How to Create an IAM User A Guide to Identity and Access Management
 Aditya Gadhave
Aditya Gadhave
Identity and Access Management (IAM) in Amazon Web Services (AWS)
IAM stands for Identity Access Management.
IAM allows you to manage users and their level of access to the aws console.
It is used to set users, permissions and roles. It allows you to grant access to the different parts of the aws platform.
AWS Identity and Access Management is a web service that enables Amazon Web Services (AWS) customers to manage users and user permissions in AWS.
With IAM, Organizations can centrally manage users, security credentials such as access keys, and permissions that control which AWS resources users can access.
Without IAM, Organizations with multiple users must either create multiple user accounts, each with its own billing and subscriptions to AWS products or share an account with a single security credential.
Without IAM, you also don't have control about the tasks that the users can do.
IAM enables the organization to create multiple users, each with its own security credentials, controlled and billed to a single aws account.
IAM allows the user to do only what they need to do as a part of the user's job.
How IAM Works?
IAM verifies that a user or service has the necessary authorization to access a particular service in the AWS cloud. We can also use IAM to grant the right level of access to specific users, groups, or services. For example, we can use IAM to enable an EC2 instance to access S3 buckets by requesting fine-grained permissions.
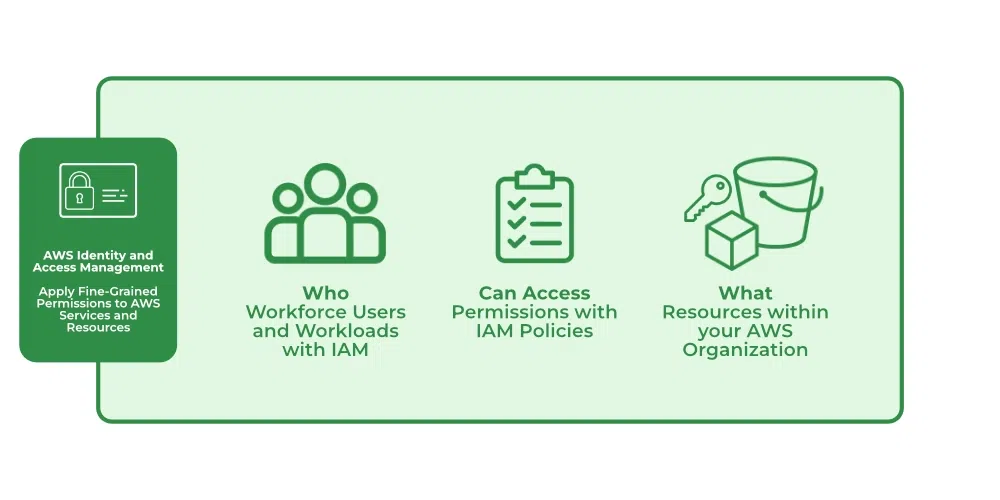
What Does IAM Do?
With the help of IAM, we perform the following
IAM Identities
IAM Identities assists us in controlling which users can access which services and resources in the AWS Console and also we can assign policies to the users, groups, and roles. The IAM Identities can be created by using the Root user
IAM Identities Classified As
IAM Users
IAM Groups
IAM Roles
AWS Account Root User
When you first create an AWS account, you create an account as a root user identity which is used to sign in to AWS.
You can sign to the AWS Management Console by entering your email address and password. The combination of email address and password is known as root user credentials.
When you sign in to AWS account as a root user, you have unrestricted access to all the resources in AWS account.
The Root user can also access the billing information as well as can change the password also.
IAM Users
We can utilize IAM users to access the AWS Console and their administrative permissions differ from those of the Root user and if we can keep track of their login information.
Example
With the aid of IAM users, we can accomplish our goal of giving a specific person access to every service available in the Amazon dashboard with only a limited set of permissions, such as read-only access. Let’s say user-1 is a user that I want to have read-only access to the EC2 instance and no additional permissions, such as create, delete, or update. By creating an IAM user and attaching user-1 to that IAM user, we may allow the user access to the EC2 instance with the required permissions.
IAM Groups
A group is a collection of users, and a single person can be a member of several groups. With the aid of groups, we can manage permissions for many users quickly and efficiently.
Example
Consider two users named user-1 and user-2. If we want to grant user-1 specific permissions, such as the ability to delete, create, and update the auto-calling group only, and if we want to grant user-2 all the necessary permissions to maintain the auto-scaling group as well as the ability to maintain EC2, we can create groups and add this user to them. If a new user is added, we can add that user to the required group with the necessary permissions.
What is a Role?
A role is a set of permissions that grant access to actions and resources in AWS. These permissions are attached to the role, not to an IAM User or a group.
An IAM User can use a role in the same AWS account or a different account.
An IAM User is similar to an IAM User; role is also an AWS identity with permission policies that determine what the identity can and cannot do in AWS.
A role is not uniquely associated with a single person; it can be used by anyone who needs it.
A role does not have long term security credential, i.e., password or security key. Instead, if the user uses a role, temporarily security credentials are created and provided to the user.
You can use the roles to delegate access to users, applications or services that generally do not have access to your AWS resources.
Situations in which "IAM Roles" can be used:
Sometimes you want to grant the users to access the AWS resources in your AWS account.
Sometimes you want to grant the users to access the AWS resources in another AWS account.
It also allows the mobile app to access the AWS resources, but not want to store the keys in the app.
It can be used to grant access to the AWS resources which have identities outside of AWS.
It can also be used to grant access to the AWS resources to the third party so that they can perform an audit on AWS resources.
Example
Consider Amazon EKS. In order to maintain an autoscaling group, AWS eks needs access to EC2 instances. Since we can’t attach policies directly to the eks in this situation, we must build a role and then attach the necessary policies to that specific role and attach that particular role to EKS.
IAM Policies
IAM Policies can manage access for AWS by attaching them to the IAM Identities or resources IAM policies defines permissions of AWS identities and AWS resources when a user or any resource makes a request to AWS will validate these policies and confirms whether the request to be allowed or to be denied. AWS policies are stored in the form of Jason format the number of policies to be attached to particular IAM identities depends upon no.of permissions required for one IAM identity. IAM identity can have multiple policies attached to them.
IAM Features
Shared Access to your Account: A team working on a project can easily share resources with the help of the shared access feature.
Free of cost: IAM feature of the Aws account is free to use & charges are added only when you access other Amazon web services using IAM users.
Have Centralized control over your Aws account: Any new creation of users, groups, or any form of cancellation that takes place in the Aws account is controlled by you, and you have control over what & how data can be accessed by the user.
Grant permission to the user: As the root account holds administrative rights, the user will be granted permission to access certain services by IAM.
Multifactor Authentication: Additional layer of security is implemented on your account by a third party, a six-digit number that you have to put along with your password when you log into your accounts.
Creating a User
To create an IAM user, please follow the steps below:
Step 1 :Log in to your AWS Management Console.

Step 2: Navigate to the IAM service.
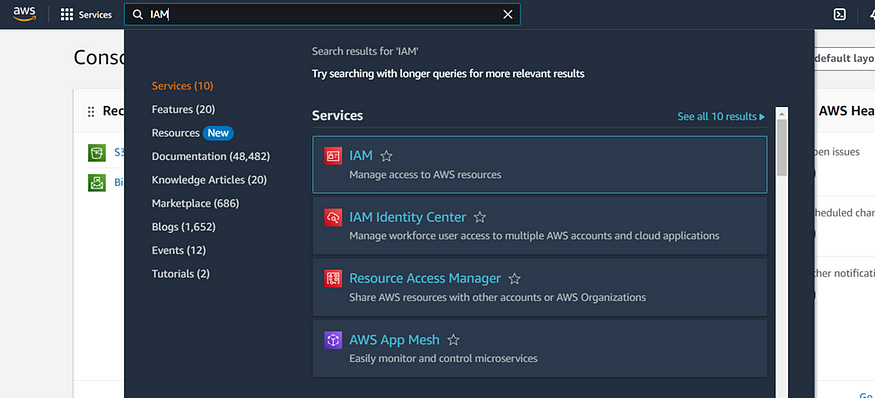
Step 3 :In the IAM dashboard, select “Users” from the left-hand menu.

Step 4 :Click the “Create user” button.

Step 6 :Enter a username for the new IAM user.

In this process, if you wish to create a user with access to the AWS Management Console, you must enable the checkbox that provides access to the console. However, if you do not need access to the console and only require a programmatic user, you can leave the checkbox disabled and proceed with the other steps.
Set permissions for the user by adding them to one or more IAM groups or attaching policies directly.
Here, I’ll attach a policy directly as follows. When you choose to attach a policy directly, you’ll see a list of predefined policies. You can select one or more policies based on your specific requirements. In this example, I will attach the “Access to S3” policy, which grants the user access to AWS S3 features.

If you’re not satisfied with the predefined policies or they don’t match your specific requirements, you have the option to create a custom policy by clicking the “Create policy” button. This way, you can define a policy that aligns with your exact needs.
Review the user’s details and permissions, then click “Create user.”
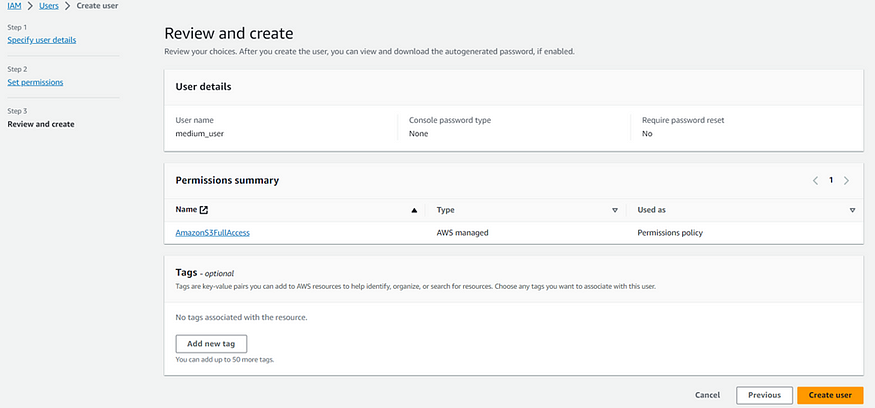
These steps will create an IAM user with the specified access and permissions.
Advantages of IAM Roles
Temporary Access and Enhanced Security:
IAM roles allow for temporary security credentials, which improve security by reducing the risk of long-term, potentially exposed credentials.
When a user or service assumes a role, they get temporary permissions, limiting the potential damage if credentials are compromised.
Granular Permission Control:
- Roles can have custom permissions policies attached, ensuring that only the minimum required permissions are granted, following the principle of least privilege.
Cross-Account Access:
- IAM roles can provide secure access to resources across different AWS accounts without sharing access keys, making it easier to manage multi-account setups.
Service-to-Service Communication:
- Roles are useful for allowing AWS services (like EC2, Lambda, or RDS) to communicate with other AWS services without embedding access keys in the code, improving security.
Easy Credential Rotation:
- Since IAM roles provide temporary credentials, AWS automatically manages credential rotation, which reduces the administrative burden of manual credential management.
Disadvantages of IAM Roles
Complex Configuration and Management:
- Configuring IAM roles can be complex, especially when dealing with cross-account access or intricate permissions, increasing the risk of misconfiguration.
Limited to AWS Environment:
- IAM roles are specific to AWS. If you have a multi-cloud setup or external resources, additional solutions are required for federated identity or cross-cloud permissions.
Permissions Overlap and Confusion:
- With multiple policies (identity-based, resource-based), there can be overlaps and potential conflicts, which may make troubleshooting permission issues challenging.
Cost of Misconfiguration:
- If IAM roles are misconfigured, they can lead to unintended access, posing security risks, or restrict needed access, impacting the application’s functionality.
Use Cases of IAM Roles in AWS
EC2 Instance Roles:
- Grant EC2 instances permissions to access AWS services (like S3, DynamoDB) securely without storing credentials in instance code.
Cross-Account Access:
- Use roles to allow users or applications in one AWS account to access resources in another account, commonly used in multi-account setups for centralized administration.
Federated Access:
- Allow external identities (e.g., from corporate identity providers like Active Directory) to access AWS resources temporarily by assuming a role, useful for hybrid environments.
Lambda Execution Roles:
- Provide AWS Lambda functions access to other AWS services, like S3 for data storage or DynamoDB for data retrieval, ensuring that the function has the least privilege necessary.
Automation and DevOps:
- IAM roles can be assigned to automation tools (like AWS CodePipeline or CloudFormation) to control resources during automated deployments and ensure security best practices are followed.
Conclusion :
AWS Identity and Access Management (IAM) Roles are essential for securely managing permissions and access across AWS services. IAM roles are different from users in that roles are meant to be assumed temporarily and are often assigned to applications, services, or users to grant specific, limited permissions to AWS resources.
If you have any questions, need clarifications, or want to discuss anything related to AWS technologies, feel free to reach out to me on LinkedIn. Connect with me at Aditya Gadhave, and I'll be more than happy to assist you. 😊
Subscribe to my newsletter
Read articles from Aditya Gadhave directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Aditya Gadhave
Aditya Gadhave
👋 Hello! I'm Aditya Gadhave, an enthusiastic Computer Engineering Undergraduate Student. My passion for technology has led me on an exciting journey where I'm honing my skills and making meaningful contributions.