Unlocking the Power of Linux Commands: Recall and Learn
 Shazia Massey
Shazia Massey
What is Linux:
Linux is an open-source, Unix-like operating system kernel initially developed by Linus Torvalds. It serves as a core component in various environments, including servers, desktops, mobile devices, and embedded systems. Known for its stability, security, and flexibility, Linux has become a foundational element in enterprise IT, powering a significant share of the world’s computing infrastructure across industries.
Start with the basic commands of Linux:
# ls-l
# drwxr-x - - 4 ubuntu ubuntu 4096 Aug 31 10:58 ubuntu
d-directory
rwx -owner (first ubuntu is the owner of the folder or the file)
r-x -group (second ubuntu is the group associated with the folder or the file)
r-x -other user
size- 4096
time-Aug 31 10:58
ubuntu(last ubuntu is the folder or the file)
Hidden folder command (.)
# ls-la
# ls lart
create a file
# touch shazia.txt
# ls
shazia.txt
# mkdir new_folder
shazia.txt new_folder
edit the text file
# vi shazia.txt (safe the file---> # :wq quit the file ---> # :q)
see the content of the file
# cat shazia.txt
moveing file & copying file
# mv shazia.txt new_folder
# cd new_folder
# ls
# shazia.txt
# cd ..
User Management:
** - -sudo /root user
# sudo su
# passwd ubuntu
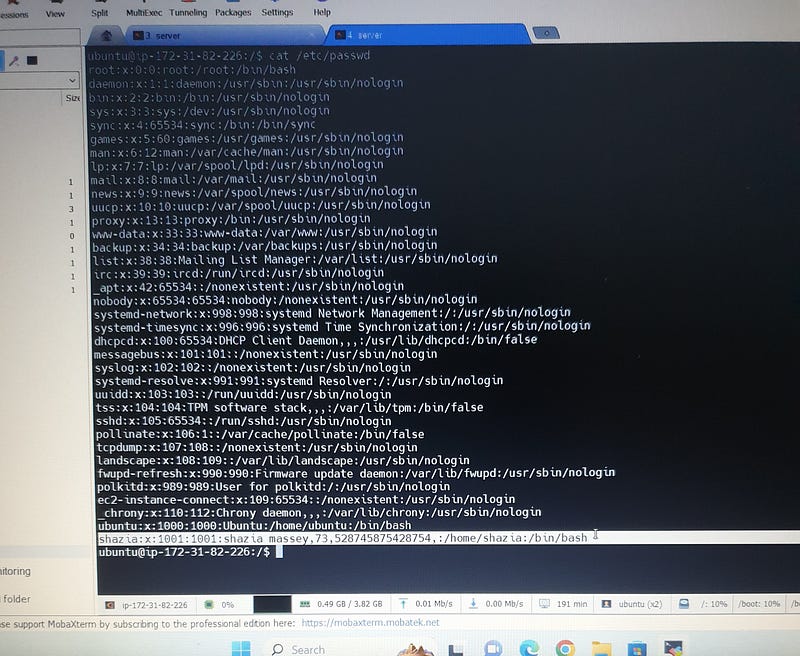
In case you want to see the users
# cd /etc
cat passwd
# ubuntu:x:1000:1000:Ubuntu:/home/ubuntu:/bin/bash
cd ..
switch user
# exit
** - -Normal User
** - -Service Account User
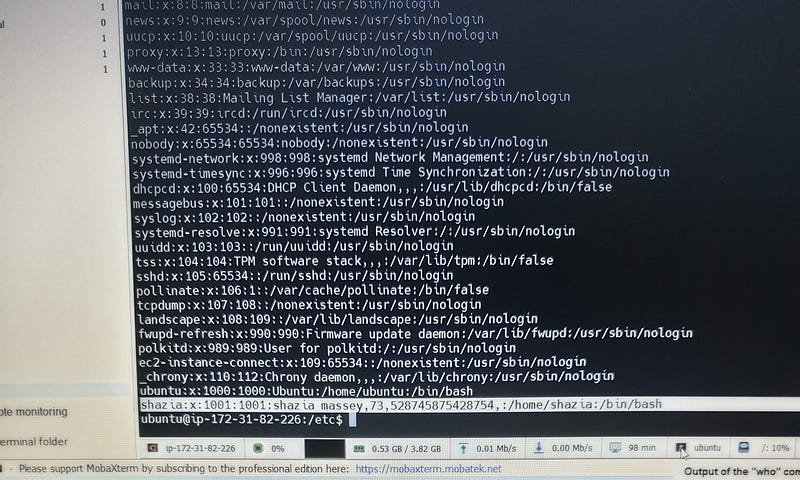
**ubuntu:x:1000:1000:Ubuntu:/home/ubuntu:/bin/bash
The line ubuntu:x:1000:1000:Ubuntu:/home/ubuntu:/bin/bash defines the user ubuntu, with UID 1000, GID 1000, home directory /home/ubuntu, full name Ubuntu, and default shell /bin/bash, with the password stored securely in /etc/shadow.
*adduser / useradd:
useradd is a low-level command for creating users with minimal setup, while adduser is a higher-level, user-friendly script that automates user creation with prompts for additional details.
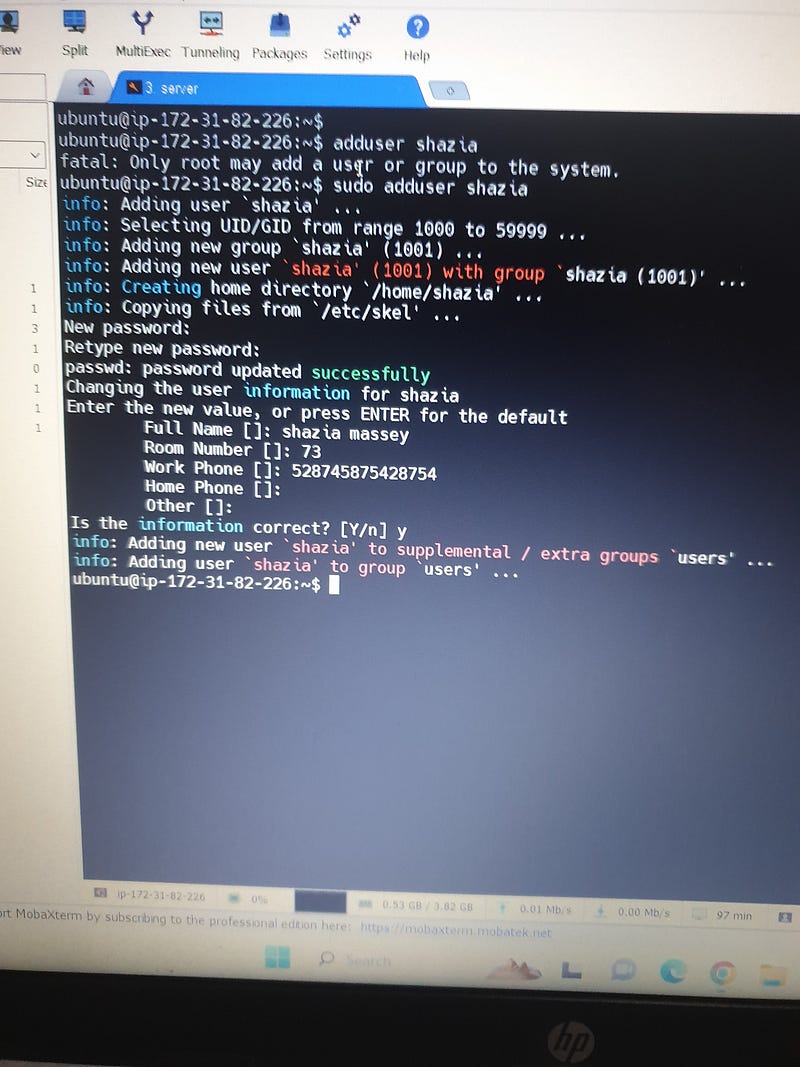
# adduser shazia
# sudo adduser shazia
# cd /etc
# ls
# passwd
# shazia:x:1001:1001:shazia massey,73,528745875428754,:/home/shazia:/bin/bash
*switch the user: ubuntu to shazia:
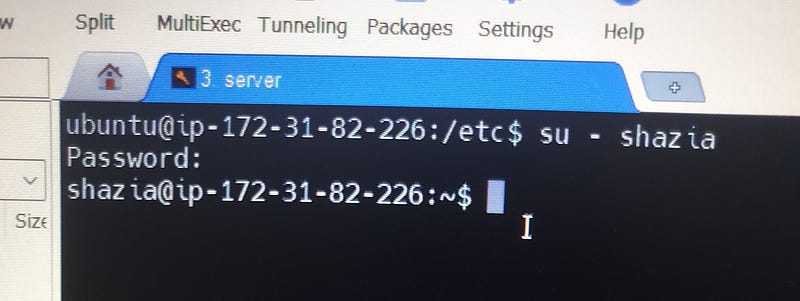
# cd /etc
# su - shazia
password
# exit
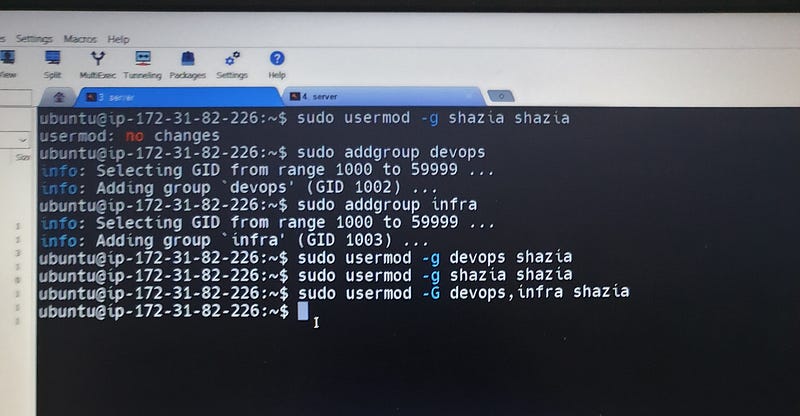
*add user shazia in another group :
# sudo usermod -g shazia shazia
# sudo addgroup devops
(primary (secondary (secondary
group) group) group)
shazia devops infra
| | |
shazia shazia shazia
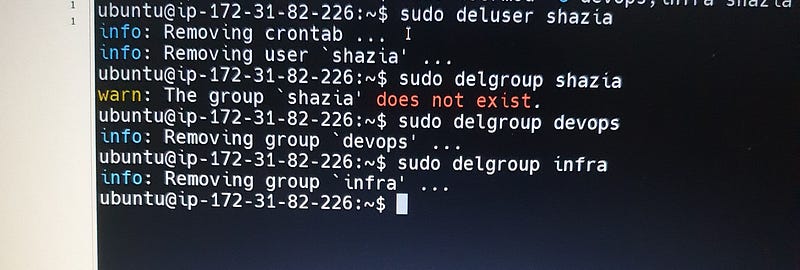
Delete User:
# sudo deluser shazia
# sudo delgroup shazia
# sudo delgroup infra
VI/VIM Editor:
vim a.txt
gg: GO to the begining of the file
G: Go to the end of the file
O: Move to the begining of the current line
$: Move to the end of the current line
w: Move to the beginning of the next word
b: Move back to the beginning of the current word
i: Enter Insert Mode before the cursor
a: Enter Insert Mode after the cursor
I: Enter Insert Mode at the beginning of the line
3G: goto line 3
/searchchpattern: searches the pattern
: %s/old/new/gc: Replace with confirmation
A: Enter Insert Mode at the end of the line
o: Open a new line below the current line
O: Open a new line above the current line
r: Replace the character under the cursor
x: Delete the character under the cursor
d2: delete 2next lines+currentline
dd: Delete the current line
u: Undo the last action
Ctrl + r: Redo the undone action
:w: Save the file
:q: Quit Vim
:wq: Save and quit
:q! Quit without saving changes
Permissions on files and folders:
To modify permissions on files and folders in a Unix-like operating system, you can use the chmod command. This command allows you to set the permissions for different users (owner, group, others) in terms of read, write, and execute access
1. Basic Permissions
There are three types of permissions:
Read (r): Allows viewing the file or listing a directory’s contents.
Write (w): Allows modifying the file or directory contents.
Execute (x): Allows running the file as a program or accessing a directory.
2. Permission Levels
Each file or folder has three levels of users:
Owner (u): The user who owns the file.
Group (g): The group that owns the file.
Others (o): All other users.
3. Numeric Notation
Each permission type is represented by a number:
Read = 4
Write = 2
Execute = 1
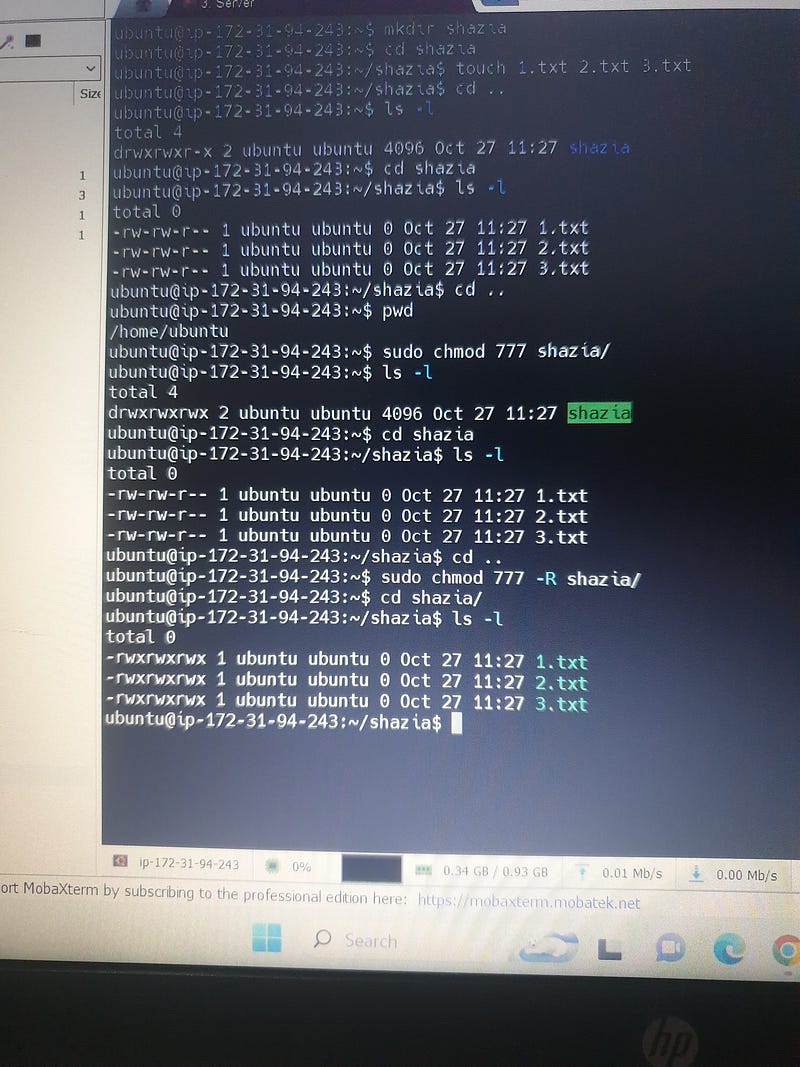
To change permissions on files or directories:
- Setting Permissions with Numeric Notation
chmod [permission] [filename]
# sudo chmod 777 shazia/
2. Changing Directory Permissions Recursively
# Sudo chmod 777 -R shazia/
3. Setting Permissions with Symbolic Notation
. Command Format:
chmod [user]+[permission] [filename]
Examples:
- Grant execute permission to the owner:
# chmod u+x myfile.txt
. Remove write permission from group:
# chmod g-w myfile.txt
. Set read, write, execute for the owner and read-only for others:
# chmod u=rwx,go=r myfile.txt
The rm -rf command is a powerful command in Unix/Linux used to delete files and directories. However, it should be used with caution as it permanently deletes files and directories without confirmation. Here’s a breakdown:
Explanation of rm -rf
rm: Stands for "remove." It’s the command to delete files or directories.-r: Recursive. This option is used to delete directories and all contents within them (subdirectories and files).-f: Force. This option forces deletion without prompting for confirmation, even for write-protected files.
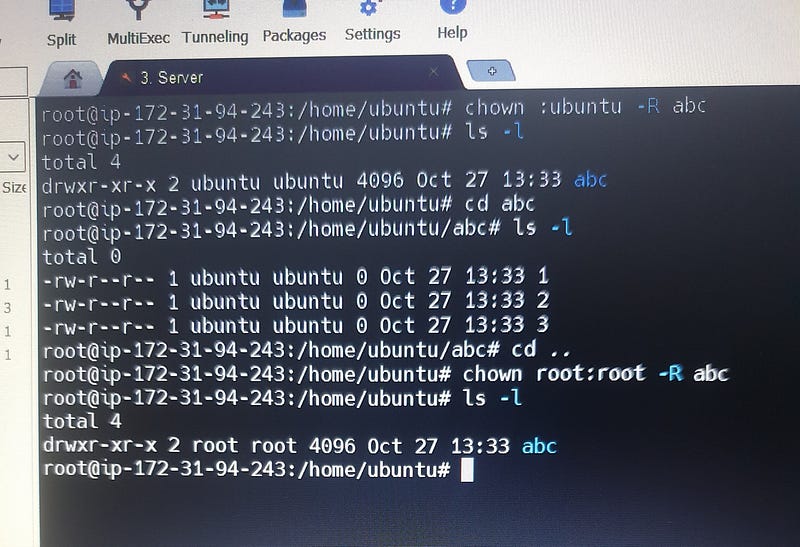
To change the ownership of files and directories in Linux, you can use the chown command. This command allows you to set the owner and/or group for files and directories.
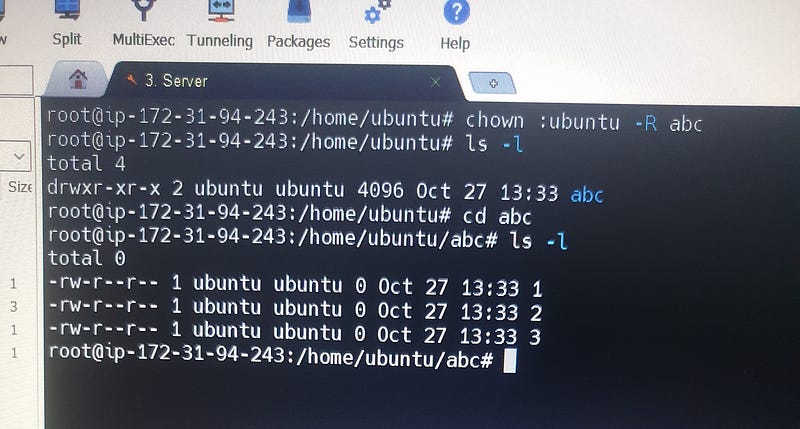
To change both the owner and group of a file or directory at the same time, use the chown command with the following syntax:
# chown newowner:newgroup filename
A package manager is a tool that automates the process of installing, updating, configuring, and removing software packages on an operating system. Package managers handle dependencies, versioning, and repositories to make it easier to manage software efficiently.
Both curl and wget are command-line tools used for downloading content from the internet, but they have different strengths and purposes. In summary, use curl for more complex data transfers and API interactions, and choose wget for simple, robust file downloads and recursive directory fetching.
**Networking Commands:
1. ifconfig: Displays or configures network interfaces.
# ifconfig
2. ip: A modern alternative to ifconfig for managing network interfaces and routing.
ip addr show # Display IP addresses
ip link show # Show network interfaces
ip route show # Display routing table
3.iwconfig: For configuring wireless network interfaces (e.g., Wi-Fi).
# iwconfig
**Connection Testing:
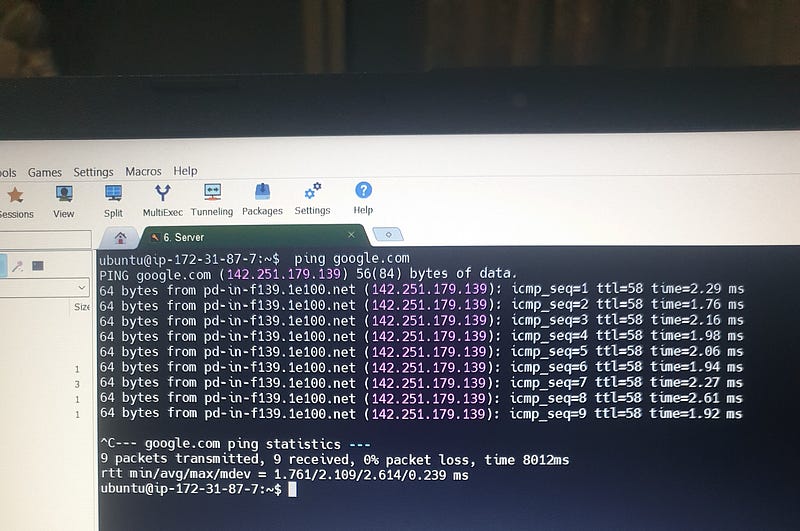
. ping: Sends ICMP packets to a host to test connectivity and measure round-trip time.
# ping google.com
. traceroute: Shows the path packets take to reach a network host.
# traceroute google.com
**Network Monitoring:
. netstat: Shows network connections, routing tables, and more.
# netstat -tuln # Show active listening ports
# netstat -i # Display network interface statistics
**DNS and Domain Name Resolution:
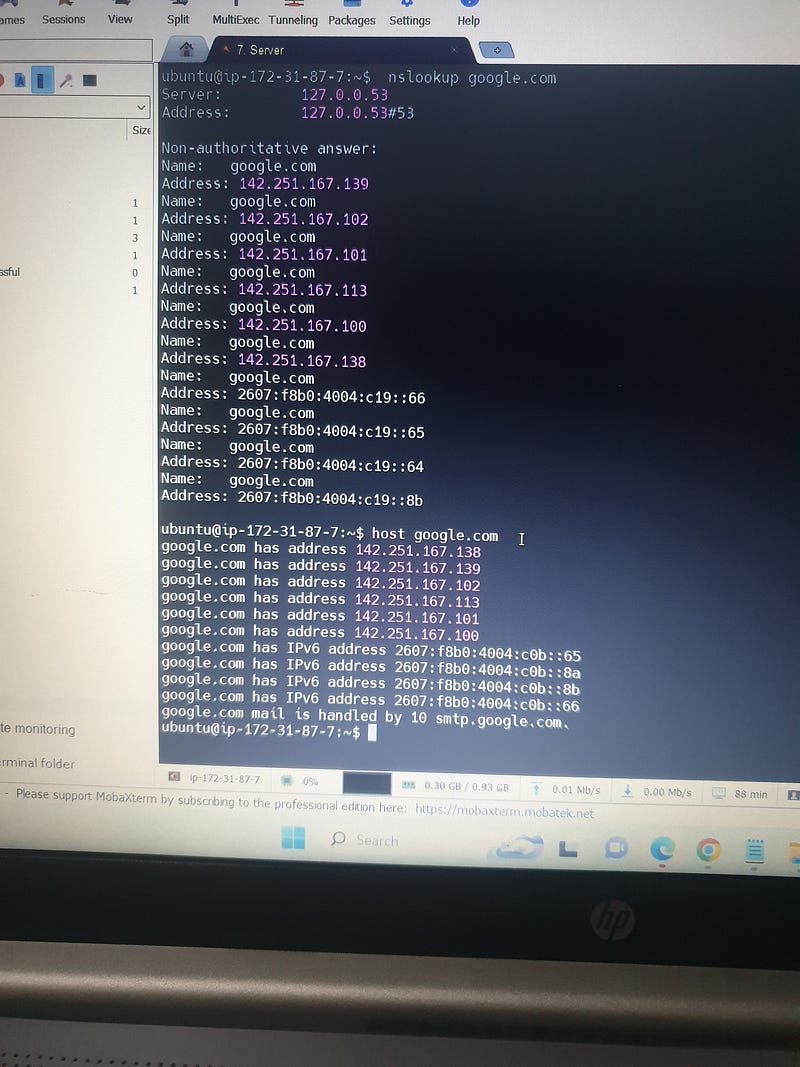
nslookup: Queries DNS to retrieve domain name or IP address information
# nslookup example.com
dig: More advanced DNS lookup tool, showing detailed DNS information
# dig example.com
host: Simple tool to find IP addresses associated with domain names
# host example.com
Mastering Linux commands boosts productivity and deepens system understanding, transforming how we engage with technology. I hope this blog serves as a valuable resource for refreshing your knowledge and sharpening your skills.
Subscribe to my newsletter
Read articles from Shazia Massey directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by
