Knowing the AWS IAM
 Vasuki Janarthanan
Vasuki Janarthanan
Identity and Access Management (IAM) :
IAM users have a set of defined permissions that they can perform in the AWS account.
Who creates IAM users and Why?
Initially, when you create an AWS account, you are known as the root user. The root user has complete access to the aws account. They perform CRUD operations in their account.
Let’s say in your organization, you are the root user. And you want to give permission to members of your organization to perform their tasks. So you are creating an IAM user and giving them permissions or restrictions based on their tasks.
If you don’t create an IAM user, everyone in the organization will act as a root user, then there is no security for your resources. It may be deleted, modified so on. To resolve this challenge IAM user comes into play.
Policies :
Policies are a set of permissions that are associated with the user group. You can create your own policy in a JSON file. Where you can say what actions can be performed, and which resources can be allocated as a list of statements in that JSON file.
Groups :
Here we can group a set of members in an organization. Instead of attaching a policy to each user, we can create a group and we can attach or detach policies.
Ex: In our organization, we have “Developers” and “Operations” groups. We create IAM users and allocate them to their specific groups. After that attaching policies to the desired groups, instead of allocating policies to each user.
Roles :
On your behalf, AWS Services will take action. To do that we attaching policies to aws services with the IAM Roles.
Let’s do the demonstration :
- Go to the IAM services
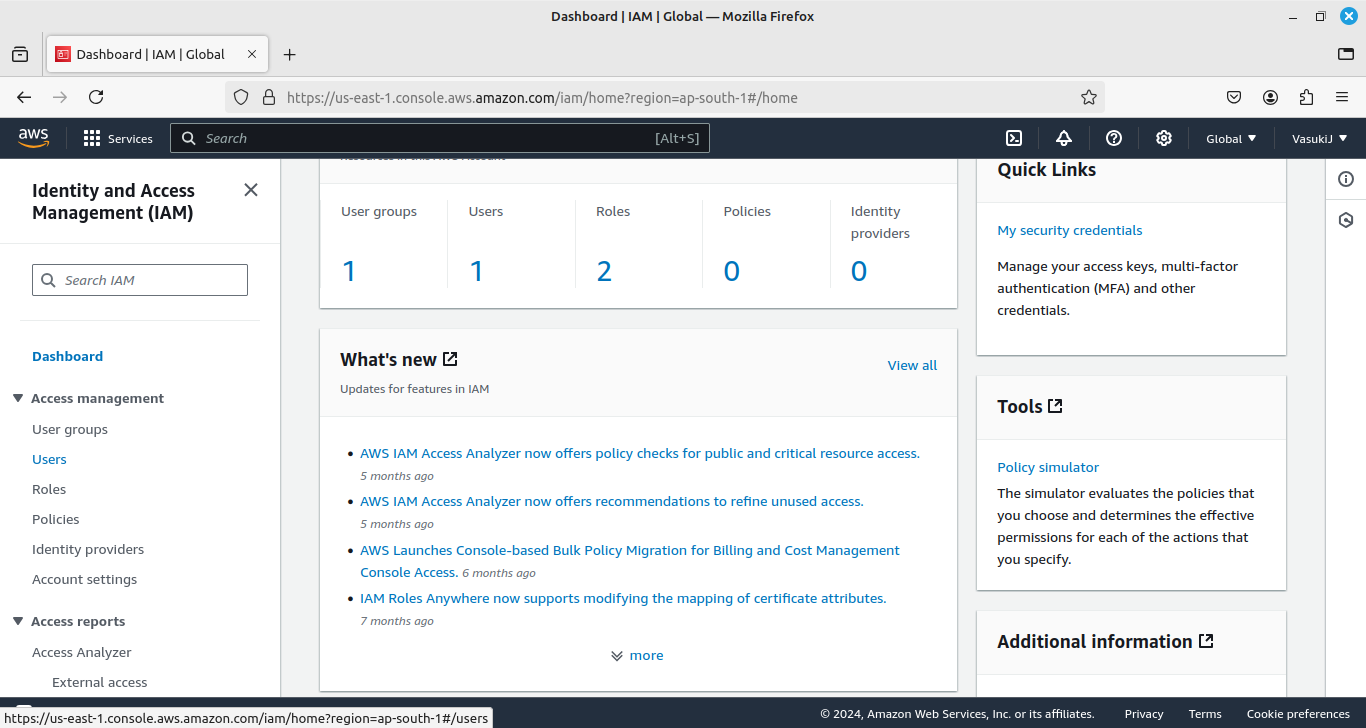
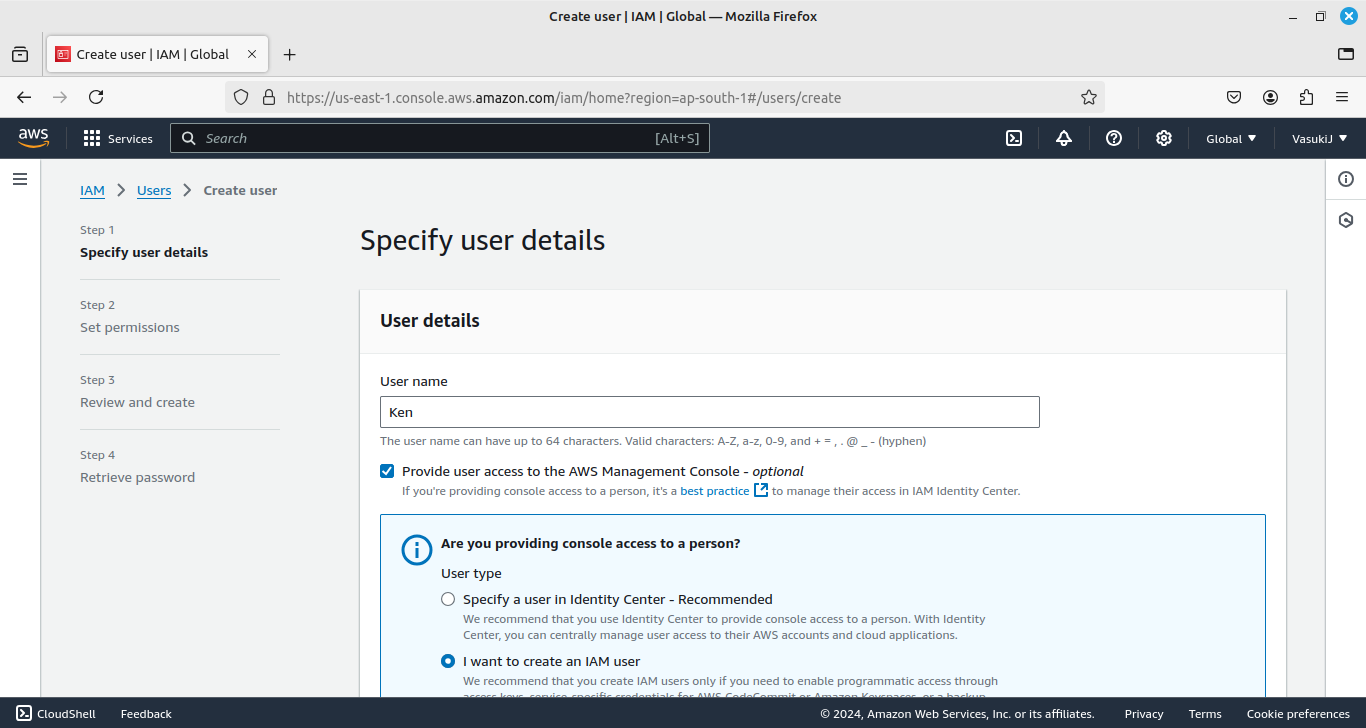
- Create an IAM User
- Create a Group named “Developers” and attach the “ec2’s ReadOnlyAccess” Policy.
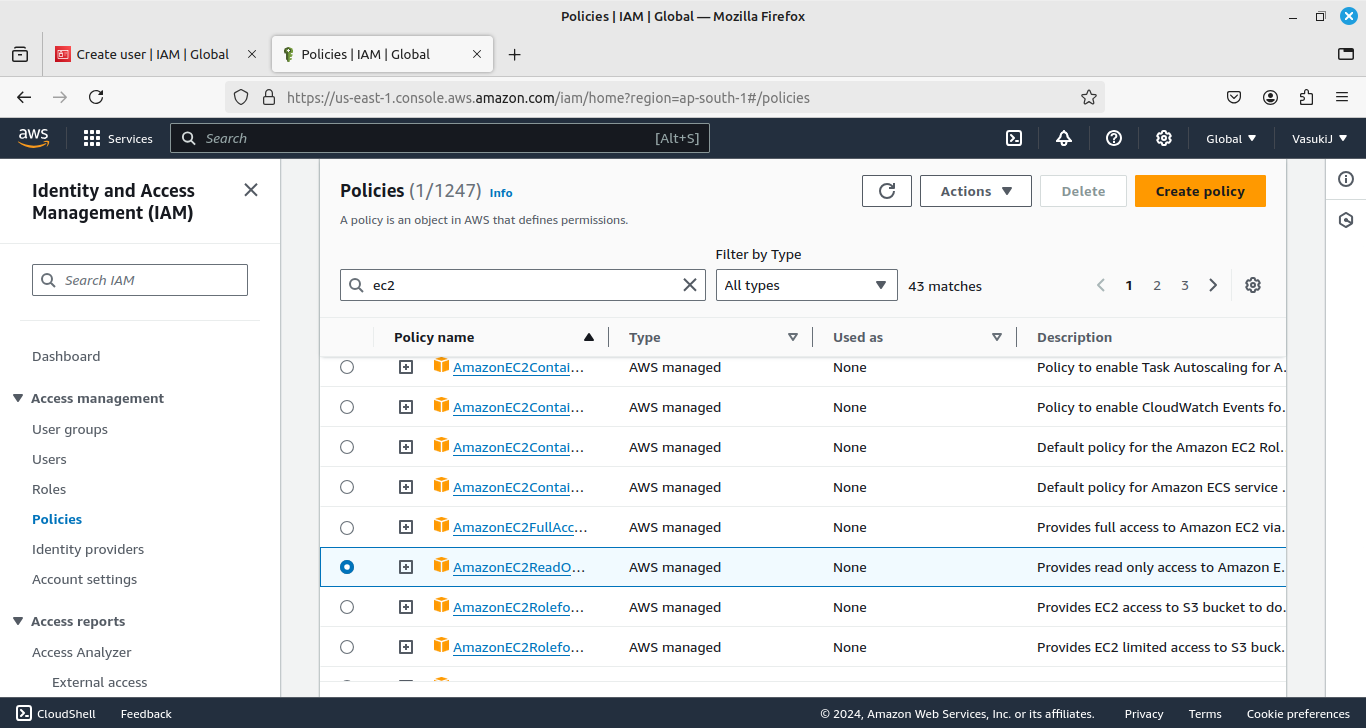
You can create the policy by clicking “Create Policy”. Then add Actions and resources for your policy.
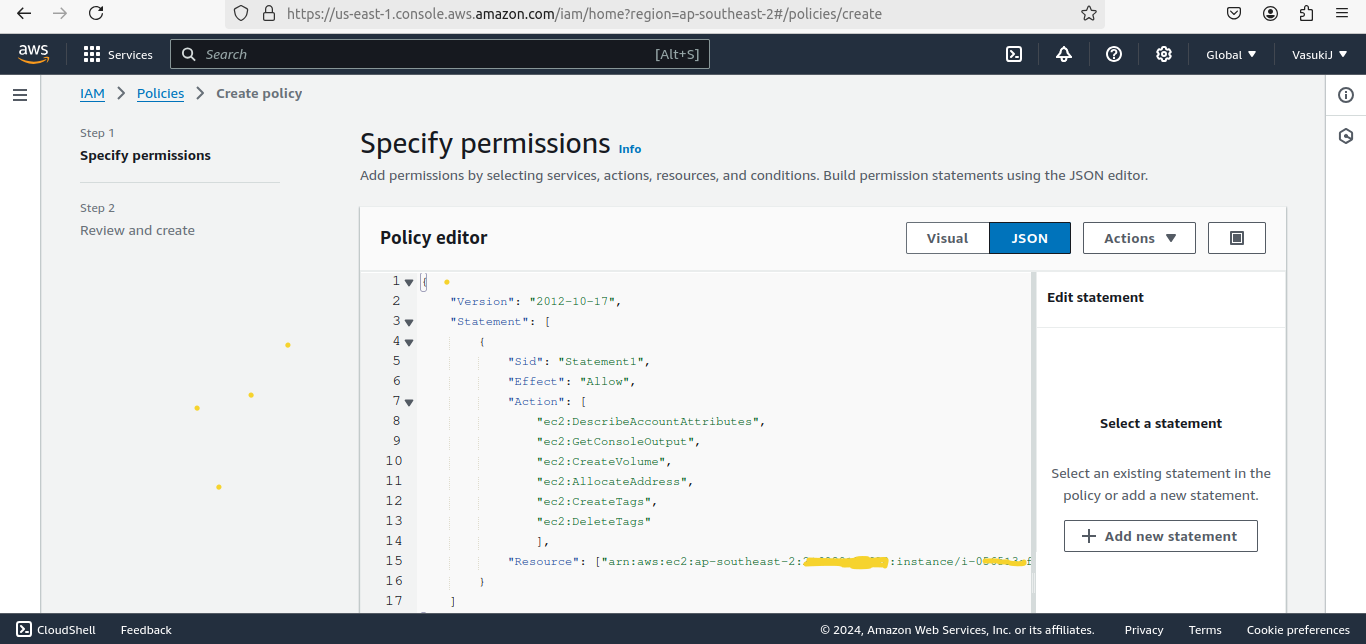
Here I defined permissions for some ec2’s actions.
Syntax for Resource :
"Resource": "arn:aws:ec2:region:account-id: instance/instance-id"
You can also use the Principal attribute for (account/user/role) to access this policy,
AWS account ID:
"Principal": { "AWS": "arn:aws:iam::123456789012:root" }
IAM users:
"Principal": { "AWS": "arn:aws:iam::123456789012:user/username" }
Role :
"Principal": { "AWS": "arn:aws:iam::123456789012:role/role-name" }
After that, we can also add a condition attribute for this policy.
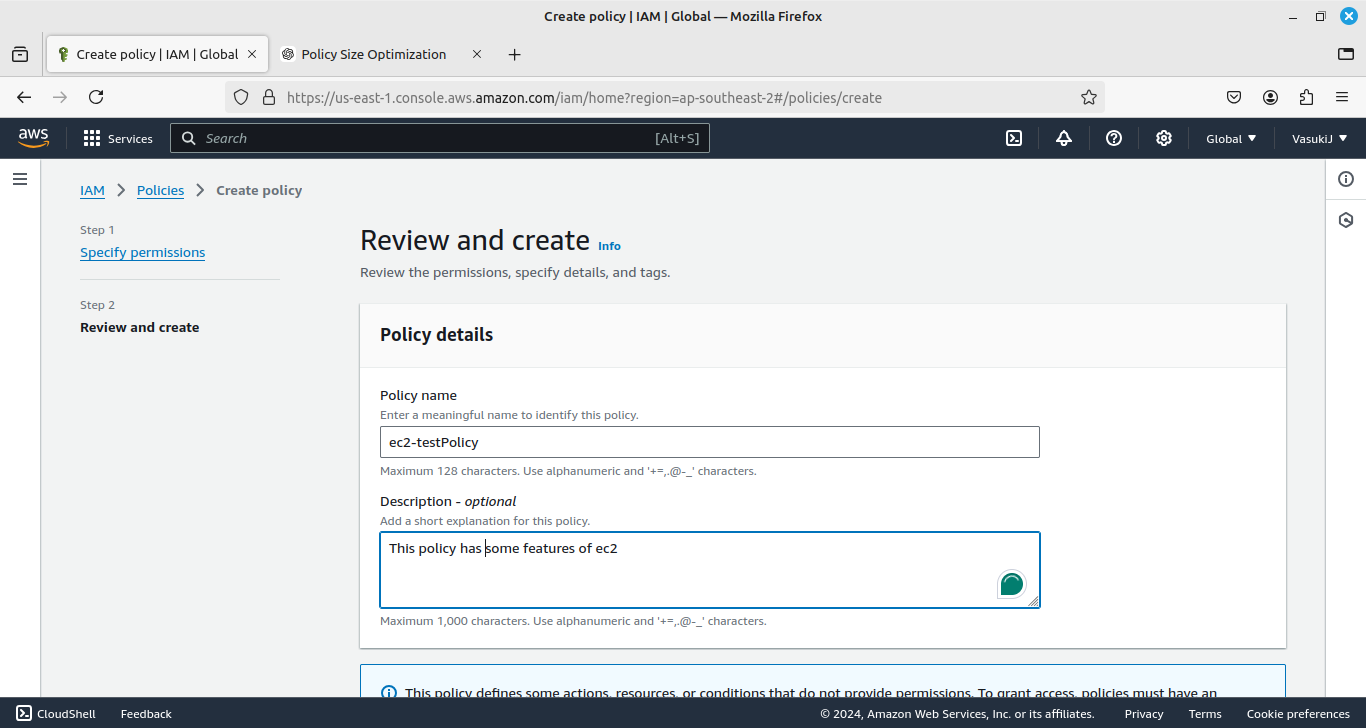
After defining the JSON file, then give the policy name and description.
- Then attach this policy to the “Developer” Group
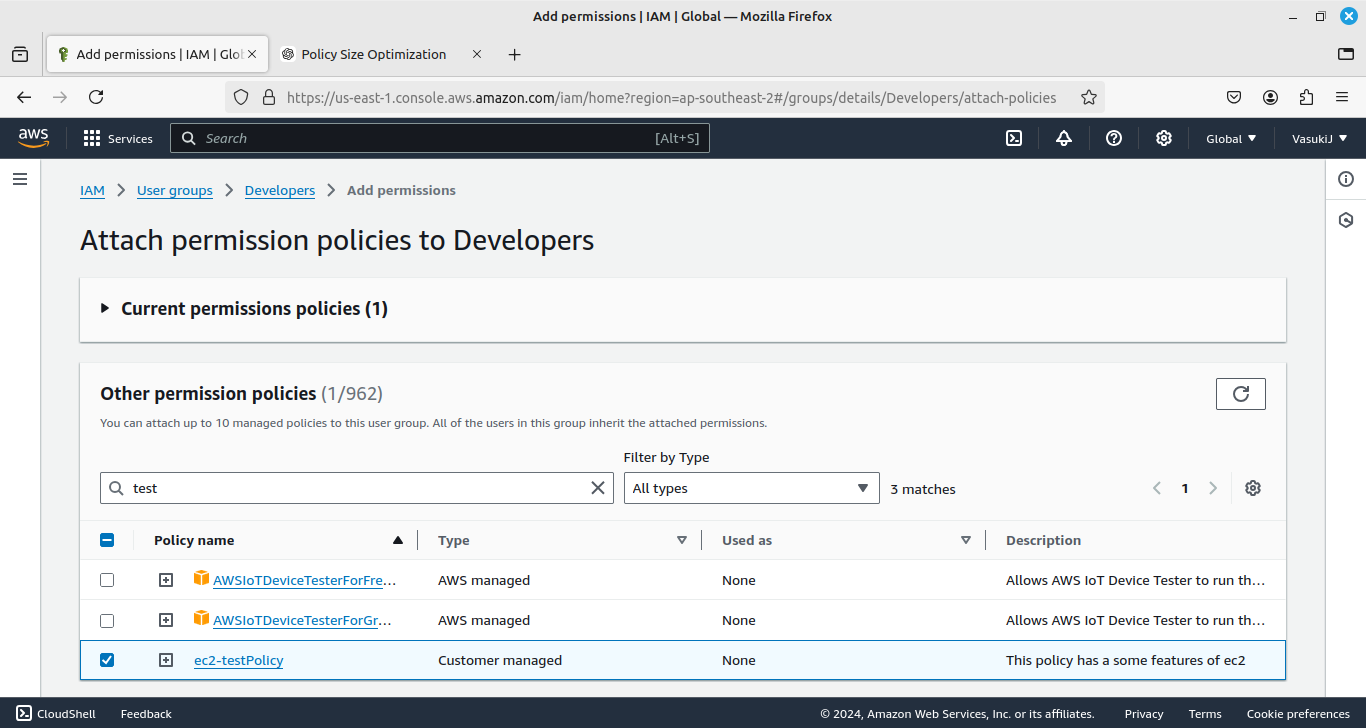
- Add IAM Users to the Developers Group.
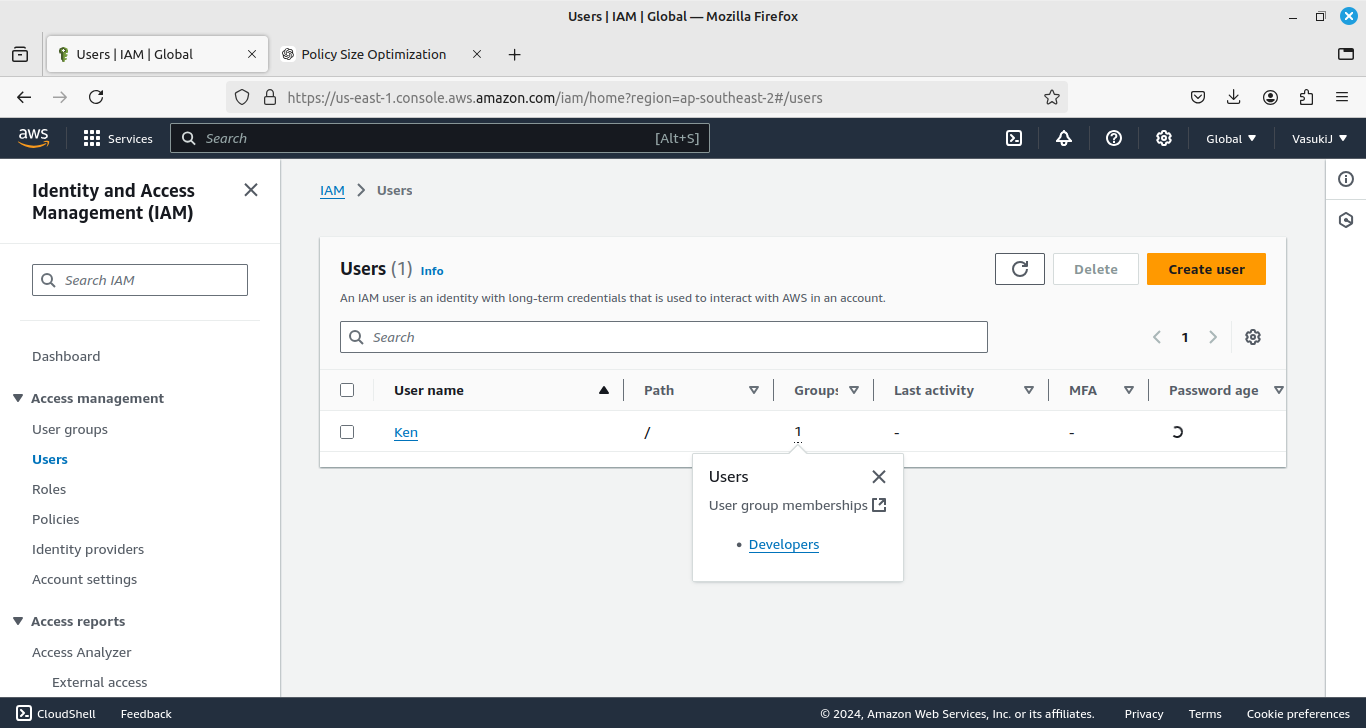
Then create some other groups, attach policies, and add users.
Now I create an admin and attach policy to the admin directly without creating a group.
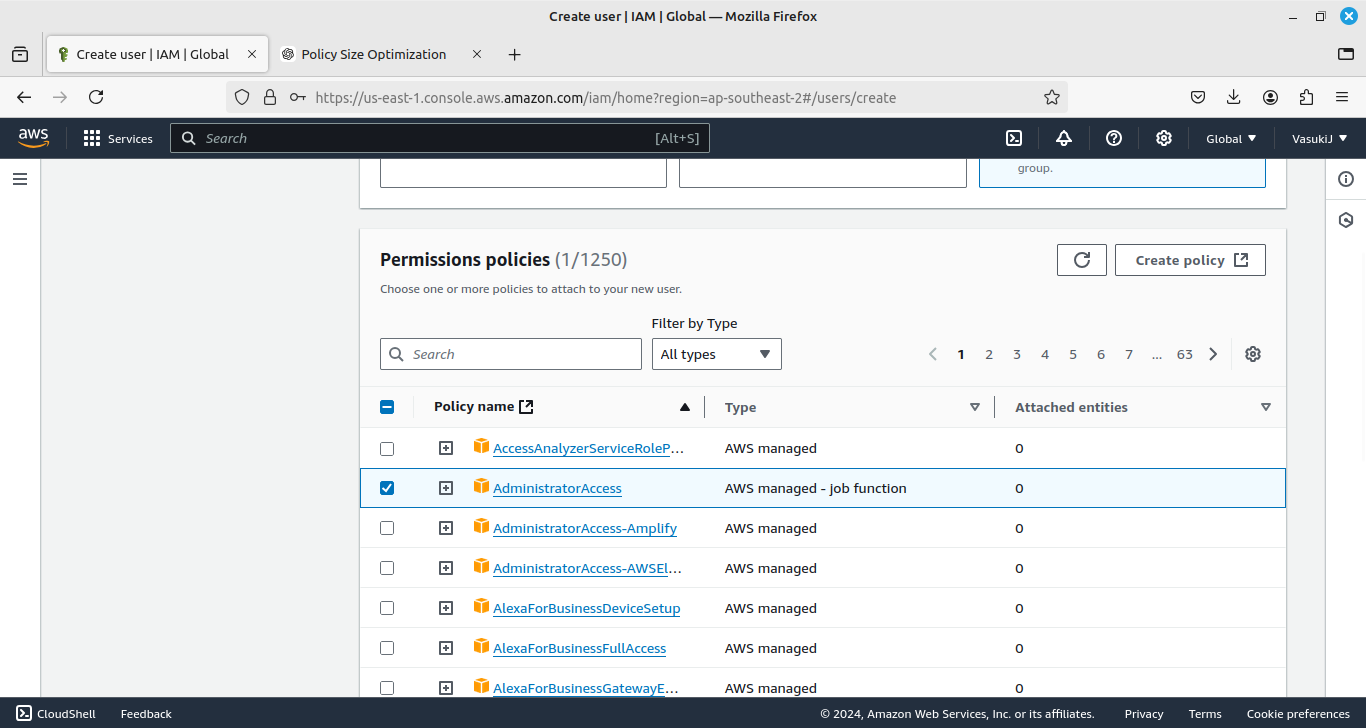
For admin, I attach a policy of “AdministatorAccess”.
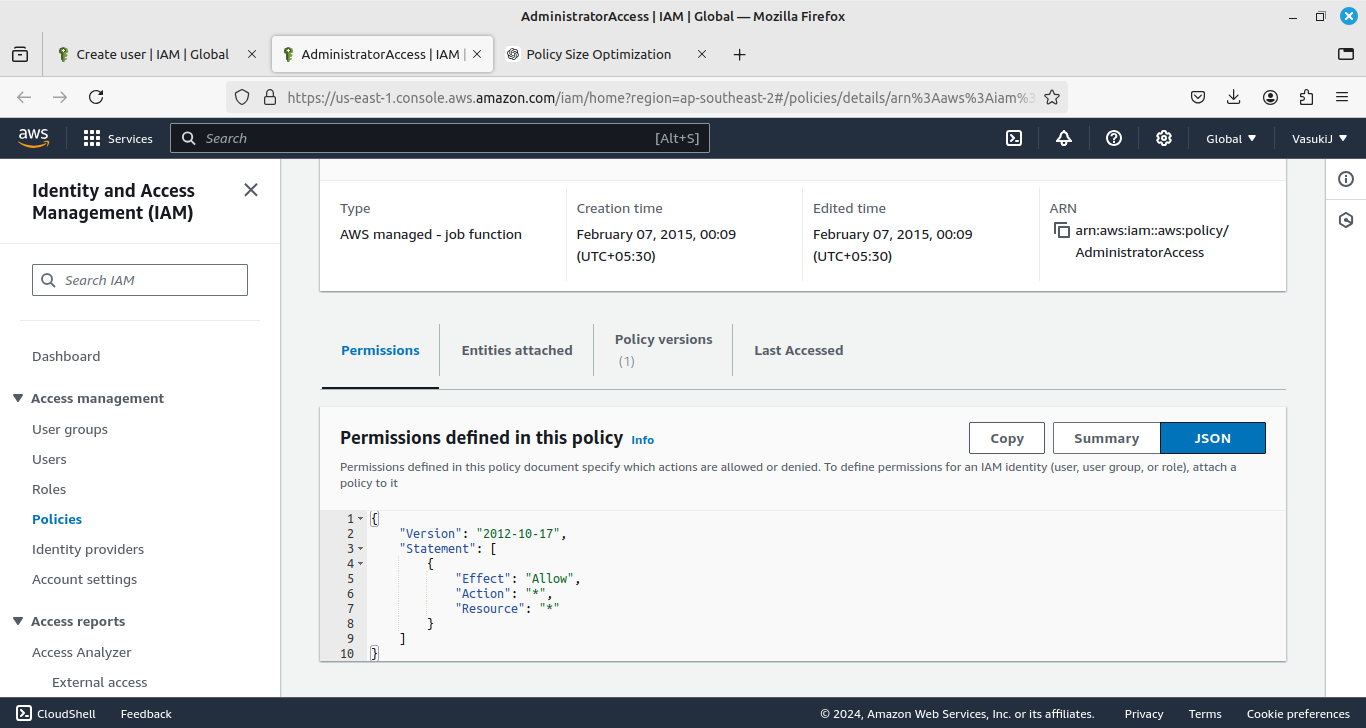
Look at this JSON file. Here, it will allocate all action and resources for this policy.
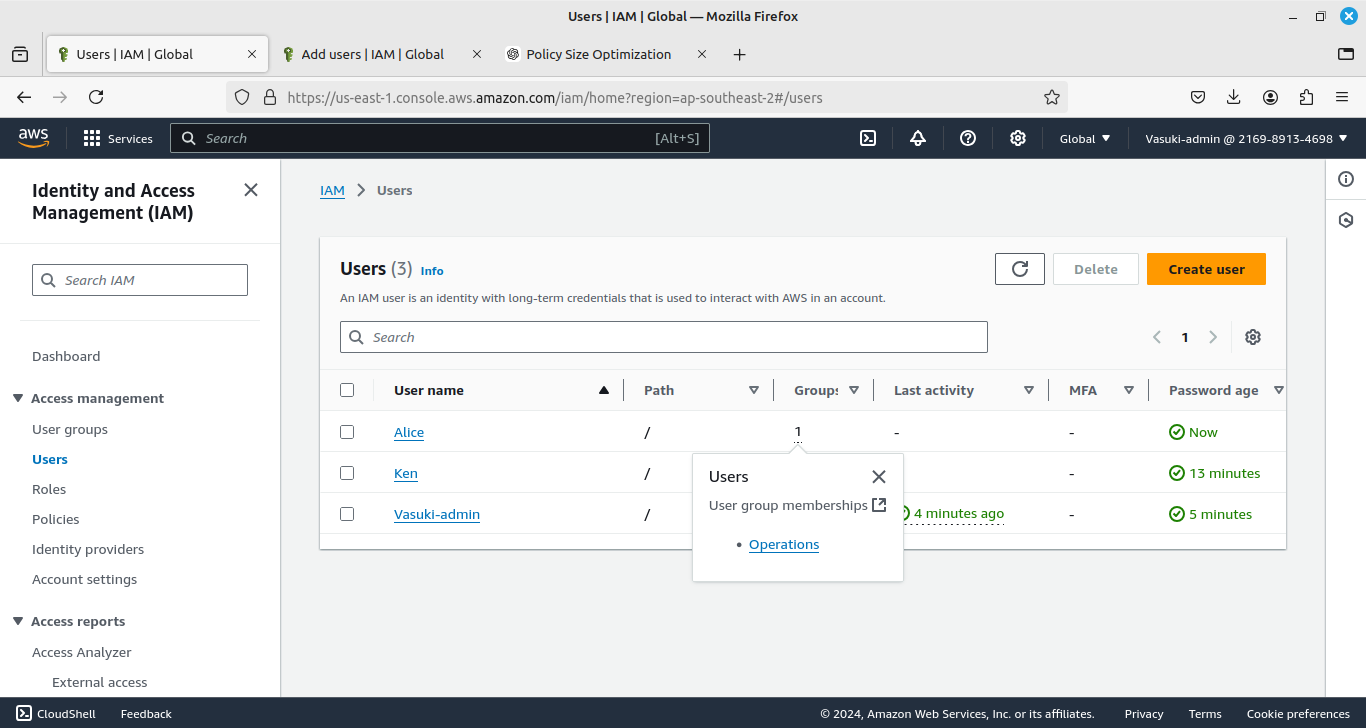
Now, we have created three IAM Users allocated them to their specific group, and given permissions for this task. Admin did not belong to any group and she has an AdministratorAccess policy.
Great! We actually explored the AWS IAM by HandsOn.
We now get to know idea about AWS IAM Users, groups, policies, and roles. How the policy will define permissions for IAM Users. By making groups we can easily attach or detach policies for all IAM Users. And roles will have policies for AWS services on behalf of the user to perform actions and all.
Thanking You!
Happy DevOps & Cloud Journey!...
Subscribe to my newsletter
Read articles from Vasuki Janarthanan directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Vasuki Janarthanan
Vasuki Janarthanan
While traveling on my DevOps Journey, I am sharing insights gained through experimenting with DevOps and Cloud practices.