How Password and Password-less Authentication Work in Ansible
 Harendra Barot
Harendra Barot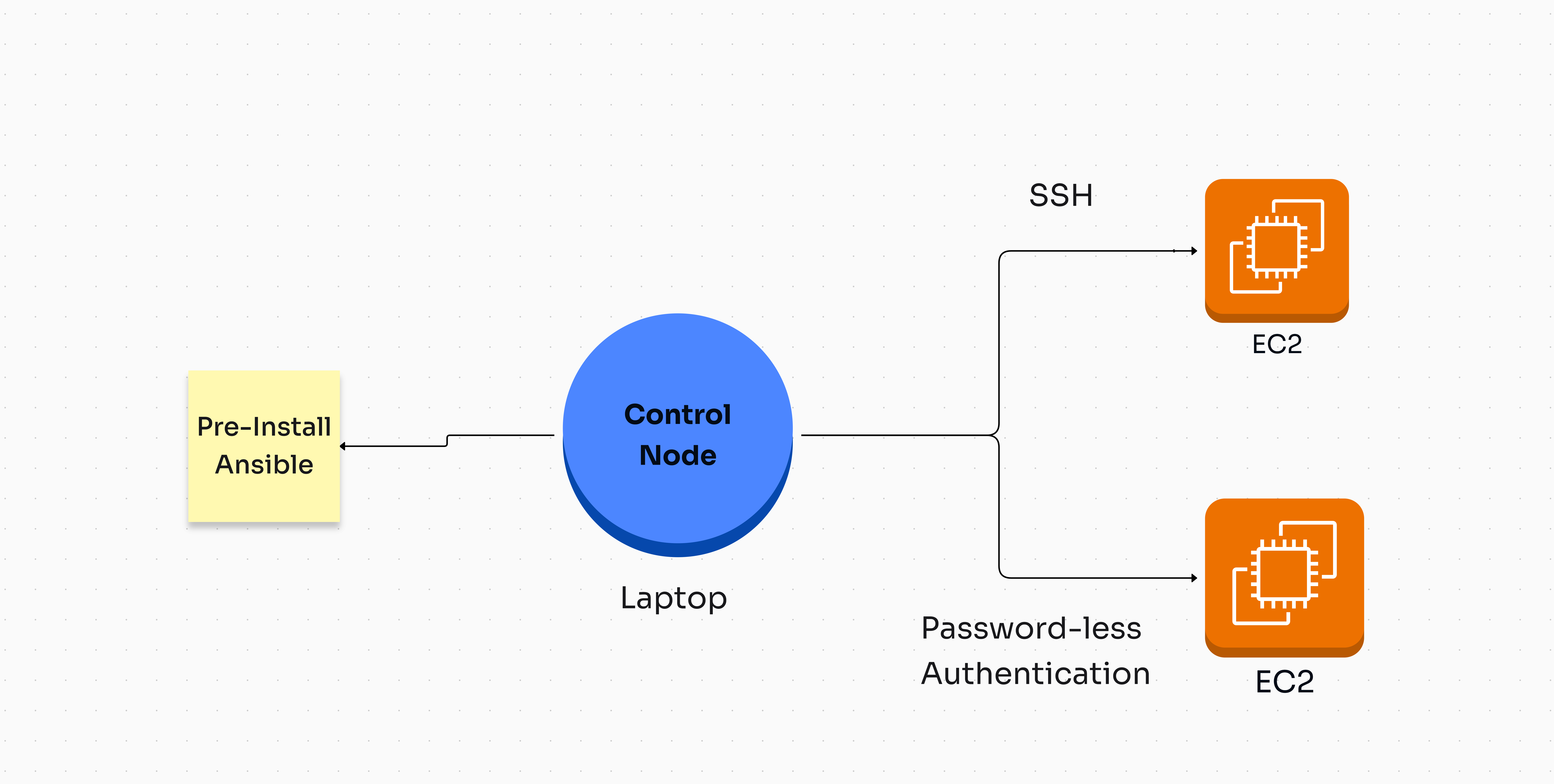
Below are the detailed steps to set up two instances for SSH with password-based authentication using Ansible:
Setting Up Mixed Authentication for Two Instances Using Ansible
Introduction: Why Mixed Authentication?
In the world of DevOps, you often work with diverse infrastructure where some instances require password-based access for convenience, while others demand the stricter security of password-less authentication. In this guide, we’ll configure:
Instance 1 for password-based SSH login.
Instance 2 for password-less authentication using an SSH key pair.
We’ll also demonstrate how these two instances can communicate and automate workflows using Ansible.
The Scenario: Two Machines, Two Authentication Methods
Here’s the plan:
Instance 1 (Control Node): Acts as your remote machine and is accessible via a password.
Instance 2 (Target Node): Configured to accept SSH key-based authentication, ensuring secure password-less access.
The goal? To manage Instance 2 from Instance 1 and your local WSL machine, each with their respective authentication methods.
Part 1: Configuring Instance 1 (Password-Based Authentication)
1. Modify SSH Configuration
Log in to Instance 1 via your local machine:
ssh -i ~/path/to/key.pem ubuntu@<Instance-1-Public-IP>Edit the SSH configuration file:
sudo vim /etc/ssh/sshd_configUpdate or add the following lines:
PasswordAuthentication yes PermitRootLogin prohibit-passwordSave and exit the file (
:wqinvim).Restart the SSH service:
sudo systemctl restart ssh
2. Set a Password for the User
Set a password for the default user (
ubuntu):sudo passwd ubuntu- Enter and confirm the password.
3. Test Password-Based Login
Try SSH from your local WSL:
ssh ubuntu@<Instance-1-Public-IP>
- Enter the password you set.
Part 2: Configuring Instance 2 (Password-Less Authentication)
1. Generate an SSH Key Pair
On your local WSL, generate a key pair (if not already done):
ssh-keygen -t rsa -b 2048
Press Enter to save the keys to
~/.ssh/id_rsa.Skip setting a passphrase (optional).
2. Add the Public Key to Instance 2
Copy the public key to Instance 2:
ssh-copy-id -i ~/.ssh/id_rsa.pub ubuntu@<Instance-2-Public-IP>Verify that the key was added:
ssh ubuntu@<Instance-2-Public-IP>- You should be logged in without a password.
3. Restrict SSH Key Permissions
Ensure the private key is secure:
chmod 600 ~/.ssh/id_rsa
Conclusion: One Setup, Two Methods
With this setup, you’ve established:
Password-based access to Instance 1, ideal for quick troubleshooting or less secure environments.
Password-less access to Instance 2, ensuring strong security for sensitive operations.
By leveraging these methods, you’ve laid the groundwork for powerful automation workflows with Ansible. Next, try creating playbooks to automate common tasks across these nodes!
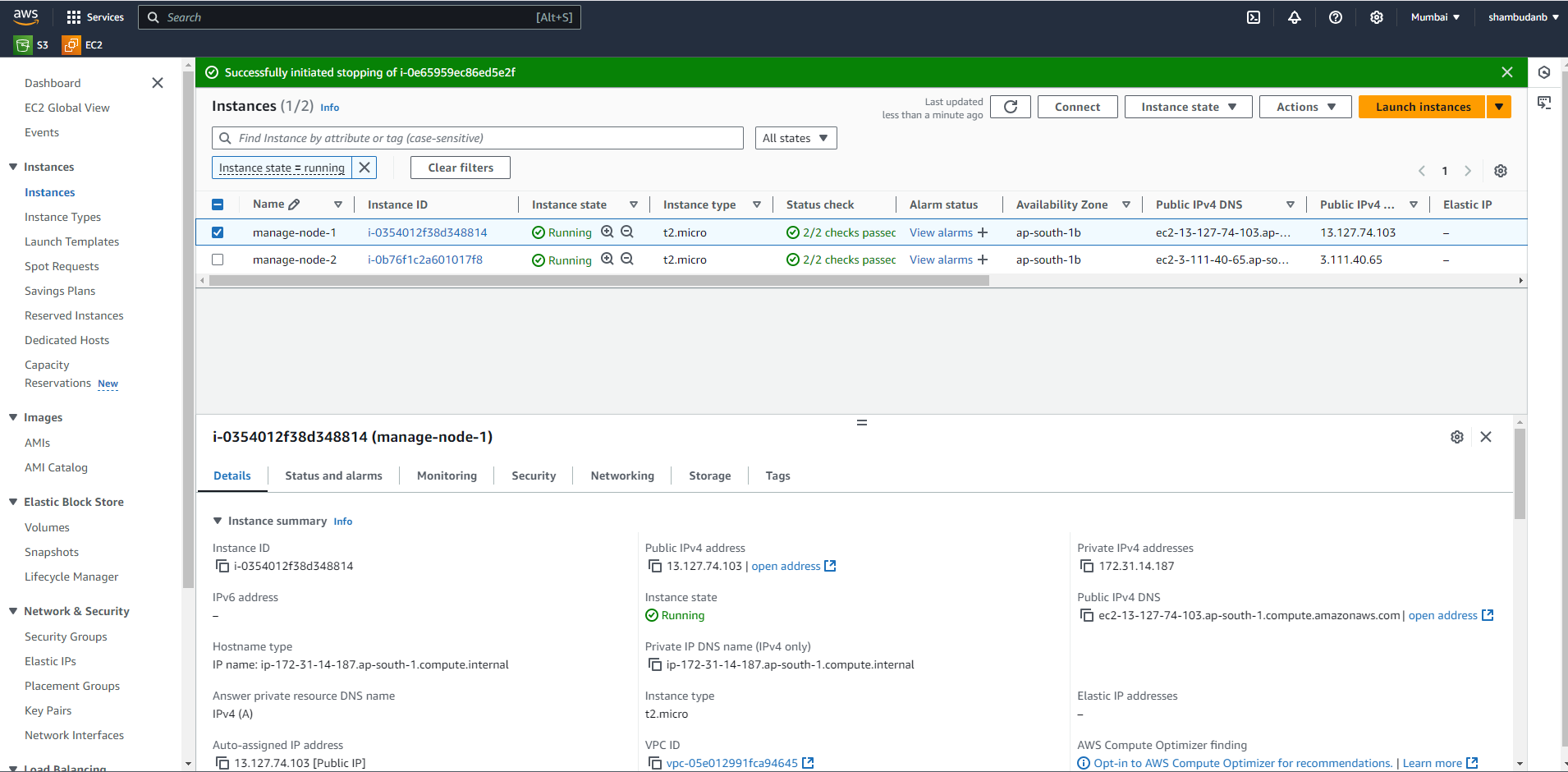
Attachment: 2 EC2 Instance used for this task
Subscribe to my newsletter
Read articles from Harendra Barot directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Harendra Barot
Harendra Barot
I'm an IT professional and business analyst, sharing my day-to-day troubleshooting challenges to help others gain practical experience while exploring the latest technology trends and DevOps practices. My goal is to create a space for exchanging ideas, discussing solutions, and staying updated with evolving tech practices.