Cyber Defense Frameworks: Diamond Model (TryHackMe)
 Jebitok
Jebitok
In this article, I will write a Diamond Chain write-up: The Basics that covers Adversary, Victim, Capability, Infrastructure, Event Meta Features, Socio-Political Component, Technology Component, and Practice Analysis.
What is the term for a person/group that has the intention to perform malicious actions against cyber resources?
Adversary OperatorWhat is the term of the person or a group that will receive the benefits from the cyberattacks?
Adversary CustomerWhat is the term that applies to the Diamond Model for organizations or people that are being targeted?
Victim PersonaeProvide the term for the set of tools or capabilities that belong to an adversary.
Adversary ArsenalTo which type of infrastructure do malicious domains and compromised email accounts belong?
Type 2 InfrastructureWhat type of infrastructure is most likely owned by an adversary?
Type 1 InfrastructureWhat meta-feature does the axiom "Every malicious activity contains two or more phases which must be successfully executed in succession to achieve the desired result" belong to?
PhaseYou can label the event results as "success", "failure", and "unknown". What meta-feature is this related to?
ResultTo what meta-feature is this phrase applicable "Every intrusion event requires one or more external resources to be satisfied prior to success"?
ResourcesAre you ready to construct the Diamond Model? Please, deploy the static site attached to this task and dive into the case study and extract the information needed to populate our Diamond Model.
(Please note: The case study for this room occurred in 2015, and is not in light of recent developments in Ukraine).
Answer the questions below
Ensure you have deployed the static site attached to this task. To complete the static site, you will need to click on each triangular section of the diamond until you have completed all eight areas of the diamond
Complete all eight areas of the diamond. What is the flag that is displayed to you?
THM{DIAMOND_MODEL_ATTACK_CHAIN}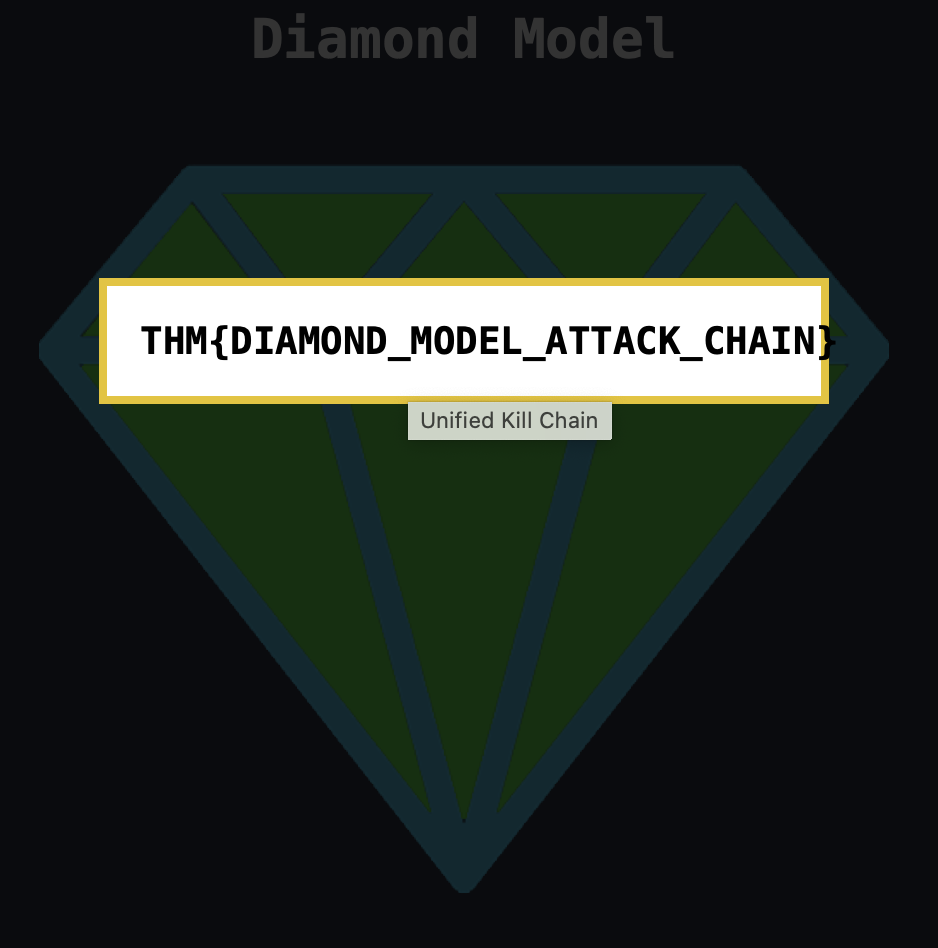
Thank you for reading my article. Please leave any questions or comments on improving my learning journey and the THM challenges.
Subscribe to my newsletter
Read articles from Jebitok directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Jebitok
Jebitok
Software Developer | Learning Cybersecurity | Open for roles * If you're in the early stages of your career in software development (student or still looking for an entry-level role) and in need of mentorship, you can reach out to me.