Cyber Defense Frameworks: Cyber Kill Chain (TryHackMe)
 Jebitok
Jebitok
In this article, I will write a Cyber Kill Chain write-up: The Basics that covers Reconnaissance, Weaponization, Delivery, Exploitation, Installation, Command & Control (C&C), Action on Objectives (Exfiltration), and Practice Analysis.
What is the name of the Intel Gathering Tool that is a web-based interface to the common tools and resources for open-source intelligence?
OSINT FrameworkWhat is the definition for the email gathering process during the stage of reconnaissance?
email harvestingThis term is referred to as a group of commands that perform a specific task. You can think of them as subroutines or functions that contain the code that most users use to automate routine tasks. But malicious actors tend to use them for malicious purposes and include them in Microsoft Office documents. Can you provide the term for it?
MacroWhat is the name of the attack when it is performed against a specific group of people, and the attacker seeks to infect the website that the mentioned group of people is constantly visiting?
Watering hole attackCan you provide the name for a cyberattack targeting a software vulnerability that is unknown to the antivirus or software vendors?
Zero-day
According to FireEye, "the zero-day exploit or a zero-day vulnerability is an unknown exploit in the wild that exposes a vulnerability in software or hardware and can create complicated problems well before anyone realizes something is wrong. A zero-day exploit leaves NO opportunity for detection at the beginning."
These are examples of how an attacker carries out exploitation:
- The victim triggers the exploit by opening the email attachment or clicking on a malicious link.
- Using a zero-day exploit.
- Exploit software, hardware, or even human vulnerabilities.
- An attacker triggers the exploit for server-based vulnerabilities.
Can you provide the technique used to modify file time attributes to hide new or changes to existing files?
TimestompingCan you name the malicious script planted by an attacker on the webserver to maintain access to the compromised system and enables the webserver to be accessed remotely?
Web shellWhat is the C2 communication where the victim makes regular DNS requests to a DNS server and domain which belong to an attacker.
DNS TunnelingCan you provide a technology included in Microsoft Windows that can create backup copies or snapshots of files or volumes on the computer, even when they are in use?
Shadow CopyWe really hope you enjoyed this room. In order to strengthen your knowledge, let's do a practice analysis.

Here is the real-world scenario for you to tackle:
The infamous Target cyber-attack, which led to one of the largest data breaches in history took place on November 27, 2013.
On December 19th, 2013, Target released a statement confirming the breach, stating that approximately 40 million credit and debit card accounts were impacted between Nov. 27 and Dec. 15, 2013. Target had to pay the fine of $18.5 million under the terms of the multistate settlement agreement. This is considered to be the largest data-breach settlement in history.
How did the data breach happen? Deploy the static site attached to this task and apply your skills to build the Cyber Kill Chain of this scenario. Here are some tips to help you complete the practical:
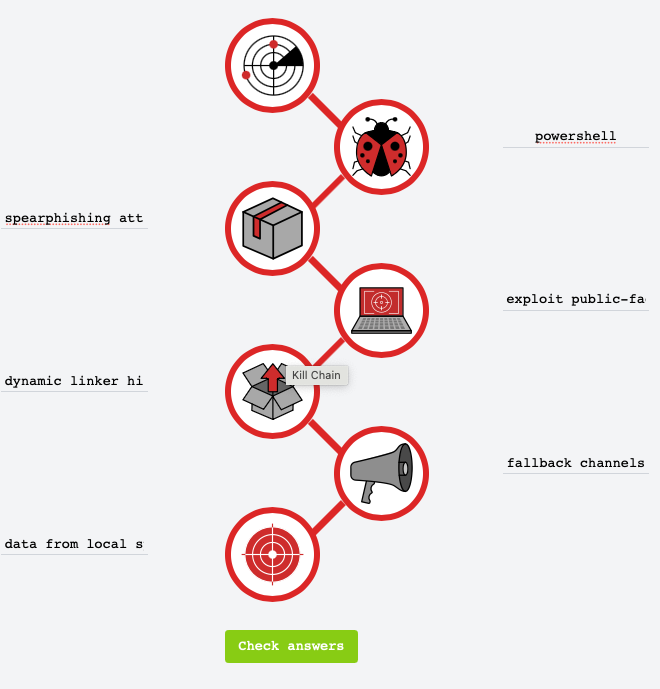
1. Add each item on the list in the correct Kill Chain entry-form on the Static Site Lab:
exploit public-facing application
data from local system
powershell
dynamic linker hijacking
spearphishing attachment
fallback channels
2. Use the ‘Check answers’ button to verify whether the answers are correct (where wrong answers will be underlined in red).
Answer the questions below

What is the flag after you complete the static site?
THM{7HR347_1N73L_12_4w35om3}Weaponization: Powershell
Delivery: spearphishing attachment
Exploitation: exploit public-facing application
Installation: dynamic linker hijacking
Command & Control: fallback channels
Actions on Objectives: data from local system
(make sure there are no spaces at the end of words)
Thank you for reading my article. Please leave any questions or comments on improving my learning journey and the THM challenges.
Subscribe to my newsletter
Read articles from Jebitok directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Jebitok
Jebitok
Software Developer | Learning Cybersecurity | Open for roles * If you're in the early stages of your career in software development (student or still looking for an entry-level role) and in need of mentorship, you can reach out to me.