Understanding Randomized MAC Addresses for Better Privacy
 Mohammad Ariful Islam
Mohammad Ariful Islam
In today’s hyper-connected world, privacy is more important than ever. Devices we carry and connect with other networks leave digital traces wherever we go, making our privacy increasingly elusive. One way that our privacy can be protected is by employing the use of randomized MAC addresses that helps keep users anonymous in public and shared networks.
This article explores the concept of MAC addresses, how they can be useful to attackers and how randomized MAC addresses work to enhance our privacy. By the end, you’ll have a grasp on why this feature is important and how to explore it yourself through simple python code and network scanning.
What is a MAC Address?
A Media Access Control (MAC) address is a unique identifier assigned to the network interface of a device, which is essential for communication within a local network. It consists of 48 bits represented in hexadecimals, e.g., 00:1A:2B:3C:4D:5E. The first 24 bits, or three bytes, represent the OUI or Organizationally Unique Identifier. This segment identifies the device manufacturer, helping network equipment and administrators recognize the vendor of connected devices. Each manufacturer has a fixed OUI, and the rest of the bits are set so that they are never repeated for another device.
What is its purpose? Network communication, of course. Devices use MAC addresses to uniquely identify each other within the network to send and receive packets, allowing routers and switches to direct traffic to the correct destination.
How MAC Addresses can be valuable to threat actors?
While MAC addresses serve a crucial role in networking, they can also present a privacy risk when exposed to network sniffers. Attack can passively monitor the network to gather information about the network. Here’s how this works:
Attackers use tools like Wireshark to capture network traffic. In passive monitoring, they observe traffic without interacting with it which makes their presence difficult to detect.
They can identify unique device MAC addresses, gain insights into device types and manufacturers and track individual devices as they move between networks.
Over time, this allows attackers to create profiles of network activity and user habits, making it possible to perhaps identify and target a specific vulnerability in the network.
Using MAC addresses, specific devices can be tracked across networks, may be targeted if they have vulnerabilities and is a major privacy risk particularly in public networks.
What are Randomized MAC Addresses?
To introduce some form of anonymity for the user devices, device manufacturers have introduced randomized MAC addresses in wireless networks. This feature allows a device to create a new, temporary MAC address instead of using its built-in static address.
When a device connects to a Wi-Fi network, it generates a randomized MAC address based on certain network parameters, such as the network name (SSID) and security type. This generated address often stays the same for each unique network to maintain functionality, such as bypassing login screens or enabling parental controls. However, devices may periodically update or “rotate” their randomized MAC addresses to enhance security and prevent long-term tracking.
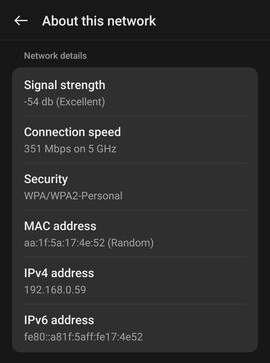
This process of MAC address randomization provides an additional layer of anonymity when devices connect to Wi-Fi networks. By frequently changing the MAC address, this feature prevents network observers from easily identifying devices, safeguarding user privacy in shared or public network environments.
Practical Example: Creating a Basic Network Scanner
To illustrate the use of randomized MAC Addresses, let’s explore a basic network scanner using Python using Scapy, a python library, to scan for connected devices and display their IP and MAC addresses. Before we get into the code:
Make sure your laptop/computer is connected via an ethernet cable.
Find your IP range using the command “ipconfig” in Windows command prompt or “ifconfig” in Linux.
Set your IP addressing to static instead of DHCP to identify your device in the results. For my android phone, I set the Ip address to 192.168.0.59.
from scapy.all import ARP, Ether, srp
import requests
def scan_network(ip_range):
# create an ARP request packet
arp = ARP(pdst=ip_range)
ether = Ether(dst="ff:ff:ff:ff:ff:ff")
packet = ether / arp
# send the packet and capture the response
result = srp(packet, timeout = 3, verbose=0)[0]
# parse the results
devices = []
for sent, received in result:
devices.append({'ip': received.psrc, 'mac': received.hwsrc})
return devices
def get_device_manufacturer(mac_address):
url = f"https://api.macvendors.com/{mac_address}"
try:
response = requests.get(url)
if response.status_code == 200:
return response.text
else:
return "Unknown"
except requests.RequestException:
return "Unknown"
if __name__ == "__main__":
network_devices = scan_network("192.168.0.0/24") # your network range
for device in network_devices:
device['manufacturer'] = get_device_manufacturer(device['mac'])
print(f"IP: {device['ip']}, MAC: {device['mac']}, Manufacturer:",
f" {device['manufacturer']}")
Explanation:
The
scan_networkfunction uses Scapy’s ARP and Ethernet classes to create a ARP broadcast packet and send to all devices within a specified IP range (e.g.,192.168.0.0/24). Each device responds with its IP and MAC address.For each device, the MAC address is sent to the macvendors.com API to identify the manufacturer. If the lookup is successful, the manufacturer’s name is returned.
The script prints the IP address, MAC address, and manufacturer (if available) for each device on the network.
Results:
The following results demonstrate that it is difficult to identify devices or gather more information about the hardware when randomized MAC addressing is used.
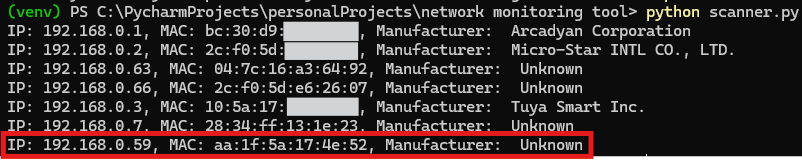
I have hidden part of the identified MAC addresses to protect privacy, but you can still see that the devices, or more specifically, the manufacturers of the network cards, have been identified.
The red-marked box highlights my device. The addresses match the Wi-Fi configurations shown in the previous section. However, note that the manufacturer could not be found for this device. Now, let’s change the MAC address on my Android device so that the original MAC address is used.
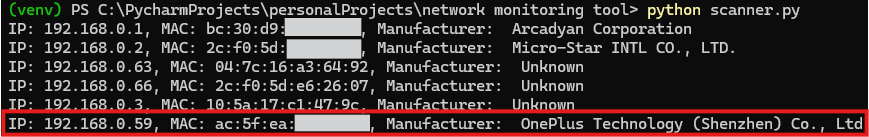
Setting my MAC address to static means that someone could identify that I am using a OnePlus device(with a bunch of vertical green lines). Just kidding.
Conclusion
I have to admit, I never even knew MAC address randomization was a feature until I decided to create a simple network scanner script to identify device types on my network—just for fun. As I was scanning and reviewing the results, something didn’t quite add up. The MAC addresses didn’t match up with what I expected. That’s when I stumbled upon the concept of randomized MAC addresses.
From this blog, here are a few key takeaways:
What MAC Addresses Are: MAC addresses are unique identifiers for devices on a network, and they can be used to track or identify devices across networks.
How Randomized MAC Addresses Work: Randomized MAC addresses add an extra layer of privacy by preventing network sniffers from tracking your device by its unique, static address.
The Role of Manufacturers: The MAC address reveals the manufacturer of the device, but with randomization, this is often hidden.
The Benefits for Privacy: Randomized MAC addresses make it much harder for attackers or advertisers to identify and track your devices across networks.
As we continue to explore MAC address randomization, it opens up a deeper question: Are there other ways we can remain anonymous and safeguard our privacy on public networks? With the increasing surveillance in our digital world, it’s worth considering how much control we really have over our online presence.
References
ProtonVPN. What is a MAC Address? Available at: https://protonvpn.com/blog/what-is-mac-address
CableLabs. MAC Address Randomization: How User Privacy Impacts Wi-Fi and Internet Service Providers. Available at: https://www.cablelabs.com/blog/mac-address-randomization-how-user-privacy-impacts-wi-fi-and-internet-service-providers
InterDigital. Random MAC Addresses for Better Wi-Fi Security and Privacy. Available at: https://www.interdigital.com/post/random-mac-addresses-for-better-wifi-security-and-privacy-
Android Source. Wi-Fi MAC Randomization Behavior. Available at: https://source.android.com/docs/core/connect/wifi-mac-randomization-behavior
Subscribe to my newsletter
Read articles from Mohammad Ariful Islam directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Mohammad Ariful Islam
Mohammad Ariful Islam
Cybersecurity enthusiast and co-founder of LiveCampus, pursuing a Master’s in Cybersecurity at RMIT. Exploring Python, Next.js, and Linux, and sharing my journey in tech, network security, and software development!