Introduction to Offensive Security: Network Security (TryHackMe)
 J3bitok
J3bitok
In this article, I will write a write-up for Network Security that covers Methodology and Practical Examples of Network Security.
What type of firewall is Windows Defender Firewall?
Host FirewallDuring which step of the Cyber Kill Chain does the attacker gather information about the target?
Recon
Let’s summarize what we have done in this task to get root access on the target system of IP address MACHINE_IP:
We used
nmapto learn about the running services.We connected to the FTP server to learn more about its configuration.
We discovered a file containing the root password mistakenly copied to a public folder.
We used the password we found, allowing us to log in successfully.
We gained access to all the users’ files.
What is the password in the
secret.txtfile?ABC789xyz123
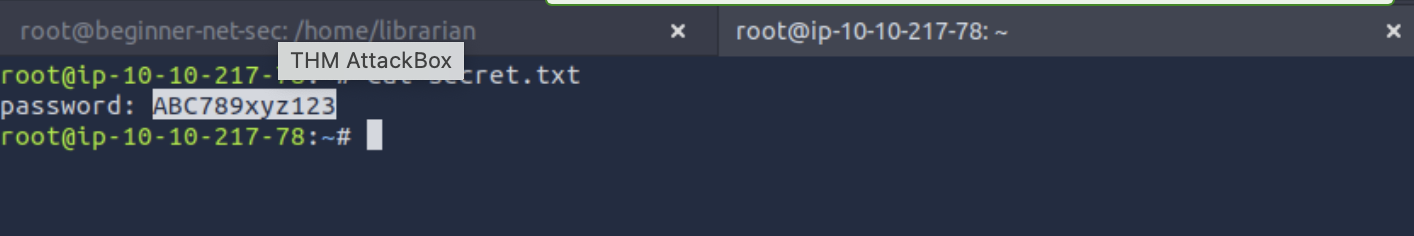
What is the content of the
flag.txtin the/rootdirectory?THM{FTP_SERVER_OWNED}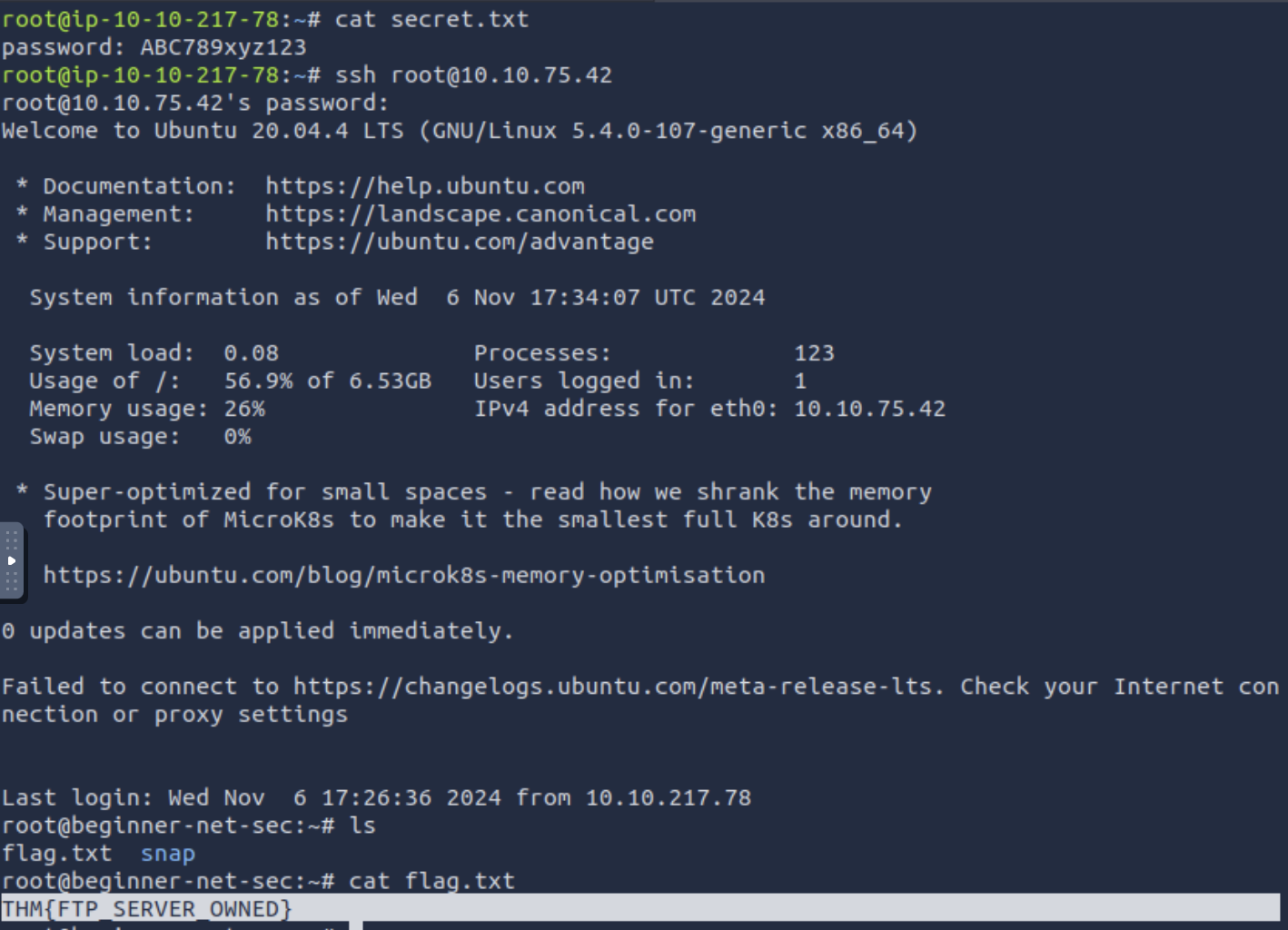
What is the content of the
flag.txtin the/home/librariandirectory?THM{LIBRARIAN_ACCOUNT_COMPROMISED}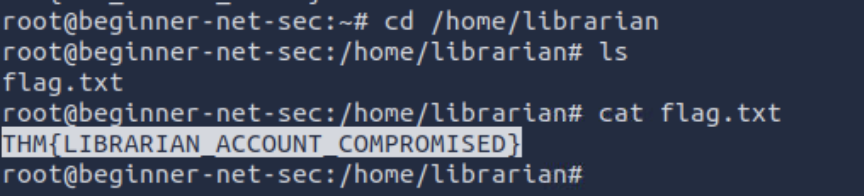
Thank you for reading my article. Please leave any questions or comments on improving my learning journey and the Lab THM challenges. We can also connect more on LinkedIn or X.
Subscribe to my newsletter
Read articles from J3bitok directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

J3bitok
J3bitok
Software Developer Learning Cloud and Cybersecurity Open for roles * If you're in the early stages of your career in software development (student or still looking for an entry-level role) and in need of mentorship you can book a session with me on Mentorlst.com.