Defensive Security: Incident Response Fundamentals (TryHackMe)
 Jebitok
Jebitok
In this article, I will write a write-up for Incident Response Fundamentals that covers Introduction to Incident Response, What are Incidents, Types of Incidents, Incident Response Process, Incident Response Techniques, and Lab Work Incident Response.
What is triggered after an event or group of events point at a harmful activity?
AlertIf a security solution correctly identifies a harmful activity from a set of events, what type of alert is it?
true positiveIf a fire alarm is triggered by smoke after cooking, is it a true positive or a false positive?
false positiveA user's system got compromised after downloading a file attachment from an email. What type of incident is this?
malware infectionWhat type of incident aims to disrupt the availability of an application?
Denial of serviceThe Security team disables a machine's internet connection after an incident. Which phase of the SANS IR lifecycle is followed here?
containmentWhich phase of NIST corresponds with the lessons learned phase of the SANS IR lifecycle?
Post Incident ActivityStep-by-step comprehensive guidelines for incident response are known as?
PlaybooksYou will perform a complete incident response after a phishing email hits multiple hosts in a network. You have to follow the steps given in the site and answer the questions below:
What was the name of the malicious email sender?
Jeff Johnson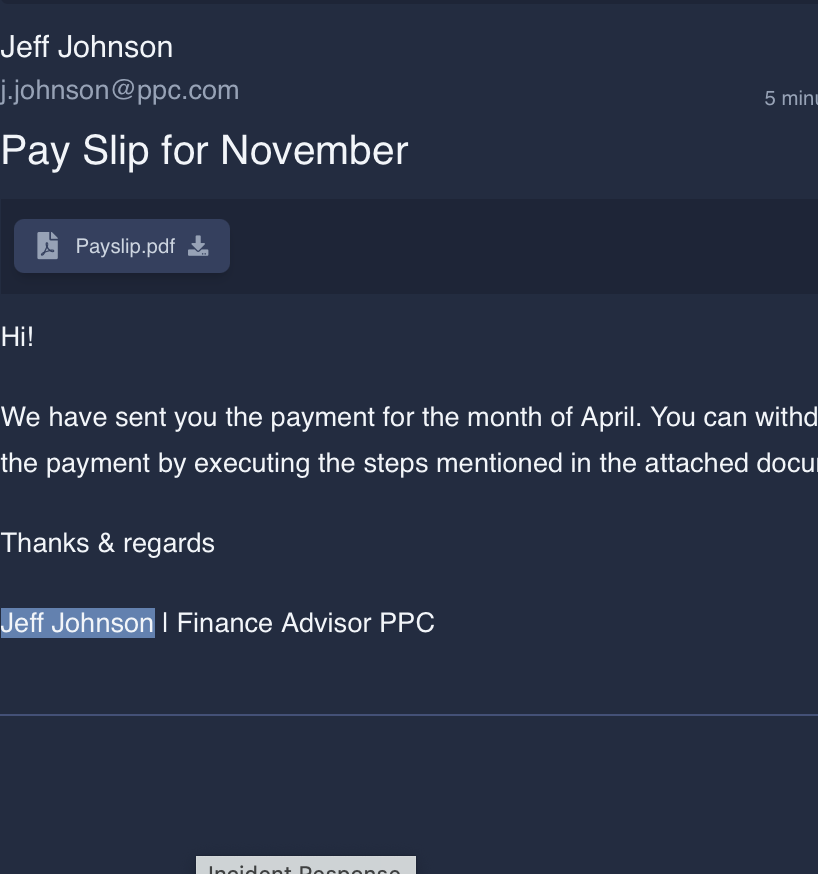
What was the threat vector?
Email AttachmentHow many devices downloaded the email attachment?
3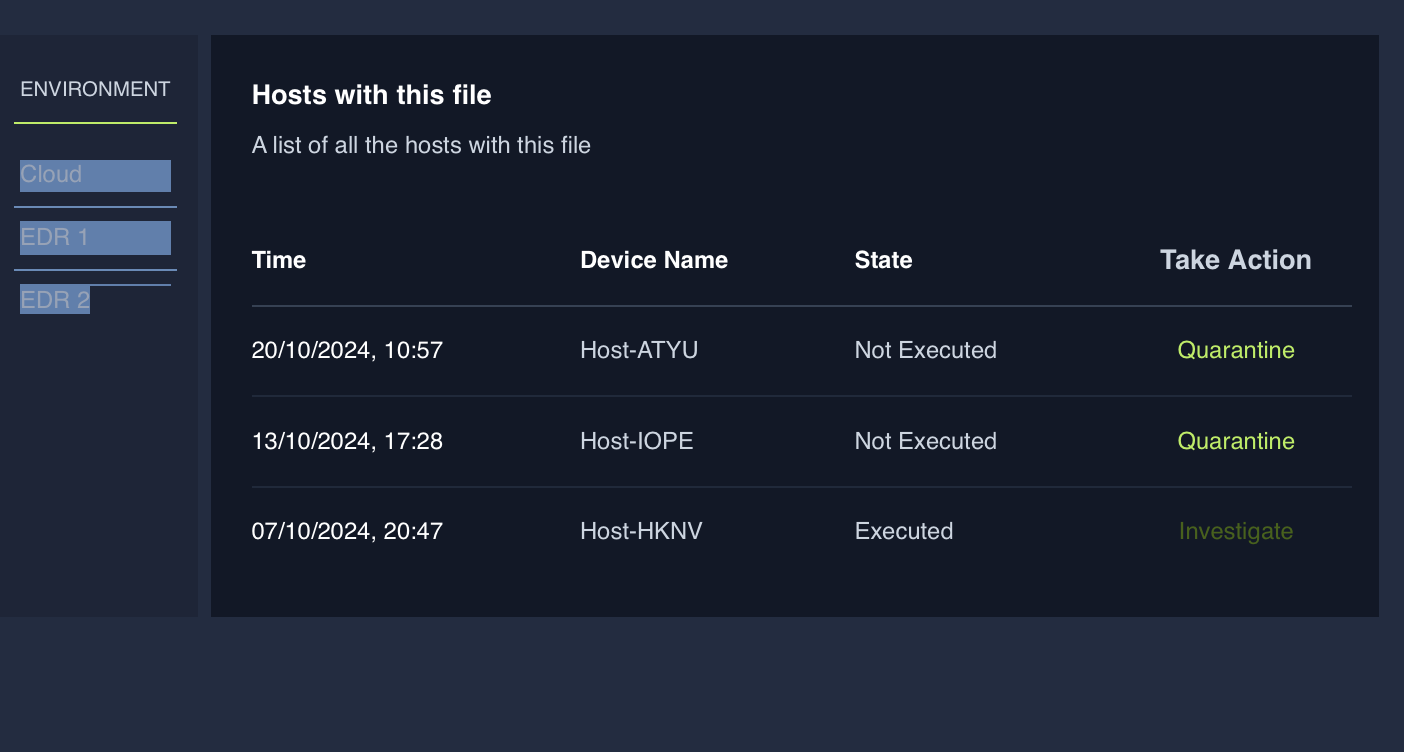
How many devices executed the file?
1What is the flag found at the end of the exercise?
THM{My_First_Incident_Response}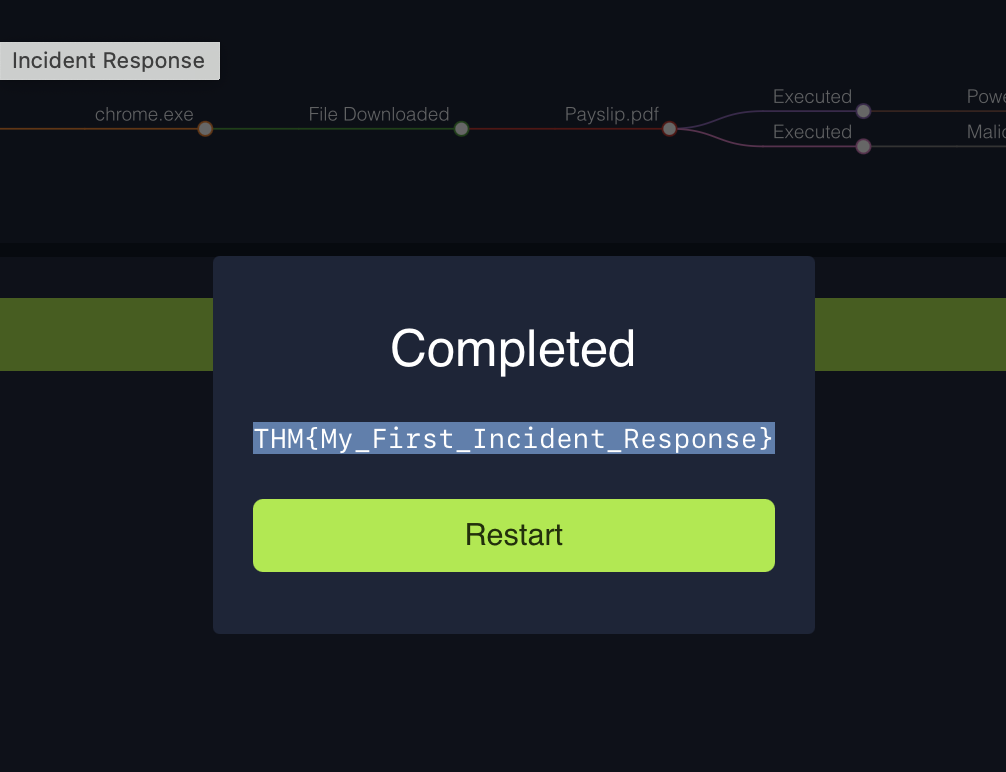
Thank you for reading my article. Please leave any questions or comments on improving my learning journey and the THM challenges.
Subscribe to my newsletter
Read articles from Jebitok directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Jebitok
Jebitok
Software Developer | Learning Cybersecurity | Open for roles * If you're in the early stages of your career in software development (student or still looking for an entry-level role) and in need of mentorship, you can reach out to me.