Update network access for Autonomous DB
 Matt Mulvaney
Matt Mulvaney
In Oracle Cloud Infrastructure (OCI) > Autonomous Database (ADB), the "Choose Network Access" setting lets you control how users can connect to your database.
Important: If you make a change, it changes the connections in the Wallet. So you must re-download the wallet.
Important: You cannot do this on Always Free. This is only possible on Paid ADBs.
How to make a change
Find your Autonomous Database in OCI, click More Actions > Update network access
If you cannot find this option… you are probably using Always Free & the option is not available.
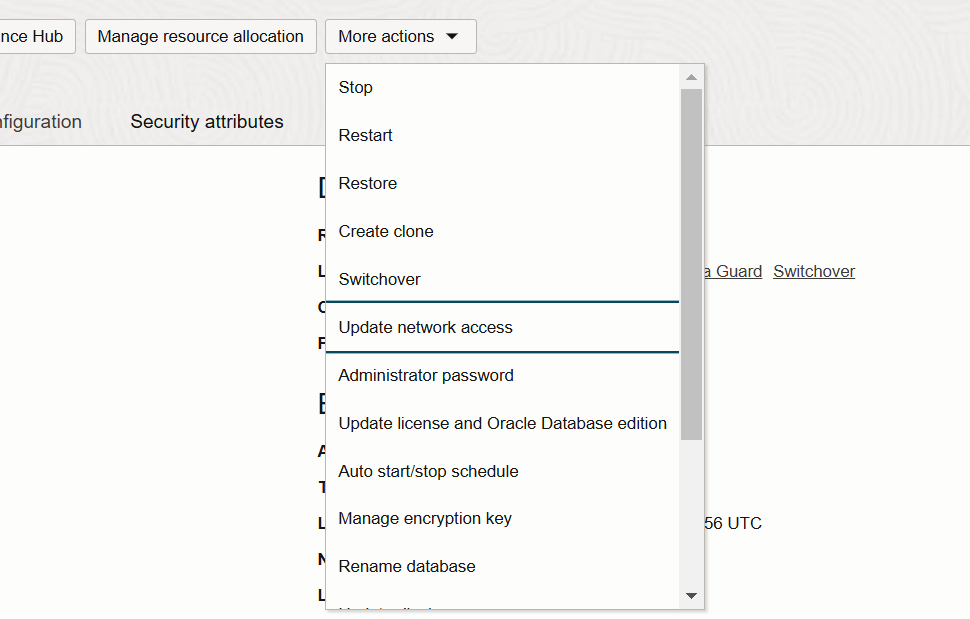
Settings
Here are what the settings look like:
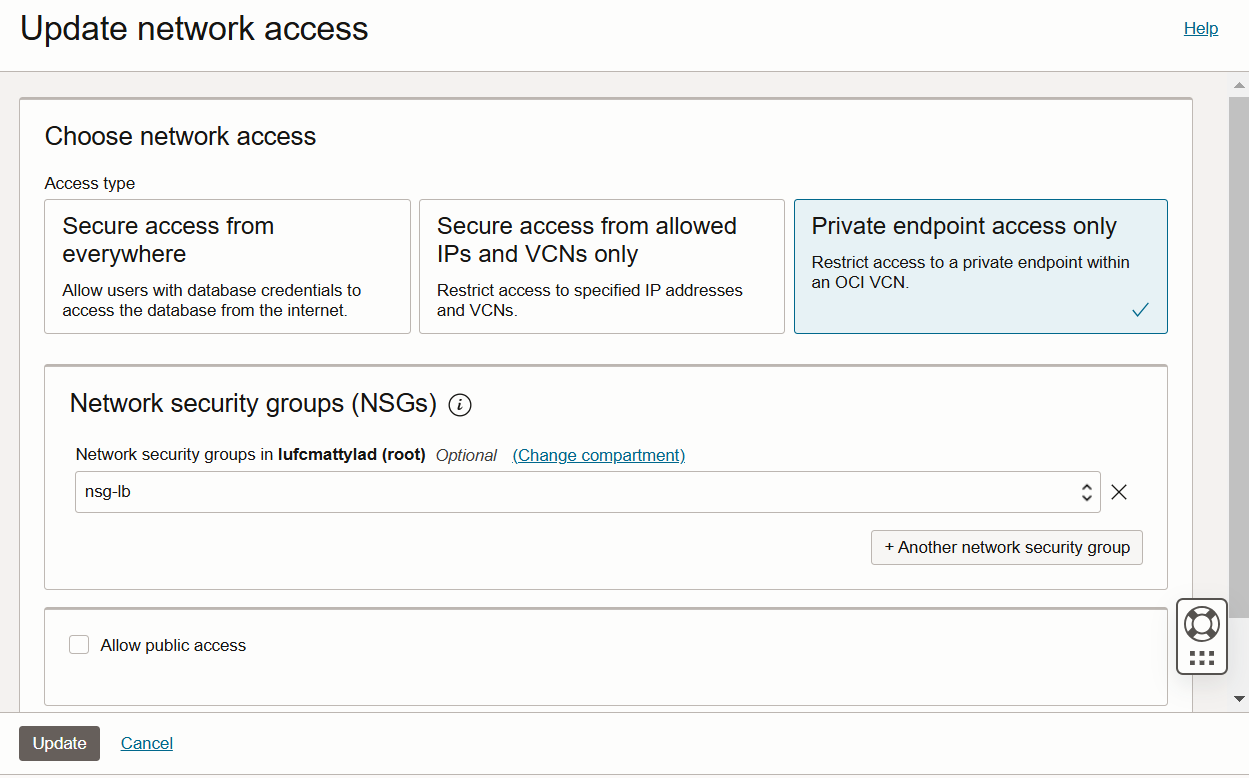
What they are used for
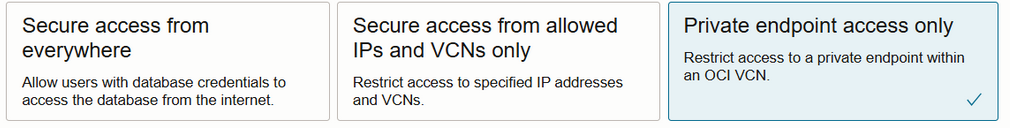
TL;DR From left to right, just think Public, Mixed, Private
Secure Access from Everywhere
Use Cases:
Public applications needing global database access
Distributed teams or clients connecting from varied locations
APEX will be available across the Internet
Database will accessible given the Username, Password, Service & Wallet.
Secure Access from Allowed IPs and VCNs Only
Use Cases:
Controlled access for internal company IPs or office locations i.e over VPNs. Oracle has some good documentation on this.
Applications requiring restricted connectivity from specific OCI VCNs
Which means
IPs i.e useful for controlled access by remote teams, developers, or users outside of OCI who are connecting from static IP addresses.
VCNs i.e Ideal for applications, resources, or other services within OCI that need direct interaction with APEX or the database.
This option is more flexible for mixed-access needs
Private Endpoint Access Only
Use Cases:
Highly secure, internal applications within OCI
Used for Load Balancers
This option provides stricter security with full isolation within OCI.
It restricts access entirely to OCI’s private network, with no internet exposure.
Only resources within the same VCN or peered VCNs can access the database.
Changing a setting
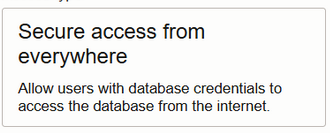
Secure Access from Everywhere
Just click the icon
Secure Access from Allowed IPs and VCNs Only
Click the Icon
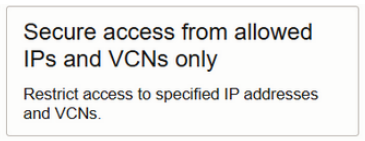
And then optionally set the IPs and VCNs afterwards
Private Endpoint Access Only
This moves the ADB to a private subnet belonging to a VCN. This is the highest level of security. The ADB can be accessed by any compute on the same VCN or on another VCN via the LPG.
To change to Private Endpoint, a Network Security Group can be optionally set now, or later. A Network Security Group (NSG) on Oracle Cloud Infrastructure (OCI) is like a firewall that defines security rules to control inbound and outbound traffic - so by assigning an ADB to a NSG, you are assigning it to a set of rules which contain ingress/egress (i.e the incoming/outgoing CIDRs) of the VCNs including port numbers. For example, ORDS on Autonomous operates on port 443, so I may allow my public subnet to allow incoming (ingress) traffic (http or tcp on port 443).
In addition, public access can be allowed by an IP. A public IP does work, although defeats the object, as this could present a security vulnerability because it contradicts the isolation typically expected with private subnets. However is could be used for Remote Developer Access or REST access from third party sources.
After making a change
If you make a change, it changes the connections in the Wallet. So you must re-download the wallet.
Database Connection > Download Wallet
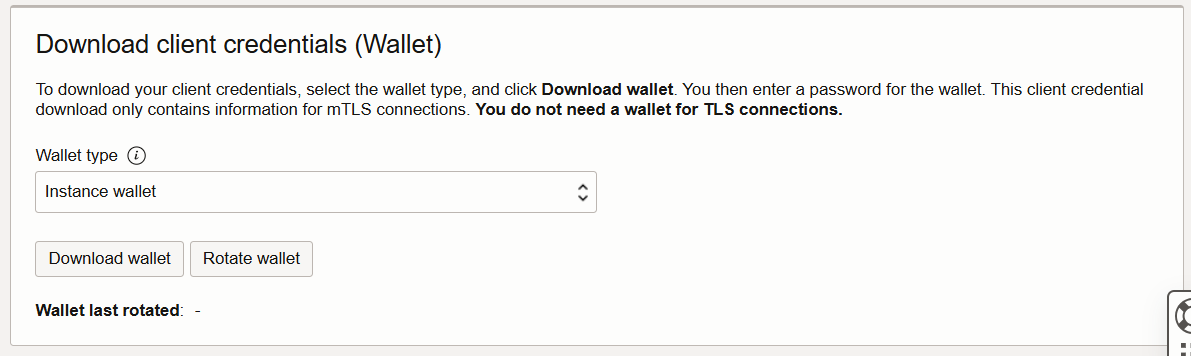
ENJOY!
What’s the picture? Someone left the door open at Knareborough Castle, which is rare, so I snapped this quick picture - it looks like its in good nick too. Visit Yorkshire!
Subscribe to my newsletter
Read articles from Matt Mulvaney directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Matt Mulvaney
Matt Mulvaney
With around 20 years on the job, Matt is one of the most experienced software developers at Pretius. He likes meeting new people, traveling to conferences, and working on different projects. He’s also a big sports fan (regularly watches Leeds United, Formula 1, and boxing), and not just as a spectator – he often starts his days on a mountain bike, to tune his mind.