Introduction to Defensive Security: Security Operations (TryHackMe)
 Jebitok
Jebitok
In this article, I will write a Security Operations write-up covering an Introduction to Security Operations, Elements of Security Operations, and a Practical Example of SOC.
What does SOC stand for?
Security Operations CenterHow many hours a day does the SOC monitor the network?
24What does NSM stand for?
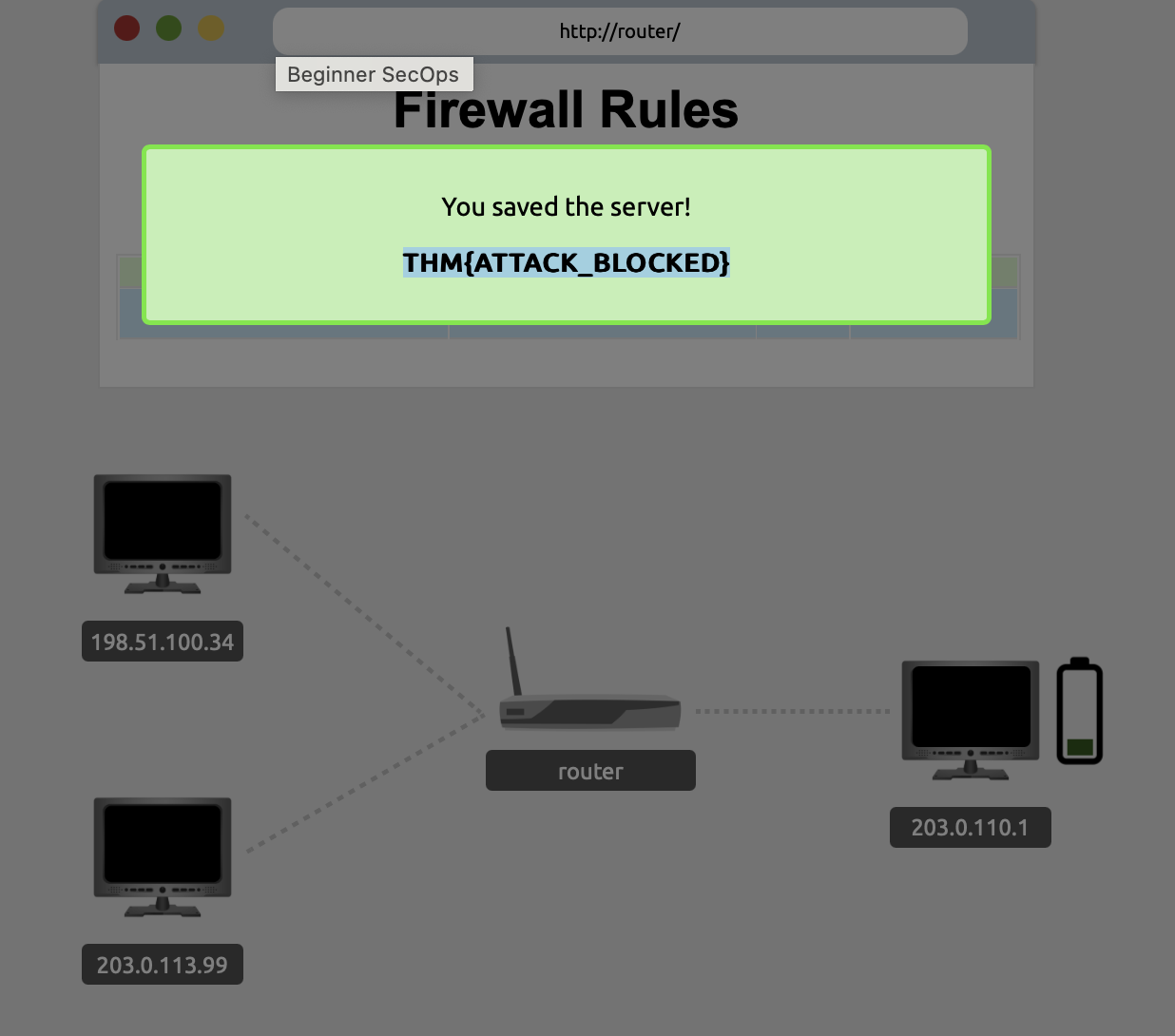
Network security monitoringAdd the necessary firewall rules to block the ongoing attack. What is the flag that you have received after successfully stopping the attack?
THM{ATTACK_BLOCKED}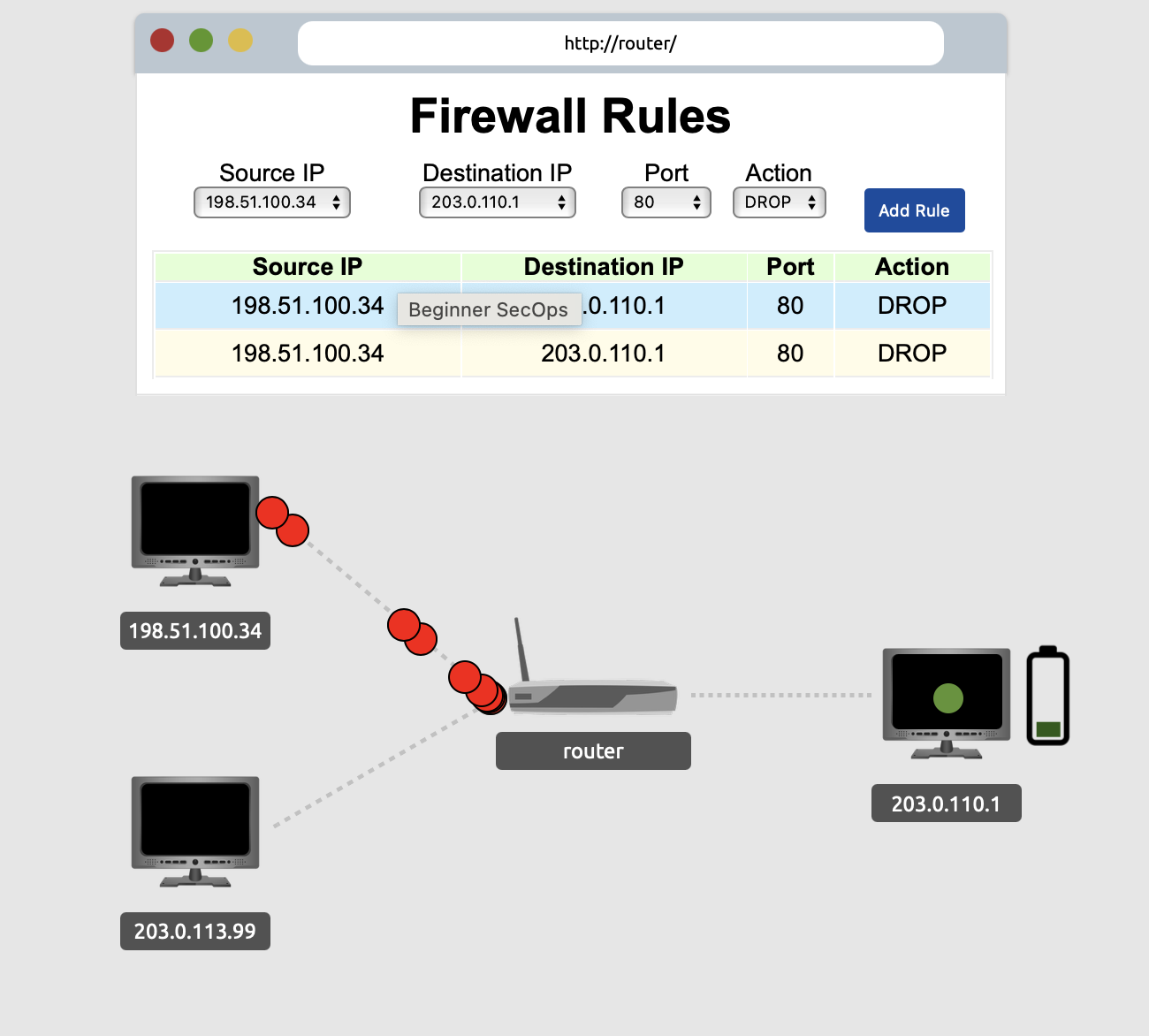
Thank you for reading my article. Please leave any questions or comments on improving my learning journey and the Lab THM challenges.
Subscribe to my newsletter
Read articles from Jebitok directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Jebitok
Jebitok
Software Developer | Learning Cybersecurity | Open for roles * If you're in the early stages of your career in software development (student or still looking for an entry-level role) and in need of mentorship, you can reach out to me.