Beginner Cybersecurity Tools: A Practical Guide to Wireshark, Nmap, and Metasploit
 Aboelhamd Abdellatif
Aboelhamd Abdellatif
Introduction
In the world of cybersecurity, tools like Wireshark, Nmap, and Metasploit are essential starting points for anyone looking to understand networks and digital security. Whether you're a novice eager to explore network analysis, scanning, or penetration testing, these tools open the door to fundamental concepts in cybersecurity. This guide offers an introduction to each tool, practical scenarios for use, and tips to maximize their value in safe lab environments.
Wireshark: The Network Analyzer
Wireshark is a widely used open-source packet analyzer that allows users to capture and inspect data across networks in real-time. It’s an invaluable tool for network administrators, cybersecurity professionals, and learners, offering insights into network traffic and protocols.
Practical Scenario 1: Monitoring HTTP Traffic
Starting a Packet Capture: Launch Wireshark and select the network interface to begin capturing traffic. Filter the traffic by entering
httpinto the display filter bar to focus solely on HTTP packets.Inspecting a Packet: Once packets are captured, you can select any HTTP packet to view detailed information. Wireshark presents packet data in three main panels:
Packet List: Displays each captured packet.
Packet Details: Shows breakdowns of individual packet layers.
Packet Bytes: Displays raw packet data.
Applying Filters: Filtering options, like specifying IP addresses or port numbers, narrow down traffic types.
Advanced Scenario: Diagnosing Network Latency Imagine a network experiencing latency issues. You can filter by protocols such as TCP and analyze TCP handshake delays to pinpoint problem areas.
Example of Filtering on the TCP protocol:
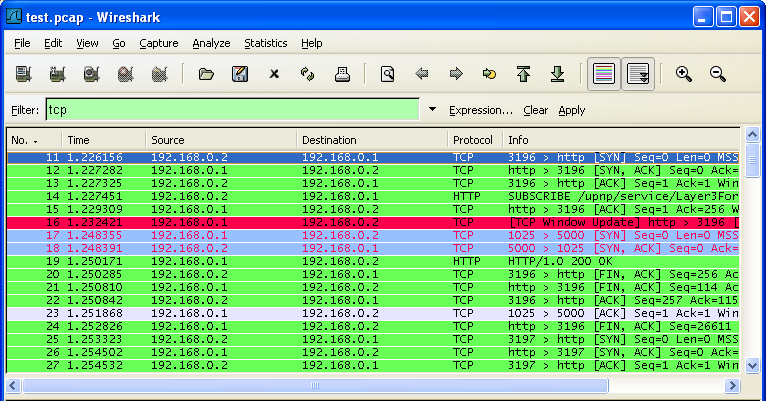
Nmap: The Network Mapper
Nmap, short for Network Mapper, is a powerful open-source scanning tool that identifies active devices and services on a network. It’s widely used for network inventory, managing service upgrade schedules, and monitoring host or service uptime.
Practical Scenario 2: Scanning a Local Network for Open Ports
Basic Host Discovery: Use
nmap -sP 192.168.1.0/24to identify active hosts in a local network.Port Scanning: To identify open ports on a specific device, try
nmap -sT [IP Address]. This reveals open ports, letting users understand which services are accessible.Service Detection: The
-sVoption allows for version detection of the running services, offering insights into potential vulnerabilities.
Advanced Scenario: Service Version Scanning for Vulnerability Assessment With version detection enabled, Nmap helps you evaluate potential vulnerabilities by determining service versions, a valuable first step in assessing risks on a network.
Nmap Cheat Sheet:
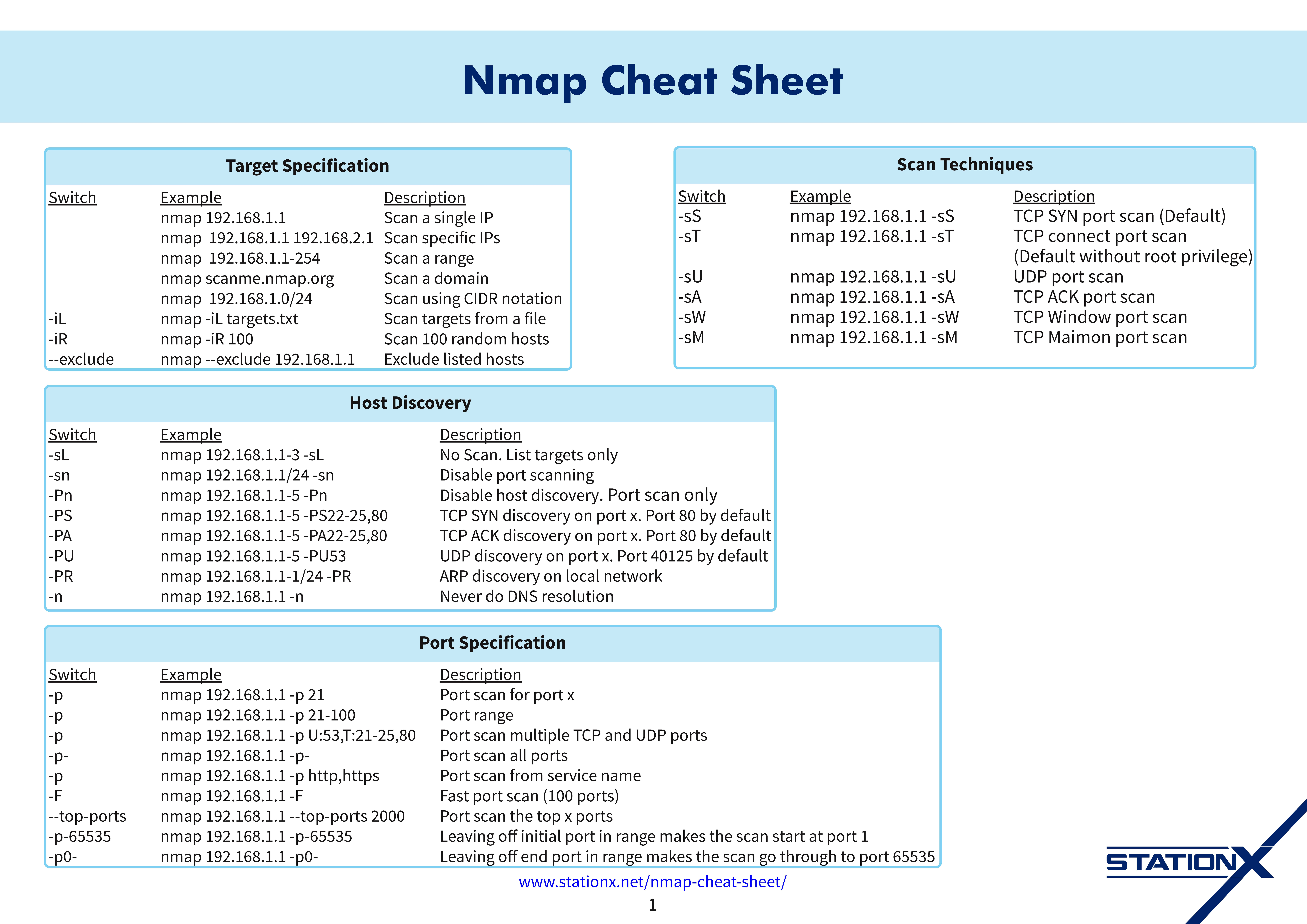
Metasploit: The Penetration Testing Framework
Metasploit is an advanced tool used for penetration testing and simulating attacks. Developed by Rapid7, this framework includes hundreds of exploits for various platforms, making it highly versatile for security professionals.
Practical Scenario 3: Exploiting a Vulnerability in a Controlled Lab Environment
Choosing a Target: In a secure, isolated lab environment, launch Metasploit and connect to the Metasploit console.
Selecting an Exploit and Payload: After setting up a vulnerable target, select an exploit with
use exploit/[path]. Configure options withsetcommands for target IP, payload, and more.Executing the Attack: Run
exploitto deploy the payload and access the target, assuming the vulnerability is unpatched.Post-Exploitation: Demonstrate access to certain files or processes to showcase the implications of successful exploitation.
Advanced Scenario: Metasploit for Simulated Penetration Testing Professionals use Metasploit to simulate real-world attack scenarios, providing critical insights into the security posture of their networks.
Metasploit help options:
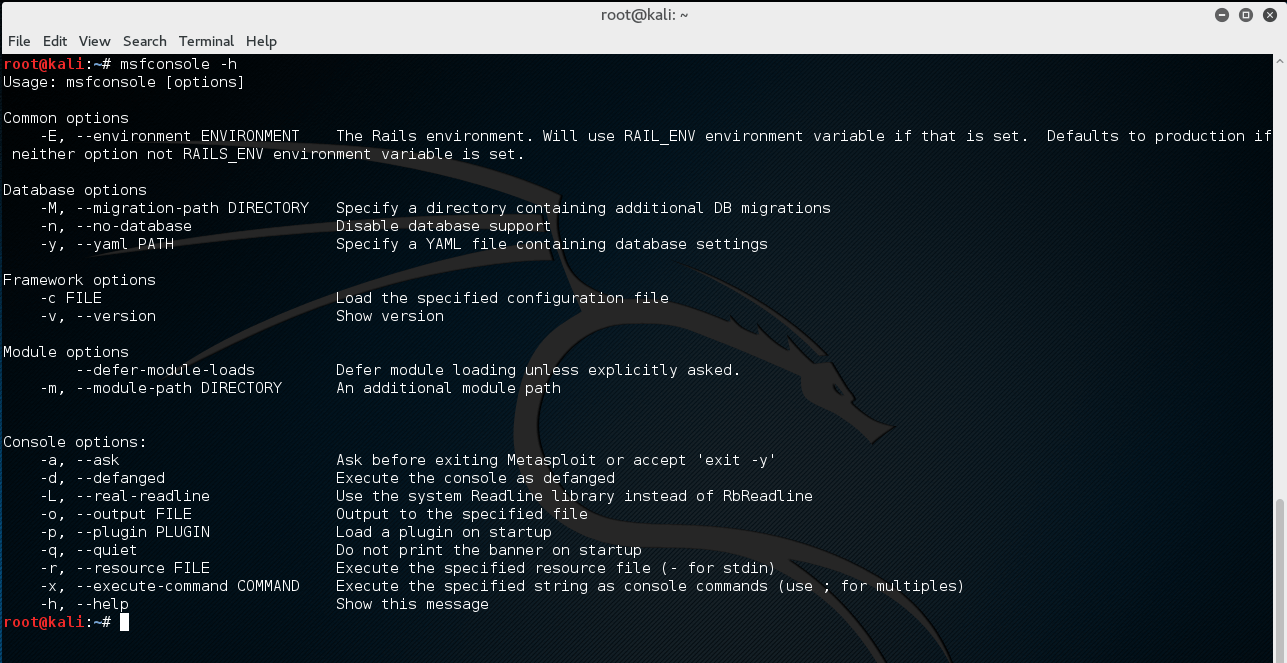
Conclusion
Learning Wireshark, Nmap, and Metasploit equips cybersecurity beginners with practical skills to analyze, scan, and assess network security. With consistent practice, these tools open doors to more advanced cybersecurity practices and offer foundational knowledge essential for both defensive and offensive security.
Subscribe to my newsletter
Read articles from Aboelhamd Abdellatif directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Aboelhamd Abdellatif
Aboelhamd Abdellatif
Cybersecurity Infrastructure Specialist | Aspiring Penetration Tester With over 5 years of experience in designing and securing ICT infrastructures, I specialize in implementing systems that protect critical assets and ensure operational efficiency. My work focuses on enhancing security measures, ensuring compliance, and safeguarding environments against evolving cyber threats. Currently, I'm expanding my skill set in offensive security, having completed foundational courses on TryHackMe, including the Introduction to Cyber Security, Pre-Security, and Cyber Security Complete Beginner paths. Additionally, I hold hands-on certifications in BlackArch Linux, Netcat, and C++ for Pentesters from EC-Council, and I’m actively preparing for OSCP and CEH certifications to deepen my expertise in penetration testing and vulnerability assessment.