Cyber Defence Frameworks: MITRE (TryHackMe)
 Jebitok
Jebitok
In this article, I will write an MITRE write-up: The Basics that covers Introduction to MITRE, Basic Terminology, ATT&CK Framework, CAR Knowledge Base, MITRE Engage, MITRE D3FEND, ATT&CK Emulation Plans, and ATT&CK and Threat Intelligence.
Besides Blue teamers, who else will use the ATT&CK Matrix? (Red Teamers, Purpe Teamers, SOC Managers?)
Red TeamersWhat is the ID for this technique?
T1566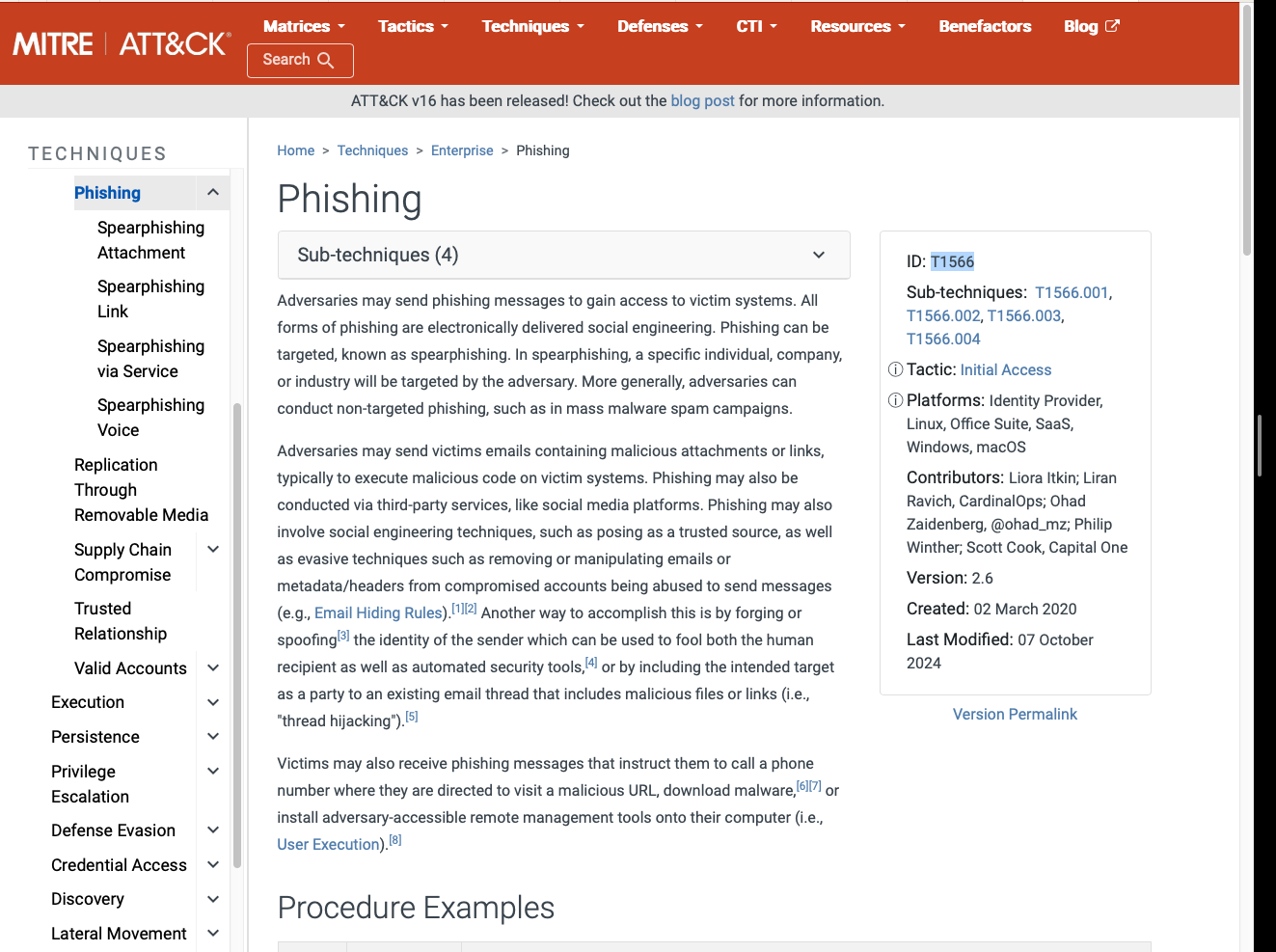
Based on this technique, what mitigation covers identifying social engineering techniques?
User Training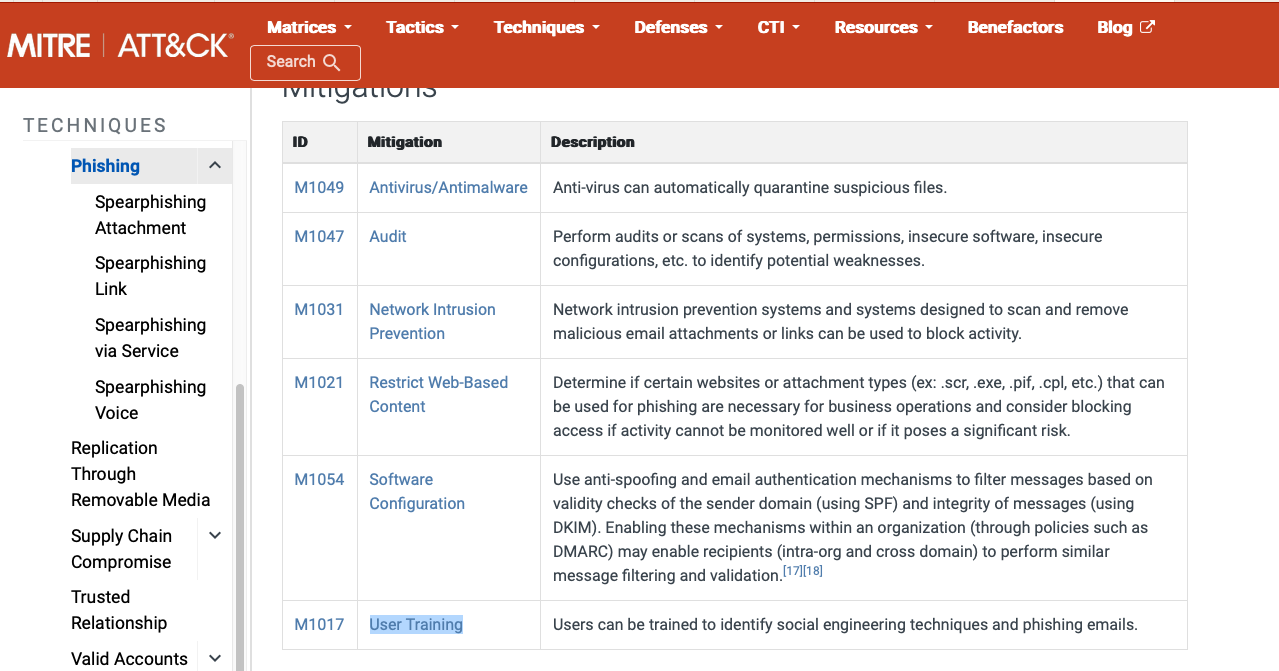
What are the data sources for Detection? **(**format: source1,source2,source3 with no spaces after commas)
Application Log,File,Network Traffic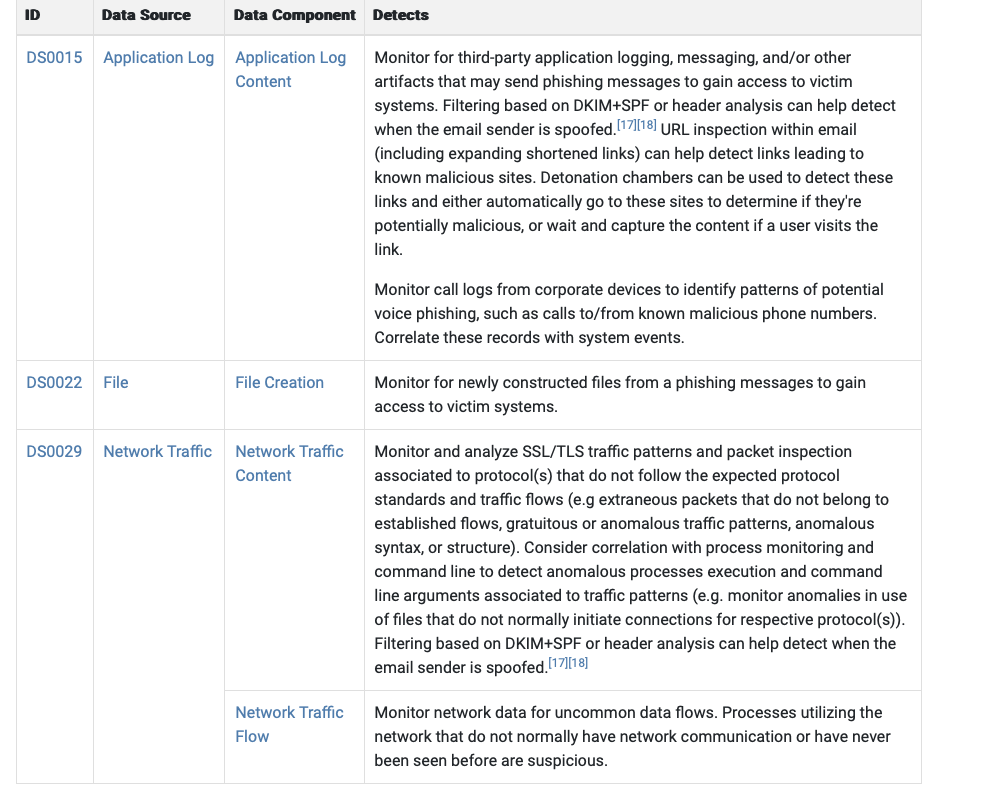
What groups have used spear-phishing in their campaigns? (format: group1,group2)
Axiom,Gold SOUTHFIELD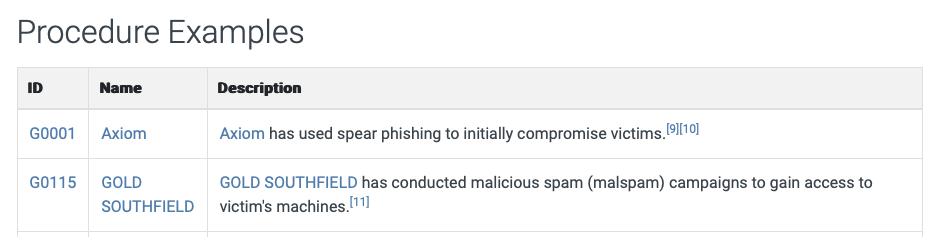
Based on the information for the first group, what are their associated groups?
Group 72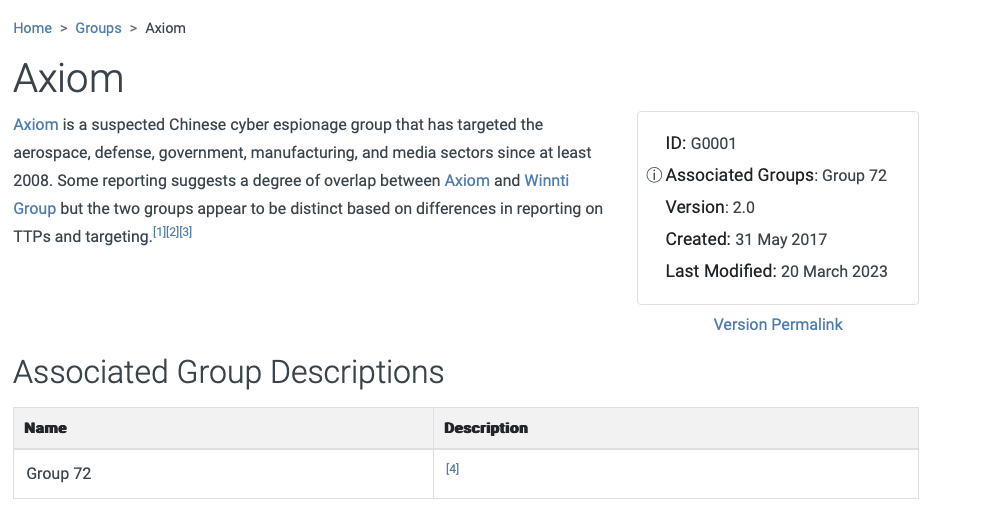
What software is associated with this group that lists phishing as a technique?
Hikit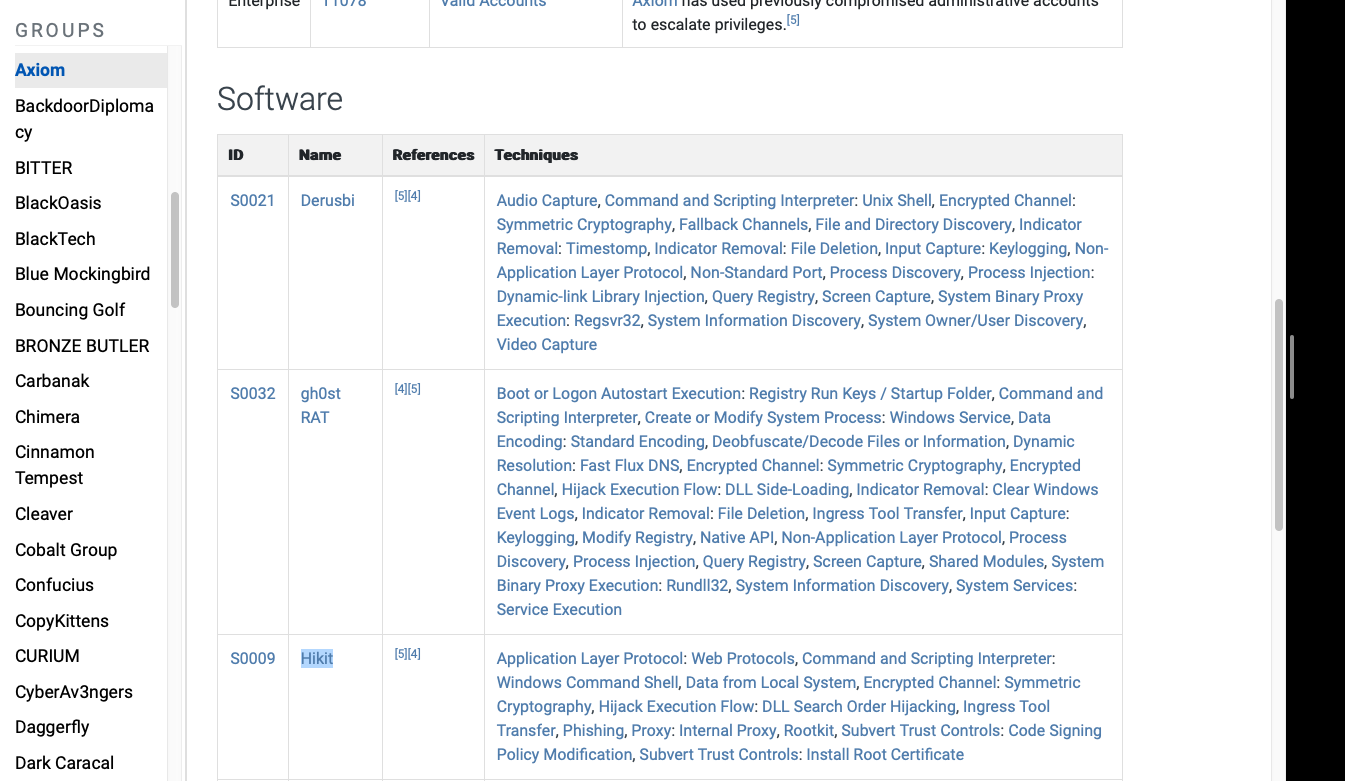
What is the description for this software?
Hikit is malware that has been used by Axiom for late-stage persistence and exfiltration after the initial compromise.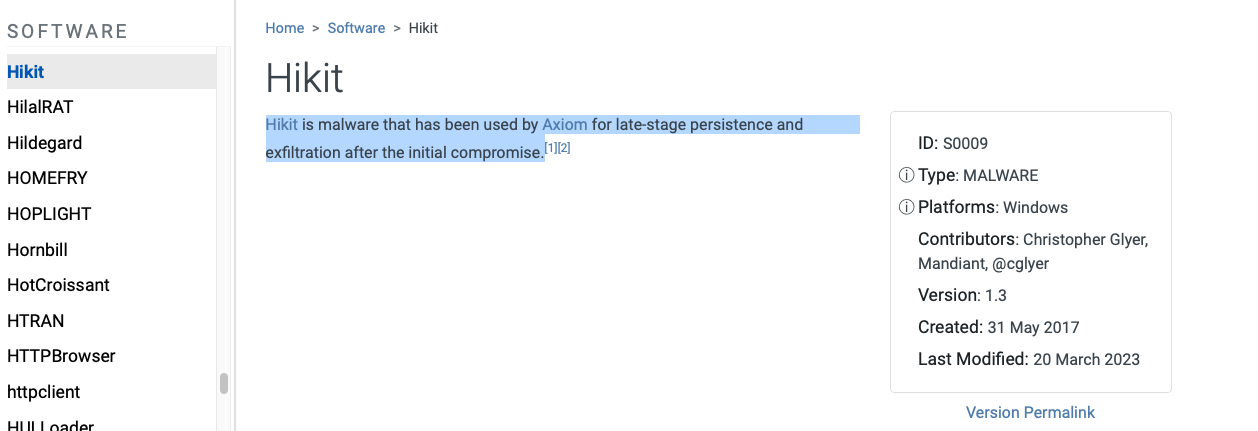
This group overlaps (slightly) with which other group?
Winnti Group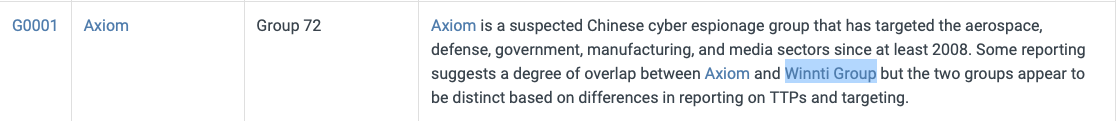
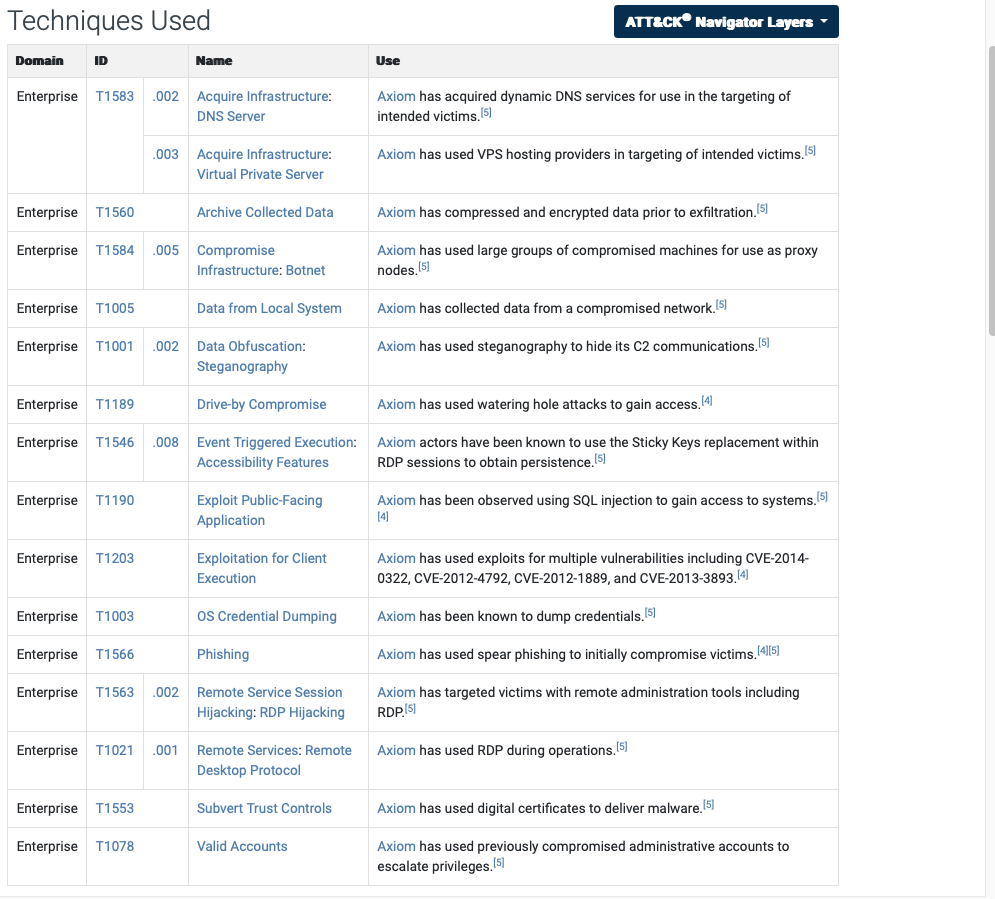
How many techniques are attributed to this group?
15count the number of enterprises/techniques but ignore ID that has two parts for example T1583, you count it as one technique
What tactic has an ID of TA0003?
Persistence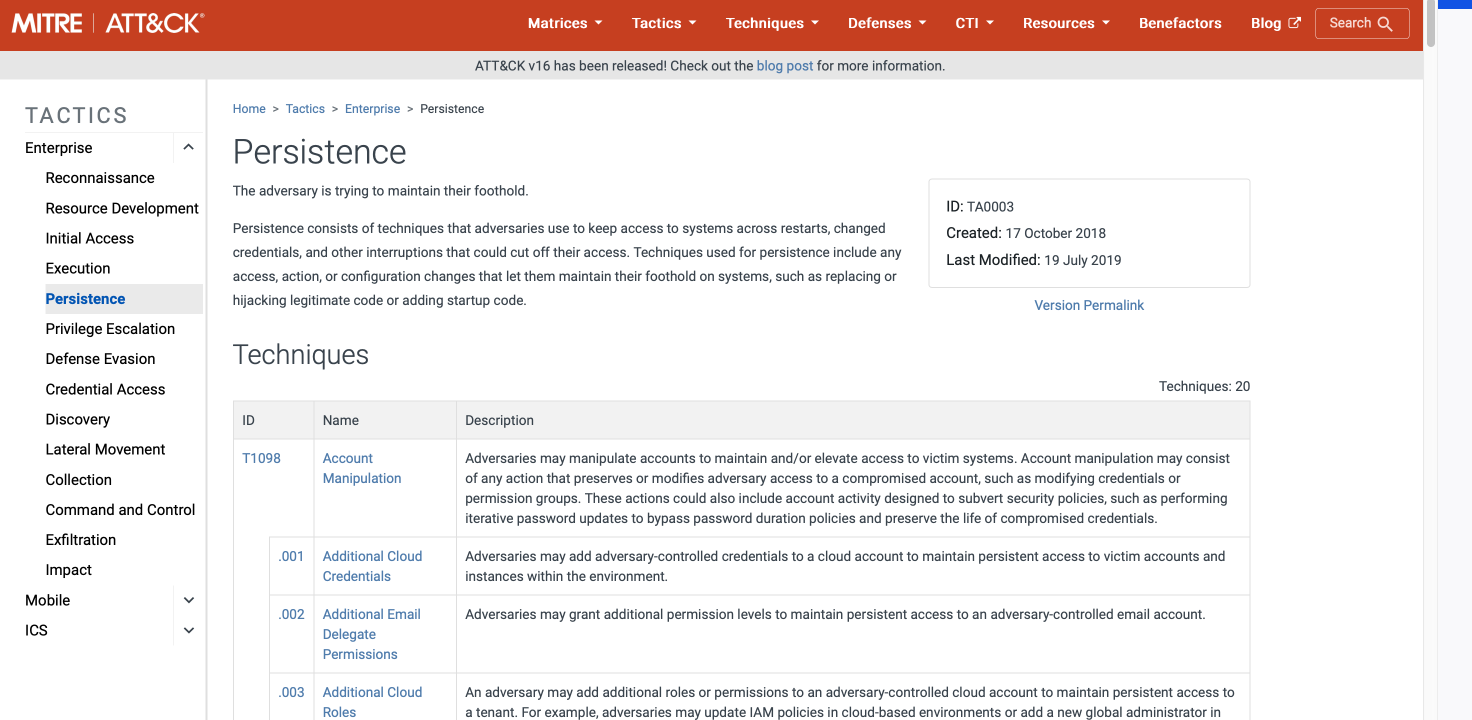
What is the name of the library that is a collection of Zeek (BRO) scripts?
BZAR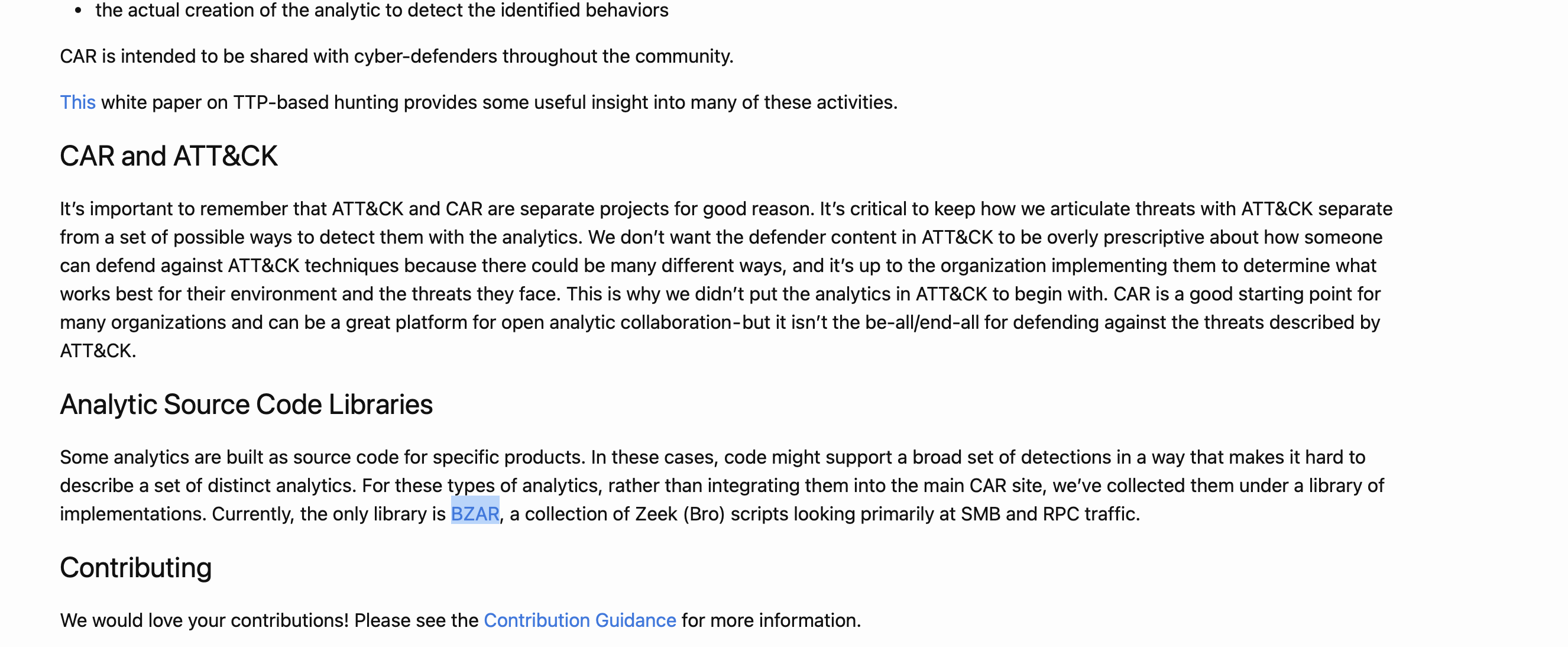
What is the name of the technique for running executables with the same hash and different names?
Masquerading
Examine CAR-2013-05-004, besides Implementations, what additional information is provided to analysts to ensure coverage for this technique?
Unit Tests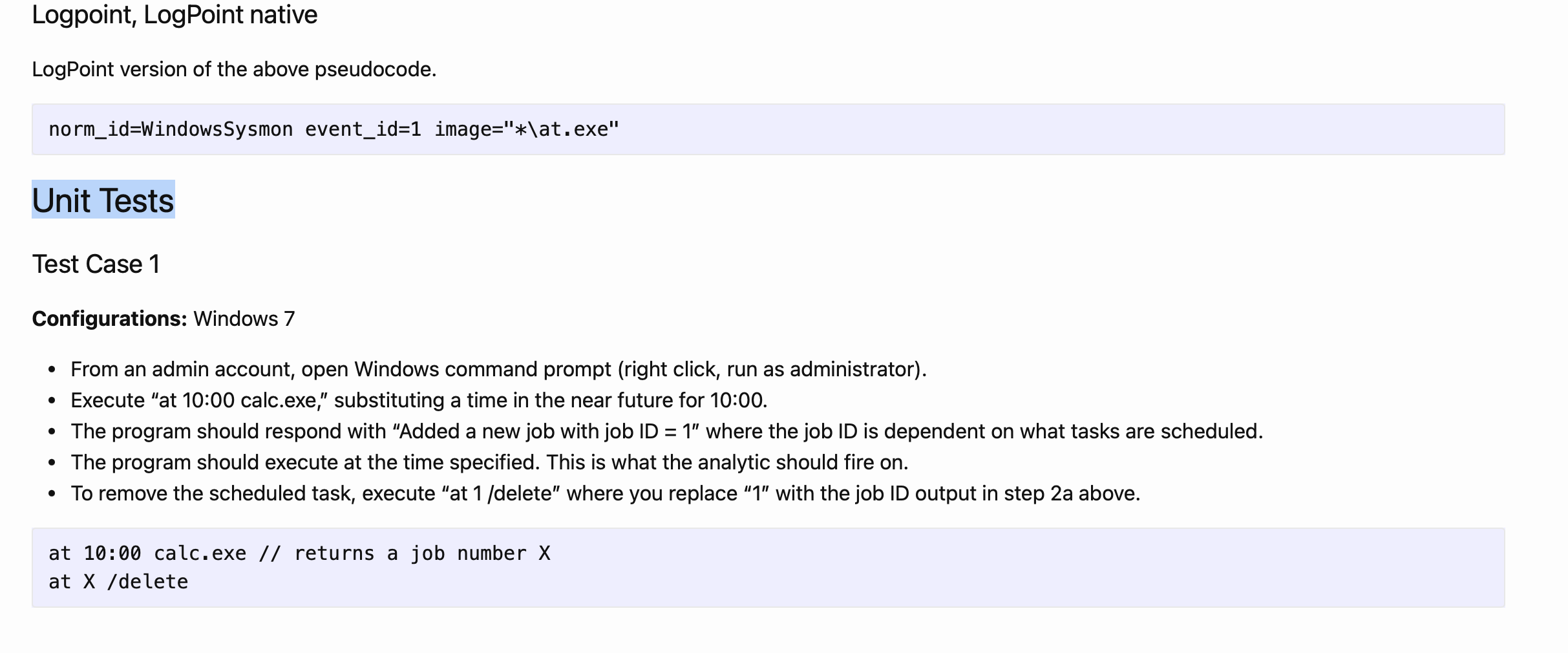
Under Prepare, what is ID SAC0002?
Persona Creation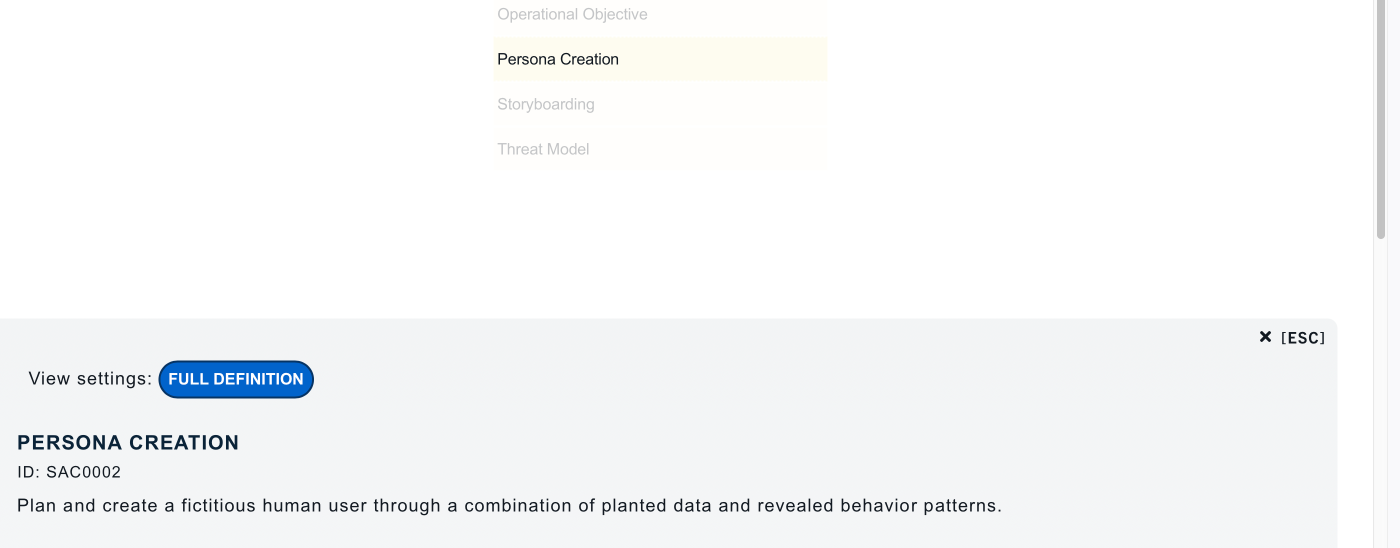
What is the name of the resource to aid you with the engagement activity from the previous question?
Persona Profile Worksheet
Which engagement activity baits a specific response from the adversary?
LuresWhat is the definition of Threat Model?
A risk assessment that models organizational strengths and weaknesses
What is the first MITRE ATT&CK technique listed in the ATT&CK Lookup dropdown?
Data Obfuscation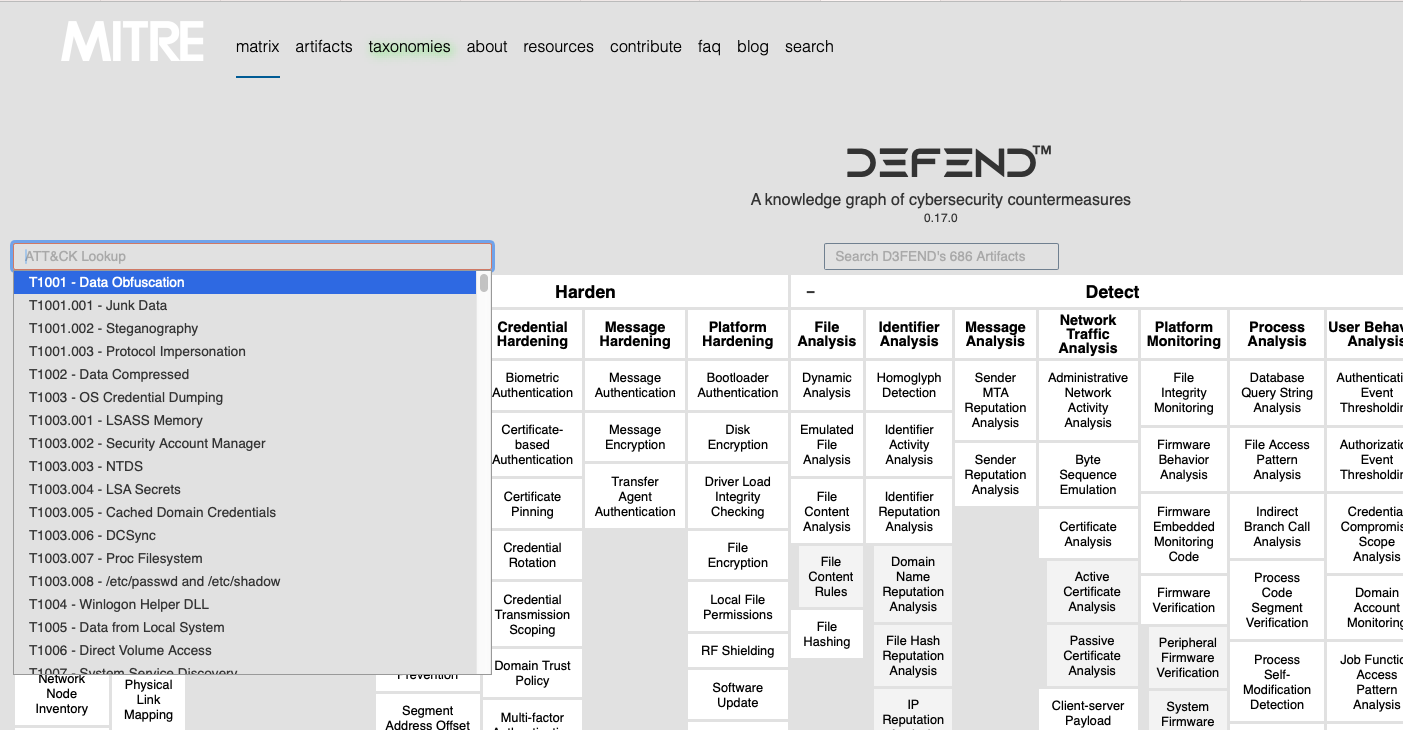
In D3FEND Inferred Relationships, what does the ATT&CK technique from the previous question produce?
Outbound Internet Network Traffic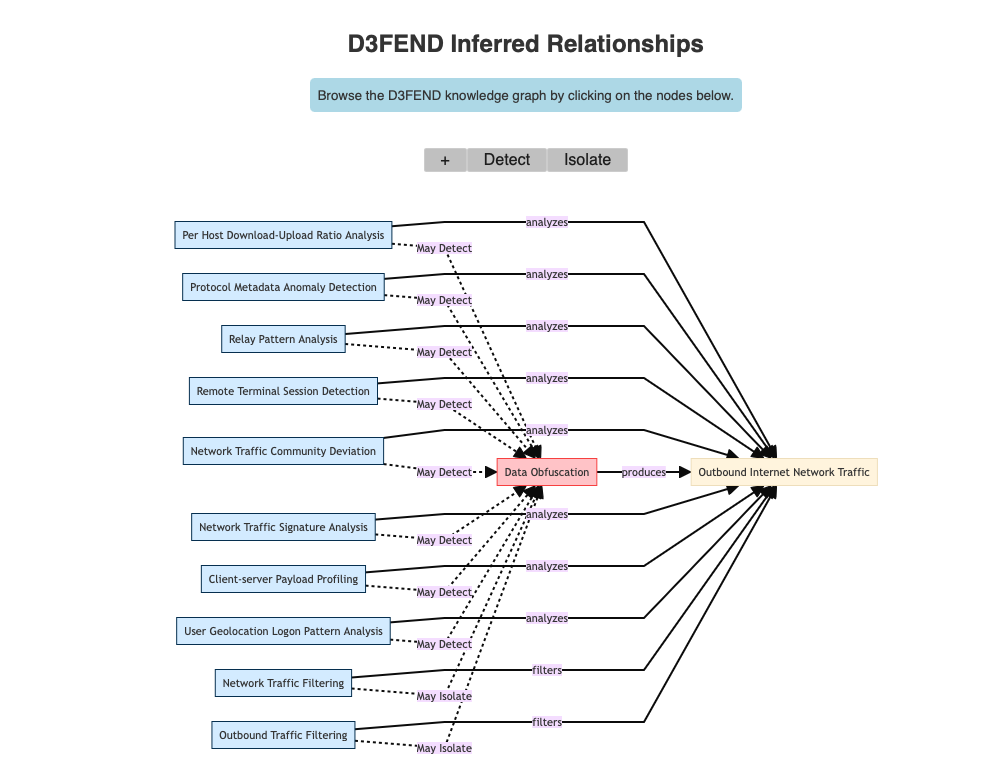
In Phase 1 for the APT3 Emulation Plan, what is listed first?
C2 Setup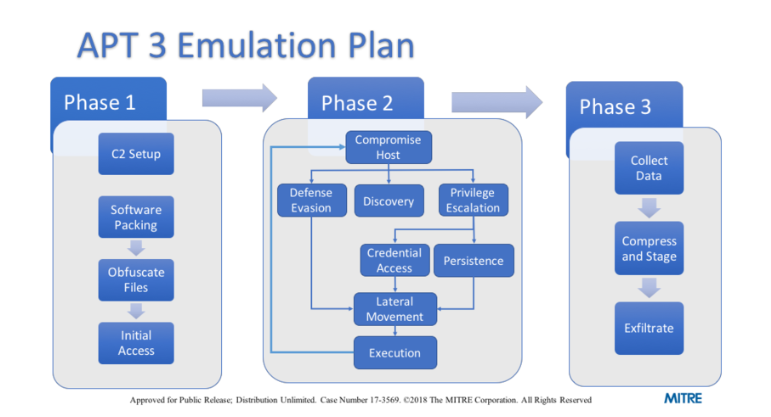
Under Persistence, what binary was replaced with cmd.exe?
sethc.exe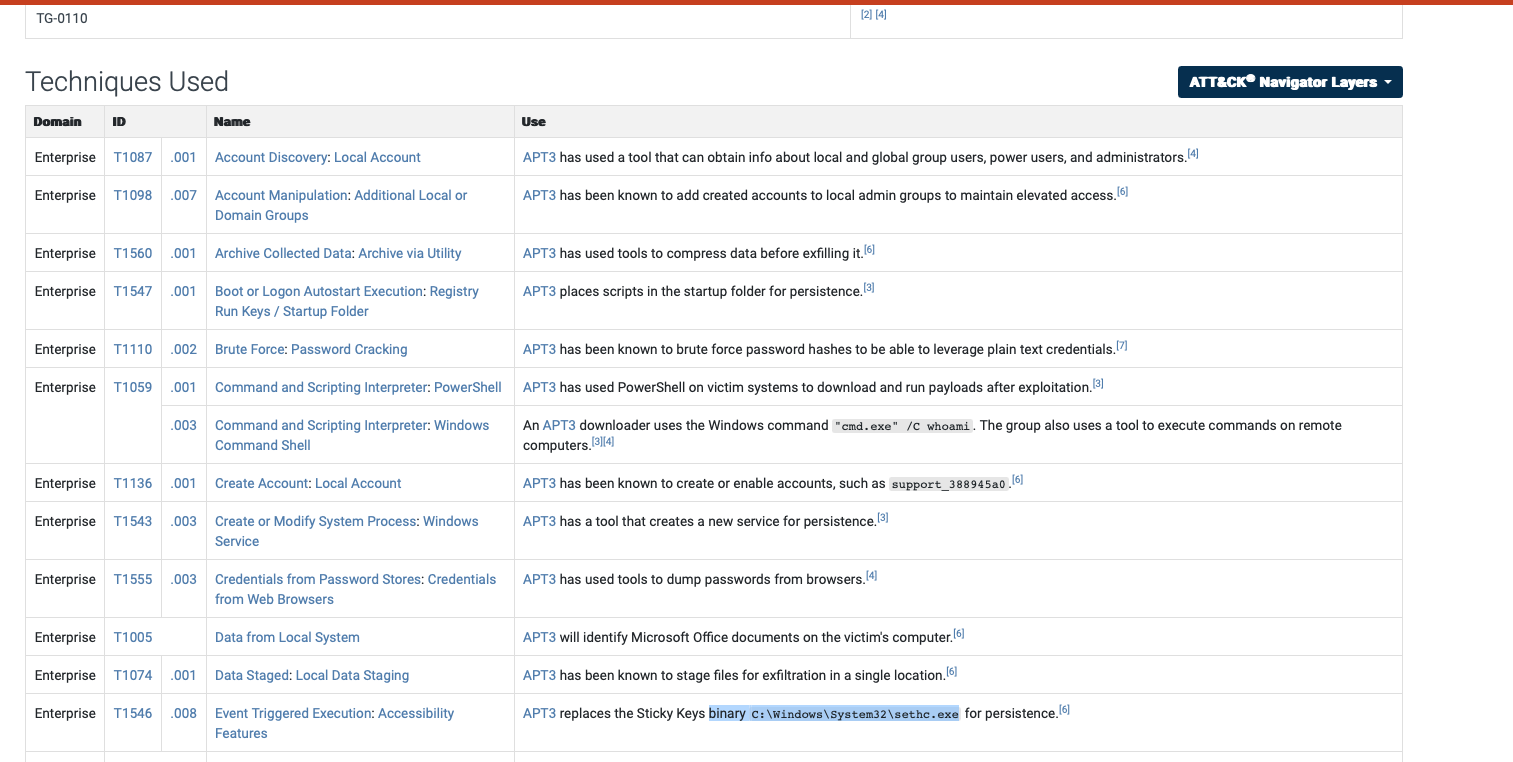
Examining APT29, what C2 frameworks are listed in Scenario 1 Infrastructure? (format: tool1,tool2)
Pupy,Metasploit Framework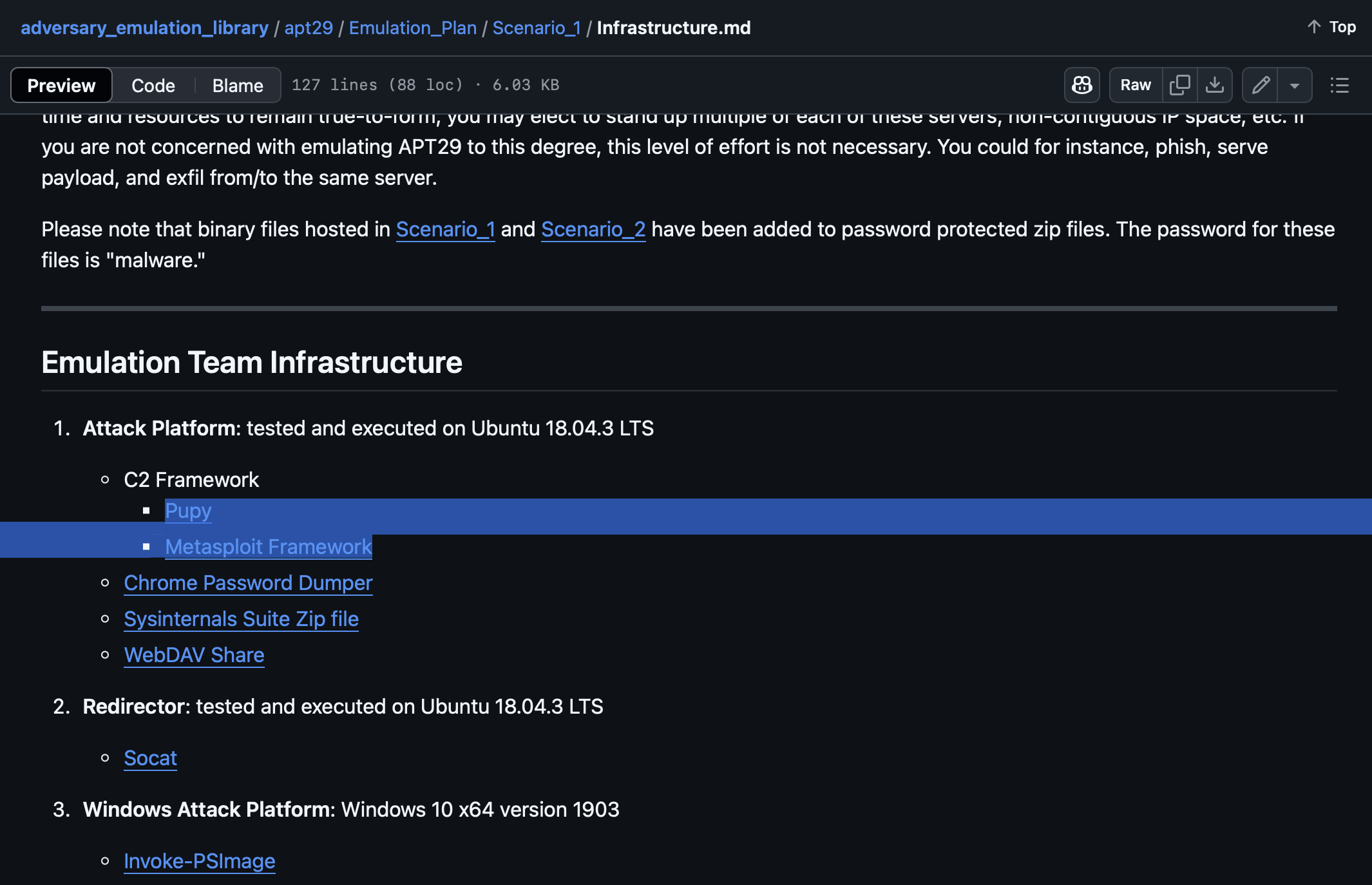
What C2 framework is listed in Scenario 2 Infrastructure?
PoshC2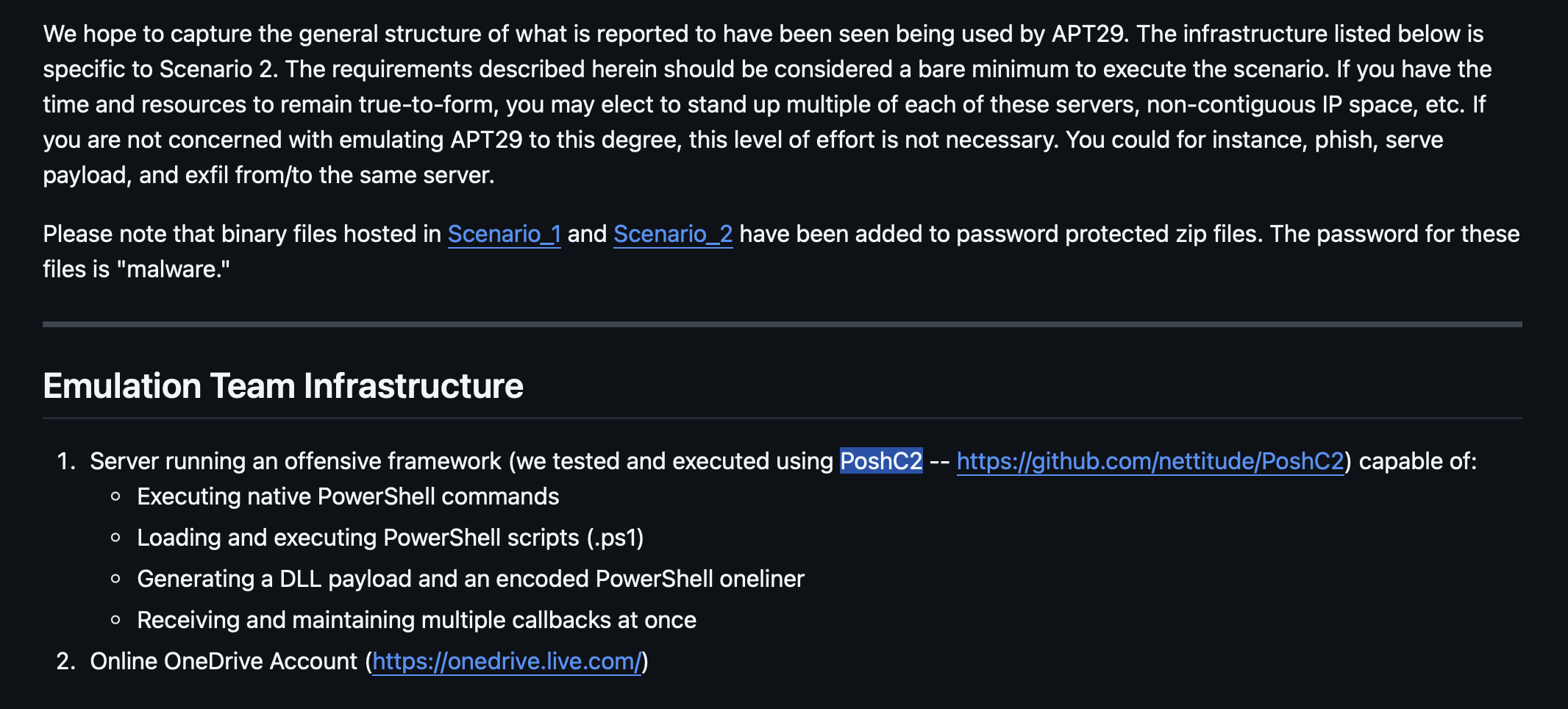
Examine the emulation plan for Sandworm. What webshell is used for Scenario 1? Check MITRE ATT&CK for the Software ID for the webshell. What is the id? (format: webshell,id)
P.A.S.,S0598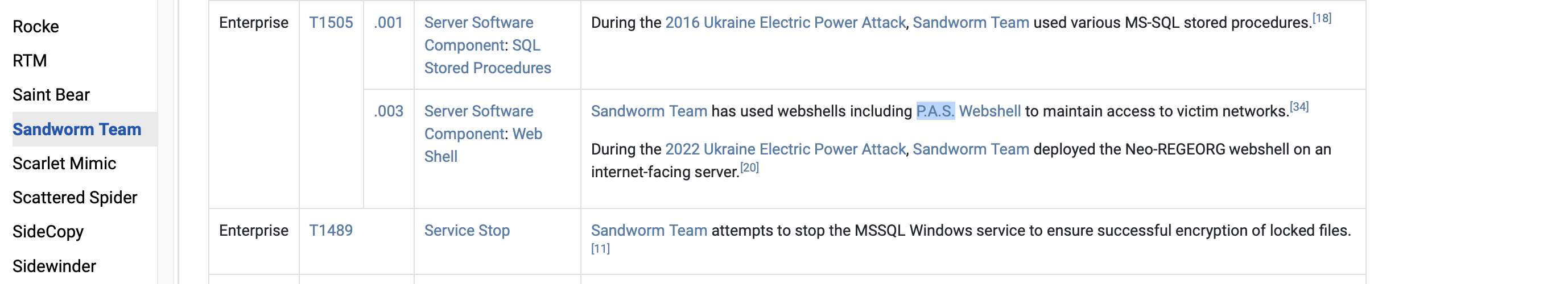
Install the ATT&CK Powered Suit browser extension on Chrome, Brave, or any other browser. Then open the extension by clicking the & icon then search P.A.S. and the ID (
S0598) will popup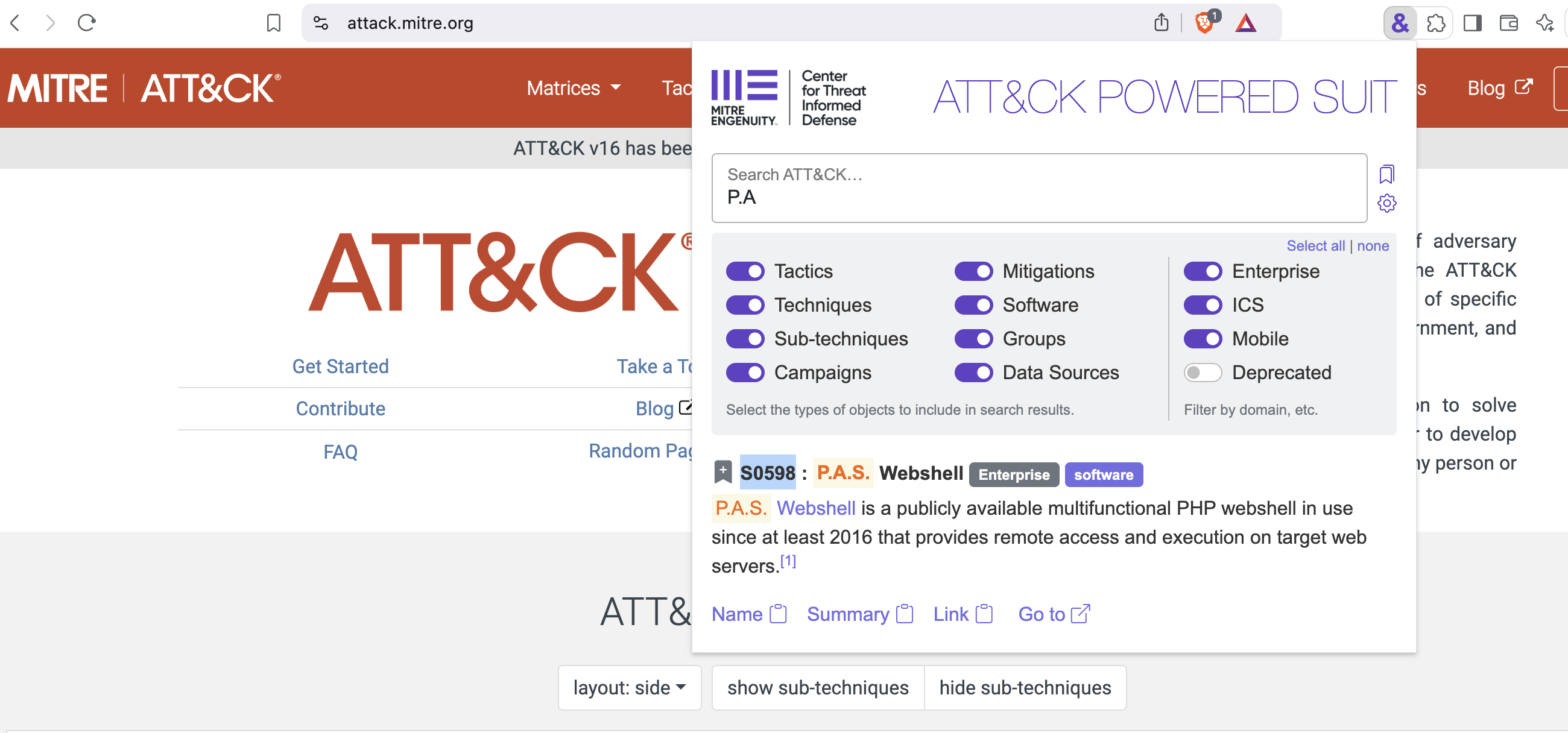
What is a group that targets your sector who has been in operation since at least 2013?
APT33
As your organization is migrating to the cloud, is there anything attributed to this APT group that you should focus on? If so, what is it?
Cloud Accounts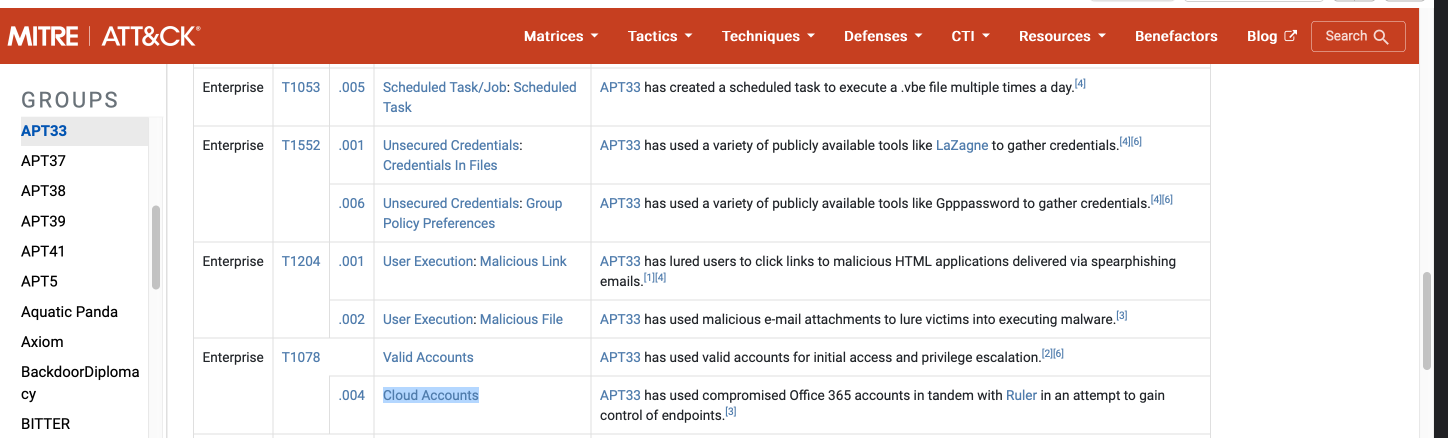
What tool is associated with the technique from the previous question?
Ruler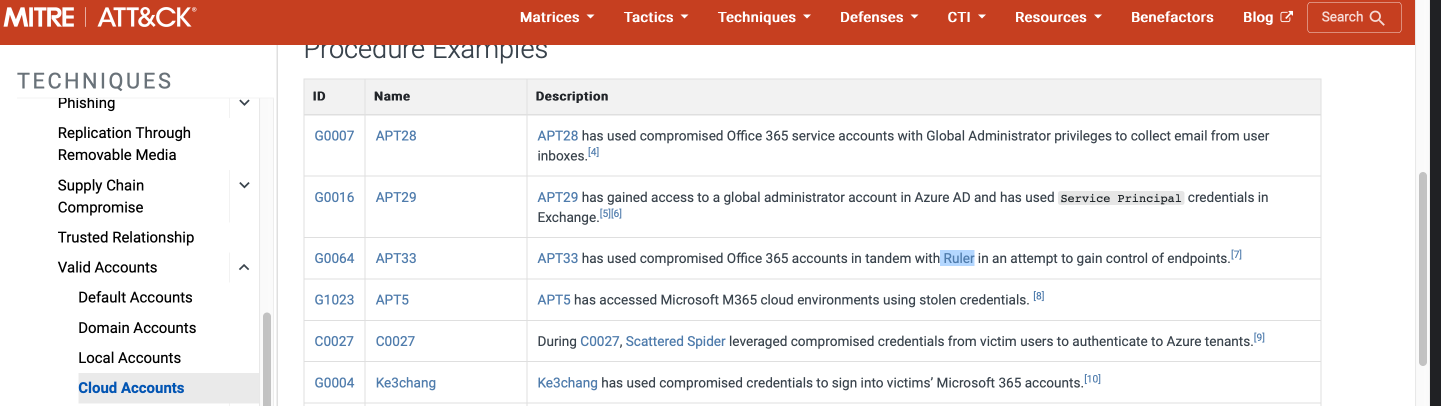
Referring to the technique from question 2, what mitigation method suggests using SMS messages as an alternative for its implementation?
Multi-factor Authentication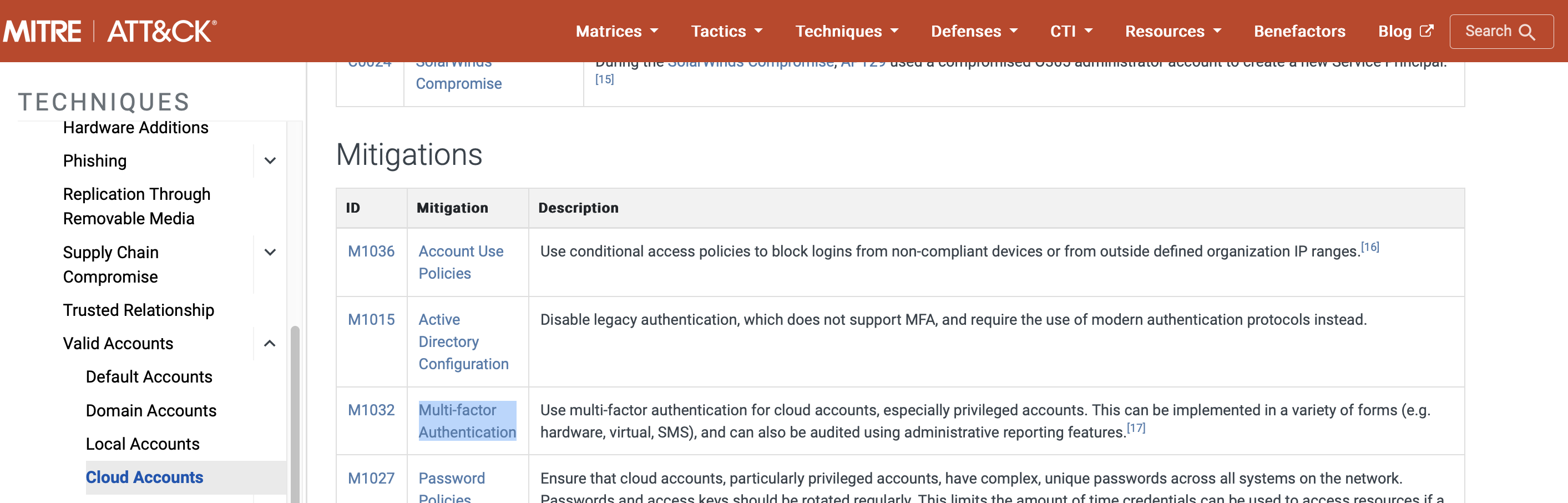
What platforms does the technique from question #2 affect?
Azure AD, Google Workspace, IaaS, Office 365, SaaSIn this room, we explored tools/resources that MITRE has provided to the security community. The room's goal was to expose you to these resources and give you a foundational knowledge of their uses. Many vendors of security products and security teams across the globe consider these contributions from MITRE invaluable in the day-to-day efforts to thwart evil. The more information we have as defenders, the better we are equipped to fight back. Some of you might be looking to transition to become a SOC analyst, detection engineer, cyber threat analyst, etc. These tools/resources are a must to know.
This is not only for defenders. As red teamers, these tools/resources are useful as well. Your objective is to mimic the adversary and attempt to bypass all the controls in place within the environment. With these resources, as the red teamer, you can effectively mimic a true adversary and communicate your findings in a common language that both sides can understand. In a nutshell, this is known as purple teaming.
This room made me like threat hunting and threat intelligence in general, I might consider it as a path.
Thank you for reading my article. Please leave any questions or comments on improving my learning journey and the THM challenges.
Subscribe to my newsletter
Read articles from Jebitok directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Jebitok
Jebitok
Software Developer | Learning Cybersecurity | Open for roles * If you're in the early stages of your career in software development (student or still looking for an entry-level role) and in need of mentorship, you can reach out to me.