Cyber Defense Frameworks: SOC Level 1 (TryHackMe)
 Jebitok
Jebitok
In this article, I will write a Pyramid of Pain write-up: The Basics that covers Hash Values, IP Addresses, Domain Names, Host Artifacts, Network Artifacts, Tools, TTPs, and a Practical of the Pyramid of Pain.
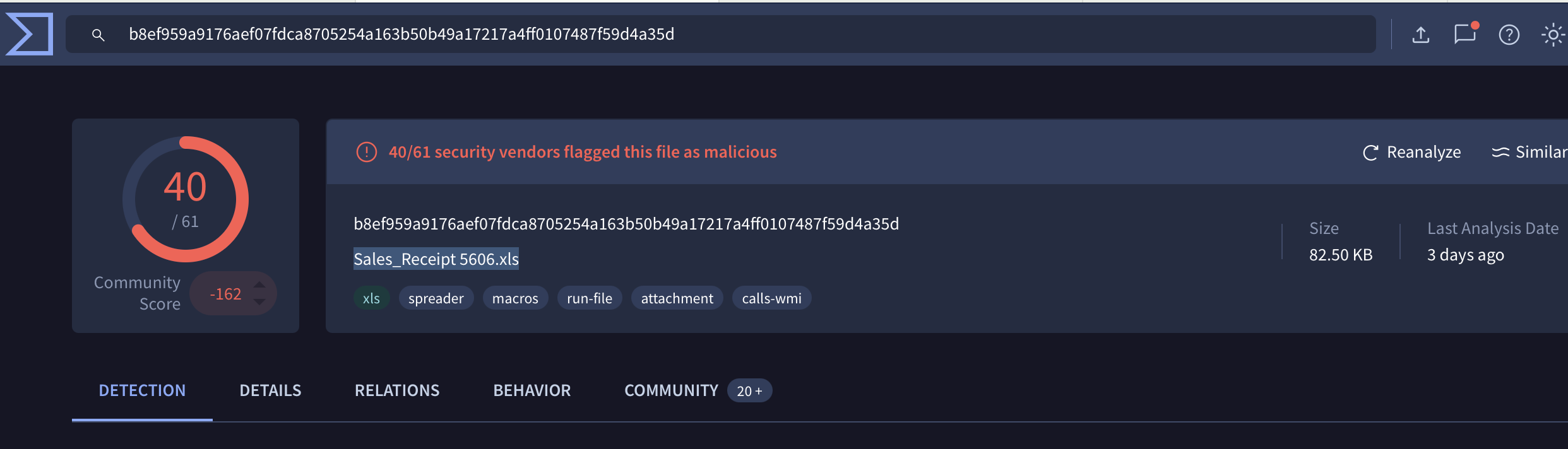
- Analyse the report associated with the hash "b8ef959a9176aef07fdca8705254a163b50b49a17217a4ff0107487f59d4a35d" here. What is the filename of the sample?
Sales_Receipt 5606.xls
I used VirusTotal to search the hash inorder to find the filename
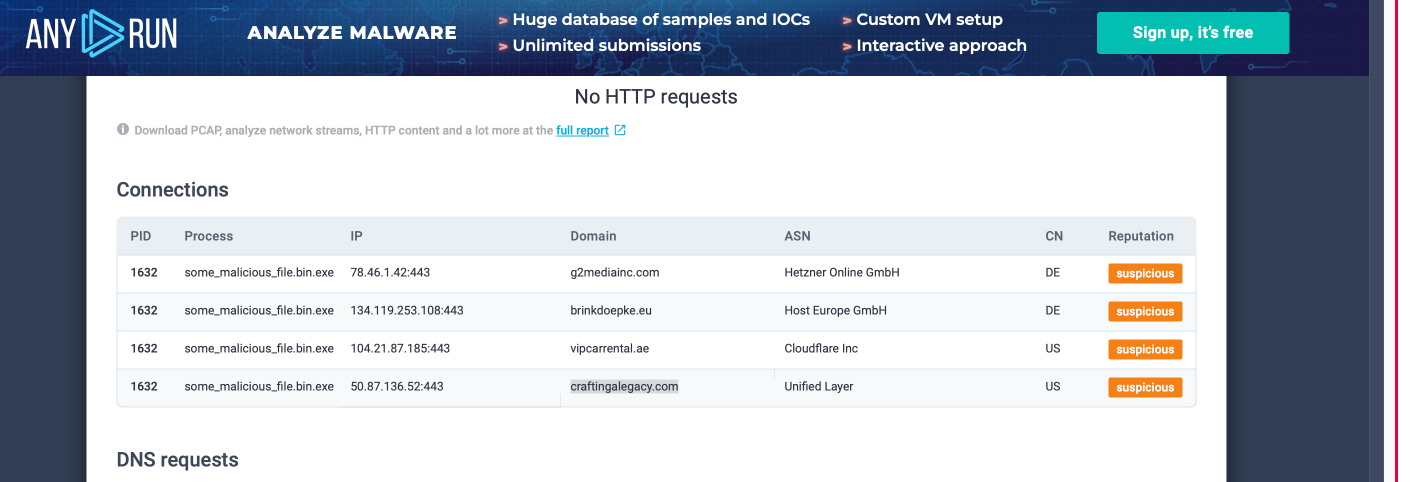
2. Read the following report to answer this question. What is the first IP address the malicious process (PID 1632) attempts to communicate with? 50.87.136.52
3. Read the following report to answer this question. What is the first domain name the malicious process ((PID 1632) attempts to communicate with? craftingalegacy.com
You will find an answer by scrolling through this page i.e a screenshot provided
4. Go to this report on app.any.run and provide the first suspicious domain request you are seeing, you will be using this report to answer the remaining questions of this task. craftingalegacy.com
click the text report for the suspicious domain request and you will find this domain on the redirected page
What term refers to an address used to access websites?
Domain NameWhat type of attack uses Unicode characters in the domain name to imitate the a known domain?
Punycode attackProvide the redirected website for the shortened URL using a preview: https://tinyurl.com/bw7t8p4u
https://tryhackme.com/
just run this shortened URL on the web and it will open the Tryhackme website mine opened my THM dashboard but notice that the answer ends at .com/
A security vendor has analysed the malicious sample for us. Review the report here to answer the following questions.
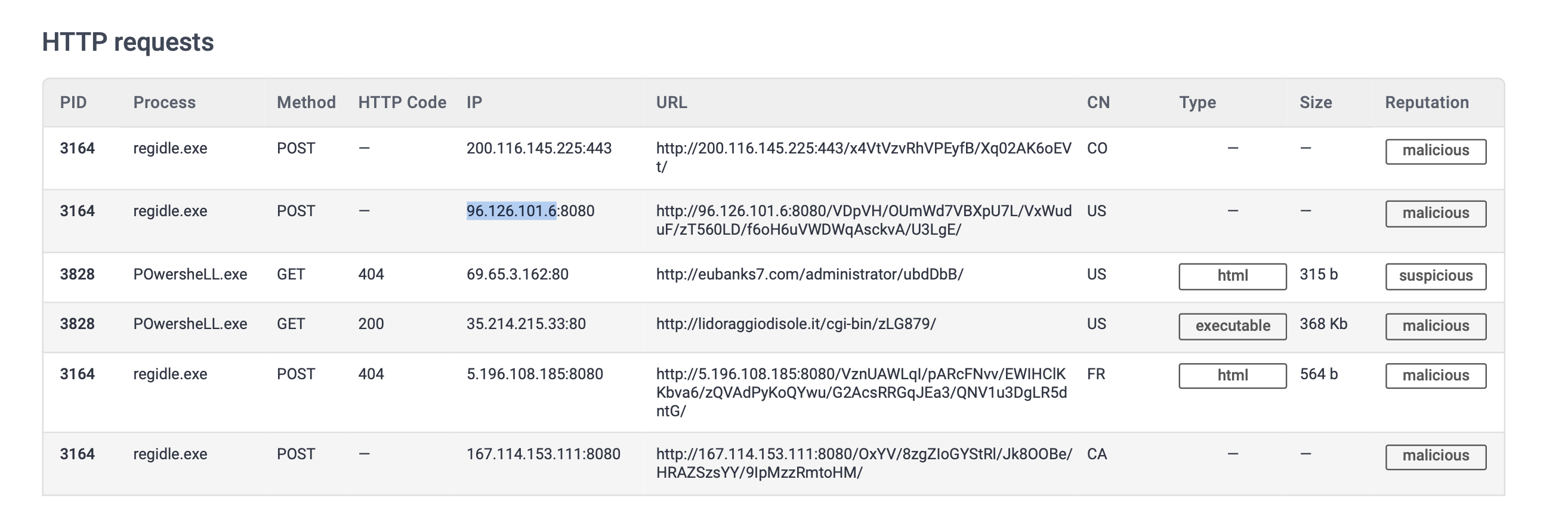
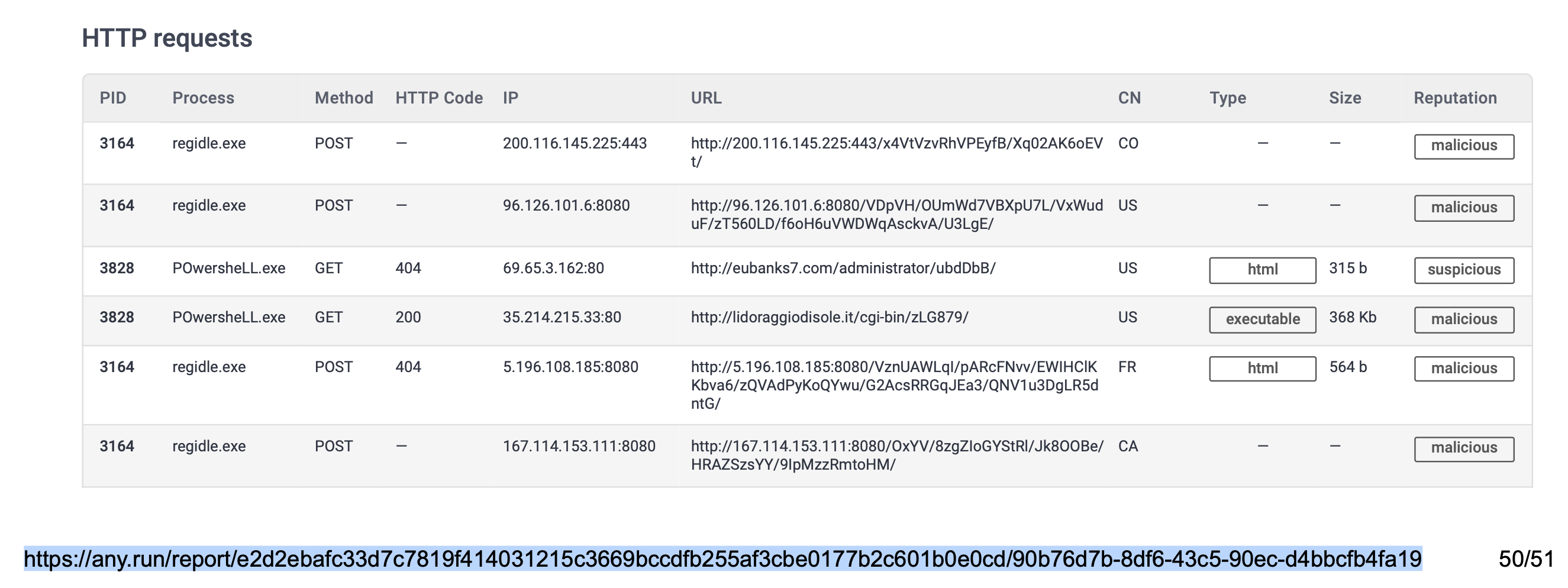
A process named regidle.exe makes a POST request to an IP address based in the United States (US) on port 8080. What is the IP address?
96.126.101.6
open the URL to the report then scroll down to HTTP Requests checking the one that has port 8080 and based in the US
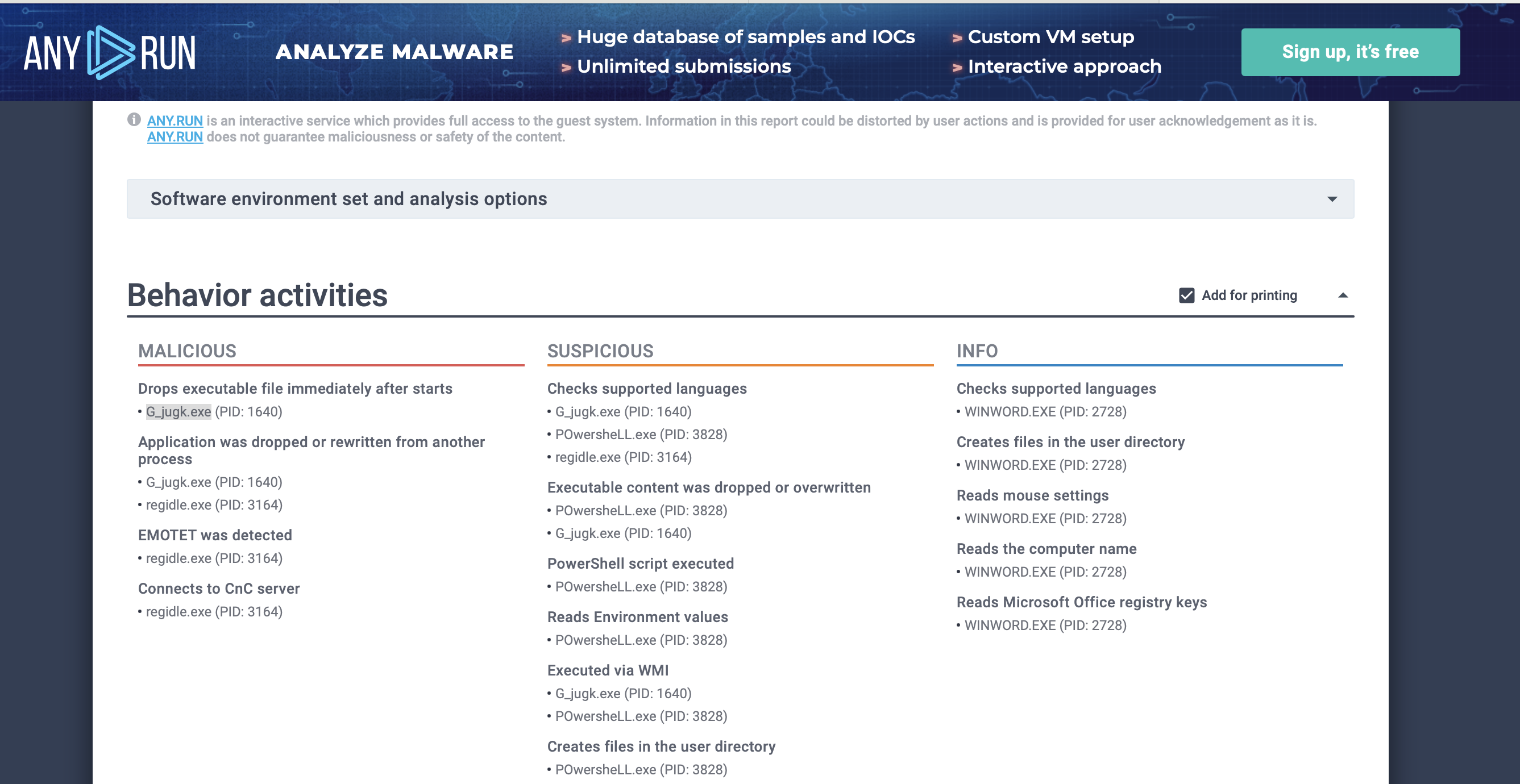
The actor drops a malicious executable (EXE). What is the name of this executable?
G_jugk.exeafter the HTTP Requests, there’s a link to a report on Any.Run which is an interactive malware-hunting service. Under Malicious you’ll check for the ‘Drops executable file immediately after starts’
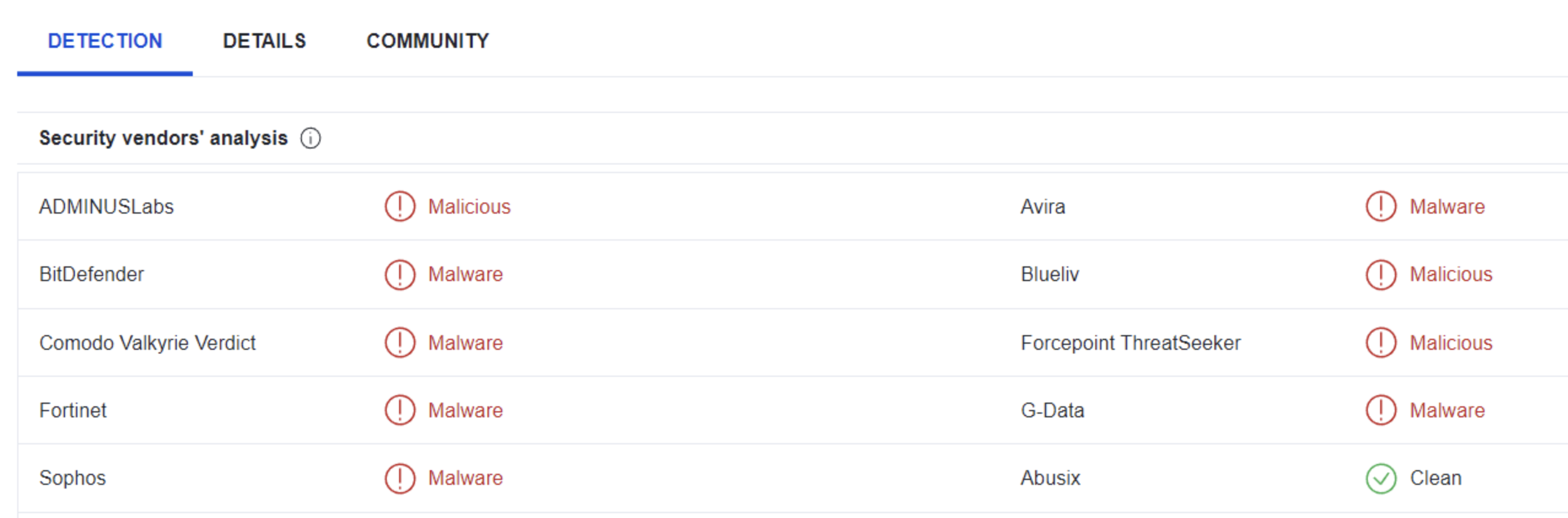
Look at this report by Virustotal. How many vendors determine this host to be malicious?
9
According to the hint we’re to count both the malicious and malware labels
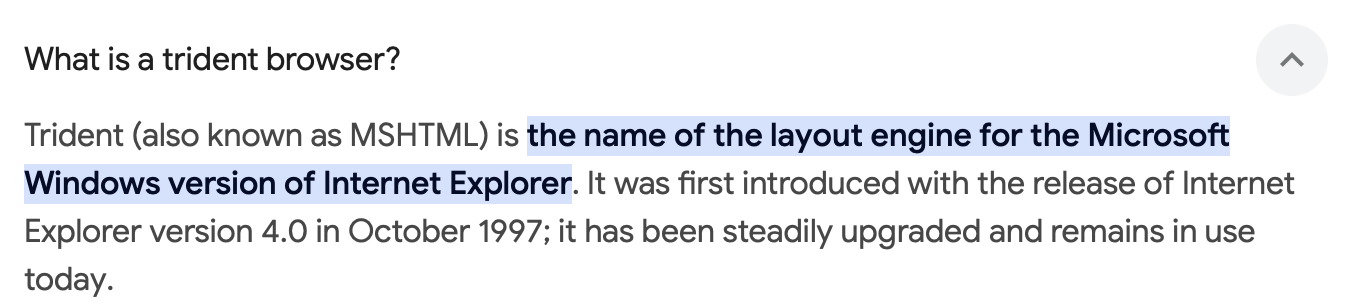
What browser uses the User-Agent string shown in the screenshot above?
Internet Explorer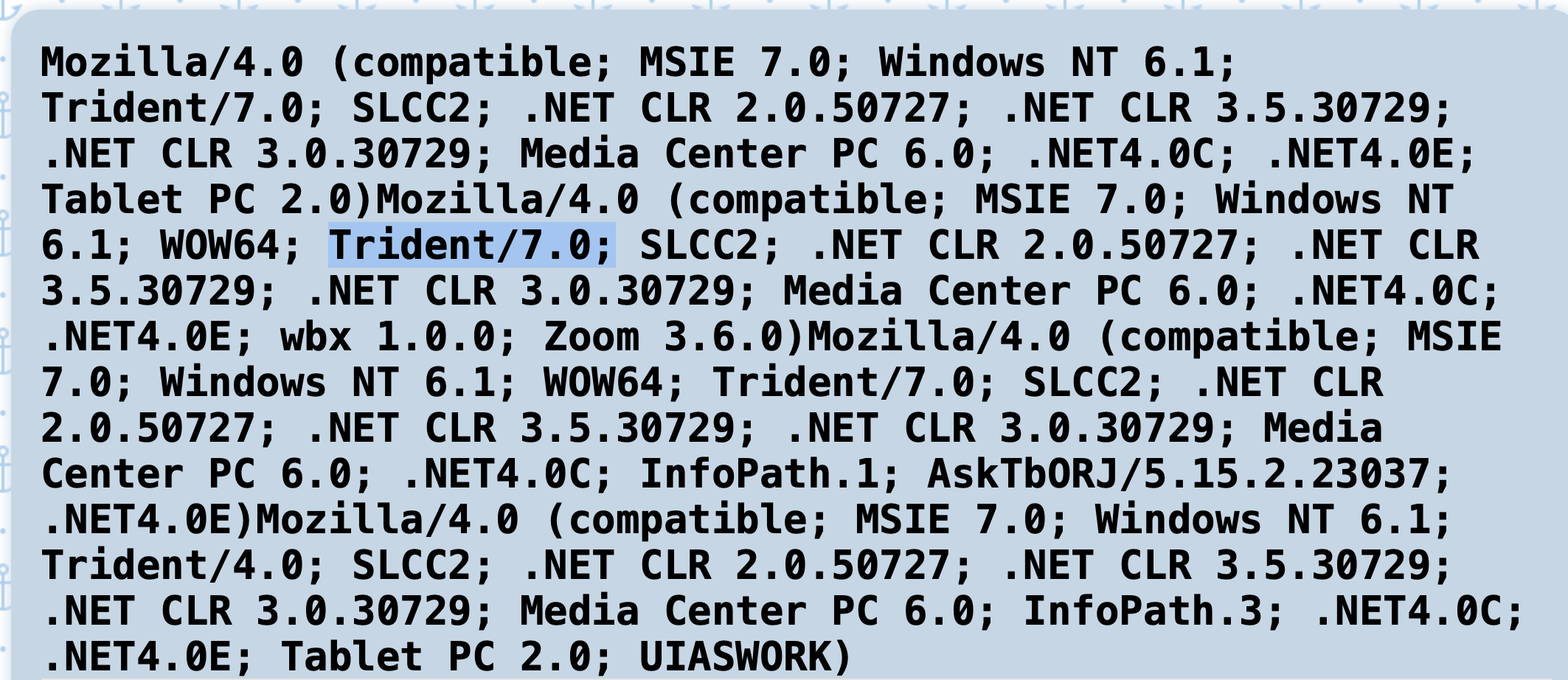
How many POST requests are in the screenshot from the pcap file?
6Provide the method used to determine similarity between the files
Fuzzy HashingProvide the alternative name for fuzzy hashes without the abbreviation
context triggered piecewise hashes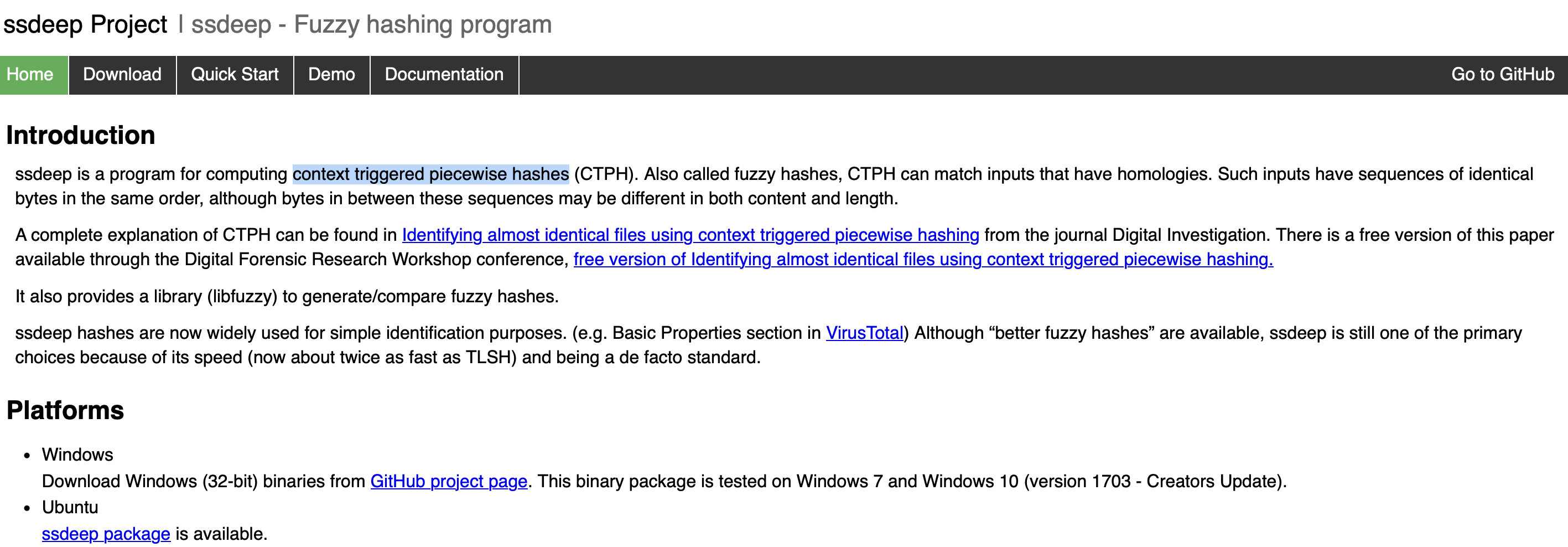
Navigate to ATT&CK Matrix webpage. How many techniques fall under the Exfiltration category?
9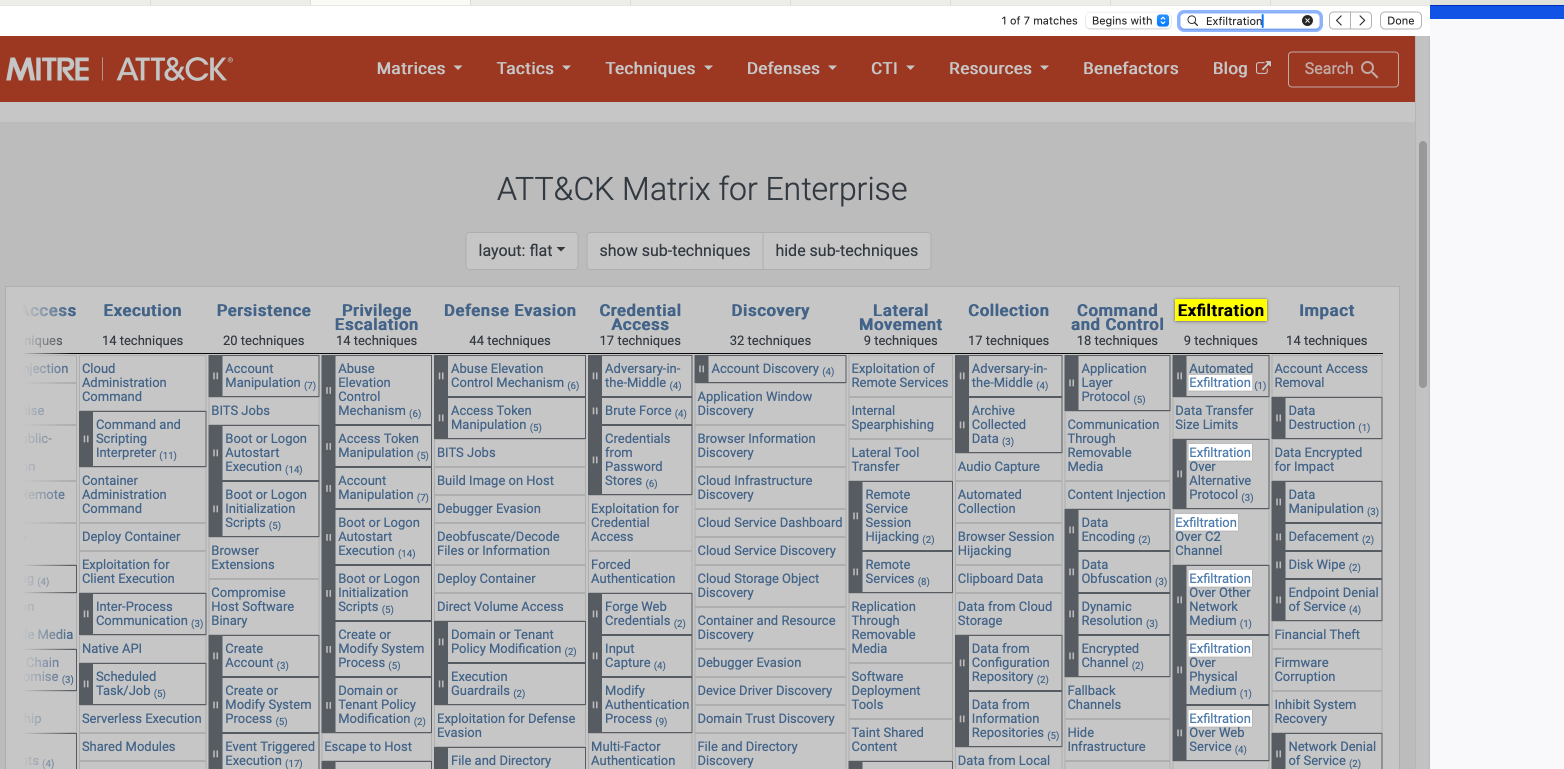
Chimera is a China-based hacking group that has been active since 2018. What is the name of the commercial, remote access tool they use for C2 beacons and data exfiltration?
Cobalt Strike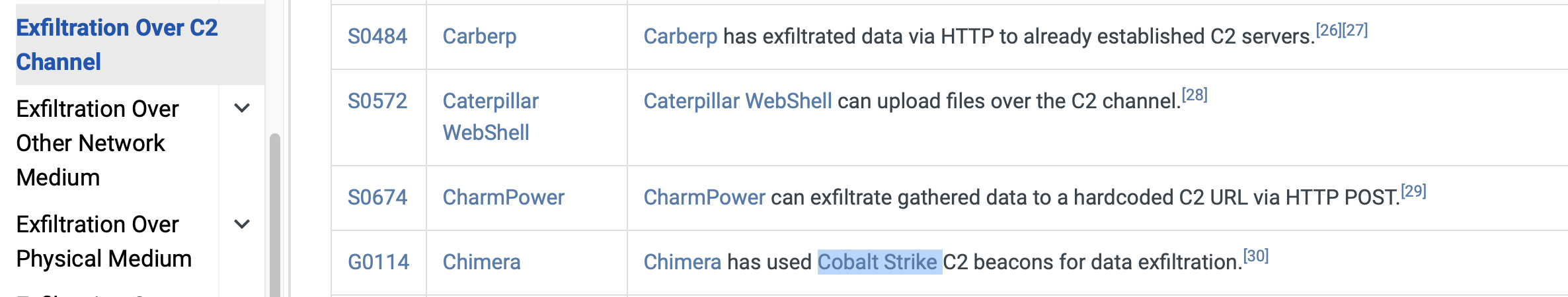
Deploy the static site attached to this task and place the prompts into the correct tiers in the pyramid of pain!
Once you are sure, submit your answer on the static site to retrieve a flag!
Answer the questions below
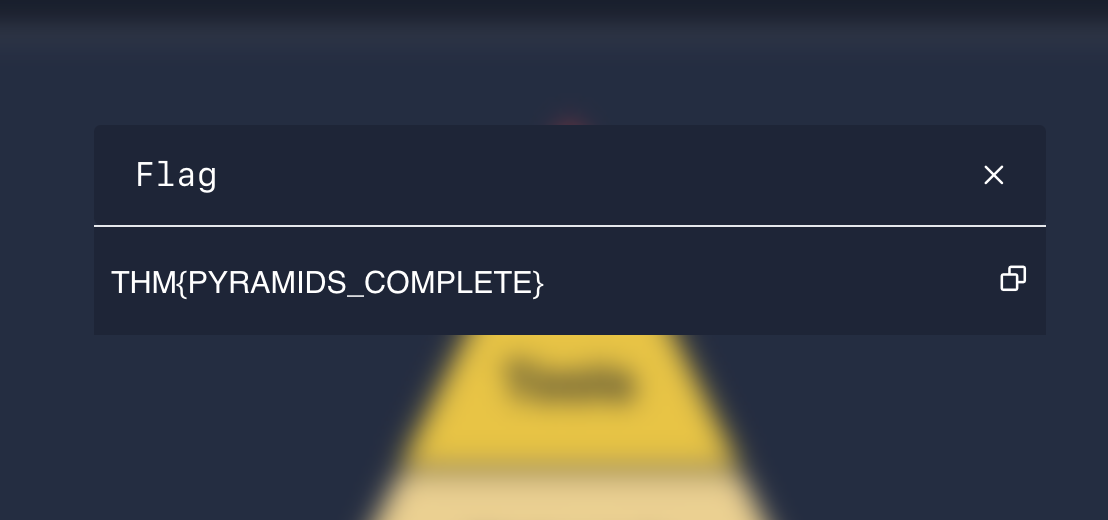
Complete the static site. What is the flag?
THM{PYRAMIDS_COMPLETE}TTP (Tactics, Techniques, and Procedures) - "The attackers' plans and objectives"
- TTPs describe the behavior and methods attackers use to achieve their objectives.
Tools - "The attackers have utilized these to accomplish their objective"
- Tools are the software, scripts, or utilities used by attackers to carry out their activities.
Network - "These artifacts can present themselves as C2 traffic, for example"
- Network artifacts like traffic patterns or protocols can indicate command-and-control (C2) communications.
IP addresses - "These addresses can be used to identify the infrastructure an attacker is using for their campaign"
- IP addresses are often tied to servers or hosts used in an attacker’s infrastructure.
Hash values - "These signatures can be used to attribute payloads and artifacts to an actor"
- Hash values uniquely identify files or payloads, helping attribute them to specific threat actors or campaigns.
Domain - "An attacker has purchased this and used it in a typosquatting campaign"
- Domains can be registered to resemble legitimate sites in typosquatting or phishing campaigns.
Thank you for reading my article. Please leave any questions or comments on improving my learning journey and the THM challenges.
Subscribe to my newsletter
Read articles from Jebitok directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Jebitok
Jebitok
Software Developer | Learning Cybersecurity | Open for roles * If you're in the early stages of your career in software development (student or still looking for an entry-level role) and in need of mentorship, you can reach out to me.