Defensive Security: Logs Fundamentals (TryHackMe)
 Jebitok
Jebitok
In this article, I will write a write-up for Logs Fundamentals that covers Introduction to Logs, Types of Logs, Windows Event Logs Analysis, and Web Server Access Logs Analysis.
Where can we find the majority of attack traces in a digital system?
LogsWhat is the name of the last user account created on this system?
hackedWhich user account created the above account?
Administrator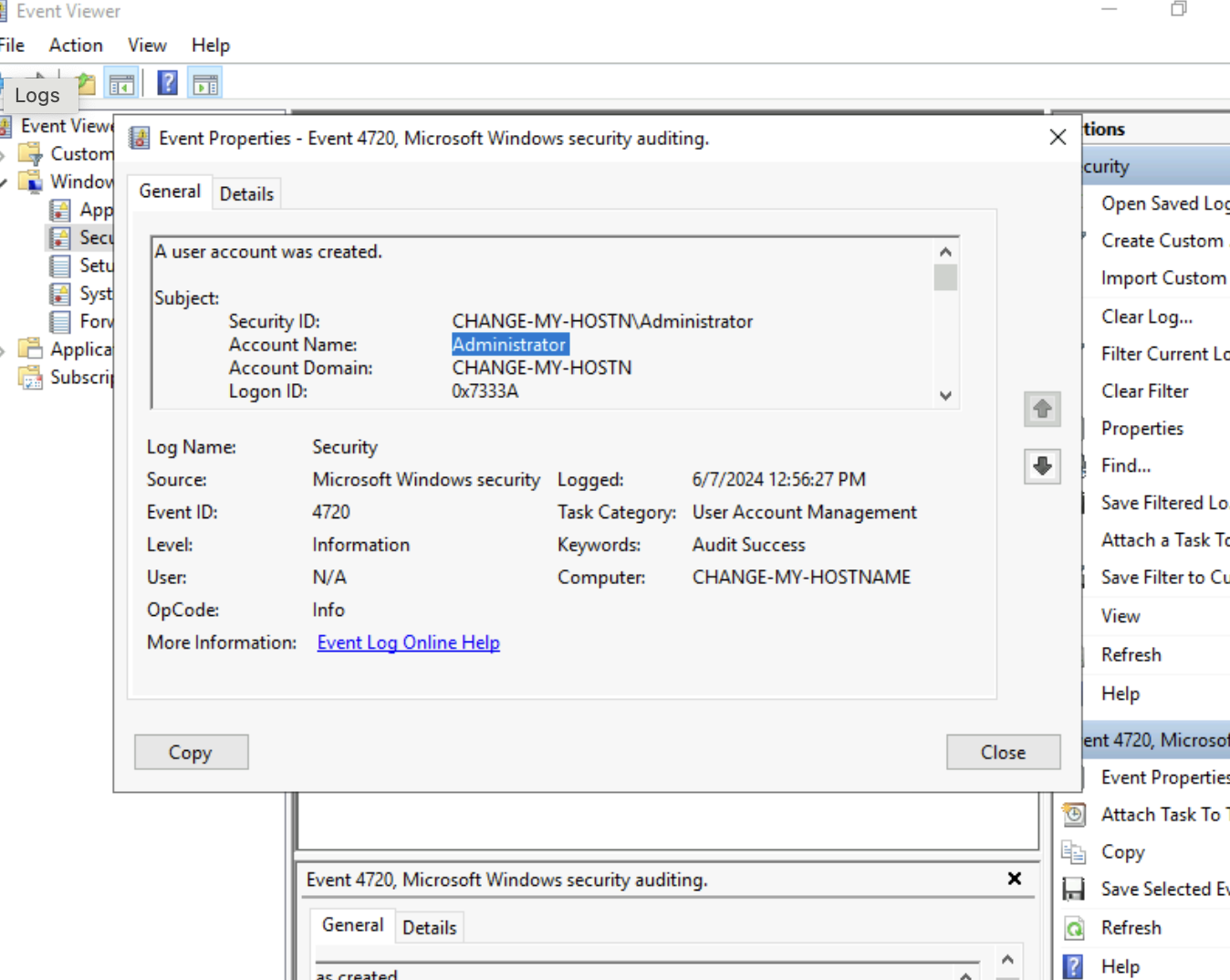
On what date was this user account enabled? Format: M/D/YYYY
6/7/2024Did this account undergo a password reset as well? Format: Yes/No
Yes
If you are downloading the log file for the analysis, some browsers like Chrome would block downloading it because it contains IP addresses, URLs, and User agent strings that may be flagged as malicious by their security mechanisms. You can click “Keep file” or any other alternative option available in your browser after it blocks the download.
What is the IP which made the last GET request to URL: “/contact”?
10.0.0.1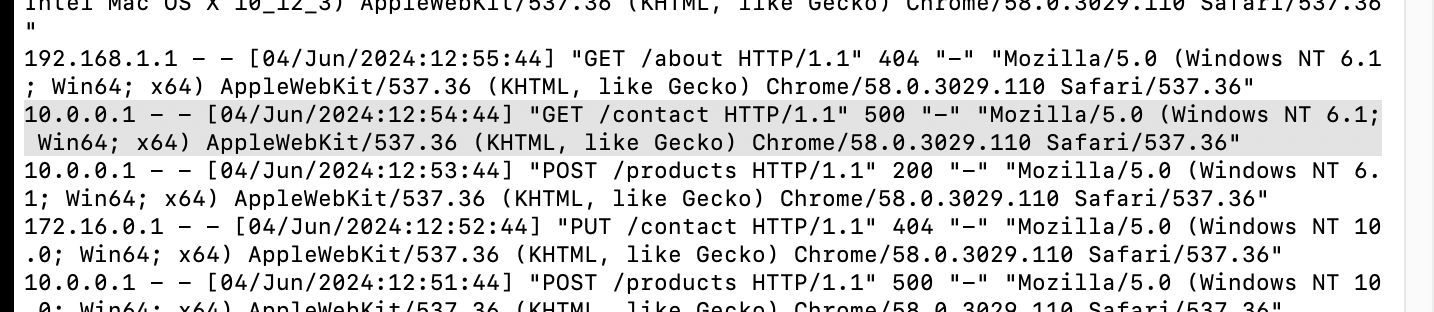
When was the last POST request made by IP: “172.16.0.1”?
06/Jun/2024:13:55:44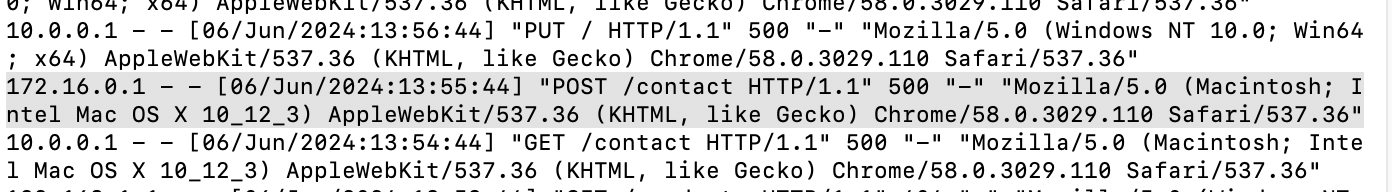
Based on the answer from question number 2, to which URL was the POST request made?
/contact
Thank you for reading my article. Please leave any questions or comments on improving my learning journey and the THM challenges.
Subscribe to my newsletter
Read articles from Jebitok directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Jebitok
Jebitok
Software Developer | Learning Cybersecurity | Open for roles * If you're in the early stages of your career in software development (student or still looking for an entry-level role) and in need of mentorship, you can reach out to me.