Exploring the Virtual Private Cloud and playing around with NACL and Security Group
 Vasuki Janarthanan
Vasuki Janarthanan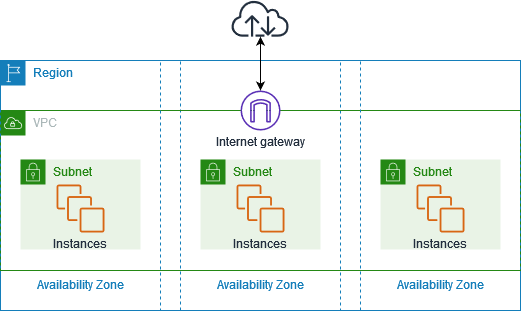
What is AWS VPC?
The isolated region where we can perform our networking tasks is separated from the public cloud world by adding lots of security.
Components of VPC :
The user in the outside world wants to access the application through the internet that is in the virtual private cloud.
What are the steps and processes involved during this process?
1. The user request will sent to Internet Gateway. Internet Gateway is the entry point that allows communication between instances in our VPC and the internet.
2. Internet Gateway will pass to the public subnet. The public subnet is the one that can be accessed outside the VPC.
3. Then Load balancer will navigate that traffic to the specified subnets using the route table. The route table defines the routes to reach the subnet.
4. Then NACL is the layer that is on top of the subnets. It will decide to accept or decline that request based on the rules defined by the DevOps or AWS engineer.
5. Then the traffic, approaches the EC2 instance before that another defense layer occurs which is the security Group. That will accept only the authorized request to the EC2 Instances.
6. Then the request traffic will access the application inside the EC2 Instances.
Accessing the application from the outside world to VPC through the internet needs this process to ensure security. That’s why a Virtual Private Cloud is more secure than a Public cloud.
Creating your Own VPC in AWS :
Initially, when you create an account in the AWS Console, it will create a default VPC for you. So that you can create ec2 instances and access the service you want.
Actually, we are telling how much space we need for our VPC in an IP address way. (i.e) By telling a range of IP addresses for our virtual region.
Ex : 10.0.0.0/16
This is IPV4 addressing. IPV4 is a 32-bit addressing, it has 4 octets separated by dots, and each octet has 8 bits. Each bit has a range of 0 to 255.
10.0.0.0 is the starting network address for our VPC. /16 means the first 16 bits were the network part and the remaining bits were for hosting the devices within that network.
Here is 10.0 -> for the network part
0.0 -> for the host part (ie 255.255)
Therefore, it has 65, 356 IP addresses inside this VPC.
How to calculate the available IPs?
10.0.0.0/16
Network bits: 16 (the first 16 bits are fixed, defining the network).
Host bits : 32 – 16 = 16 ( why 32? this is the ipv4 addressing bit size)
Available bits: 2^16 = 65,356
Range : 10.0.0.0 to 10.0.255.255
Allocating IP address to Subnets :
In the entire VPC, we can split into subnetworks(subnets) for each resource. By allocating an IP address for each subnet from the VPC IP address range.
This means you can split this large area into smaller “streets” (subnets) for different uses within your VPC.
NACL :
Network Access Control List(NACL) applied at the subnet level. NACL acts as a first layer of defense that will allow or decline requests at the subnet layer.
Security Groups:
Act as a virtual firewall at the instance level. It has two traffics.
Inbound traffic:** This is the request from the outside world to the EC2 Instance.
Outbound traffic:** This is the request from EC2 Instance to fetch some information from the outside world. For this, it will navigate through the NAT(Network Address Translation) Gateway to mask its IP address and hide from the outside world.
By default any instances it has only outbound request traffic only.
What DevOps engineer will do?
As a DevOps engineer, we will create a Virtual Private Cloud. And defining the rules for which requests will be allowed and which requests will be declined based on the specified port address we will define.
Instead of setting rules inside the security groups for each EC2 Instance, we automate this task by defining the NACL Layer to which port will allow or decline.
Security group Vs NACL :
NACL will act as a first layer, let’s say port no 8000 will not allow in the NACL and that port will allow in the Security group means, of course, NACL will win. Because NACL will act as a first layer. Even the application developer will allow the port, if NACL allows then only the request reaches to Security group. If the security group allows that port, it can access the application inside the EC2 Instance.
NACL -> Have ALLOW and DECLINE Options for the traffic
SECURITY GROUP -> HAS ONLY ALLOW Option for the traffic
Playing with NACL and Security groups inside the VPC:
1. Create a VPC in your AWS account. By default, it creates an internet gateway, NACl with default configurations and route table.
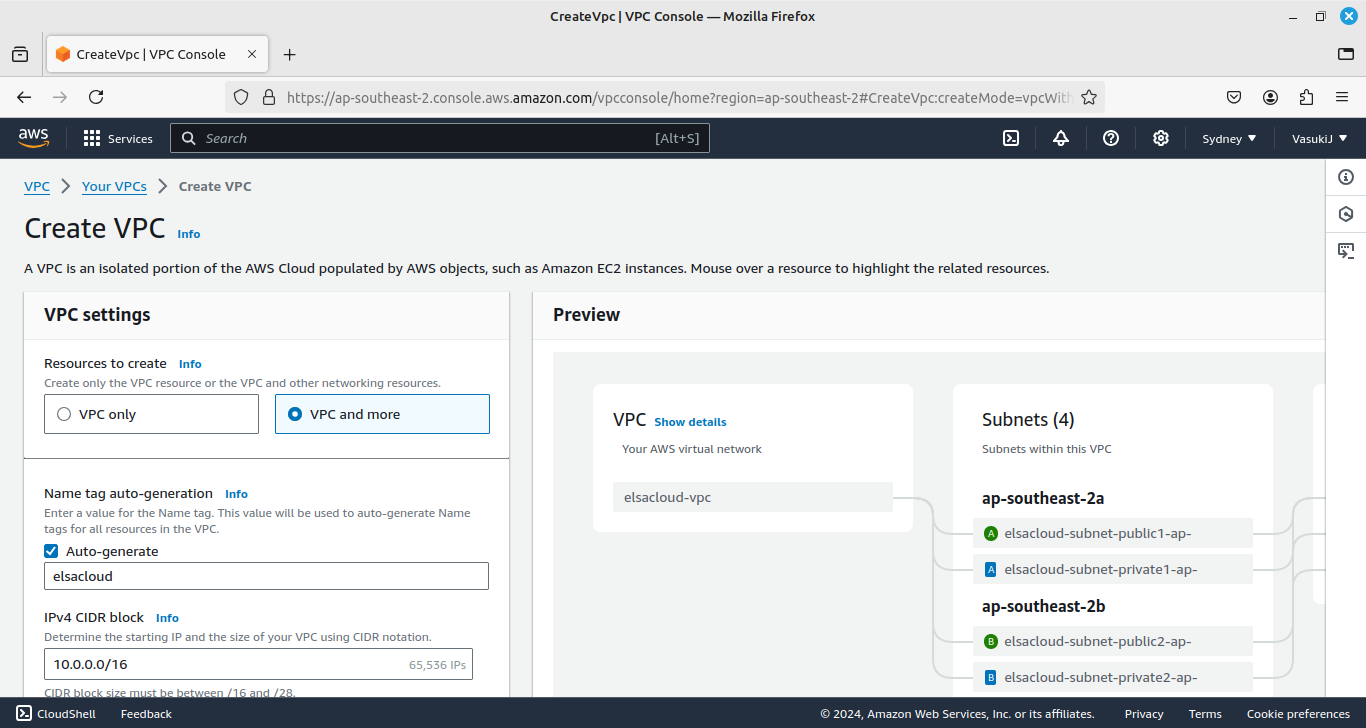
This is the preview of our Created VPC,

You can see that, there is a combination of public and private subnets in the two availability zone.
Only public subnets are connected to the igw (internet gateway).
2. Then create an EC2 Instance and place it inside the VPC that you have created by editing the network configurations.
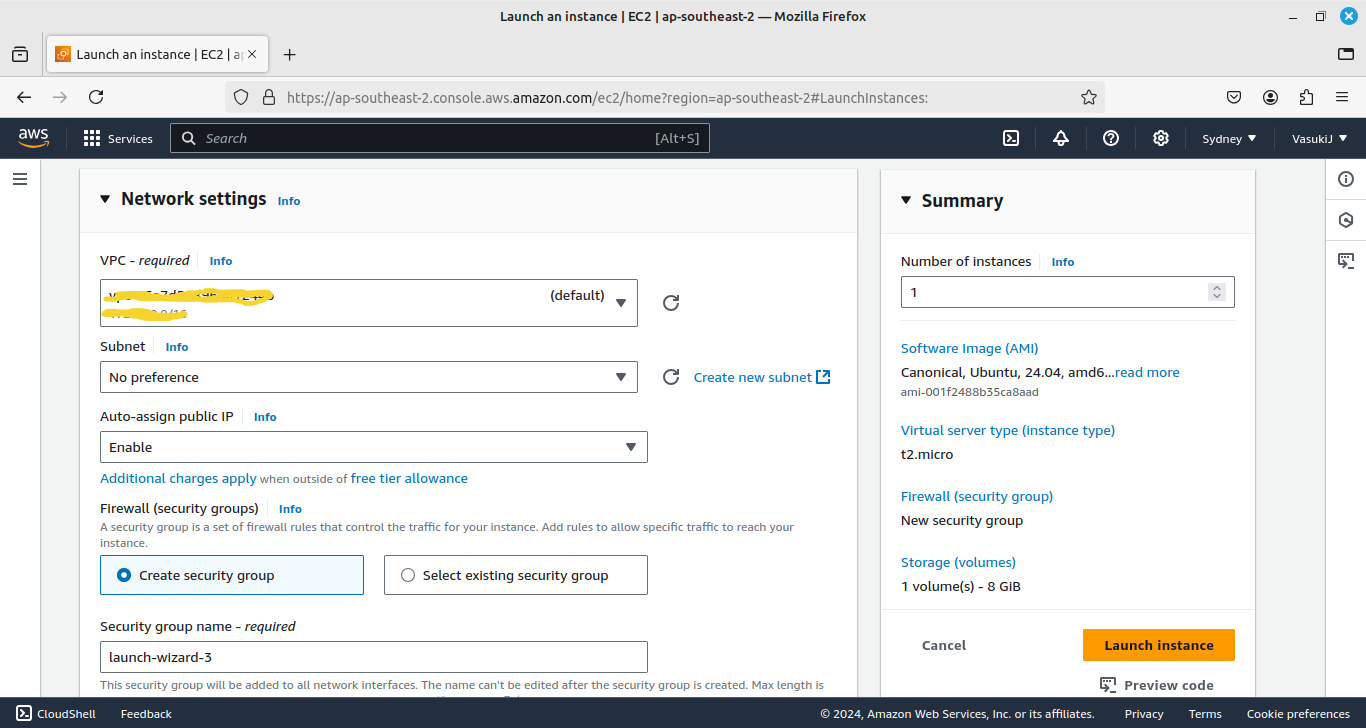
Choose the newly created VPC instead of the default one. Then launch instance.
3. Then log in to your instance from the terminal and install the Python application.
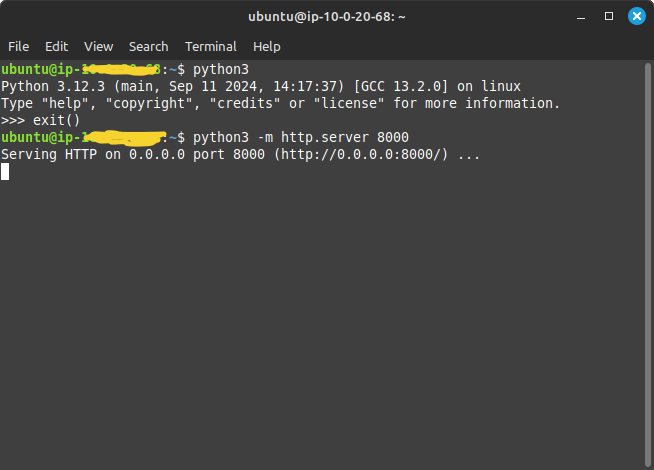
4. Run the simple HTTP server on the Python application with the port 8000.
5. Then try to access the http://your_ip_address:8000. The application will not be accessed.
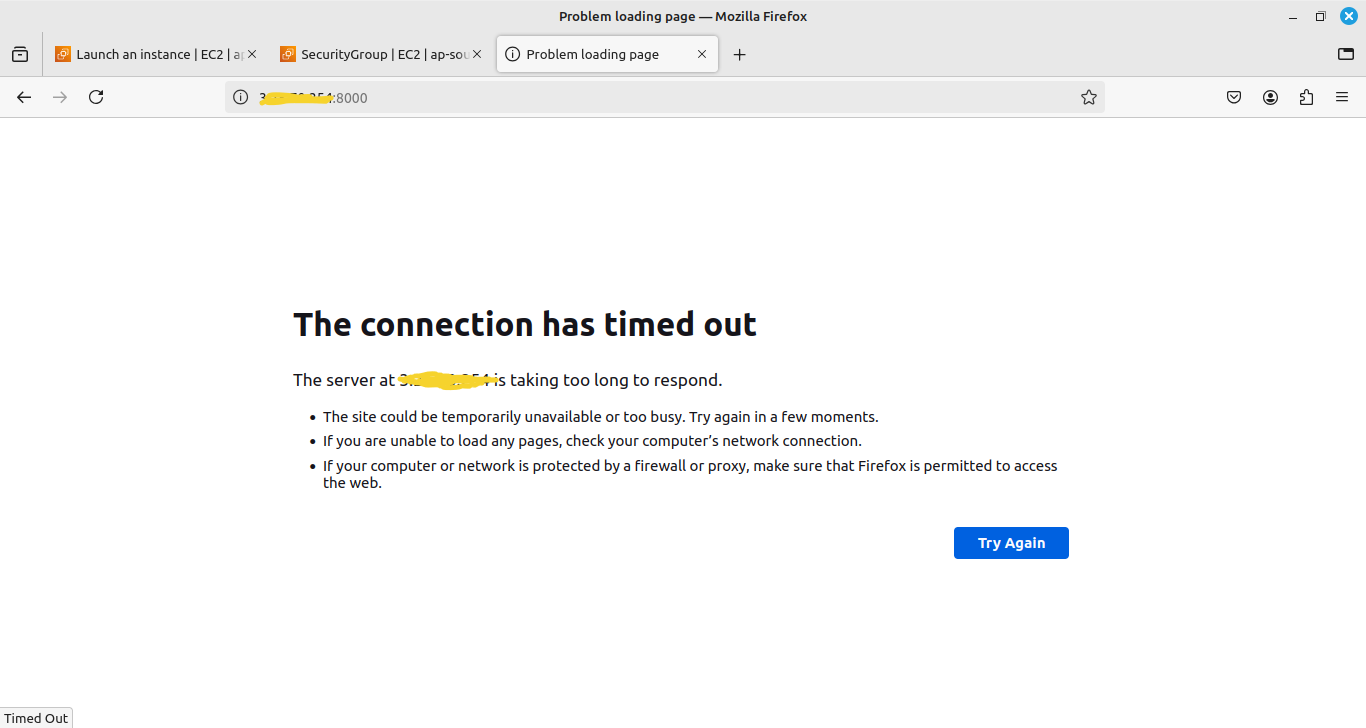
Why it was not accessed? Because the security group has only outbound requests by default. As a DevOps engineer, we have to configure or add the rule for incoming request traffic.
First, we check that NACL will allow the inbound traffic,
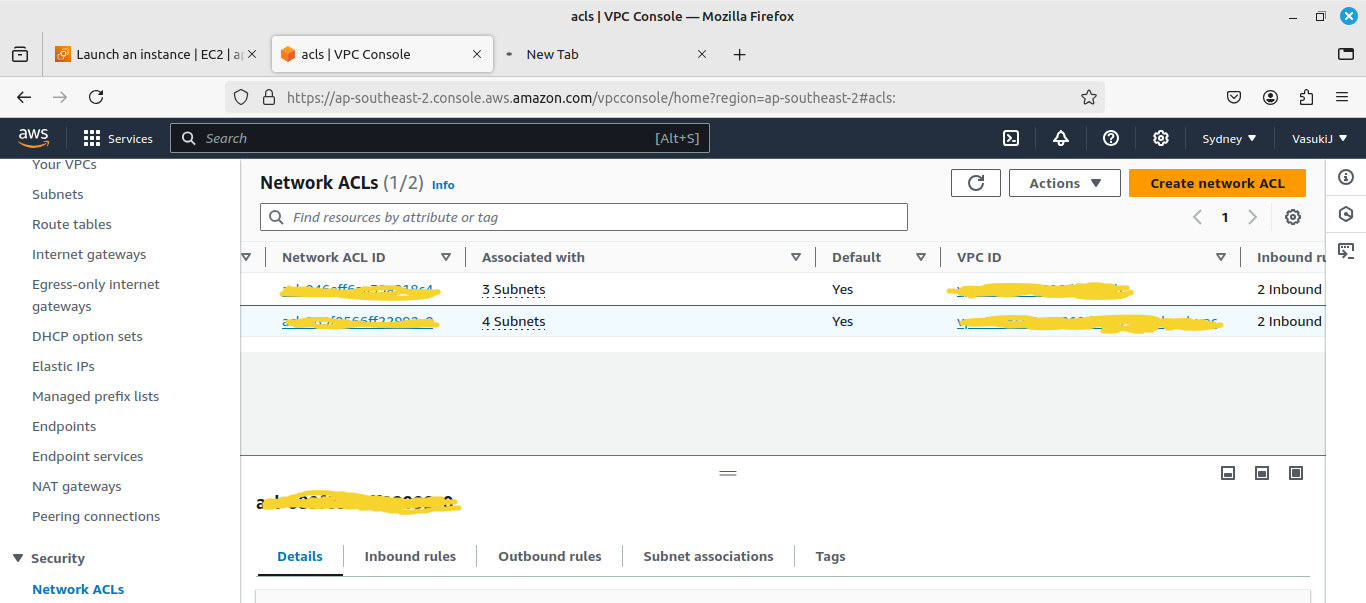
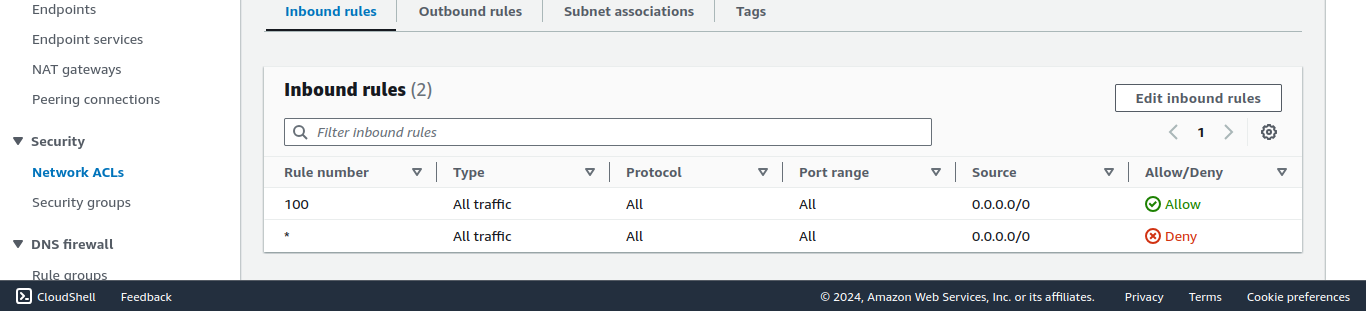
As you see, in NACL in Rule number 100 it was allowing all traffic. So NACL will allow all traffic. So the problem is in the Security group, we want to configure that.
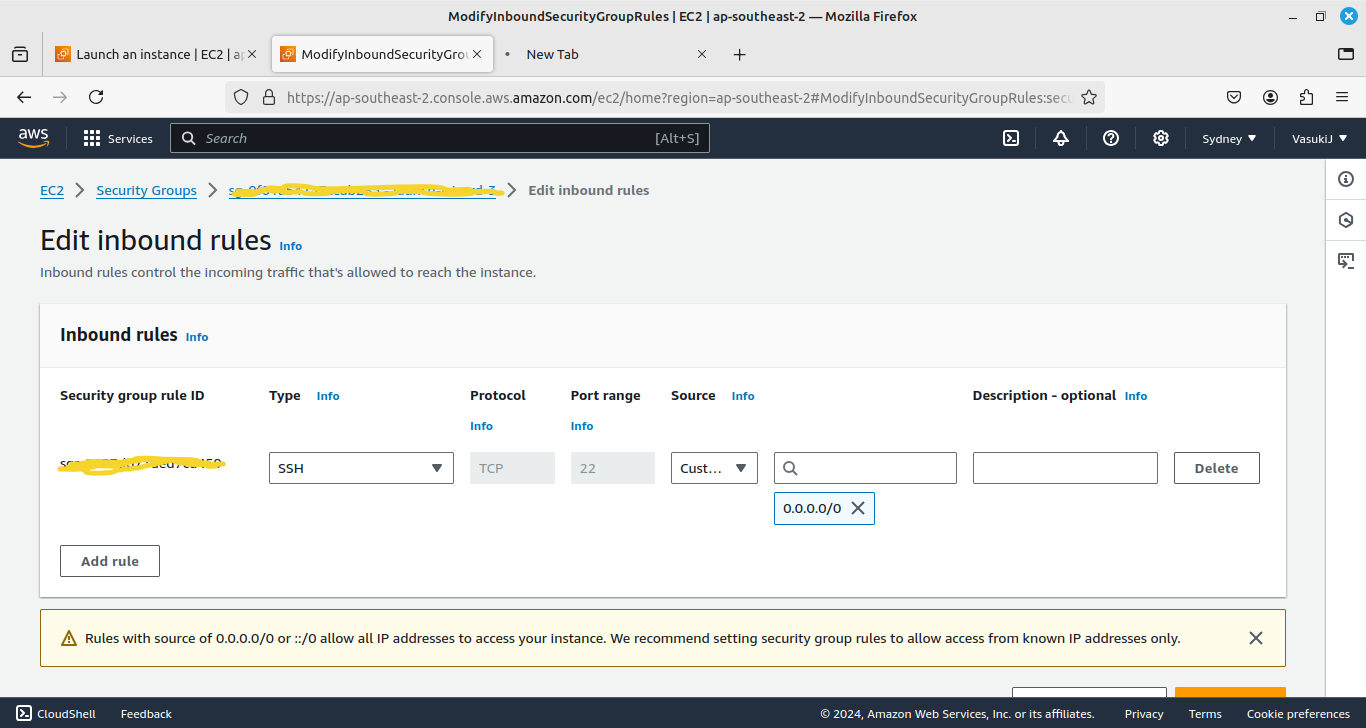
Initially, the Security group only allowed port 22 as an inbound rule. Port 22 is for only accessing the EC2 Instances. We want to add the rule, to allow the Port 8000.
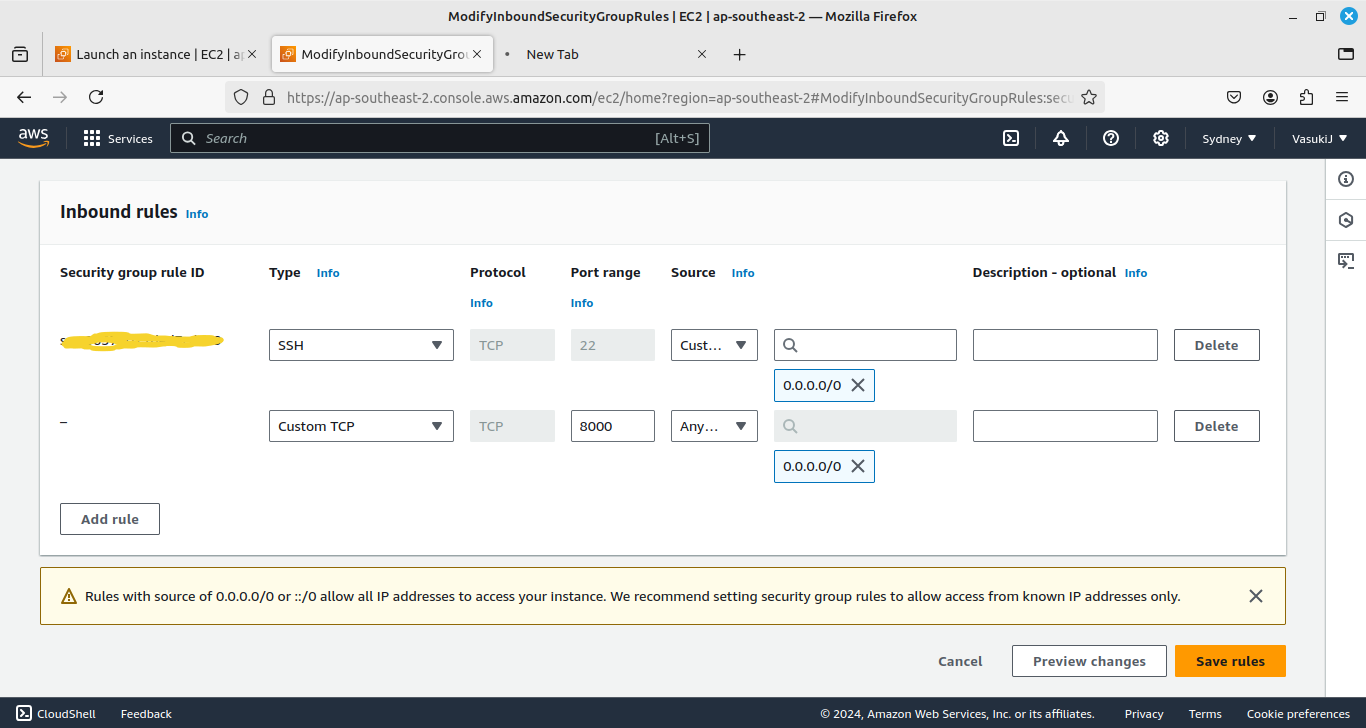
In this choose source as Any IPV4 addressing.
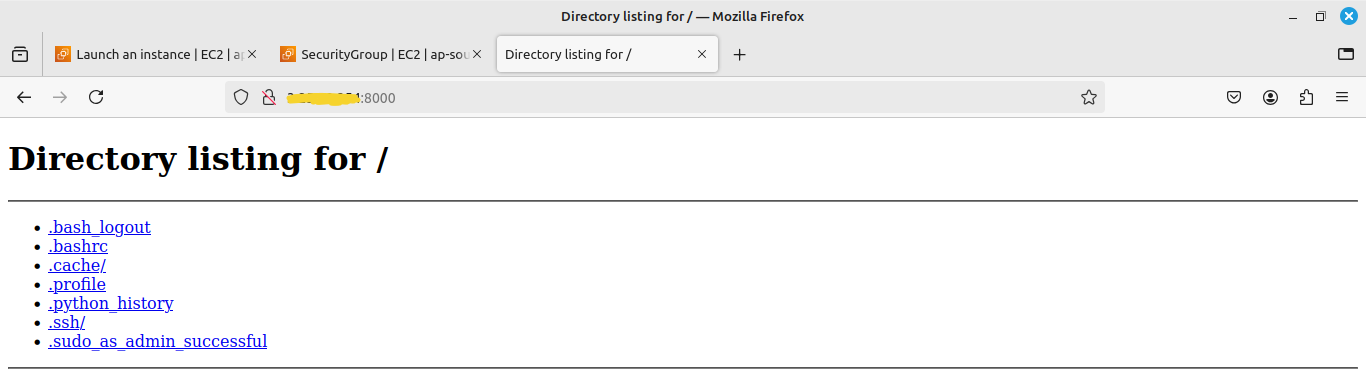
7. Then you will see the output.
Now we block that port in NACL by choosing the Deny option.
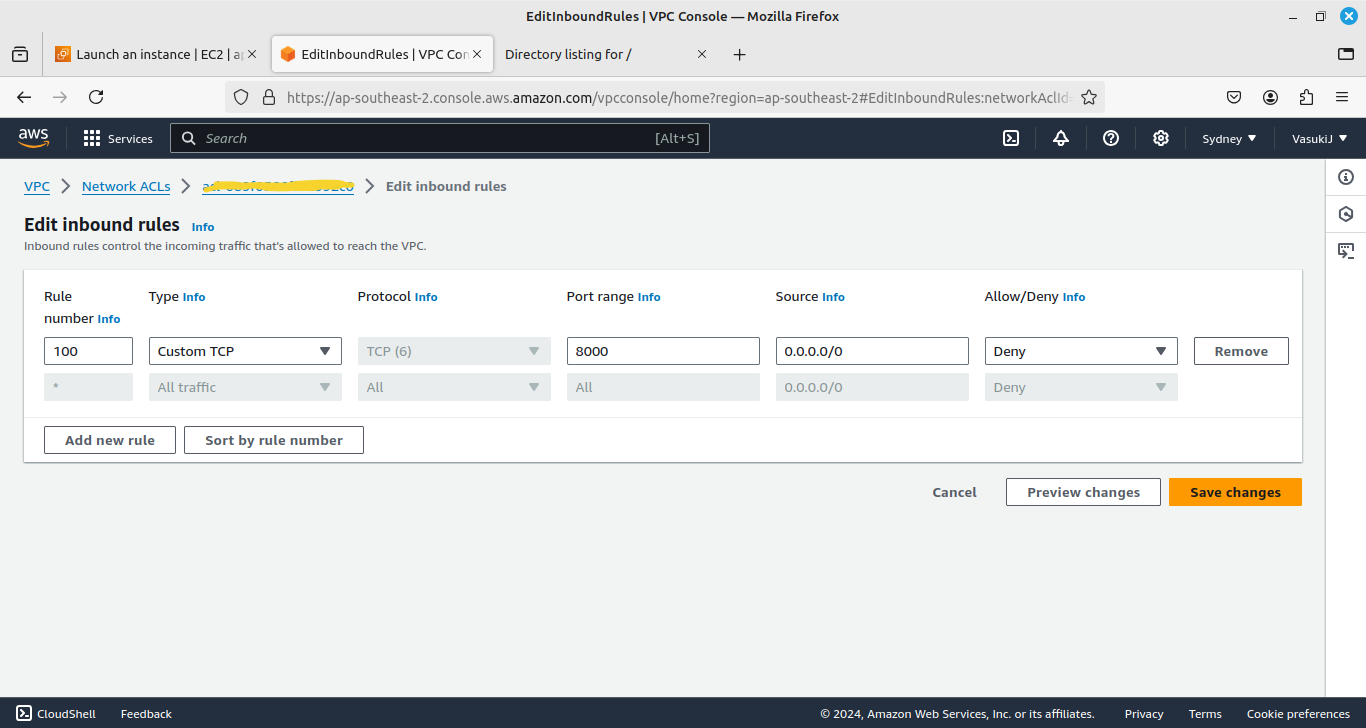
Even now EC2 Instance’s virtual firewall which is the Security group will allow that port means, NACL will not allow that port. The request traffic is not accessible to the application inside the EC2 Instance
In NACL, Priority will go on the lowest order first.
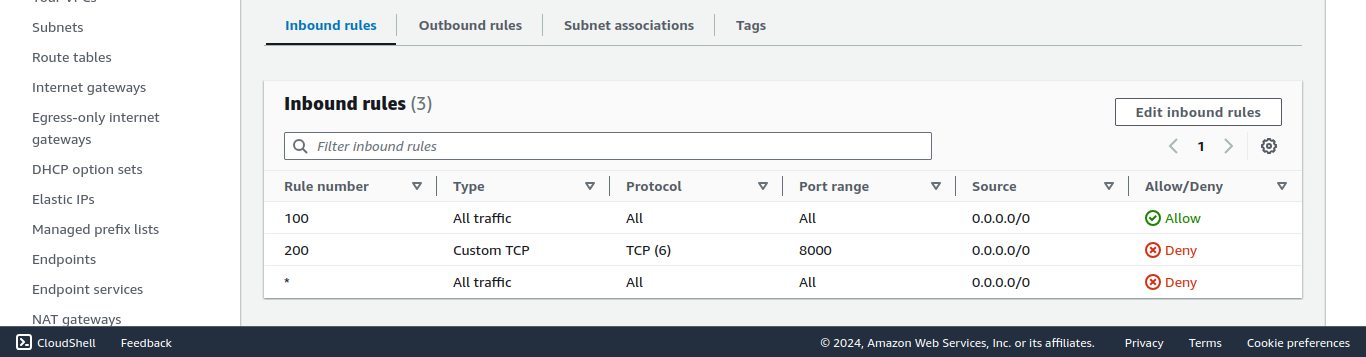
Here, we deny the port in rule number 200. Still, it will allow the traffic. Because It follows the lower number rule as a priority. So rule number 100 will execute which allows all traffic. If the incoming traffic doesn’t match with rule 100 then only rule number 200 will execute then so on priority-wise.
We can see the outcomes reflected in the terminal itself.
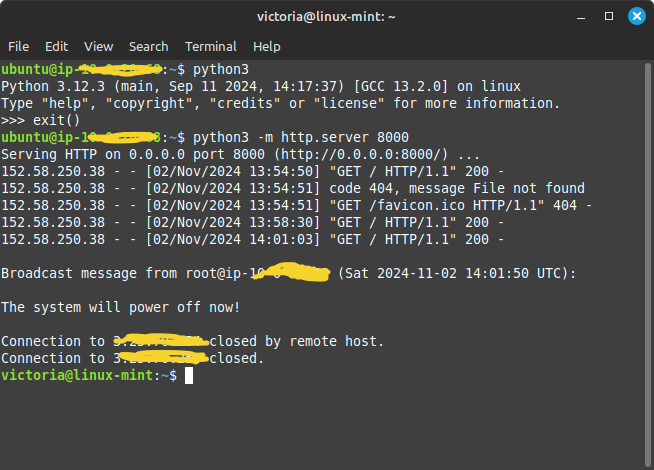
Great, We actually created our own VPC and experimented with the security groups and NACL by allowing and declining the inbound traffic for accessing the simple Python application that runs inside the public subnet.
Thank you!
HAPPY DEVOPS JOURNEY!
Subscribe to my newsletter
Read articles from Vasuki Janarthanan directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Vasuki Janarthanan
Vasuki Janarthanan
While traveling on my DevOps Journey, I am sharing insights gained through experimenting with DevOps and Cloud practices.