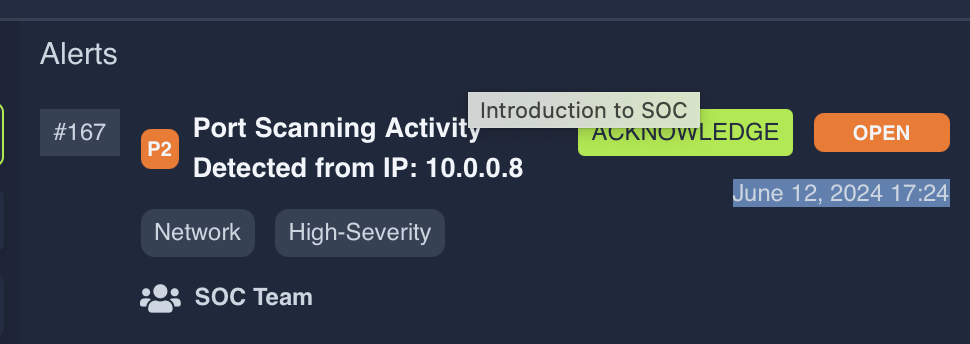
Where: Destination host IP?
10.0.0.3Who: Source host name?
Nessus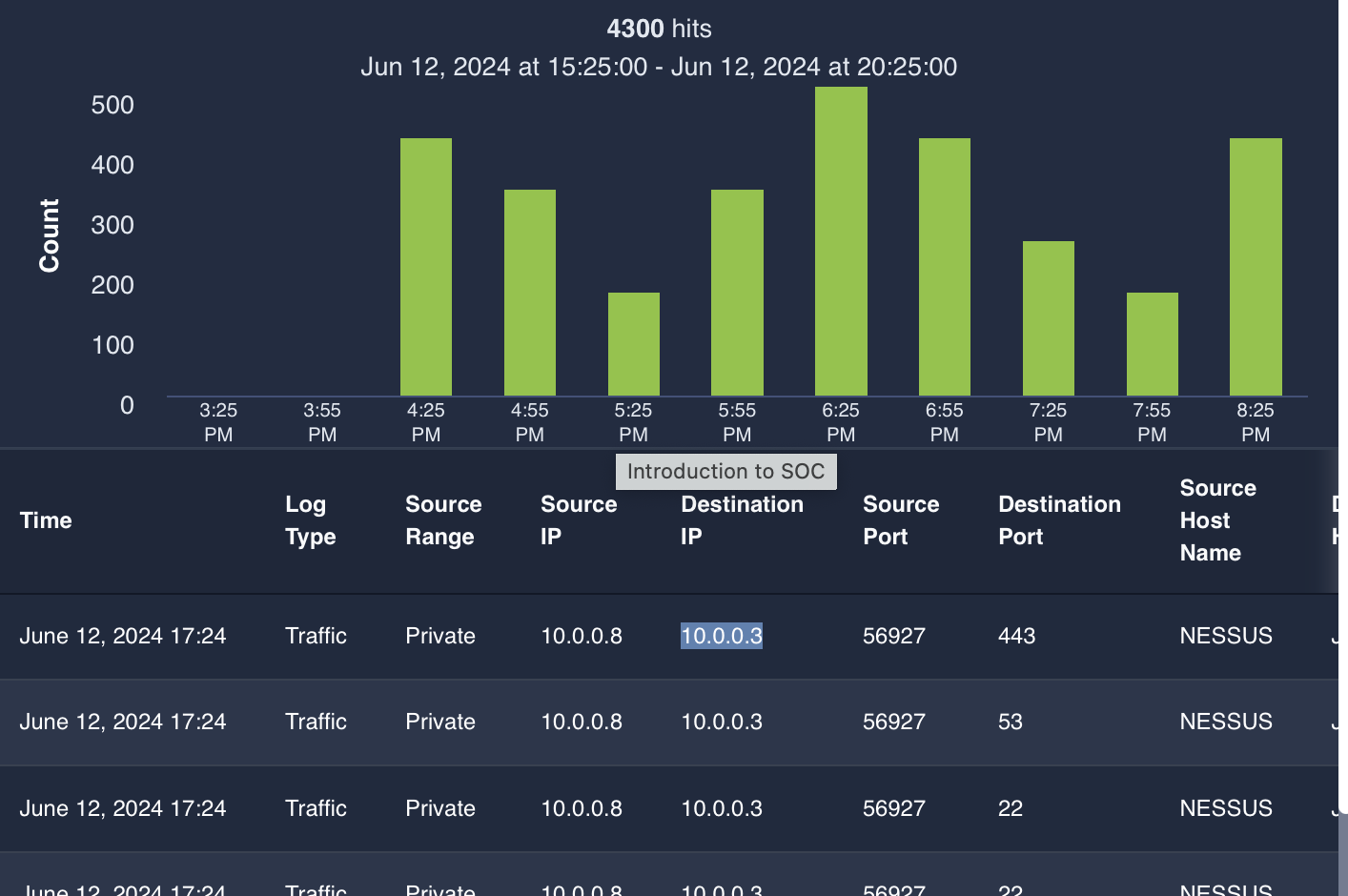
Why: Reason for the activity? Intended/Malicious
IntendedAdditional Investigation Notes: Has any response been sent back to the port scanner IP? (yea/nay)
yeaWhat is the flag found after closing the alert?
THM{000_INTRO_TO_SOC}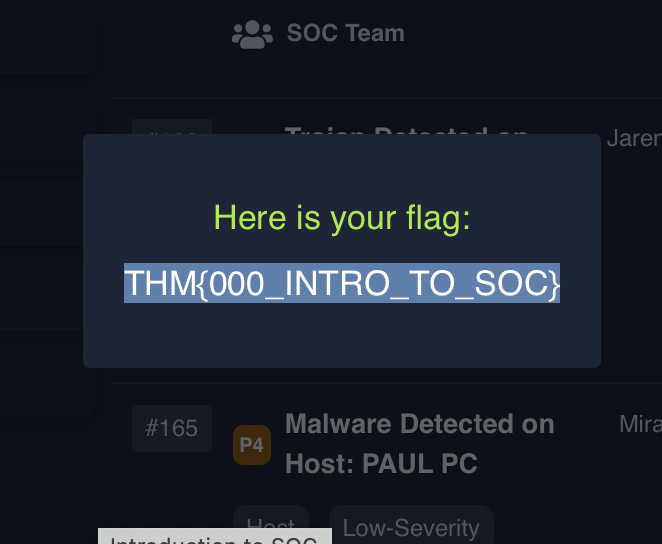
Thank you for reading my article. Please leave any questions or comments on improving my learning journey and the THM challenges.
Subscribe to my newsletter
Read articles from Jebitok directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Jebitok
Jebitok
Software Developer | Learning Cybersecurity | Open for roles * If you're in the early stages of your career in software development (student or still looking for an entry-level role) and in need of mentorship, you can reach out to me.