Title: Enhancing Reverse Shell Interactivity with Python's pty Module
 Anuj Singh Chauhan
Anuj Singh ChauhanIn the world of cybersecurity, reverse shells play a crucial role in penetration testing, allowing security professionals to interact with remote systems from a compromised session. But, a raw reverse shell often lacks the interactivity needed for efficient operations, limiting command history, job control, and even terminal output display. Here’s how Python is used to upgrade a basic shell into a fully interactive terminal session.
Steps to Upgrade the Reverse Shell:
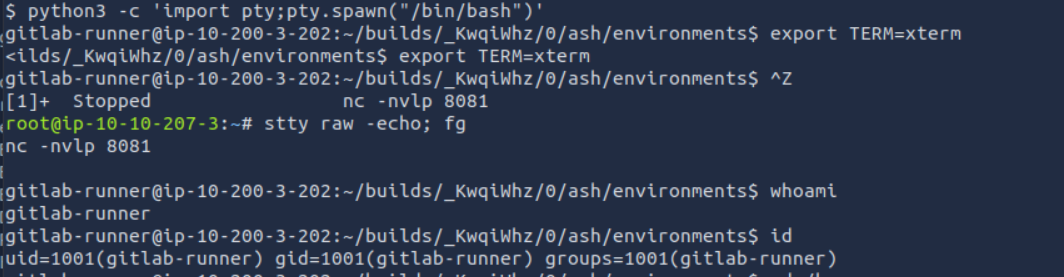
1. Spawn a Pseudo-Terminal (pty) Shell:
python3 -c 'import pty;pty.spawn("/bin/bash")'
This command uses Python's pty module to create a pseudo-terminal, transforming the reverse shell into an interactive Bash shell. The pty shell allows for a more stable connection.
2. Set the Terminal Type for Improved Output:
export TERM=xterm
Setting the terminal type to xterm enhances display features, improving text formatting and colors. This small tweak makes navigating and working within the shell much smoother. Like you can use commands just like a regular terminal.
3. Suspend the Shell Process (^z):
^z
Pressing ^z suspends the shell temporarily, allowing us to adjust the terminal settings on our end. This is essential for making the reverse shell behave like a native terminal.
4. Configure the Attacker’s Terminal:
stty raw -echo; fg
stty raw -echo: Configures the terminal to disable special character interpretation and stops echoing typed commands. This makes the shell more responsive.
fg: Brings the shell back into the foreground, resuming the interactive session.
Subscribe to my newsletter
Read articles from Anuj Singh Chauhan directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by
