Defensive Security Tooling: CAPA: The Basics (TryHackMe)
 Jebitok
Jebitok
In this article, I will write a write-up for CAPA: The Basics that covers Tool Overview: How CAPA Works, Dissecting CAPA Results Part 1: General Information,, MITRE and MAEC, Dissecting CAPA Results Part 2: Malware Behavior Catalogue, Dissecting CAPA Results Part 3: Namespaces, Dissecting CAPA Results Part 4: Capability and More Information, More fun!.
What command-line option would you use if you need to check what other parameters you can use with the tool? Use the shortest format.
-hWhat command-line options are used to find detailed information on the malware's capabilities? Use the shortest format.
-vWhat command-line options do you use to find very verbose information about the malware's capabilities? Use the shortest format.
-vvWhat PowerShell command will you use to read the content of a file?
Get-ContentWhat is the sha256 of cryptbot.bin?
ae7bc6b6f6ecb206a7b957e4bb86e0d11845c5b2d9f7a00a482bef63b567ce4c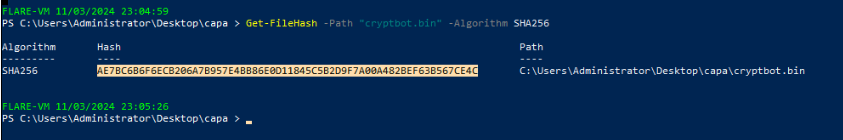
What is the Technique Identifier of Obfuscated Files or Information?
T1027What is the Sub-Technique Identifier of Obfuscated Files or Information::Indicator Removal from Tools?
T1027.005When CAPA tags a file with this MAEC value, it indicates that it demonstrates behaviour similar to, but not limited to, Activating persistence mechanisms?
launcherWhen CAPA tags a file with this MAEC value, it indicates that the file demonstrates behaviour similar to, but not limited to, Fetching additional payloads or resources from the internet?
DownloaderWhat serves as a catalogue of malware objectives and behaviours?
Malware Behavior CatalogueWhich field is based on ATT&CK tactics in the context of malware behaviour?
ObjectiveWhat is the Identifier of "Create Process" micro-behavior?
C0017What is the behaviour with an Identifier of B0009?
Virtual Machine DetectionMalware can be used to obfuscate data using base64 and XOR. What is the related micro-behavior for this?
Encode DataWhich micro-behavior refers to "Malware is capable of initiating HTTP communications"?
HTTP CommunicationWhich top-level Namespace contains a set of rules specifically designed to detect behaviours, including obfuscation, packing, and anti-debugging techniques exhibited by malware to evade analysis?
anti-analysisWhich namespace contains rules to detect virtual machine (VM) environments? Note that this is not the TLN or Top-Level Namespace.
anti-vm/vm-detectionWhich Top-Level Namespace contains rules related to behaviours associated with maintaining access or persistence within a compromised system? This namespace is focused on understanding how malware can establish and maintain a presence within a compromised environment, allowing it to persist and carry out malicious activities over an extended period.
persistenceWhich namespace addresses techniques such as String Encryption, Code Obfuscation, Packing, and Anti-Debugging Tricks, which conceal or obscure the true purpose of the code?
obfuscationWhich Top-Level Namespace Is a staging ground for rules that are not quite polished?
NurseryWhat rule yaml file was matched if the Capability or rule name is check HTTP status code?
check-http-status-code.ymlWhat is the name of the Capability if the rule YAML file is
reference-anti-vm-strings.yml?reference anti-VM stringsWhich TLN or Top-Level Namespace includes the Capability or rule name run PowerShell expression?
load-codeCheck the conditions inside the
check-for-windows-sandbox-via-registry.ymlrule file from this link. What is the value of the API that ends inExis it looking for?RegOpenKeyEx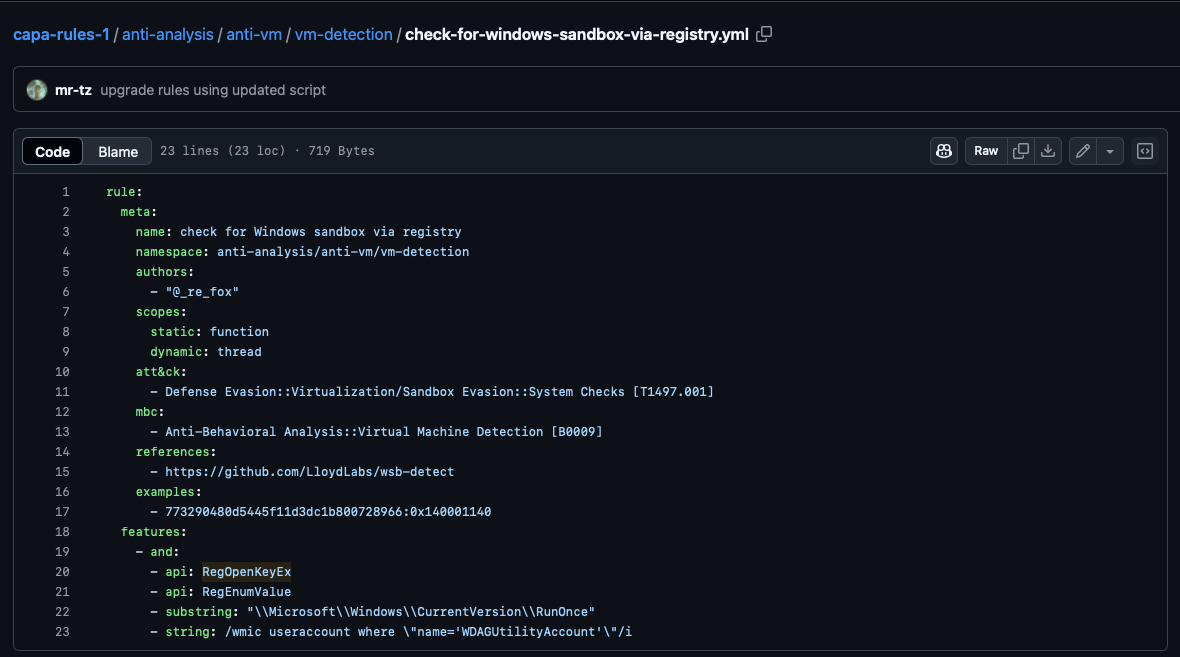
Which parameter allows you to output the result of CAPA into a .json file?
-jWhat tool allows you to interactively explore CAPA results in your web browser?
CAPA Web ExplorerWhich feature of this CAPA Web Explorer allows you to filter options or results?
Global Search Box
Thank you for reading my article. Please leave any questions or comments on improving my learning journey and the Lab THM challenges.
Subscribe to my newsletter
Read articles from Jebitok directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Jebitok
Jebitok
Software Developer | Learning Cybersecurity | Open for roles * If you're in the early stages of your career in software development (student or still looking for an entry-level role) and in need of mentorship, you can reach out to me.