Automating AWS Security Scans with Prowler, Fargate, and EventBridge
 Akanksha Giri
Akanksha Giri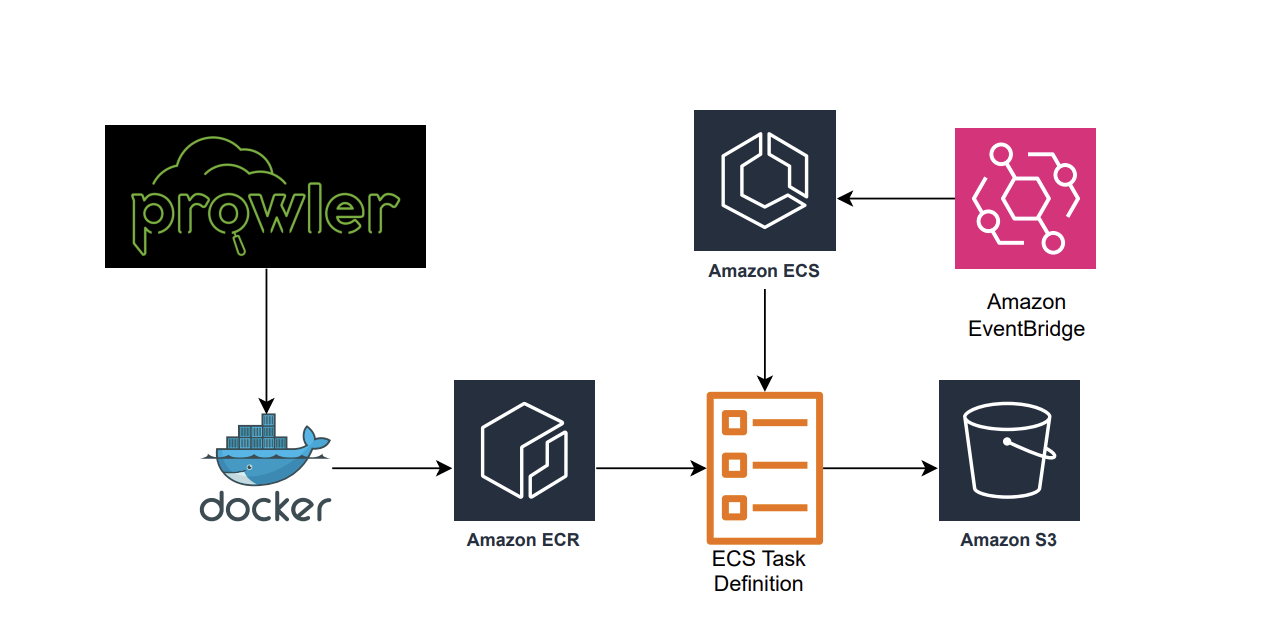
Introduction
Keeping your AWS environment secure can feel like a never-ending task. But with the right tools and automation, it doesn’t have to be overwhelming. In this blog, I’ll show you how to use AWS Fargate to run Prowler, a security scanner, on your AWS infrastructure. Prowler checks for security issues, outputs the results in a CSV file, and automatically uploads them to an S3 bucket.
Creating the Docker Image
This Dockerfile creates a lightweight container with Python, AWS CLI, and Prowler pre-installed, setting prowler as the default command.
FROM python:latest
WORKDIR /prowler
RUN \
apt update && \
apt upgrade -y && \
pip install awscli && \
apt install -y python3-pip
RUN pip install prowler
ENTRYPOINT ["prowler"]
Then save the Dockerfile and navigate to the directory where the Dockerfile is saved. Run the following command to build the Docker image:
docker build -t prowler-image .
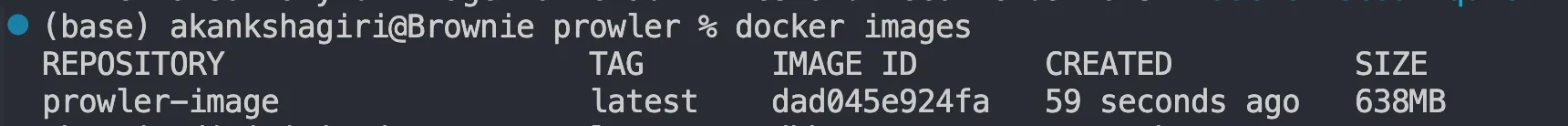
To verify image creation you can use the command docker images to list your available images.
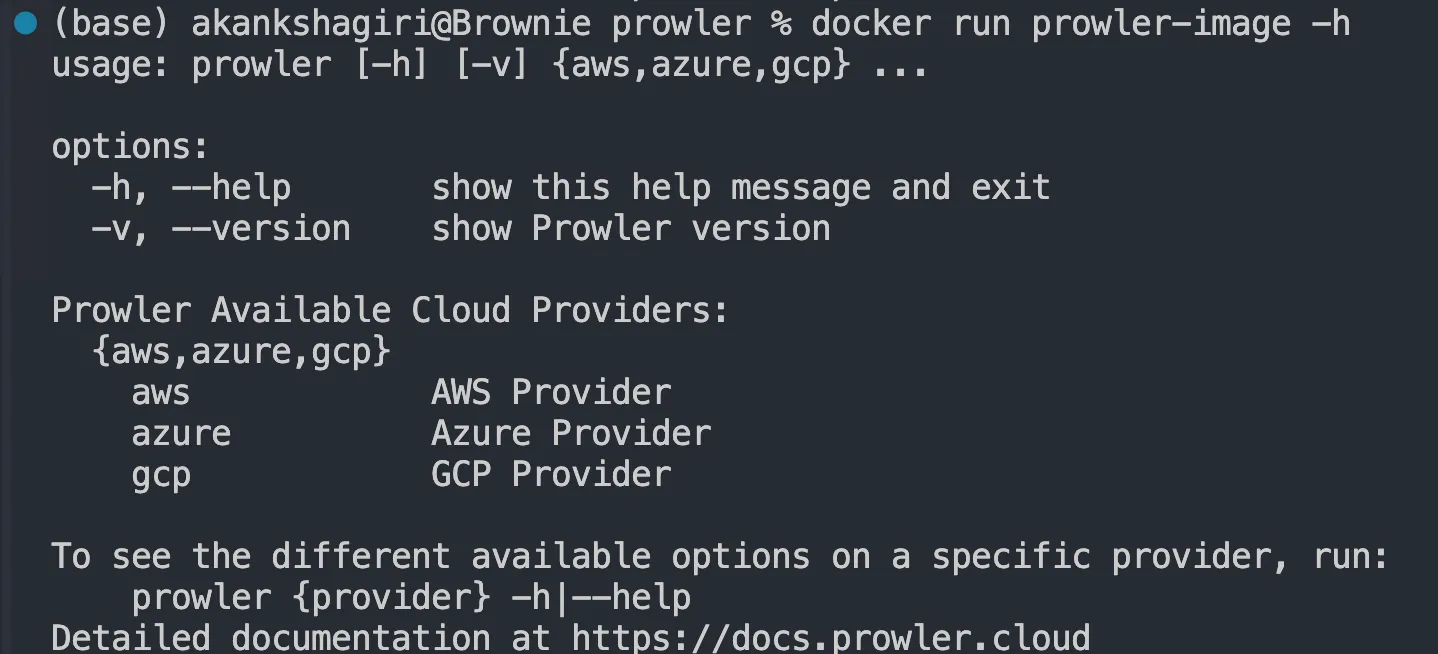
After building the Docker image, you can run it locally to verify that Prowler is working correctly.
Push Docker Image to ECR
Navigate to Amazon ECR console from AWS Management Console. Then click on Create.
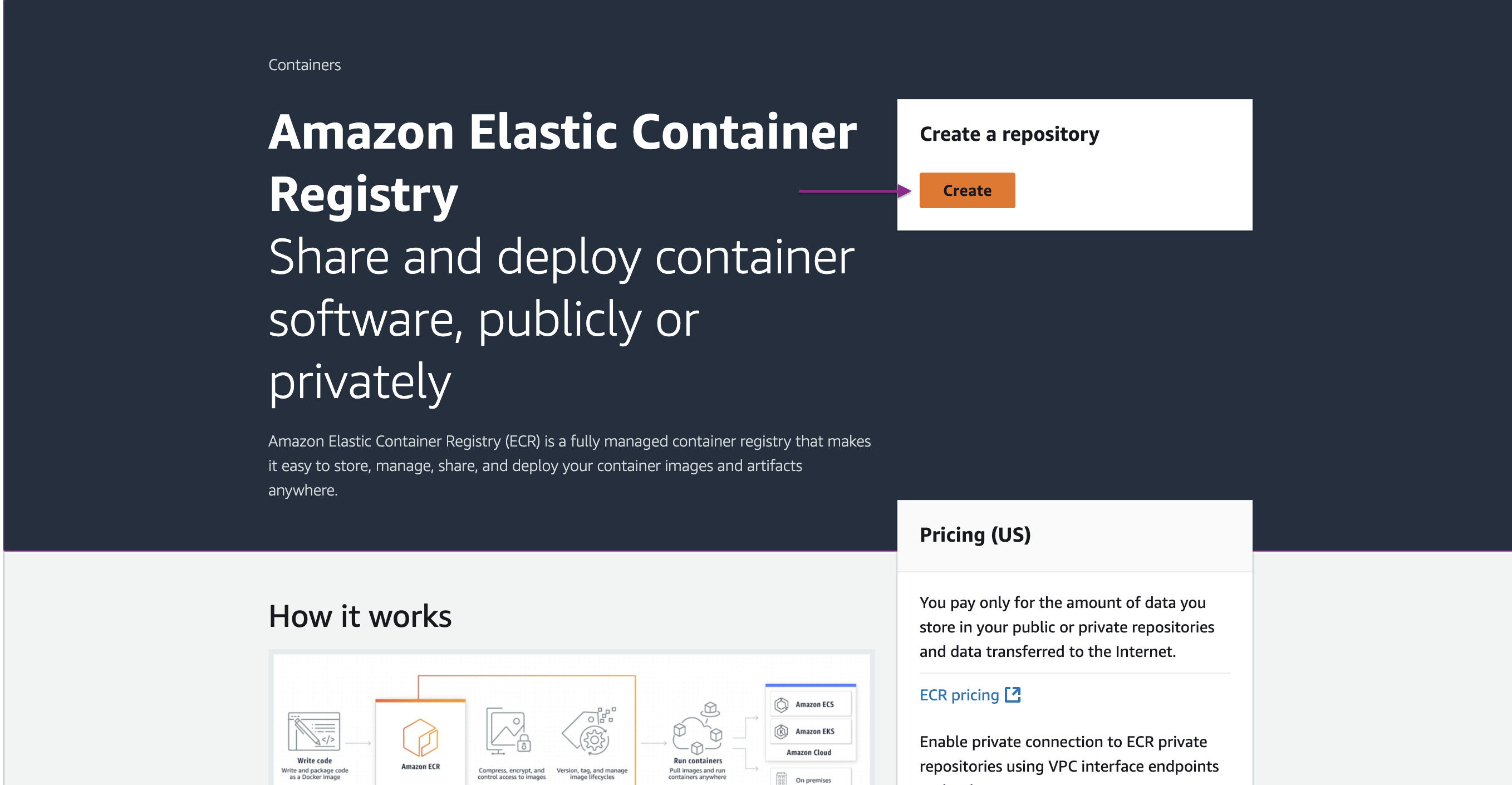
Then give your repository a name. I’ve kept other settings as default and then select Create to create your repository.
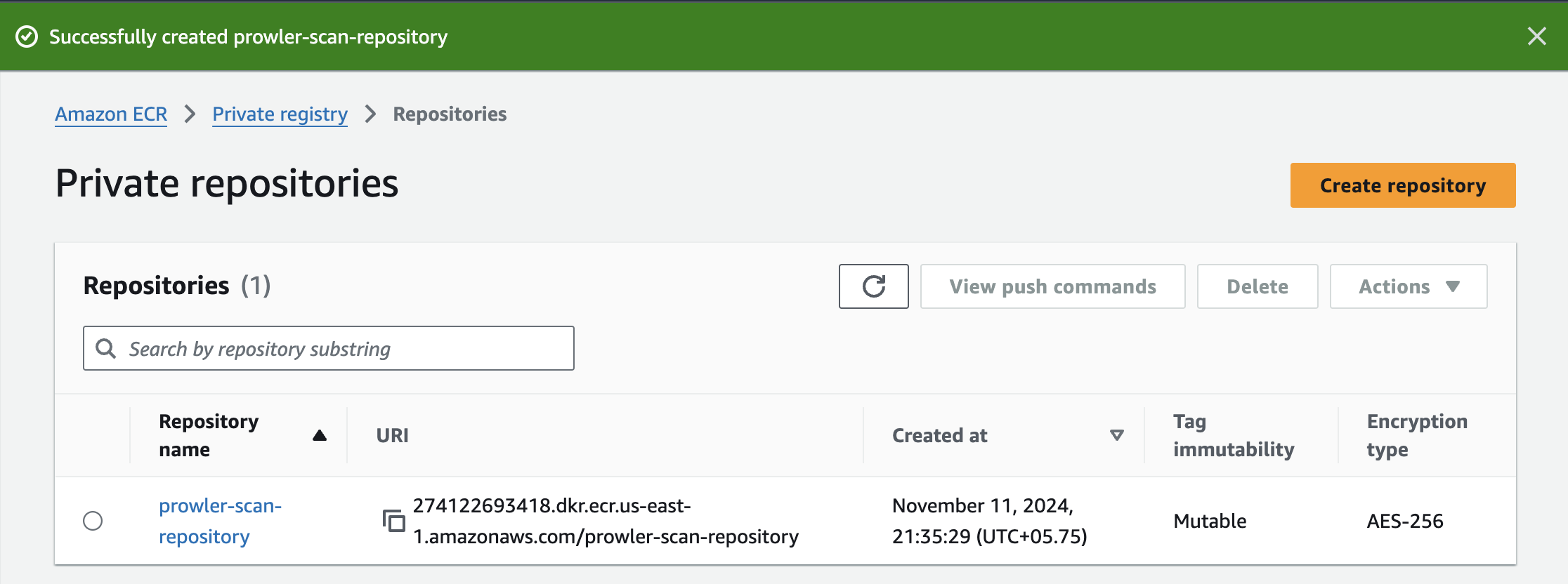
In the Amazon ECR console, select the created repository and click the View push commands button. Then follow the provided instructions to authenticate Docker with ECR registry and push the Docker image.
To authenticate your Docker client to the Amazon ECR registry:
aws ecr get-login-password --region <your-region> | docker login --username AWS --password-stdin <your-account-id>.dkr.ecr.<your-region>.amazonaws.com
Before pushing, you need to tag the Docker image with the ECR repository URL:
docker tag prowler-image:latest <your-account-id>.dkr.ecr.<your-region>.amazonaws.com/prowler-scan-repository:latest
Now, we can push your Docker image to the ECR repository:
docker push <your-account-id>.dkr.ecr.<your-region>.amazonaws.com/prowler-scan-repository:latest
Go back to the Amazon ECR console and navigate to your prowler-scan-repository. We should see our Docker image listed there.
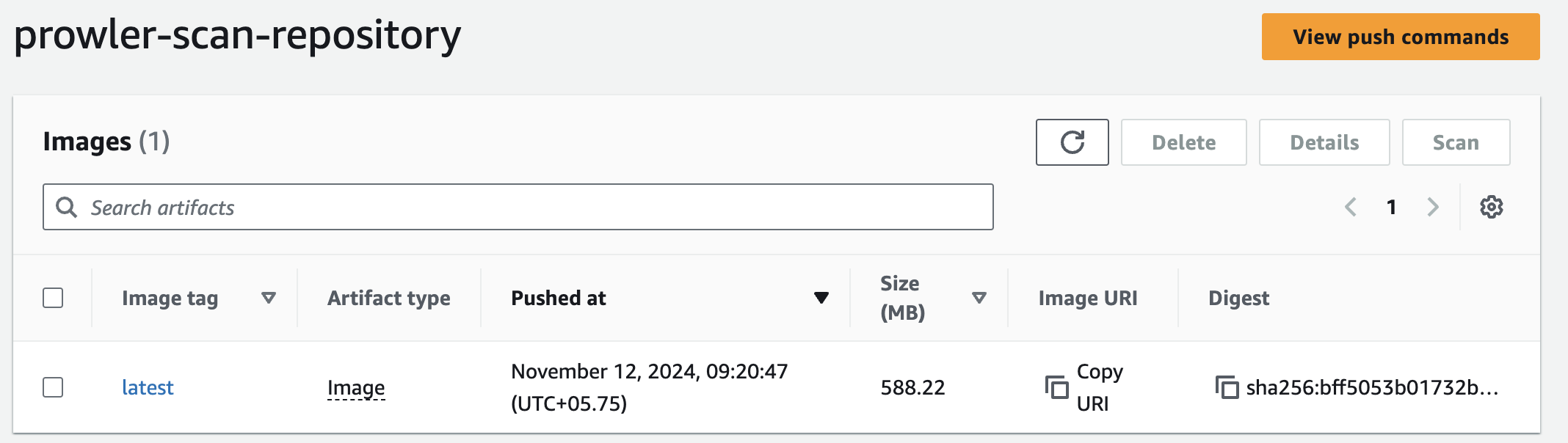
Configuring the ECS Task Definition
An ECS Task Definition is a configuration file in Amazon ECS that tells ECS how Docker containers should run.
Navigate to Amazon ECS console then click on Task Definitions in the left navigation pane. And then click on Create new Task Definition.
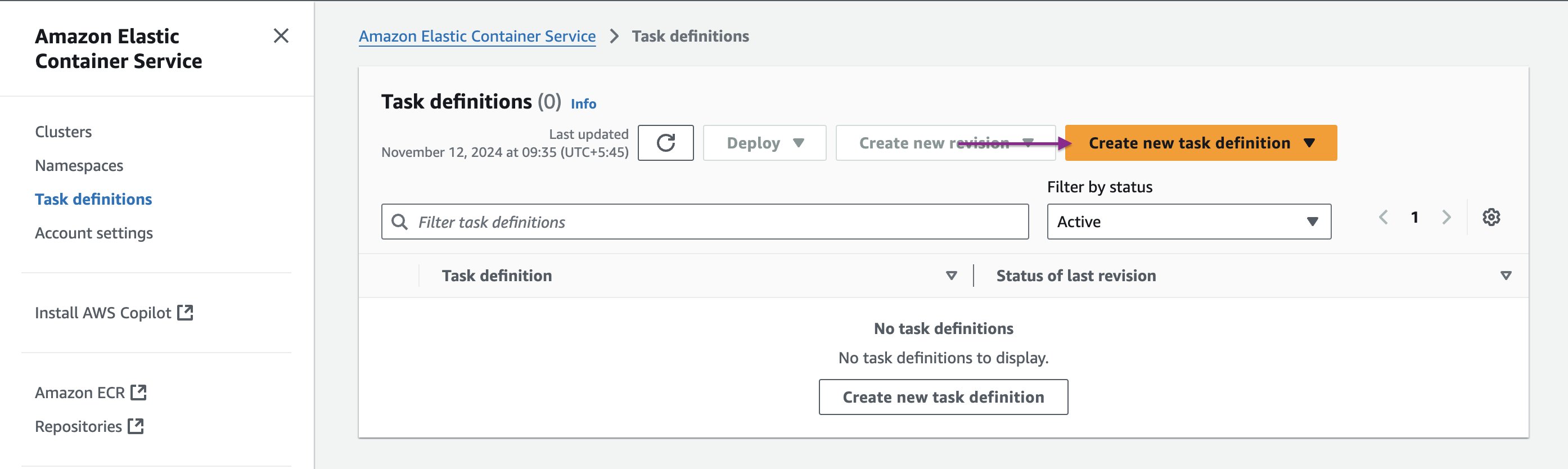
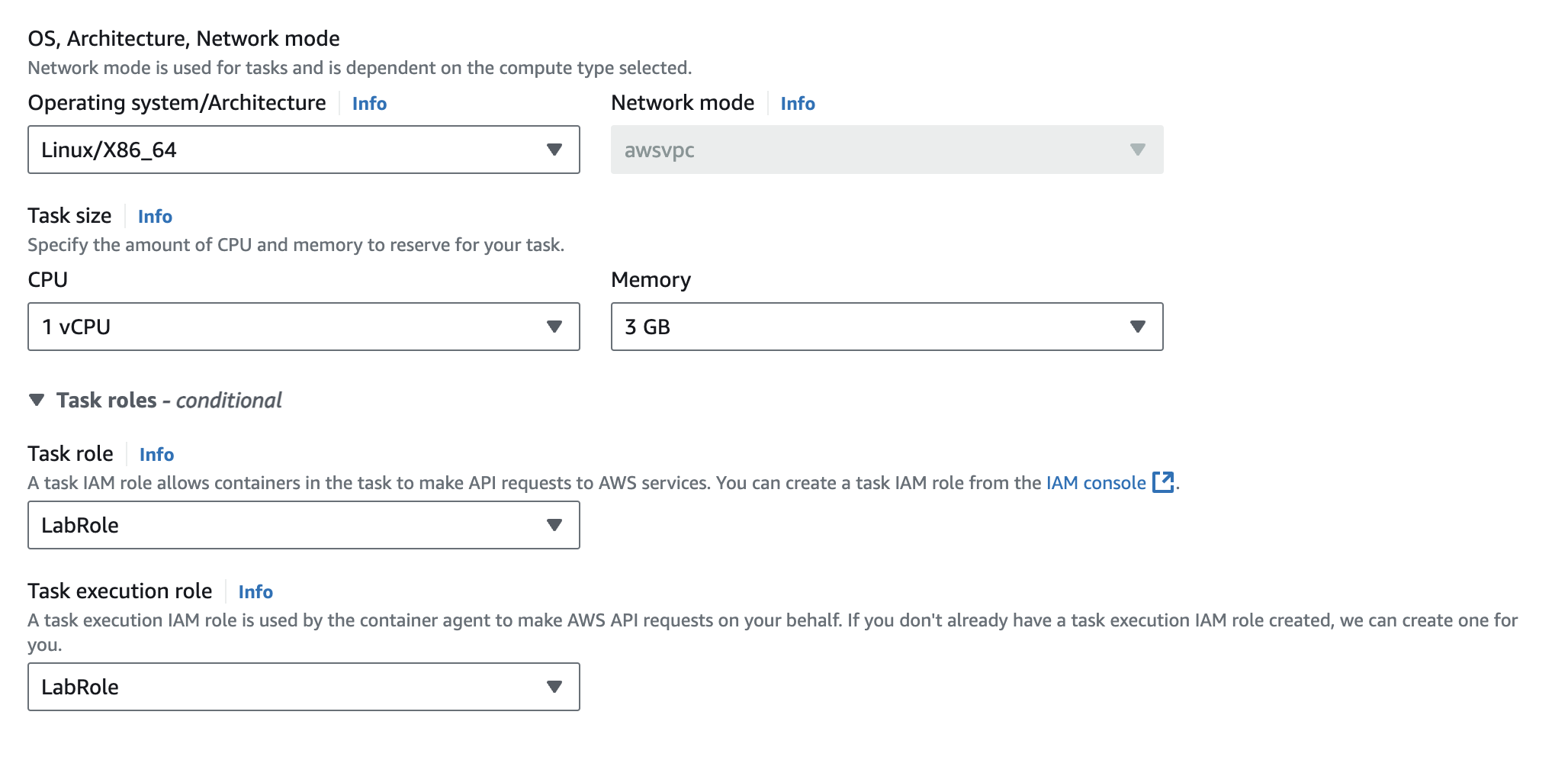
Name the task definition. Keep AWS Fargate selected, and I’ve left all other settings as default.
Select or create an existing role with the necessary permissions for ECS task role that Prowler needs to complete its scans. You can find more information about these permissions on the official Prowler GitHub page.
I’m currently using AWS Learner’s Lab for this project , so i don’t have permission to create an IAM role. Hence, I’m using the LabRole available in this environment.
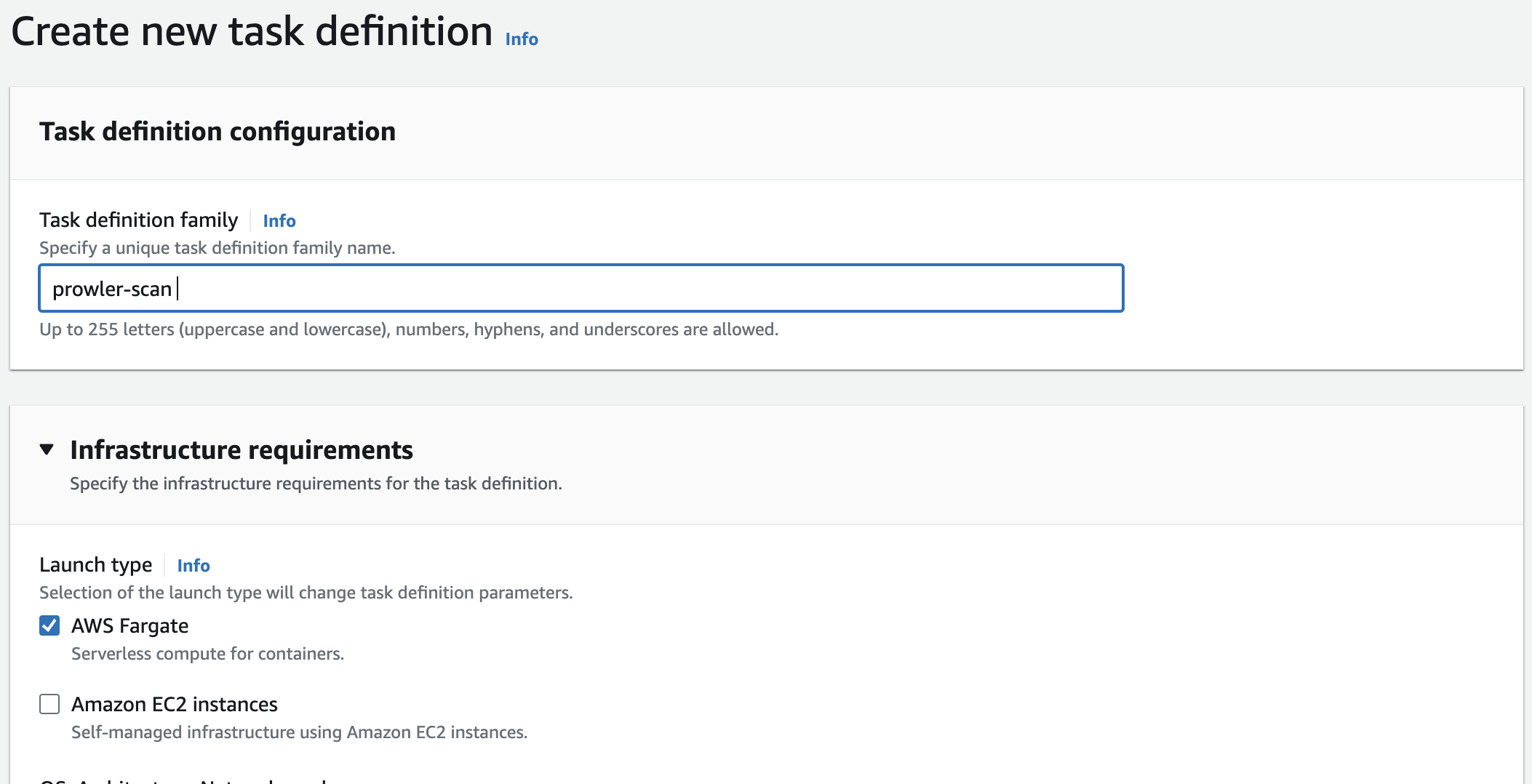
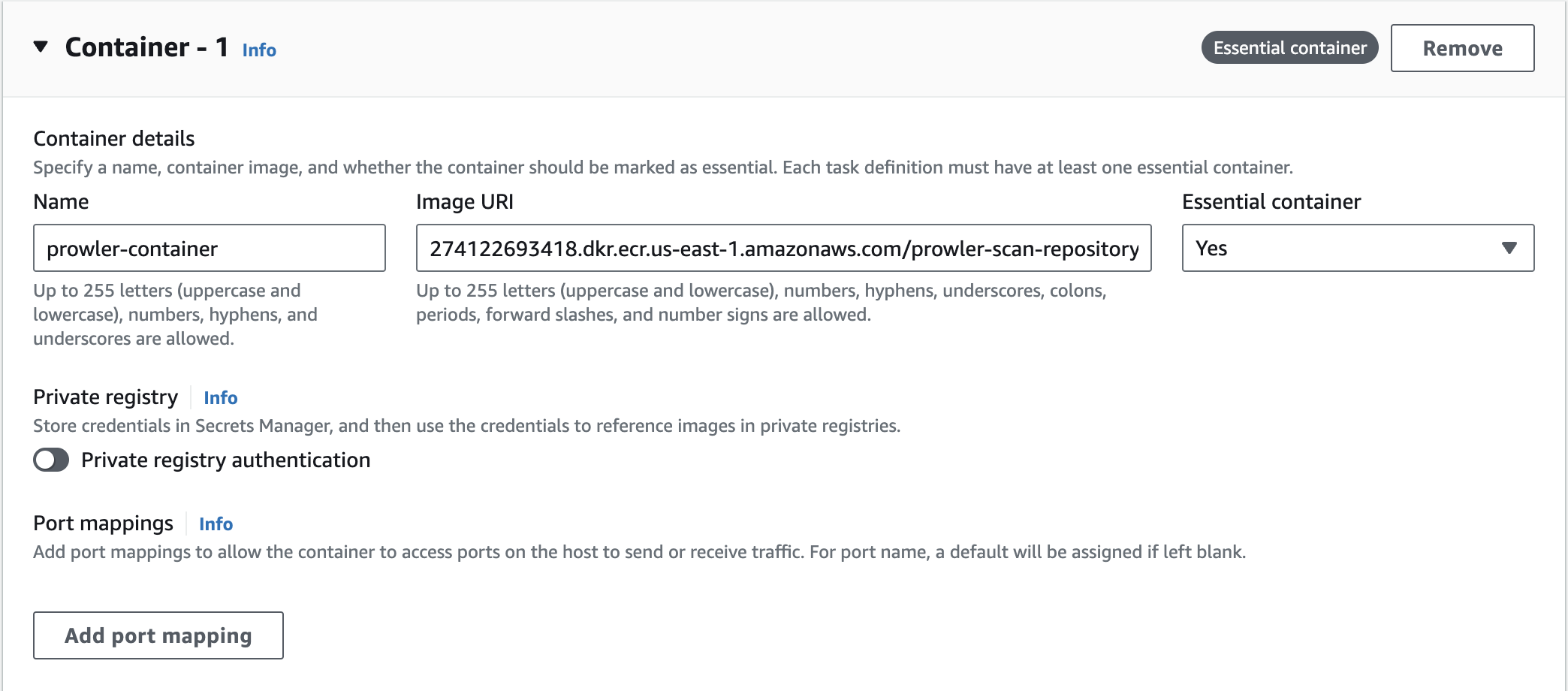
In the container definitions give a container name and provide the URL of the Docker image in ECR. Click the Remove button next to the default container port mapping as this container does not need to expose any ports for inbound traffic.
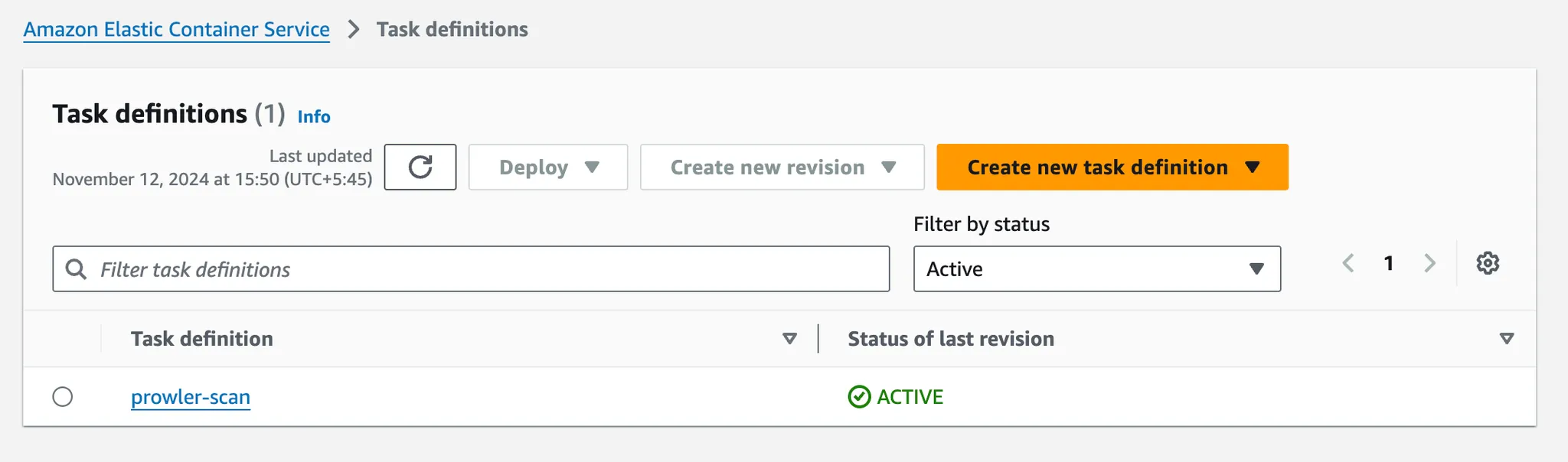
Then click Create. Go back to the ECS console and navigate to Task Definitions. You should see your task definition listed there.
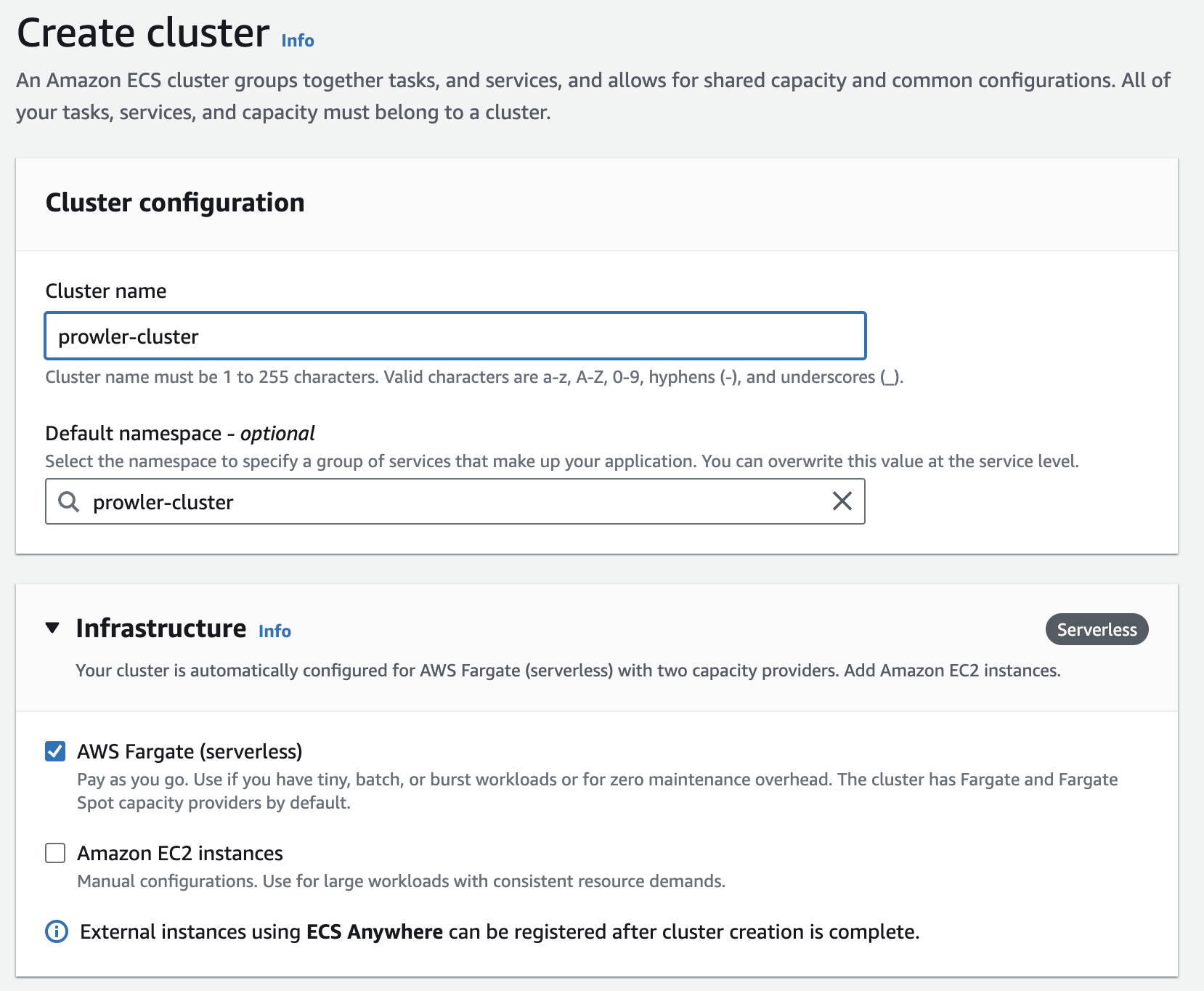
Setting Up the ECS Cluster
In Amazon ECS console, Click on Clusters in the left navigation pane. Click on the Create Cluster button.
Give a suitable name for the cluster. Under Infrastructure, leave the default selection as AWS Fargate. I’ve left all the other settings as default.Then review your configurations, and then click on the Create button.
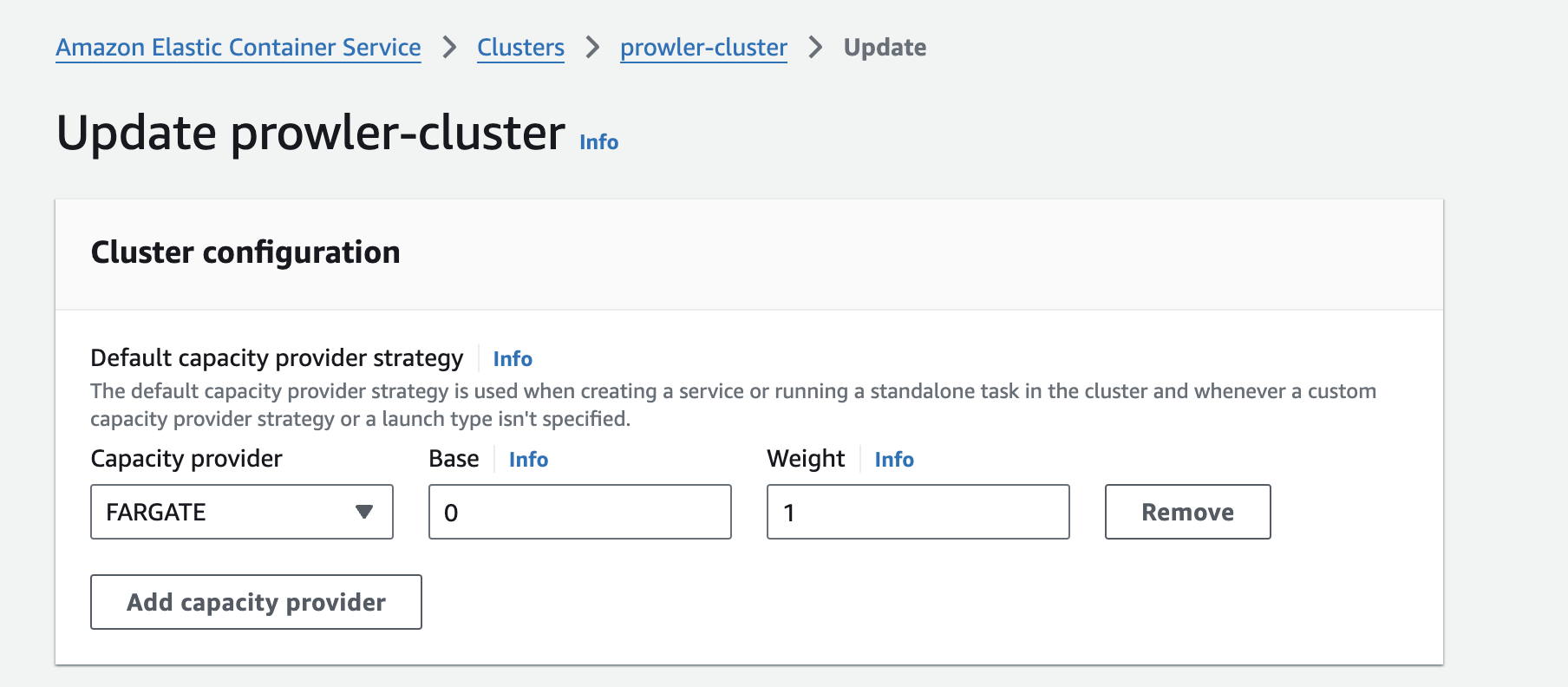
Once the cluster is created, click on its name to view its details. Click on the Update Cluster button in the top right corner. Define a default capacity provider strategy. Select FARGATE and leave the weight as 1. Click Update
Automating with Amazon EventBridge
In the Amazon EventBridge console, scroll down and click Schedules under the Scheduler feature. Then click on Create schedule.
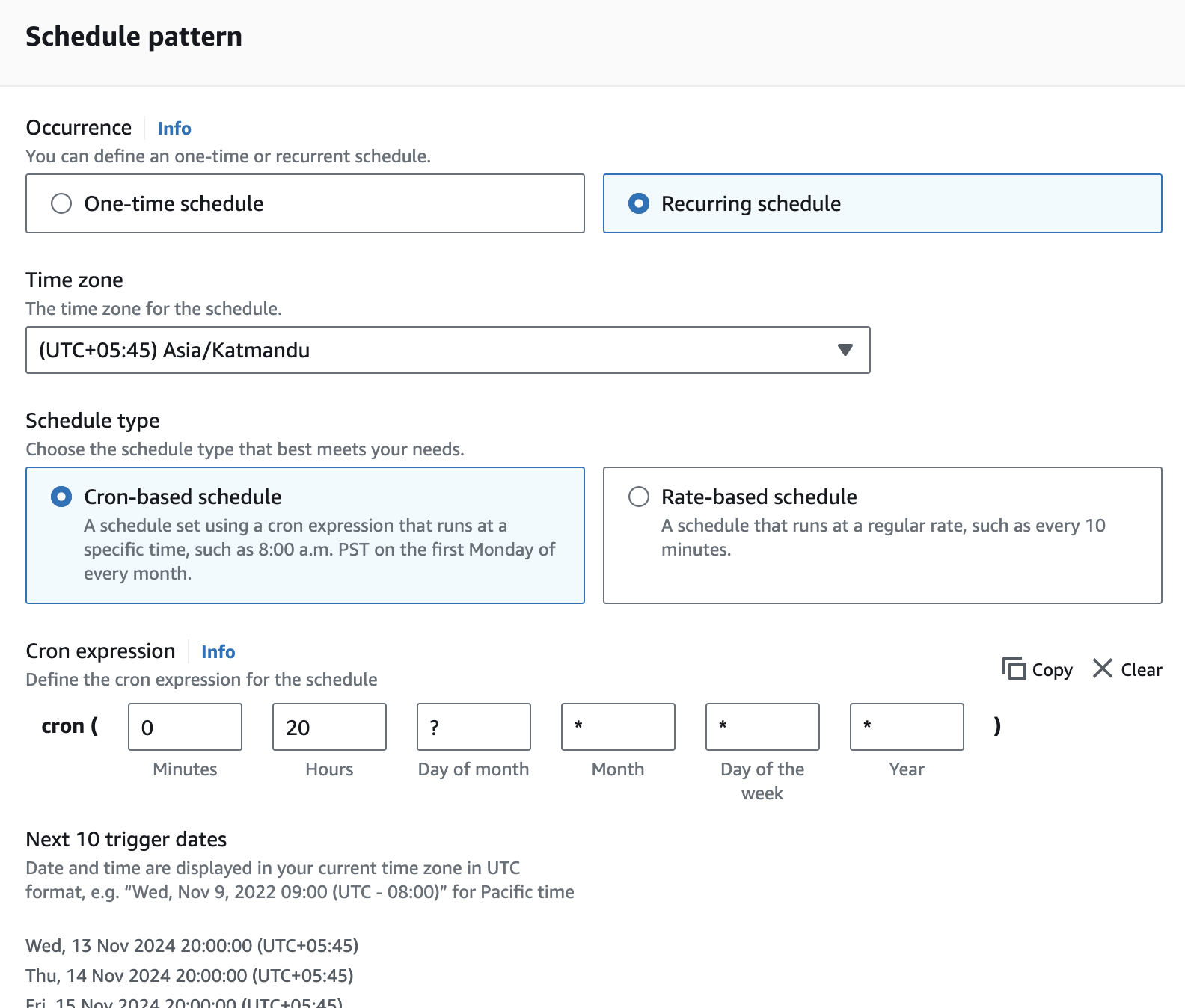
Under Schedule pattern, choose Recurring schedule. To set up daily scans at 8 PM, use the cron expression 0 20 ? * * *, and select a Flexible time window to off. Then click on Next.
On the Select target section, choose ECS RunTask from the options. For Cluster, select the ECS cluster we've previously set up. For Task Definition, select your Prowler task definition. Under Subnets , specify the subnet. Then click Next.
To retry the execution in case of failures, I’ve set the Retry policy to retry 3 times.
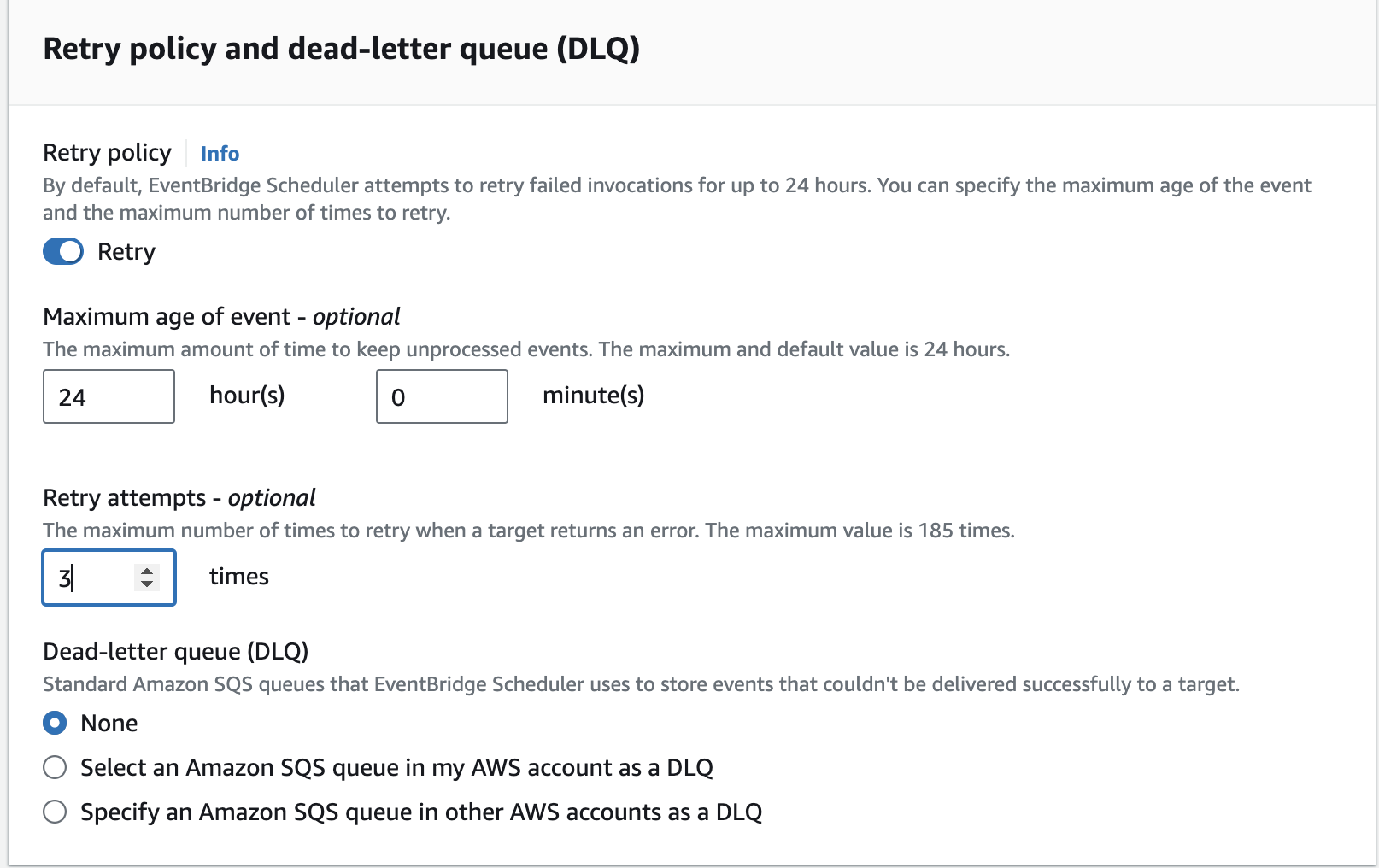
At the bottom, there is an option to create a new role or select an existing one for the scheduler to use to run the task. By selecting Create new role it will automatically set up an appropriate role. Then click Next then review all your configurations and then click on the Create button. On the EventBridge console we can the scheduler created.
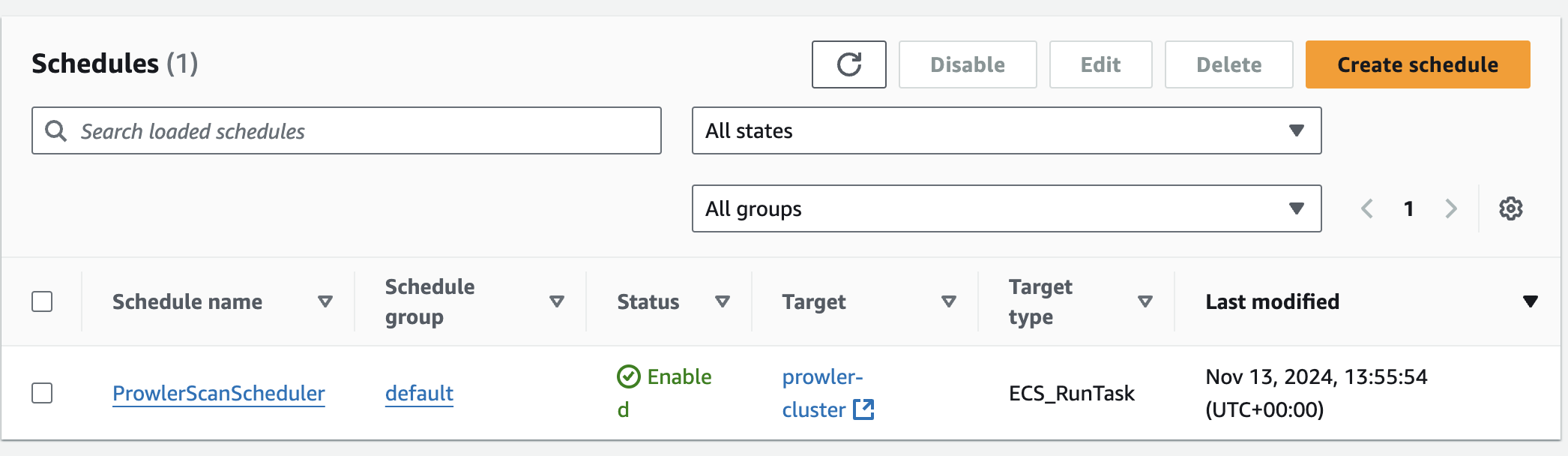
We’ve set up an automated execution of the Prowler scan task in ECS using Amazon EventBridge. The task will automatically run every day at 8 PM.
Conclusion
By automating Prowler scans with AWS Fargate and sending results to S3, you’ve set up a simple yet powerful security monitoring system. For future, we can also go a step further by setting up automated monitoring with AWS Lambda and Security Hub, so you can quickly catch and respond to security findings without manual intervention.
References:
Subscribe to my newsletter
Read articles from Akanksha Giri directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by
