Security Solutions: IDS Fundamentals (TryHackMe)
 Jebitok
Jebitok
In this article, I will write a write-up for IDS Fundamentals that covers What is an IDS, Types of IDS, IDS Examples: Snort, Snort Usage, and a Practical.
Can an intrusion detection system (IDS) prevent the threat after it detects it? Yea/Nay
NayWhich type of IDS is deployed to detect threats throughout the network?
Network Intrusion Detection SystemWhich IDS leverages both signature-based and anomaly-based detection techniques?
Hybrid IDSWhich mode of Snort helps us to log the network traffic in a PCAP file?
Packet Logging ModeWhat is the primary mode of Snort called?
Network Intrusion Detection System ModeWhere is the main directory of Snort that stores its files?
/etc/snortWhich field in the Snort rule indicates the revision number of the rule?
revWhich protocol is defined in the sample rule created in the task?
icmpWhat is the file name that contains custom rules for Snort?
local.rulesWhat is the IP address of the machine that tried to connect to the subject machine using SSH?
10.11.90.211$ cd /etc/snort $ sudo snort -r Intro_to_IDS.pcap -c /etc/snort/snort.conf -A console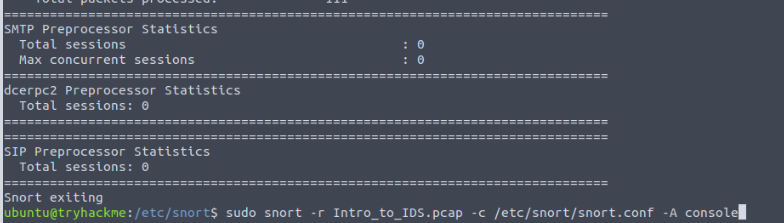
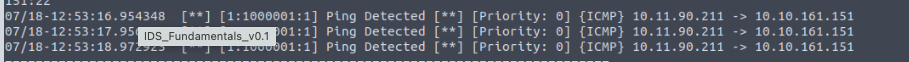
What other rule message besides the SSH message is detected in the PCAP file?
Ping DetectedWhat is the sid of the rule that detects SSH?
1000002
Thank you for reading my article. Please leave any questions or comments on improving my learning journey and the Lab THM challenges.
Subscribe to my newsletter
Read articles from Jebitok directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Jebitok
Jebitok
Software Developer | Learning Cybersecurity | Open for roles * If you're in the early stages of your career in software development (student or still looking for an entry-level role) and in need of mentorship, you can reach out to me.