Storing Secrets in Azure Key Vault and Accessing with Managed Identity
 Freeman Madudili
Freeman MadudiliTable of contents
- Why Use Azure Key Vault?
- 1. Prerequisites
- 2. Create an Azure Key Vault
- 3. Adding Secrets to Key Vault
- 4. Assigning RBAC Permissions for Key Vault Access
- 5. Enabling Managed Identity for the Function App
- 6. Configuring Access for the Function App’s Managed Identity
- 7. Configuring the Function App to Use the Key Vault Secret
- Wrap-Up
- Additional: Key Vault vs. App Settings
In this guide, I’ll walk you through securing sensitive information, like database connection strings, using Azure Key Vault and accessing it from your Function App or App Service with a managed identity. This way, you avoid hardcoding secrets in your application, enhancing security and making your app more manageable.
Why Use Azure Key Vault?
Azure Key Vault allows you to securely store and manage application secrets. By integrating it with your Function App, you keep sensitive information like your Cosmos DB connection string safe from accidental exposure.
1. Prerequisites
Before starting, ensure you’ve deployed a Function App. If you haven’t, check out the previous post: Deploying a Serverless Function App with Azure CLI. Now, let’s get into securing and connecting with Key Vault.
2. Create an Azure Key Vault
First, create a Key Vault to store your secrets.
az keyvault create --name <KeyVaultName> --resource-group <ResourceGroupName> --location ukwest
This command creates a Key Vault in your specified resource group and region.
3. Adding Secrets to Key Vault
Next, store the Cosmos DB connection string as a secret in your Key Vault.
az keyvault secret set --vault-name <KeyVaultName> --name CosmosDbConnectionString --value "<CosmosDbConnectionString>"
Note: If you encounter a "ForbiddenByRbac" error, you’ll need to grant your account the correct role. Follow these steps to fix it.
4. Assigning RBAC Permissions for Key Vault Access
To avoid the "ForbiddenByRbac" error, let’s set up your permissions:
Retrieve your Azure user ID:
az ad signed-in-user show --query id -o tsvGet your subscription ID:
az account list --output tableAssign the Key Vault Administrator role to your user account:
az role assignment create --role "Key Vault Administrator" --assignee <YourUserObjectId> --scope "/subscriptions/<SubscriptionId>/resourceGroups/<ResourceGroupName>/providers/Microsoft.KeyVault/vaults/<KeyVaultName>"
After setting this, try adding the secret again.
5. Enabling Managed Identity for the Function App
To access Key Vault secrets securely, we’ll enable the managed identity for your Function App.
az functionapp identity assign --name <FunctionAppName> --resource-group <ResourceGroupName>
This command assigns a system-assigned managed identity to your Function App, which will securely access secrets in Key Vault.
6. Configuring Access for the Function App’s Managed Identity
Now, let’s grant your Function App’s identity permission to read secrets from Key Vault.
Retrieve the Function App’s principal ID:
az functionapp identity show --name <FunctionAppName> --resource-group <ResourceGroupName> --query principalId -o tsvGrant the Key Vault Secrets User role to the Function App’s identity:
az role assignment create --role "Key Vault Secrets User" --assignee <FunctionAppPrincipalId> --scope "/subscriptions/<SubscriptionId>/resourceGroups/<ResourceGroupName>/providers/Microsoft.KeyVault/vaults/<KeyVaultName>"
This setup allows the Function App’s identity to access secrets in Key Vault securely.
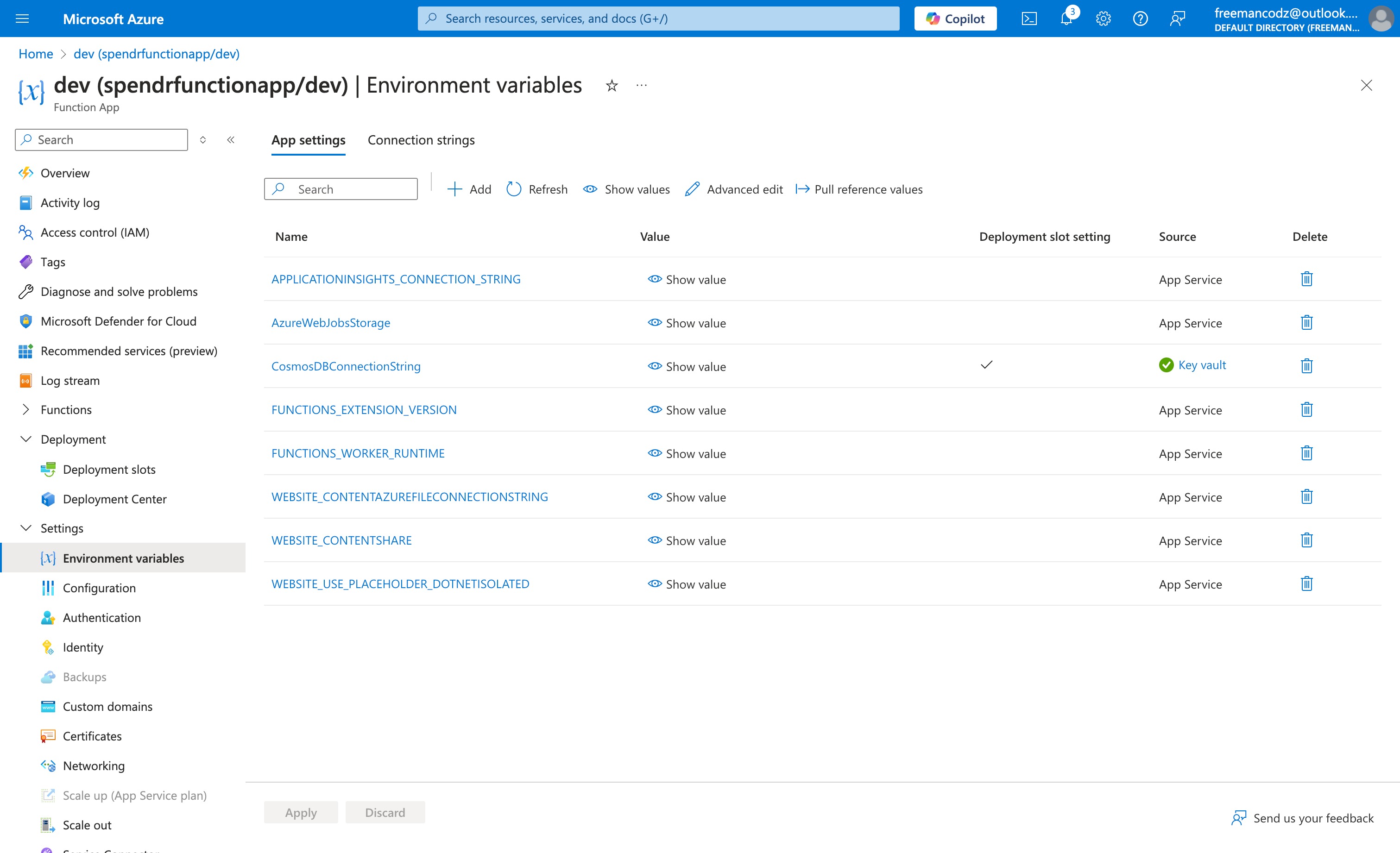
7. Configuring the Function App to Use the Key Vault Secret
Finally, reference the Key Vault secret in your Function App’s application settings.
az functionapp config appsettings set --name <FunctionAppName> --resource-group <ResourceGroupName> --settings "CosmosDBConnectionString=@Microsoft.KeyVault(VaultName=<KeyVaultName>;SecretName=CosmosDbConnectionString)"
This command tells the Function App to retrieve the CosmosDBConnectionString from Key Vault when it runs, keeping your connection string secure.
Wrap-Up
Your Function App is now set up to access secrets securely from Azure Key Vault using a managed identity. This approach keeps sensitive information safe and avoids the need to hardcode credentials directly in your code.
Additional: Key Vault vs. App Settings
When it comes to securing sensitive information, Azure Key Vault offers enhanced security over traditional app settings. Key Vault provides fine-grained access control, logging, and encryption, which are particularly useful when managing secrets at scale. However, it can add a slight performance overhead due to network calls, so consider your application’s security requirements versus performance needs.
By following these steps, you’ve added a solid layer of security to your Function App, ensuring best practices in cloud development.
Subscribe to my newsletter
Read articles from Freeman Madudili directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Freeman Madudili
Freeman Madudili
Hi, I’m Freeman, a Software Developer specializing in C#, .NET, and Azure. With a passion for creating seamless web and cloud solutions, I’ve built and deployed apps that solve real-world problems. Follow along as I share insights, projects, and tips from my journey in tech!