OCI Confidential Computing : A quick look at a little-known feature
 Walid Hajeri (WalidHaj)
Walid Hajeri (WalidHaj)
Understanding what Confidential Computing is
Confidential computing is a feature that many people overlook or don't activate, maybe because it's unclear exactly what it is. It is true that the text that appears on the console to explain it, well… does not explain it very clearly :
Confidential computing is hardware technology in CPUs that encrypts data in-use while being processed and protects against these threats.
If we dig into the documentation, however, it gets much more interesting. We understand that this activates real-time data encryption. The underlying technology is different depending on whether you're using Bare Metal instances or plain Virtual Machines. For VMs, it uses AMD's SEV (Secure Encrypted Virtualization). For Bare Metal, it is Transparent Secure Memory Encryption (TSME).
The idea is to add a layer of security by further isolating the VM from the hypervisor by encrypting the VM’s data while it’s in use.
Wait … "data in use"?
This term refers to non-persistent data generally accessed or processed by the Operating System or Applications, typically stored in RAM. While people often discuss encrypting data at rest (on disks, in databases, etc.) and encrypting data in transit, data in use is less commonly addressed. If you have zero trust architecture in mind and want to secure the VMs from insider threats, cloud operator access, and any potential access from the hypervisor, confidential computing is something to consider.
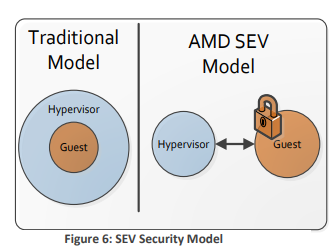
Source : AMD MEMORY ENCRYPTION AMD Whitepaper, by David Kaplan, Jeremy Powell, Tom Woller (2021).
The encryption key is unique to each VM, and kept completely separated from the VM, the hypervisor, etc, and not accessible by OCI. It is stored in a specific hardware chip called AMD Secure Processor which is part of AMD's CPU. As with all encryption tasks, there is a performance tradeoff to take into account, but for most workloads, this shouldn't be noticeable.
The obvious benefits of enabling Confidential Computing are :
Reduces the attack surface of Virtual Machine or Bare Metal instances, with minimal performance impact.
One-click enablement, no changes required to the applications or VM. See the step-by-step demo below.
No additional cost.
As you can see, this adds to the built-in OCI secure-by-design architecture that pioneered off-box virtualization among large cloud providers. By moving network virtualization outside the hypervisor, OCI ensures that if an attacker were to escape a VM, they couldn't alter the network virtualization to make lateral moves to other hosts. If you’re interested in learning more about OCI’s security architecture, please refer to the white paper linked at the end of this post.
How to enable Confidential Computing ?
The way to create a confidential compute instance is nearly identical to creating a regular compute instance
We simply find the option to enable it in the Security panel of the compute instance creation screen :
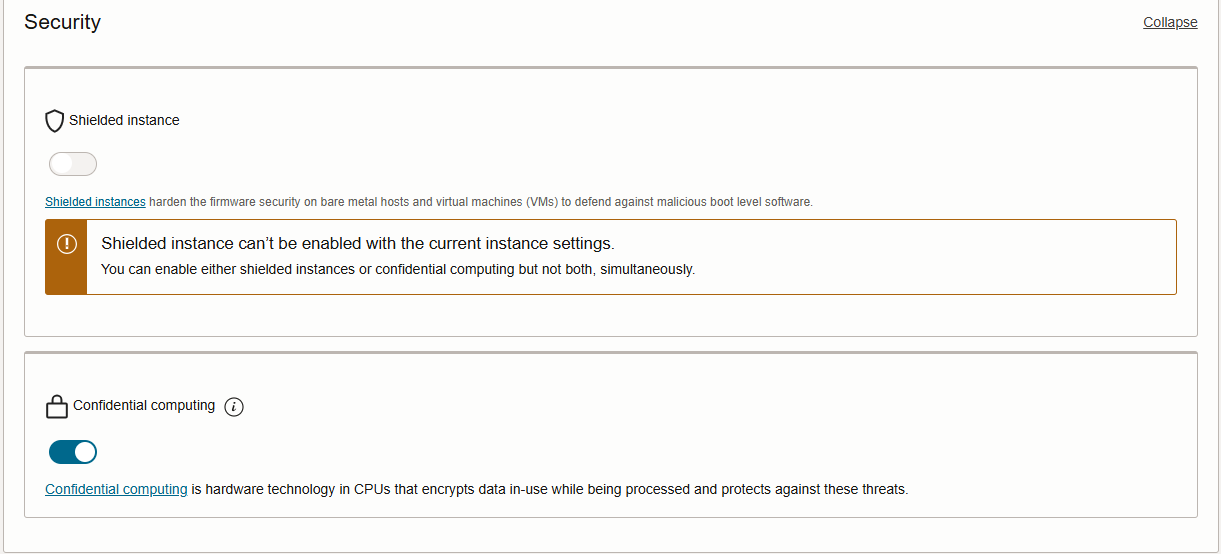
As of today, we can’t have the instance to be both shielded and confidential.
The console will allow to enable confidential computing only on compatible compute shapes that are indicated by the locker icon (see screenshot below).
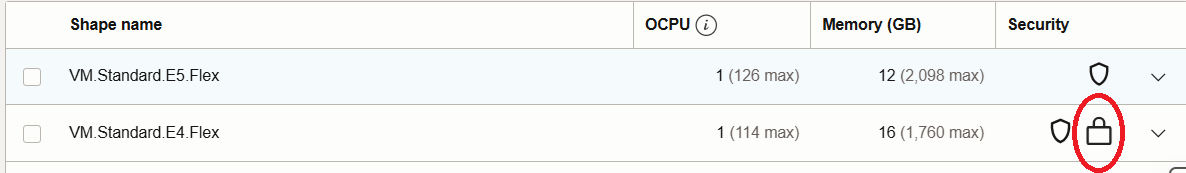
That’s it, it takes just one click to enable it. Once the instance is launched, you should see on the instance information that Confidential computing has been enabled :
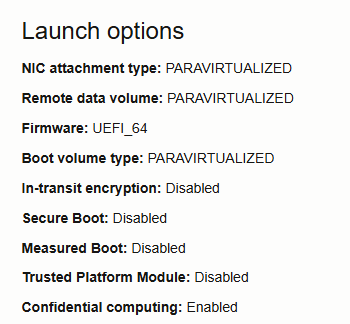
I hope you'll find this blog post useful. Thanks again for reading me !
Walid Hajeri
Disclaimer : Views are my own , none of the ideas expressed in this post are shared, supported, or endorsed in any manner by my current employer.
Sources / Knowing more :
White Paper on OCI Security : https://www.oracle.com/a/ocom/docs/oracle-cloud-infrastructure-security-architecture.pdf
https://blogs.oracle.com/cloud-infrastructure/post/first-principles-baking-security-into-the-cloud
https://blogs.oracle.com/cloud-infrastructure/post/protect-data-in-use-with-confidential-computing
https://www.ateam-oracle.com/post/ciso-perspectives-confidential-compute-protecting-data-inprocess
https://www.oracle.com/uk/a/ocom/docs/oracle-cloud-infrastructure-security-architecture.pdf
Subscribe to my newsletter
Read articles from Walid Hajeri (WalidHaj) directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Walid Hajeri (WalidHaj)
Walid Hajeri (WalidHaj)
Customer Engineer with a passion for well-designed tech products. Tech side - Interest in Cloud-native App Dev & AI Other side - University of Paris 1 Sorbonne alumnus, grew up in a creative family, passionate about all things related to visual arts & design in general.