Clearing the Confusion: Understanding SSO, SAML, OAuth 2.0, and OpenID Connect
 ritiksharmaaa
ritiksharmaaa
In today’s digital world, where users often have to navigate multiple platforms and applications, understanding authentication mechanisms is essential. In this article, we will demystify the concepts of Single Sign-On (SSO), Security Assertion Markup Language (SAML), OAuth 2.0, and OpenID Connect (OIDC). We will explore their roles, differences, and how they work together to create a seamless user experience.
Prerequisite Knowledge
Before diving into these concepts, it is crucial to have a foundational understanding of authentication methods, including:
JWT (JSON Web Tokens): A compact token format used for representing claims between two parties.
Session Authentication: A method of maintaining user authentication state across requests.
Session Storage and Cookies: Techniques used for storing user sessions on the client side.
Password Hashing: A security measure to store user passwords securely.
If you have questions or need clarification on these topics, feel free to leave a comment on this article. Your feedback can help shape future discussions.
The Problem at Hand
The challenge arises when users are required to log in to multiple platforms to access different services. Each login requires a unique username and password, leading to a significant overhead. Users often struggle to remember numerous passwords, leading to frustration and inefficiencies. This challenge gave rise to the concept of Single Sign-On (SSO), which allows users to log in once and gain access to multiple applications seamlessly.
What is Single Sign-On (SSO)?
SSO is an authentication process that enables users to access multiple applications with a single set of credentials. The name itself—"Single Sign-On"—indicates that users only need to sign in once to gain access to various websites or services. This not only simplifies the user experience but also enhances security by reducing the number of passwords users need to manage.
Evolution of Authentication Methods
Over the years, different methods for implementing SSO have emerged, with three primary standards widely used in the industry:
SAML (Security Assertion Markup Language) - Introduced in 2002.
OAuth 2.0 - Established in 2006.
OpenID Connect (OIDC) - Launched in 2014.
These technologies have evolved to meet the growing demands of web applications, addressing issues related to security, usability, and interoperability.
Identifying Business Needs
In a business context, the initial problem is often identified when multiple employees require access to various sites, each with specific roles and permissions. For instance, if an employee is authorized to access two or more sites with specific roles (e.g., read-only access), the company faces a challenge in managing authentication across these platforms. Traditionally, each site required separate authentication systems, creating overhead for role management and user authentication.
A Practical Example
Let’s consider a hypothetical scenario where a company operates a blogging site that is a subsidiary of a larger SaaS-based platform. The main company must manage users and their roles across both the main SaaS platform and the blogging site. For example, if offensive posts are published on the blogging site, they must be addressed to mitigate potential legal issues. This requires a central administration to monitor posts and assign appropriate roles to employees tasked with managing content.
In this setup, employees need to log in to the blogging site as normal users and then again as centralized administrators to have their roles assigned. This dual login process is inefficient and cumbersome.
Implementing SAML for Streamlined Authentication
To alleviate these challenges, we can implement SAML for seamless authentication across both platforms. Here’s how the process works:

User Accounts and Roles: Employees already have accounts on the main SaaS platform with defined roles. When a new site is introduced, they are still required to log in and have roles assigned by centralized administration.
SSO Login Button: To streamline this process, we introduce an "SSO Login" button on the blogging site. Instead of logging in through the normal user interface, employees click this button, which redirects them to the main SaaS platform for authentication.
Authentication Flow:
Upon clicking the SSO Login button, the user is redirected to the main site, where they enter their credentials. Since the employee already has an account, the main site authenticates them.
The main site then creates a session for the employee and generates an XML file containing their basic details and roles.
XML File Handling: After successful authentication, the main site sends the XML file back to the blogging site.
here how saml xml look like : -
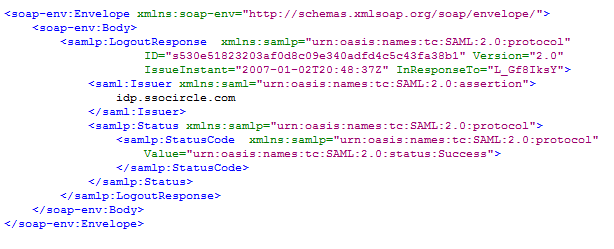
The blogging site validates the XML file to ensure it is legitimate.
If valid, the blogging site saves the employee’s information in its database and creates a new user account if it doesn’t exist already.
Session and JWT Creation: The blogging site then creates a local session or JWT with the employee's information, storing it in cookies for future use.
Managing Multiple Sessions and Expirations
In this process, two separate sessions or JWTs are created:
One for the main SaaS site.
One for the blogging site.
Each session has its own expiration policy. For example, the main site session might expire after 7 days, while the blogging site session expires after 3 days. This setup ensures that employees maintain access to the platforms they need while still adhering to security protocols.
Renewal Process
When an employee logs into the blogging site and their session or JWT has expired, they will receive a prompt indicating they are not logged in. To regain access, they click the SSO Login button, which redirects them to the main site.
Seamless Re-Authentication: If the main site session is still active, the employee is authenticated without needing to enter their username and password again.
XML File Transmission: The main site sends a new XML file with the employee’s username and role back to the blogging site.
Final Validation and Session Creation: The blogging site validates the XML file once more and creates a new local session or JWT, ensuring the employee can continue their work seamlessly.
Implementing SSO Workflow with SAML
Let’s break down the SSO implementation process using SAML in a step-by-step manner:
Step 1: User Login on the Main SaaS Site
Initial Authentication: An employee logs in to the main SaaS application using their credentials. Upon successful authentication, the IdP creates a session.
Role Management: The IdP verifies the employee's roles associated with their account.
Step 2: SSO Login on the Blogging Site
Accessing the Blogging Site: When the employee wants to access the blogging site, they click on the SSO Login button instead of entering their credentials again.
Redirection to IdP: The system redirects the employee to the IdP for authentication.
Step 3: IdP Authentication
Credential Verification: The IdP checks the employee's credentials. If they are valid and the session is still active, the IdP generates a SAML assertion that includes the employee's role.
SAML Assertion Generation: The SAML assertion is packaged with relevant user details and their roles.
Step 4: Redirecting Back to the Blogging Site
Returning to the Blogging Site: The IdP sends the SAML assertion back to the blogging site, usually through the employee’s browser.
Assertion Validation: The blogging site validates the SAML assertion to ensure it originates from a trusted IdP.
Step 5: Session Creation in the Blogging Site
Role Assignment: Upon successful validation, the blogging site extracts the employee's roles from the SAML assertion and assigns them accordingly.
Local Session Creation: The blogging site creates a session or JWT for the employee, allowing them to access the platform based on their assigned roles.
Managing Sessions and Expiration
In this setup, two sessions or JWTs are created:
Main Site Session/JWT: This session may have a longer lifespan (e.g., 7 days).
Blogging Site Session/JWT: This session may be shorter (e.g., 3 days) to ensure security and regular reauthentication.
Handling Expiration Scenarios
Expiration Notification: If the blogging site session expires, the user will be prompted to log in again.
Seamless Renewal: If the main site session is still active, the employee can authenticate without entering their credentials again.
Revalidation of User Role: The IdP generates a new SAML assertion, which the blogging site verifies, allowing for the creation of a new session.
Conclusion
Understanding the nuances of SSO, SAML, OAuth 2.0, and OpenID Connect is crucial in today’s interconnected digital landscape. By implementing SAML and an SSO login process, companies can streamline authentication for their employees, reducing the burden of managing multiple credentials while enhancing security.
The journey from traditional authentication methods to modern SSO solutions illustrates the importance of addressing user experience and security in equal measure. As we continue to navigate the complexities of authentication, it is essential to stay informed about the technologies that shape our digital interactions.
If you have any questions or comments about this article or would like to dive deeper into any of these topics, feel free to leave a comment below. Your insights are valuable and can foster a greater understanding of these essential concepts!
Subscribe to my newsletter
Read articles from ritiksharmaaa directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

ritiksharmaaa
ritiksharmaaa
Hy this is me Ritik sharma . i am software developer