AWS VPC -Basics
 Subbu Tech Tutorials
Subbu Tech TutorialsThis blog includes some of the resources from Mr. Chetan Agrawal’s Udemy course, AWS VPC and Networking. This course is highly insightful and an excellent choice for learning AWS VPC concepts. Thank you very much, Mr. Chetan Agrawal.
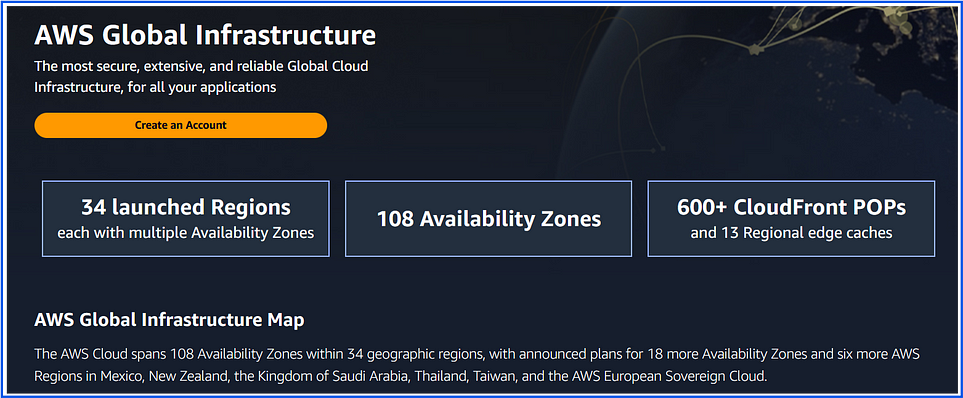
1. AWS Region
A geographical area where AWS has multiple data centers, called Availability Zones (AZs).
Each region operates independently for fault tolerance and data residency.
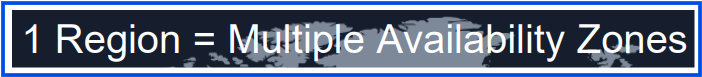
2. Availability Zone (AZ)
A single data center or a group of data centers within an AWS region.
AZs are isolated from each other but connected via low-latency networks for high availability.
VPC:
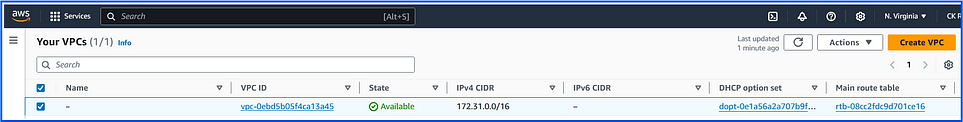
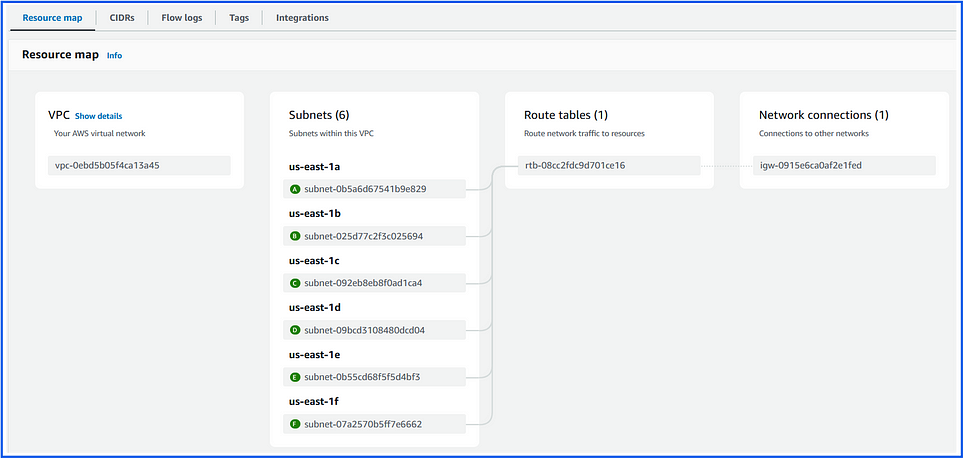
In AWS, a Virtual Private Cloud (VPC) is a logically isolated network within the AWS cloud that you define and manage. It allows you to have complete control over your virtual networking environment, including IP address ranges, subnets, route tables, and security settings.
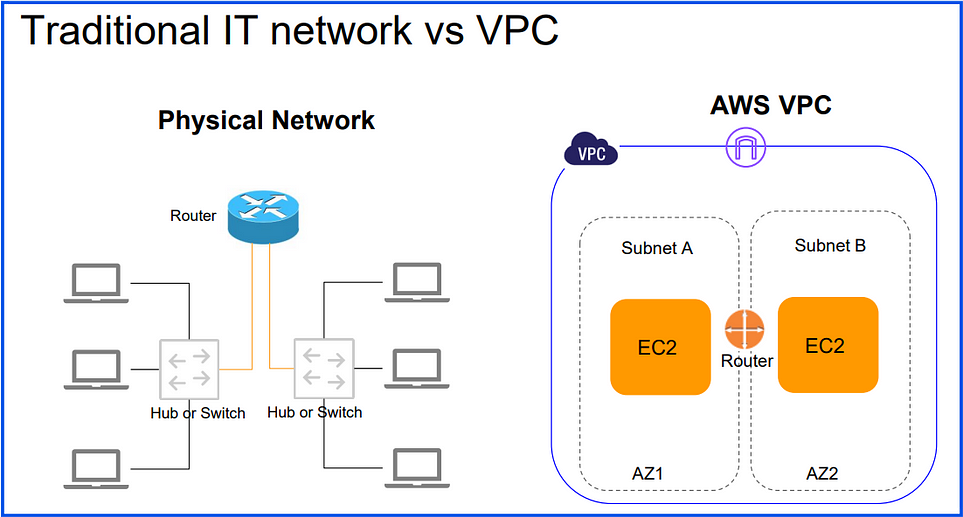
When creating a VPC, you define the IP address range (CIDR block) for that VPC (e.g., 172.31.0.0/16).
VPC Scope
Account-Level: Each VPC is tied to a single AWS account.
Region-Level: Each VPC is specific to a single AWS region and cannot span multiple regions.
Availability Zone Level: A VPC can span multiple AZs within its region, but individual subnets within the VPC are confined to a single AZ.
VPC building blocks:
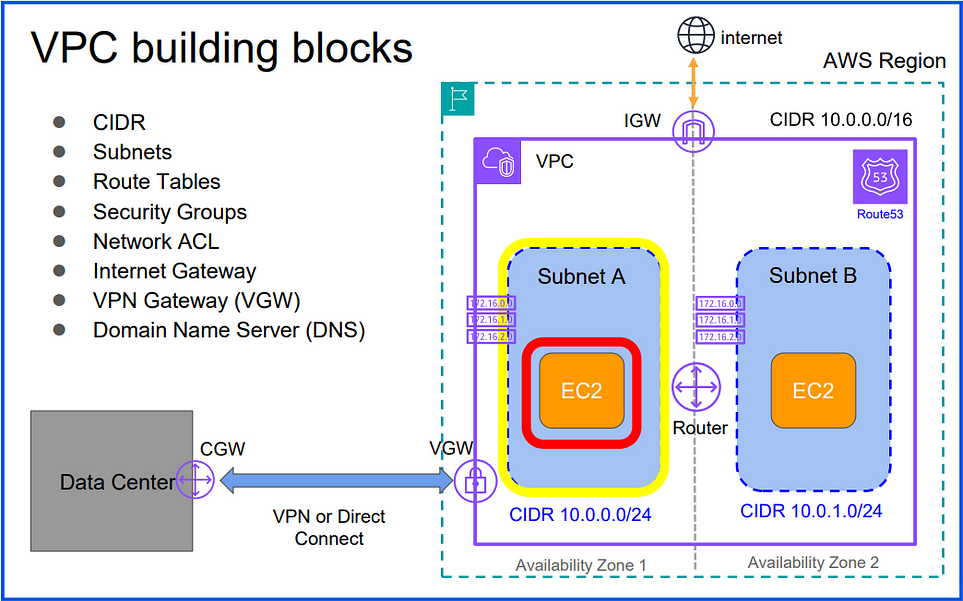
1. CIDR — Classless Inter Domain Routing:
Before jumping into CIDR we should know about IP addresses:
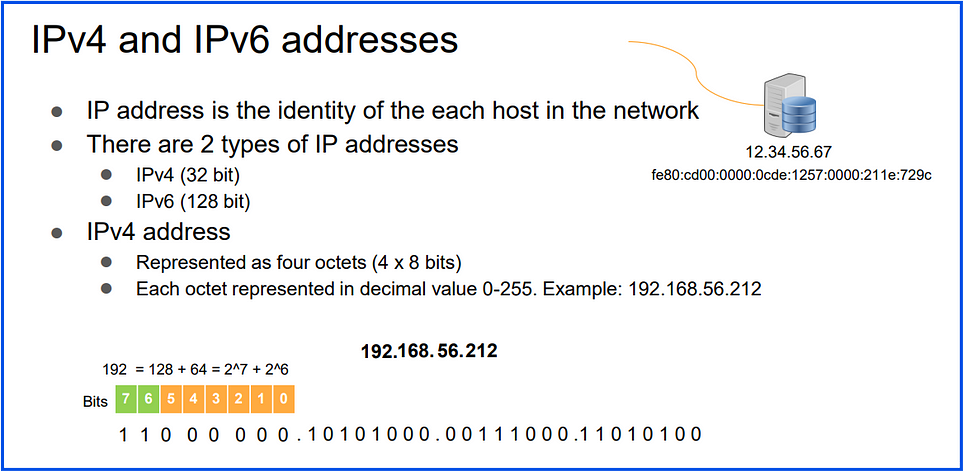
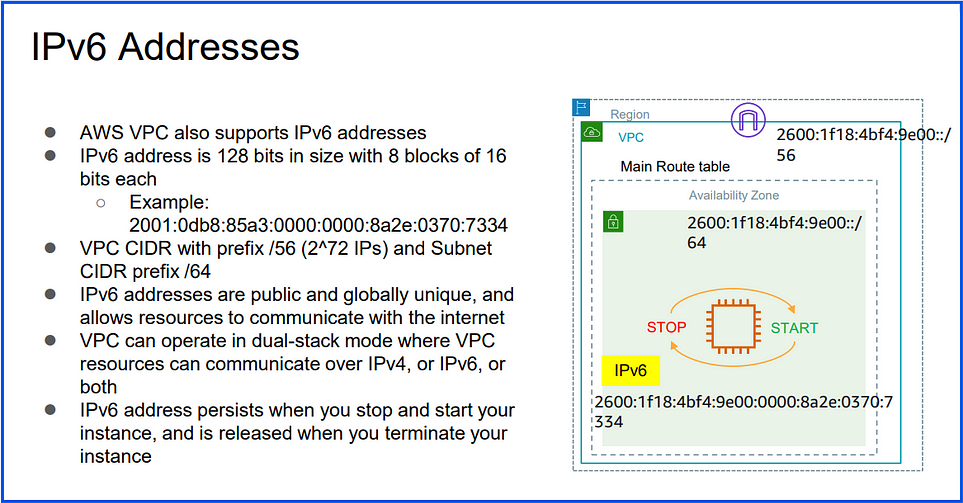
IPv4 and IPv6 addresses:
IP Address: An IP (Internet Protocol) address is a unique number assigned to each device on a network, allowing them to communicate with each other. It’s like a device’s “address” on the internet or local network.
There are 2 types of IP addresses
● IPv4 (32 bit)
● IPv6 (128 bit)
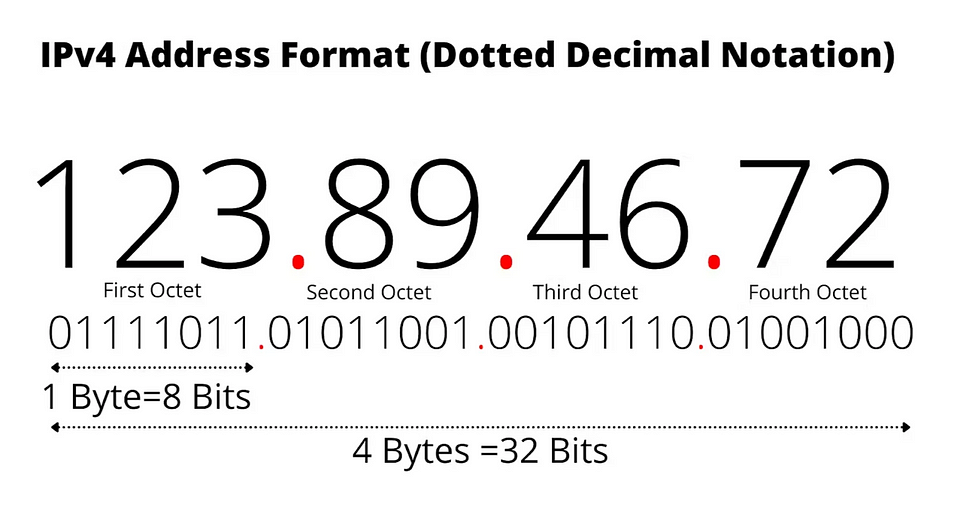
IPv4 address:
● Represented as four octets (4 x 8 bits)
● Each octet represented in decimal value 0–255. Example: 123.89.46.72
IPv6 address:
- 128-bit address, written in eight groups of hexadecimal numbers (e.g.,
2001:0db8:85a3:0000:0000:8a2e:0370:7334).
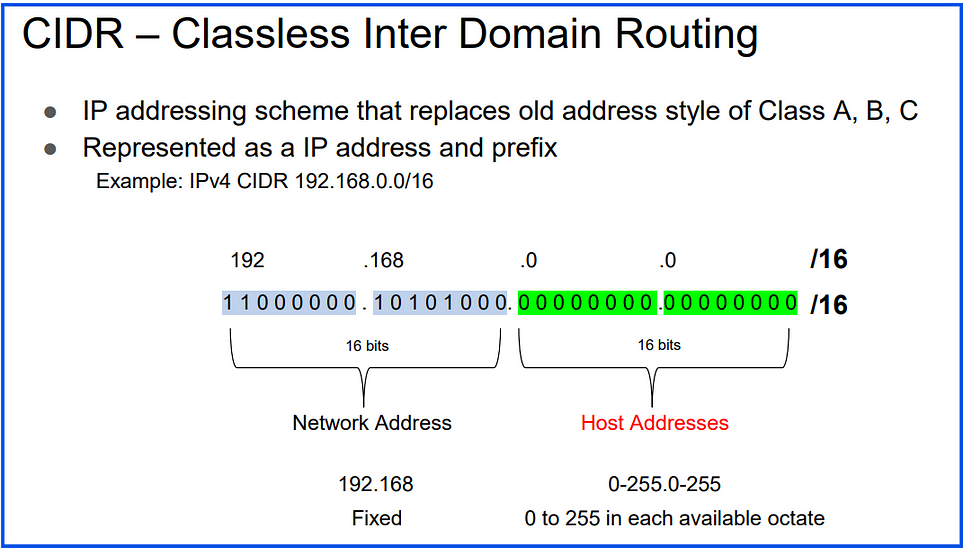
CIDR (Classless Inter-Domain Routing) is a method for allocating IP addresses and routing internet traffic efficiently. In CIDR notation, an IP address is followed by a “/” and a number, which indicates the number of bits in the network prefix.
Example:
CIDR Notation:
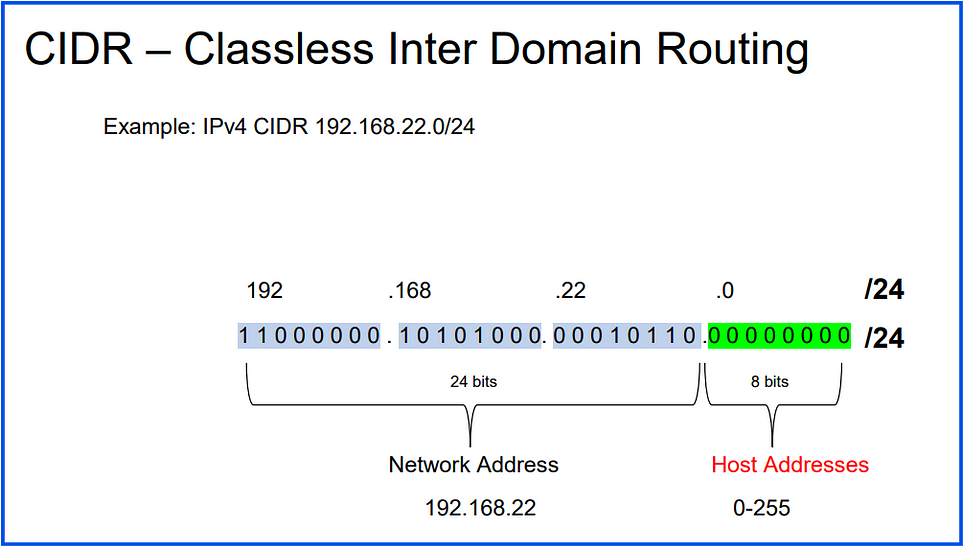
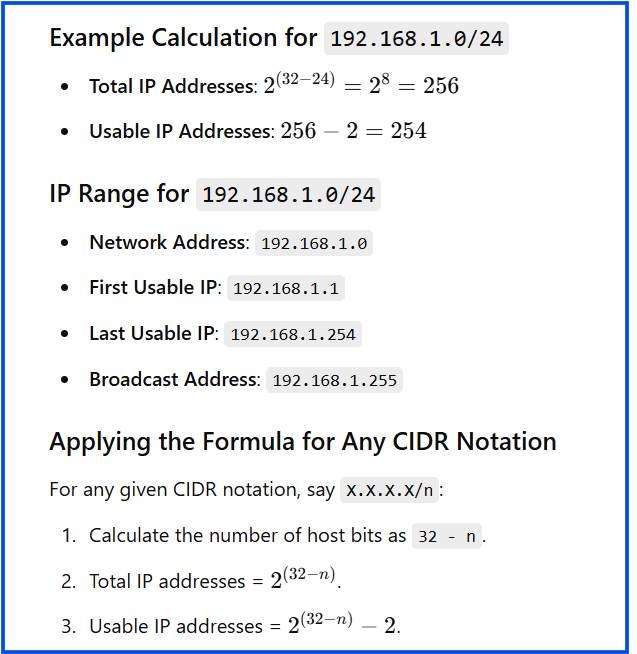
192.168.1.0/24192.168.1.0: Network address/24: Prefix length, indicating the first 24 bits are the network portion, and the remaining bits are for host addresses.
Key Points:
IP Range Allocation: CIDR allows specifying ranges, making IP allocation more flexible than traditional subnetting.
Efficient Routing: Reduces the number of routing entries by aggregating IP addresses.
Common CIDR Blocks:
/16(e.g.,10.0.0.0/16): Provides 65,536 addresses./24(e.g.,192.168.1.0/24): Provides 256 addresses./32(e.g.,192.168.1.1/32): Represents a single IP address.
CIDR is widely used in VPC design to define IP ranges for networks and subnets.
Example:
2. Subnets:
Divides a network into smaller, more manageable segments.
Example: A network with IP address 192.168.1.0/24 can be divided into subnets like 192.168.1.0/25 and 192.168.1.128/25.
A subnet (short for “subnetwork”) is a segmented portion of a Virtual Private Cloud (VPC) in a cloud environment, like AWS, Azure, or GCP.
- Public Subnets: Subnets that are connected to the internet via an Internet Gateway. Resources within public subnets (e.g., web servers) can have direct internet access.
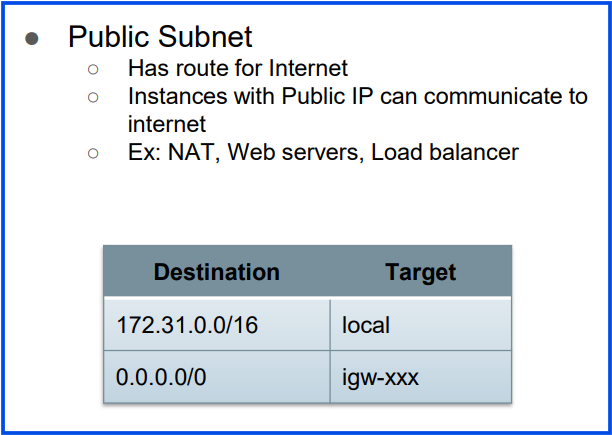
- Private Subnets: Subnets that are not directly accessible from the internet. Resources in private subnets (e.g., databases) can connect to the internet via a NAT Gateway but do not accept inbound connections from the internet.
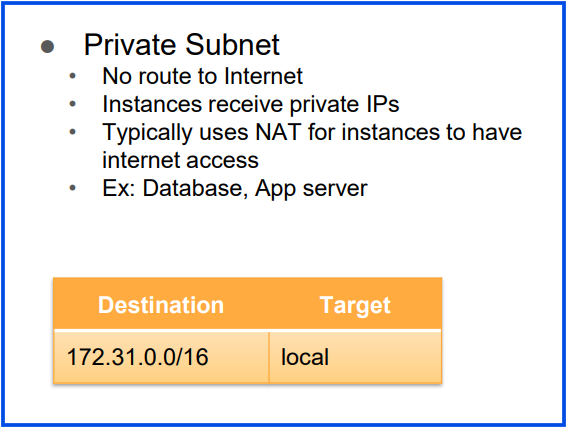

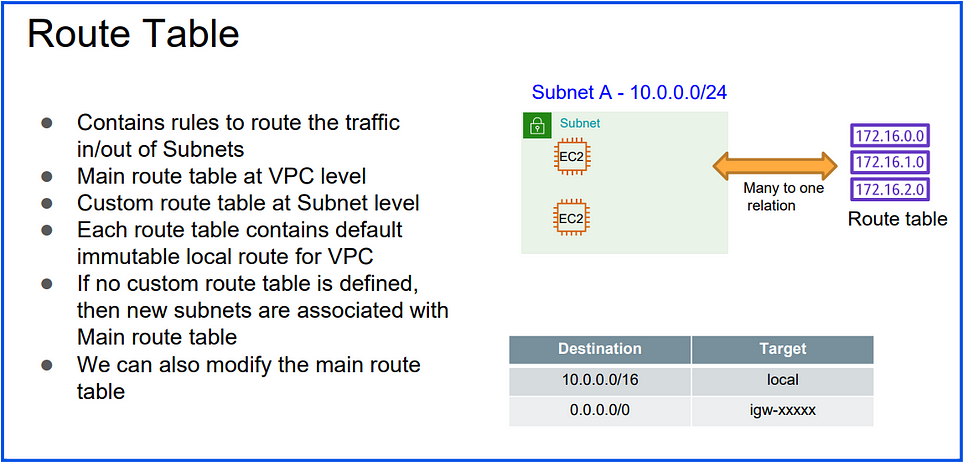
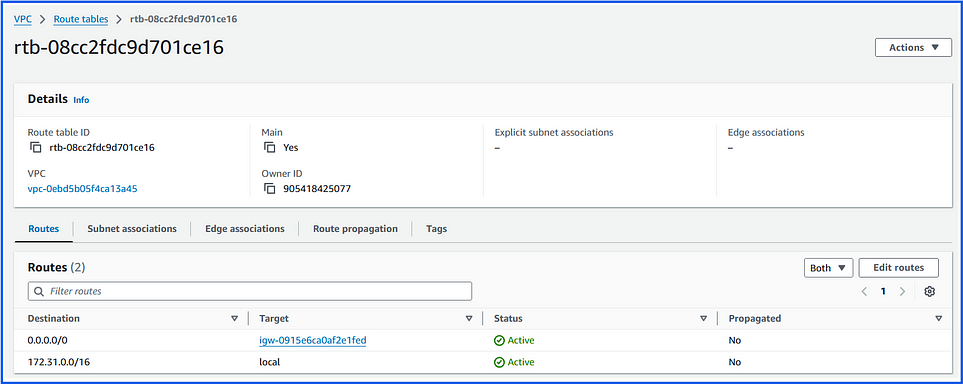
3. Route Tables:
Subnets are associated with route tables, which control the routing of traffic within and outside the VPC.
Public subnets typically have routes pointing to an Internet Gateway, while private subnets use a NAT Gateway or stay isolated.
— — — — — — — — — — — — — — — — — — — — — — — — — — — — — — — —
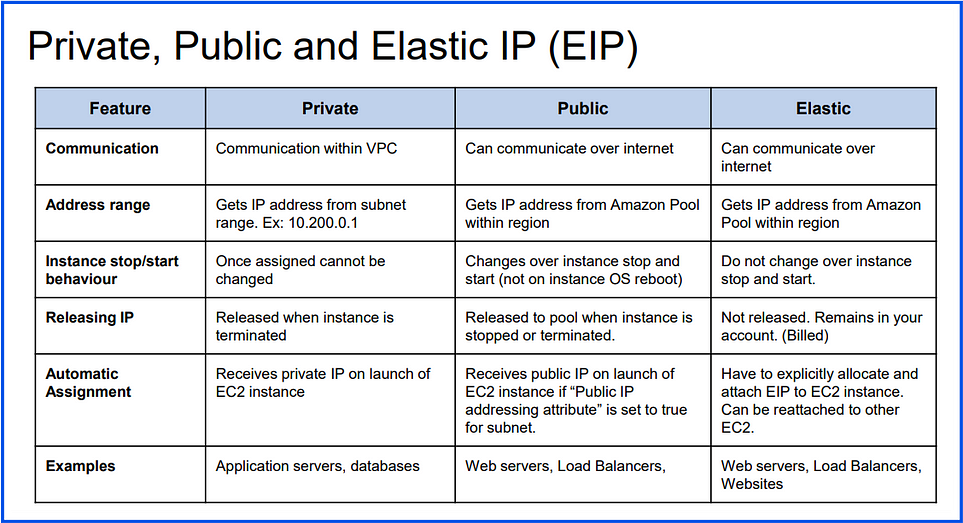
Public IP and Private IP are two types of IP addresses commonly used in networking.
Public IP:
Definition: A globally unique IP address that is accessible over the internet.
Usage: Used for devices or resources (e.g., web servers) that need to communicate with external networks or the internet.
Assignment: Assigned by ISPs or cloud providers, ensuring uniqueness worldwide.
Example Range: Any IP outside private IP ranges, like
8.8.8.8(Google DNS).Visibility: Visible to anyone on the internet.
Private IP:
Definition: An IP address used within a private network, not directly accessible from the internet.
Usage: Used for internal communication within a network (e.g., between devices in a company’s local network or within a VPC in the cloud).
Assignment: Defined by network administrators within specific IP ranges.
Reserved Ranges:
10.0.0.0 – 10.255.255.255(10.0.0.0/8)172.16.0.0 – 172.31.255.255(172.16.0.0/12)192.168.0.0 – 192.168.255.255(192.168.0.0/16)Visibility: Only accessible within the local network.
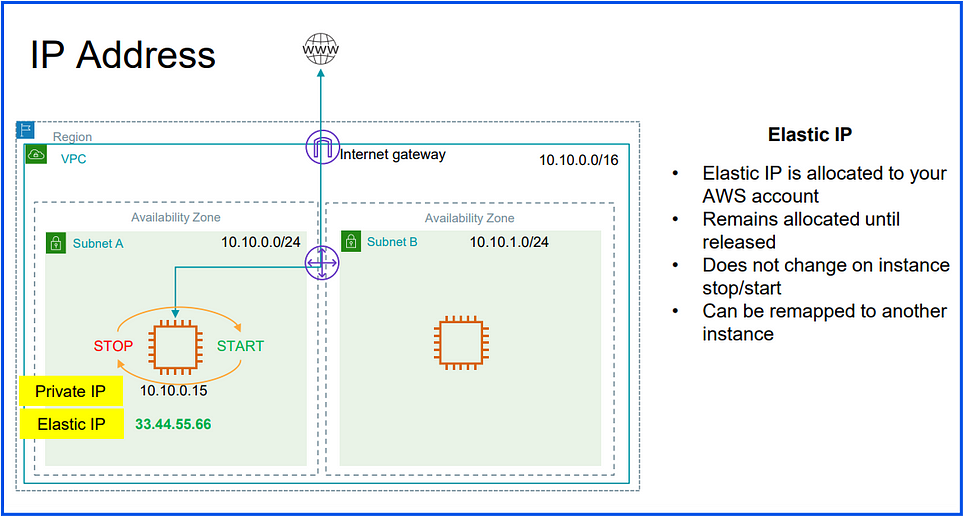
Elastic IP (EIP):
An Elastic IP (EIP) is a static, public IPv4 address in AWS:
Purpose: Provides a consistent IP for instances needing reliable public access (e.g., web servers).
Attachable: Can be reassigned to different instances for high availability and failover.
Costs: Free while associated with a running instance; charges apply for unused EIPs.
Limit: Typically limited to five per region per account.
4. Security Groups:
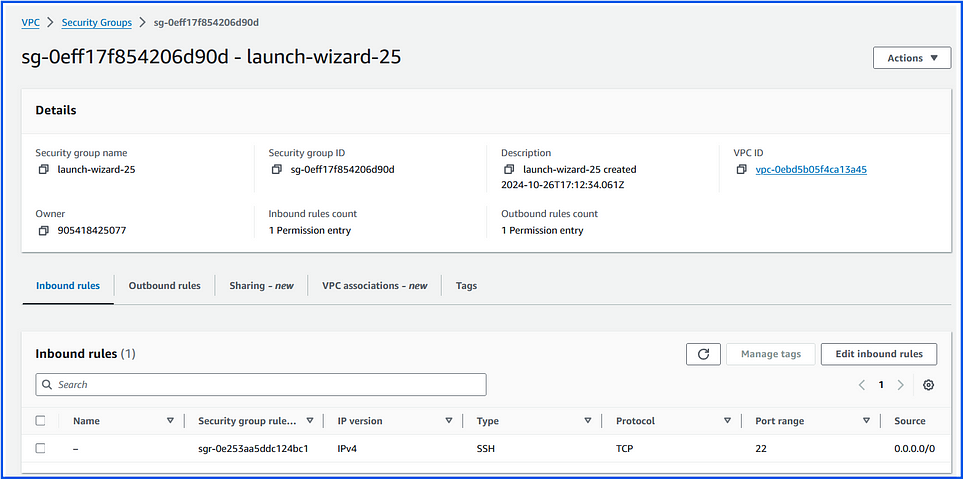
A Security Group in AWS is a virtual firewall for controlling inbound and outbound traffic to resources, such as EC2 instances, within a VPC.
Key Points:
Stateful: In simple terms, stateful means that if you allow a connection to go out, AWS automatically allows the response to come back in without needing an additional rule.
Inbound and Outbound Rules: Define allowed traffic based on IP addresses, protocols, and port ranges.
Instance-Level Security: Security groups are applied at the instance level, controlling traffic directly to the instance.
No Deny Rules: Only “allow” rules are specified; anything not explicitly allowed is implicitly denied.
Use Cases:
Access Control: Limit access to resources, e.g., allowing SSH only from specific IP addresses.
Network Segmentation: Separate application layers by using different security groups for web servers, databases, etc.
Here’s a text-based structural diagram to illustrate how network segmentation works in a three-tier architecture using security groups for each layer:
Internet
│
│
┌────────▼────────┐
│ SG-Web (Web) │
│-----------------│
│ Inbound: │
│ - HTTP (80) │
│ - HTTPS (443) │
│ Outbound: │
│ - To SG-App │
└───────▲─────────┘
│
│
┌───────┴─────────┐
│ SG-App (App) │
│-----------------│
│ Inbound: │
│ - From SG-Web │
│ - (e.g., port │
│ 8080) │
│ Outbound: │
│ - To SG-DB │
└───────▲─────────┘
│
│
┌───────┴─────────┐
│ SG-DB (DB) │
│-----------------│
│ Inbound: │
│ - From SG-App │
│ - (e.g., port │
│ 3306) │
│ Outbound: │
│ - Restricted │
└─────────────────┘
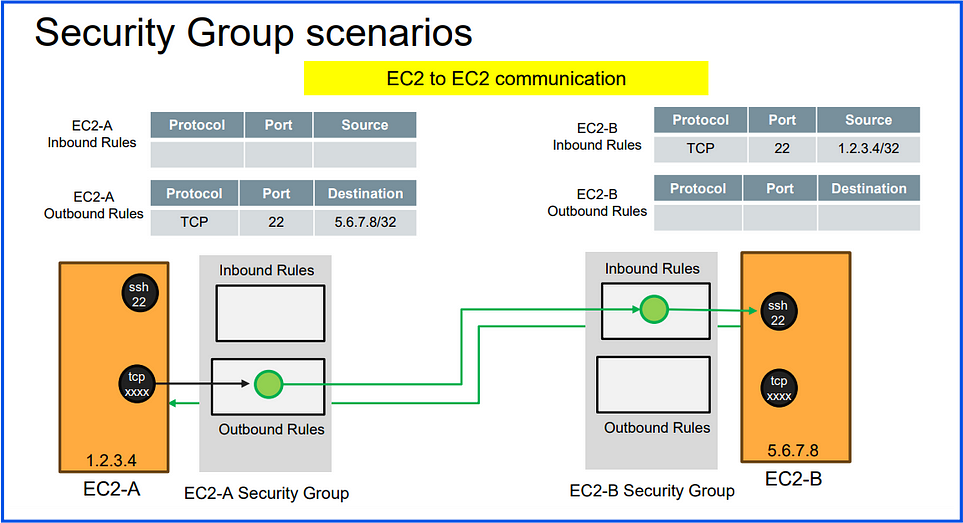
Summary for the above diagram:
EC2-A can initiate SSH connections to EC2-B due to the configured outbound rule on EC2-A’s security group and the inbound rule on EC2-B’s security group.
EC2-B allows SSH access only from EC2-A.
No other instances can SSH into these EC2 instances due to the specific source IP restrictions.
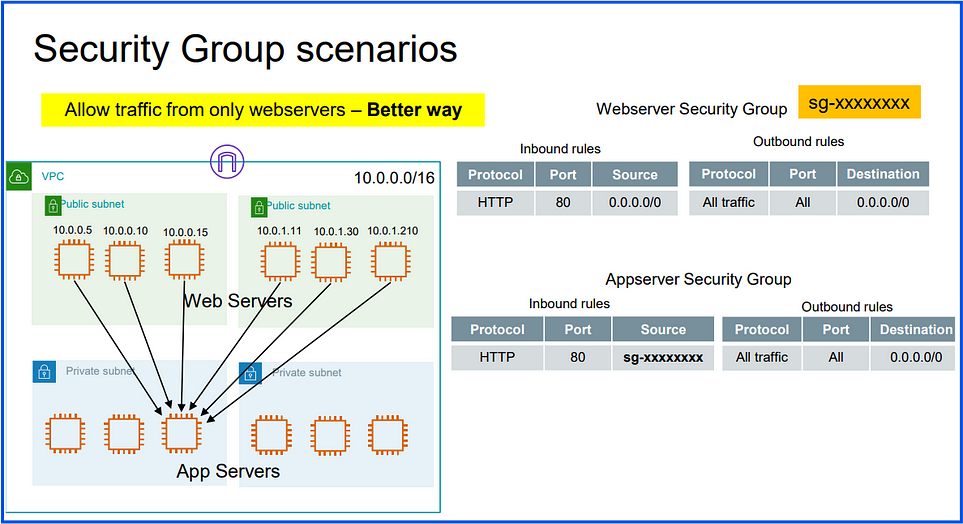
Web Server Security Group:
- Allows HTTP (port 80) traffic from any IP (
0.0.0.0/0), same as before.
App Server Security Group:
Uses the Web Server Security Group ID (SG-xxxxxxxx) as the source in its inbound rule for HTTP (port 80).
This allows any instance in the Web Server Security Group to communicate with the App Servers, making it more scalable and manageable.
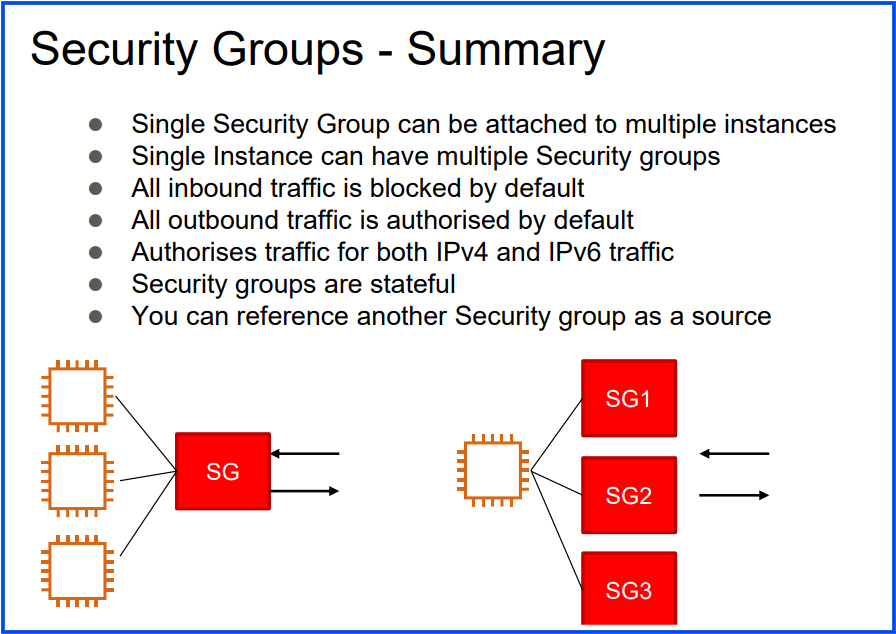
- A single Security Group (SG) can be attached to multiple instances in AWS.
Example: If you have a group of web servers that all require the same HTTP (port 80) and SSH (port 22) access, you can attach a single security group with these rules to each of those instances instead of creating separate security groups for each one.
2. A single EC2 instance can have multiple Security Groups attached to it.
Example:
Security Group A: Allows HTTP (port 80) traffic from the internet.
Security Group B: Allows SSH (port 22) traffic only from a specific IP.
Result: The instance will allow both HTTP and SSH access based on the rules from both security groups.
Security Group Default Behavior:
Inbound Traffic: Blocked by default (no access).
Outbound Traffic: Allowed by default (full access).
In summary, Security Groups are designed to allow traffic, not block it selectively. For finer-grained control, especially to block certain IP addresses, Network ACLs are the better tool.
VPC Firewall — Network ACLs
5. Network ACL:
A Network Access Control List (Network ACL or NACL) in AWS is a stateless firewall that controls inbound and outbound traffic at the subnet level within a VPC.
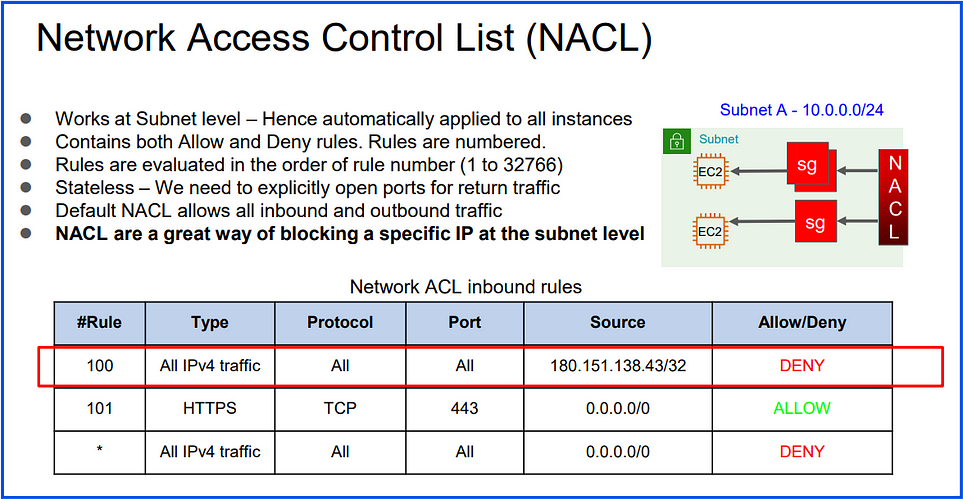
Key Points:
Subnet-Level Control: Network ACLs apply to all instances within a subnet, providing an additional layer of security on top of security groups.
Stateless: Unlike security groups, NACLs are stateless, meaning both inbound and outbound rules need to be defined explicitly. Traffic allowed in one direction must also be allowed in the opposite direction.
Rules Evaluation Order: NACL rules are evaluated in numerical order, starting from the lowest rule number. The first rule that matches the traffic will be applied, allowing you to prioritize rules.
Allow and Deny Rules: Network ACLs support both allow and deny rules, giving more granular control over traffic compared to security groups (which only allow traffic).
Default NACL: Each VPC has a default NACL, which allows all inbound and outbound traffic by default. Custom NACLs deny all traffic by default unless specific rules are added.
Example Use Case:
- You can use a NACL to block specific IP addresses (e.g., known malicious IPs) at the subnet level, while allowing other trusted traffic through.
Example of Network ACL in AWS:
Suppose you have a subnet in your VPC that contains multiple EC2 instances, and you want to apply additional security at the subnet level.
Requirement:
Allow all HTTP (port 80) traffic from any IP address.
Allow all HTTPS (port 443) traffic from any IP address.
Block all traffic from a specific IP address, 203.0.113.50,
which is known to be malicious.
NACL Rules:
Inbound Rules:
Rule #100: Allow HTTP (port 80) from 0.0.0.0/0
Rule #110: Allow HTTPS (port 443) from 0.0.0.0/0
Rule #120: Deny all traffic from 203.0.113.50/32
Outbound Rules:
Rule #100: Allow all outbound traffic to 0.0.0.0/0
Effect:
All EC2 instances in the subnet can receive HTTP and HTTPS traffic from any IP, except 203.0.113.50.
All outbound traffic is allowed from the subnet.
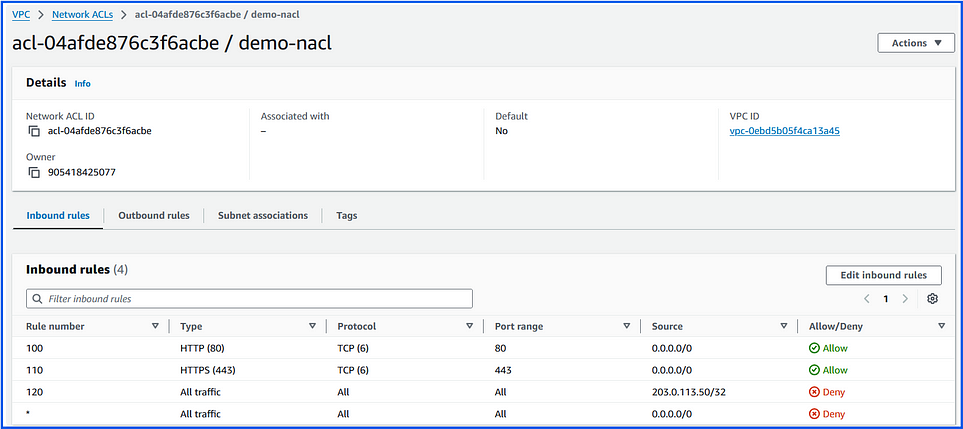
The order of execution for Network ACL (NACL) rules in AWS follows the rule number order, starting from the lowest number. AWS evaluates each rule in ascending order and applies the first rule that matches the traffic.
Execution Order:
Rule #100 is checked first. If the traffic is HTTP on port 80 from any IP, it’s allowed.
Rule #110 is checked next. If the traffic is HTTPS on port 443 from any IP, it’s allowed.
Rule #120 is checked next. If the traffic is from IP
203.0.113.50, it’s denied regardless of the protocol or port.Default Rule (*) is checked last. If the traffic doesn’t match any of the above rules, it’s denied.
Note: Rule #100 is the highest-priority rule because it’s evaluated first. Lower rule numbers indicate higher priority in NACLs.
Final Outcome:
Allowed: HTTP (80) and HTTPS (443) from any IP except
203.0.113.50.Denied: All other traffic and any requests from
203.0.113.50.
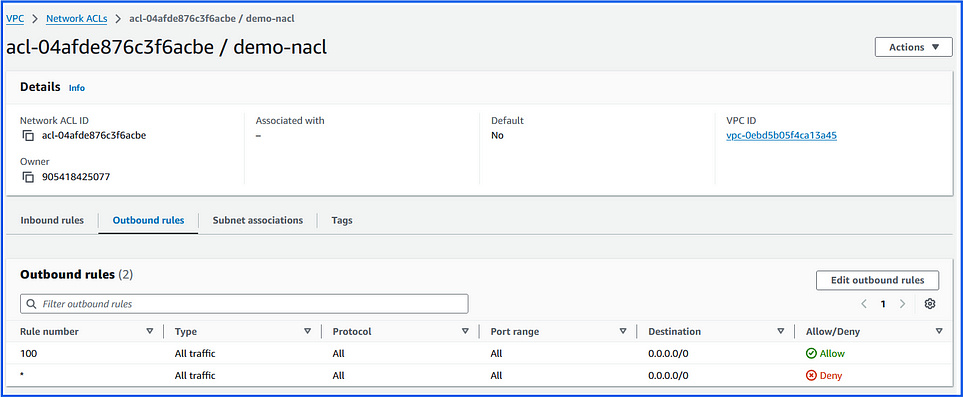
Final Outcome:
All outbound traffic from this subnet is allowed to any IP because of Rule #100. The default deny rule has no effect here since it’s only applied if no prior rules allow the traffic.
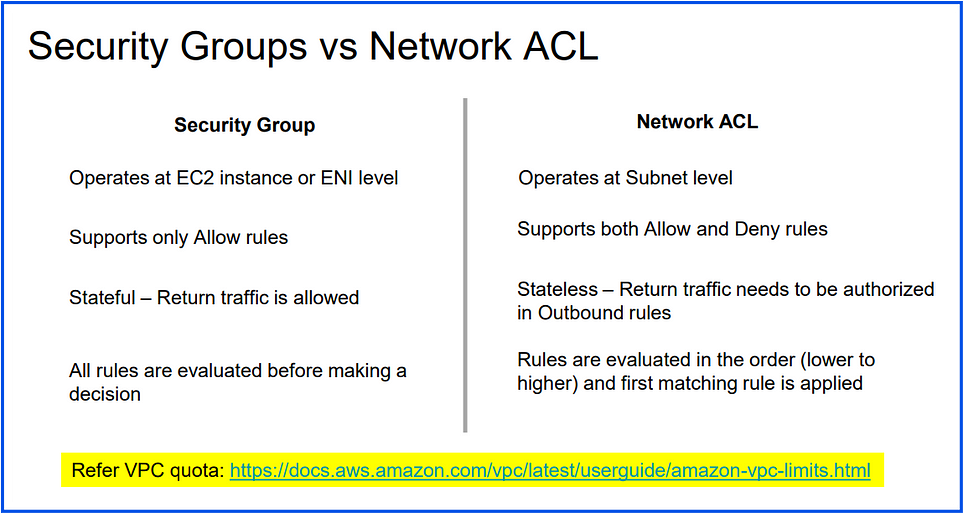
Security Groups vs Network ACL:
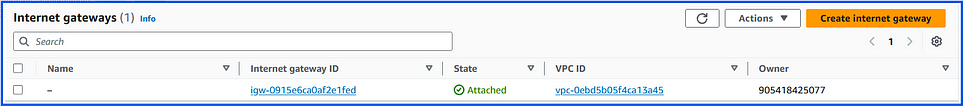
6. Internet Gateway:
An Internet Gateway (IGW) is a component in AWS that allows resources in a VPC (Virtual Private Cloud) to connect to the internet.
Key Points:
Public Access: It enables instances in public subnets to send and receive traffic from the internet.
One Per VPC: Each VPC can have one IGW attached.
Route Table: To direct traffic to the internet, the public subnet’s route table must have a route to the IGW.
Example:
Set Up:
=> You have an EC2 instance in a public subnet.
=> Attach an Internet Gateway to the VPC.
=> Update the route table for the public subnet to route
all traffic (0.0.0.0/0) to the IGW.
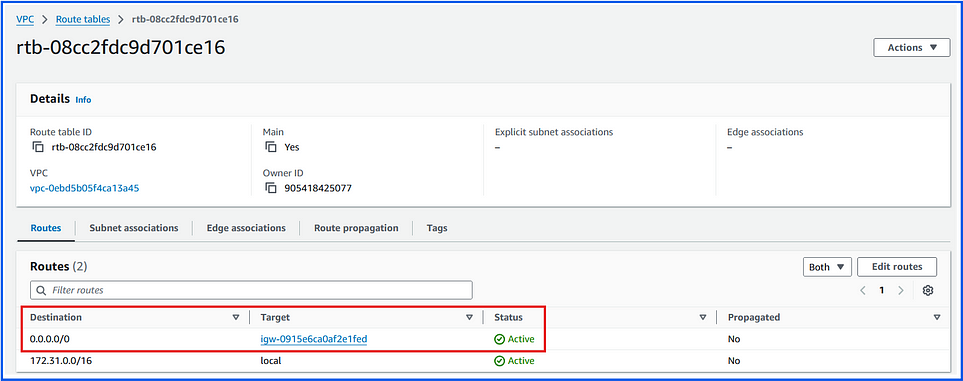
Result:
- The EC2 instance can now access the internet (e.g., browse websites or receive external requests) and be accessed from outside if security rules allow it.
Thank you and Happy learning!
Subscribe to my newsletter
Read articles from Subbu Tech Tutorials directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by
