Introduction to Authentication and Authorization
 Derrick Munyole
Derrick Munyole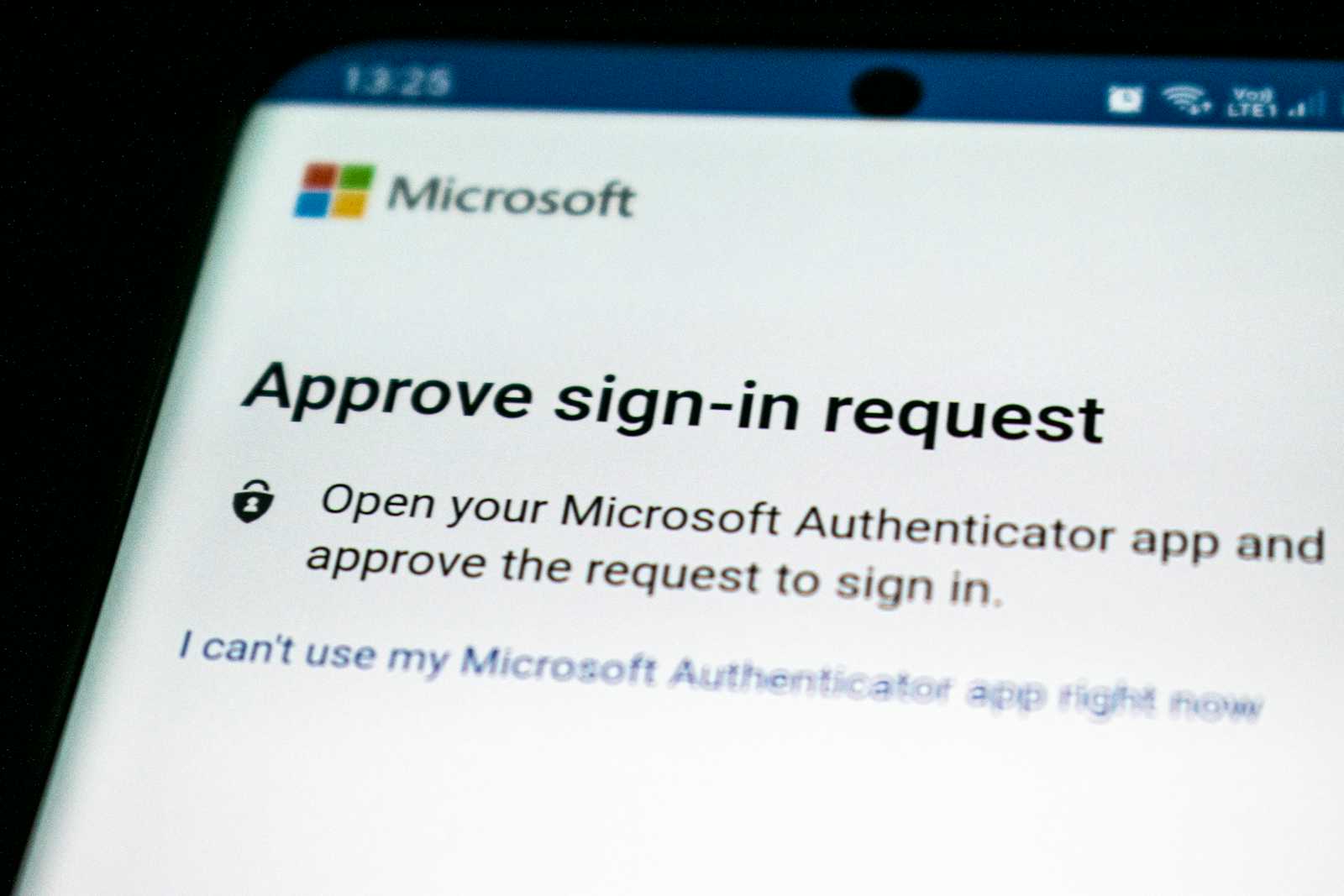

You’ve probably encountered the terms Authentication and Authorization while reading about the fascinating stories that keep popping up about Cyber Security, and your brain hurts. What the heck do they mean? And yes, they are two eerily similar words (I’m talking morphological similarity — care to look that up?😉); understanding these words will help you realize how they are the cornerstone of digital security.
What’s the difference anyway?
Good question. A helpful way of approaching this topic is in terms of the lock and key analogy, which we'll get into details shortly. It's a simple concept.

Thinking of authentication in terms of the lock and key analogy, the lock (authentication mechanism) verifies that the key (user) fits the lock. If this is the case, the user is granted entry. That’s authentication in a nutshell.
Authorization is a close twin to authentication, and thinking about the two gets most folks lost in the labyrinth. This is how they differ; even though your key fits the door, it may only open specific doors within the building (rooms). Therefore, Authorization determines which doors the user can enter within the building by checking their permissions. In the case of computer systems, you’d be thinking in terms of resources instead of buildings.
Let's take the example of an e-commerce website. You'll typically see authentication implemented as a login screen, which requires the user to input their email and password to validate that they are who they say they are. Authorization is slightly different. The e-commerce platform will also have an admin dashboard where the inventory and other aspects of the application can be managed. To access this page, the application checks whether the user is an admin or an ordinary user. In other words, in addition to being logged in, the user needs to have the admin role; otherwise, they can only see the pages accessible to general users.
Wait. That’s it?
Not exactly. There's more to authentication; not all authentication systems are created equal. Here are the different forms of authentication implemented in computing systems today:
Password-based authentication
Biometrics authentication
Token-based authentication
One-time password
Voice authentication (a type of biometric authentication)
Multi-factor authentication (MFA)
Certificate-based authentication
Push notifications

That's right. You may have encountered different variations of the above in your dominion over your digital realm. All hail to the king! (used in a totally gender-neutral, domain-ruling way, of course)
Just like your lordship should never be questioned, let's ensure your knowledge of the different authentication methods is never in doubt. Hunker down and prepare to learn about the variations in authentication implementation.

Ready to take the plunge, me lord?
Ready if you are… Let’s go!
Password-based authentication
Aah... the old classic and probably the most ubiquitous form of authentication. Password-based authentication is slowly paving the way for new and improved authentication systems like passkeys. The industry is steadily moving away from password-based authentication because of its inherent weaknesses. For example, many users reuse passwords across different services for convenience. Also, many users create weak passwords because they are easier to remember. The World Economic Forum published an interesting article on the world's most used passwords in 2024. Crazy, right? It's important to note that passwords will remain with us for some time. Therefore, it's necessary to learn how to manage your passwords. Stay tuned for an upcoming post on password management best practices to help with your digital hygiene.
Biometrics authentication
Biometrics authentication fascinates me. It reminds me of scenes from the myriad sci-fi movies I watched: a character approaches a door, and with a glance, the lock clicks open—no passwords, no hassles (It's hocus pocus, really). It just captures the unique imprint of their identity with astonishing accuracy! Welcome to the biometric authentication multiverse, courtesy of the Hogwarts Express, where your face, fingerprints, voice, or even your heartbeat become the keys to your digital empire. It is not merely sci-fi; some of your devices probably have a fingerprint reader.
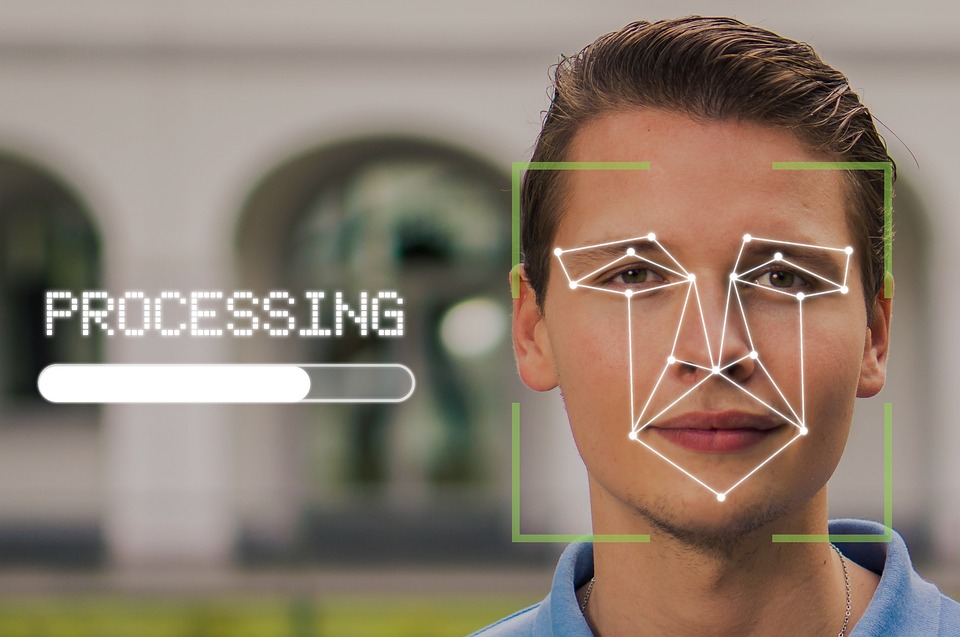
Example of biometric authentication by analyzing proportions of facial features courtesy of pixabay
Token-based authentication
Token-based authentication relies on security protocols that generate encrypted security tokens. When users visit a website and verify their identity (as earlier discussed), they receive an encrypted authentication token from the authenticating server, which the user's browser stores. For subsequent requests, the browser submits this token, which gives the user access to protected resources for a limited time, reducing the number of times the user re-authenticates with the system. It's the equivalent of being handed a gate pass to access secured areas. When you get to a place where your access needs to be confirmed, instead of presenting your ID, you only show your gate pass, which, if valid, will allow you to access the places. You don't waste time explaining yourself to gatekeepers (servers).

Tokens give you superpowers over authentication systems, and in Uncle Ben's famous last words:

and an expiration date! 😉
Manage them carefully. In the wrong hands, it spells Ragnarok.

One-time password
Also known as OTP codes, OTP codes are usually generated for specific sign-in events where the user receives a short code via SMS, email, or a hardware token. You've probably encountered this one when authenticating to your online banking account. The codes have a short validity period of about 30 seconds before expiring (sometimes can be as long as 1 hour). If the code the user provides matches, the system verifies that the user has the device. It's often combined with traditional passwords to add a second authentication layer.
Certificate-based authentication
Certificate-based authentication is typically used in government-based agencies and other areas of high-security requirements because of its effectiveness in physical environments. It relies on a digital certificate from cryptography to identify a user, device, or machine before being granted access to a resource. While some authentication methods are best suited for use by humans, certificate-based authentication has a broad spectrum of application areas, such as IOT devices, personal computers, servers, and e-passports. For example, computers in a network usually use certificates to identify each other across networks. While password-based authentication is based solely on what the user knows (password), certificate-based authentication also leverages what the 'user' has (for example, a private key). It's immune to common attack vectors like phishing, brute force (guessing), or social engineering attempts.
Multi-factor authentication (MFA)
As you might have guessed from the name, MFA is a verification technique where the user provides multiple pieces of proof, such as a password and a temporary code, to authenticate successfully. The most widespread form of MFA is two-factor authentication, where the user provides a code in addition to successfully submitting their username and password. However, more layers can be added according to security requirements to increase security. For example, in addition to submitting a username and password, users can be required to submit a one-time password and use an authenticator app or security tokens in the form of physical keys.
Push notification authentication
The push notification authentication method is also an interesting take on passwordless authentication. Like the passkeys, it's commonly implemented as a second-factor authentication method in most systems (like the popup notification on your phone when logging into Gmail and other Google services). In recent years, Microsoft has been pushing it as the primary means of authenticating to Microsoft services through its authenticator app. It's touted as a secure alternative to password authentication because an attacker needs to have direct access to the victim's mobile device to authenticate successfully.
Before I forget (a little bit on authorization)
You'll mostly encounter authorization in organizational instead of personal contexts. However, it's still important to understand the role (I touched on this earlier) and the different approaches to implementing authorization in computing systems.
Here's the low-down
As we defined earlier, authorization stipulates what a user (a person, application process, or system) can access. Authorization will typically take the form of levels similar to organizational structures; say you're a developer at an organization, and because you're not in a management position, you're not privy to some resources in the company. In the example, I mentioned developer, which is a role. In authorization systems, you'll typically have defined roles and get assigned a role based on your responsibilities in the company. Roles are pivotal features of authorization because they help implement the level of access. Unfortunately, I can't get into details without making the post too long, but if you're inclined, check out the different types of authorization.
And it's a wrap! We've looked at authentication and authorization and how they're foundational to digital security. We've also learned the standard authentication methods used in most computer systems. Grasping how authentication and authorization differ will build a solid start toward significantly improving digital security. Let's face it; it's the new world order.
Subscribe to my newsletter
Read articles from Derrick Munyole directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Derrick Munyole
Derrick Munyole
👋 Hi there! I'm Derrick Munyole—a computer science grad, Linux enthusiast, and software engineer with a heart for building impactful tech solutions. My journey in tech has taken me from creating software for underserved communities to deep dives into data processing, cloud computing, and AWS architecture. Right now, I’m focused on developing a versatile skill set: balancing hands-on coding and AI-assisted projects to sharpen my problem-solving skills and explore frameworks. I'm also working on portfolio projects that showcase my commitment to quality and creativity in development (hint: authentication, task management, and much more). In addition to code, I enjoy sharing my insights through technical blogs—where I break down complex concepts with a playful touch and relatable examples (think Hogwarts Express-level magic meets tech!). My goal is to make development accessible, meaningful, and just a little bit fun. When I'm not immersed in code, I'm likely optimizing Fedora, learning about kernel development, or prepping for my AWS Solutions Architect certification. All hail to the king of clean code and cool tech—let's build something amazing!