Mastering AWS Load Balancers: CLB, ALB, NLB, GWLB & More! 🌐🚦
 Venkata Pavan Vishnu Rachapudi
Venkata Pavan Vishnu RachapudiTable of contents
- What Is a Load Balancer? 🤔
- Key Functions of a Load Balancer 🌐
- Types of Load Balancers in AWS ⚙️
- Detailed Load Balancer Components and Features 🔍
- Monitoring and Logging for Load Balancers 📊
- Common Load Balancing Algorithms
- Setting Up a CNAME for Custom Domain 📛
- Benefits of Using a Load Balancer 📈
- Load Balancer Use Cases 🎯
- Security Best Practices for Load Balancers 🔐
- Choosing the Right Load Balancer for Your Needs 🏗️

Load balancers play a pivotal role in cloud infrastructure, ensuring that traffic is distributed efficiently across resources for high availability, performance, and security. In AWS, you have multiple load balancer options to choose from, each serving unique use cases:
What Is a Load Balancer? 🤔
A Load Balancer is a critical network component that automatically distributes incoming network or application traffic across multiple servers or resources to ensure that no single server becomes overloaded. This not only improves the availability, performance, and reliability of your applications but also provides a seamless user experience by routing requests efficiently.
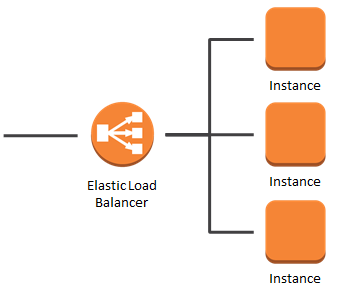
Key Functions of a Load Balancer 🌐
Traffic Distribution: Ensures that incoming traffic is spread across multiple targets (like EC2 instances, containers, or on-prem servers), preventing any single server from becoming a bottleneck.
High Availability: If one target becomes unavailable due to a failure, the load balancer automatically reroutes traffic to healthy targets, minimizing downtime.
Scalability: Dynamically manages traffic spikes by scaling resources up or down, making it easier to handle unexpected surges or seasonal fluctuations.
Security: Protects applications by terminating SSL/TLS connections, preventing unencrypted data from reaching backend servers, and integrating with security features like AWS WAF, Security Groups, and AWS Shield.
Session Persistence (Stickiness): Ensures that requests from the same user are routed to the same server throughout their session, useful for maintaining user state.
Connection Draining: Allows existing connections to gracefully close before an instance is de-registered or removed, ensuring no abrupt disconnections during maintenance.
Health Monitoring: Regularly checks the health of each registered target through health checks, ensuring traffic is only directed to healthy servers.
Cross-Zone Load Balancing: Distributes incoming traffic evenly across all registered targets in all enabled Availability Zones.
Server Name Indication (SNI): Supports multiple SSL/TLS certificates on the same load balancer, allowing it to handle multiple domains securely.
Types of Load Balancers in AWS ⚙️

- Classic Load Balancer (CLB): The traditional option, used primarily for applications built within the EC2-Classic network. Best for simple HTTP/HTTPS applications.
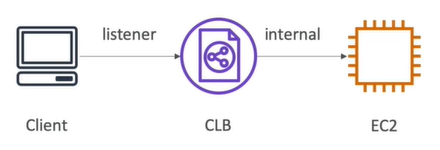
Application Load Balancer (ALB): Operates at the application layer (Layer 7) and is ideal for advanced routing, such as path-based or host-based routing, WebSockets, and HTTP/2 support.
Network Load Balancer (NLB): Functions at the transport layer (Layer 4), providing ultra-fast performance with static IPs. Ideal for TCP/UDP traffic where high-performance and low latency are critical.

- Gateway Load Balancer (GWLB): A specialized load balancer that integrates with virtual appliances, making it perfect for routing traffic through firewalls or deep packet inspection devices.

Detailed Load Balancer Components and Features 🔍
Listeners 🎧
Listeners are entry points for your load balancer. They monitor for incoming connection requests based on a protocol and port (like HTTP:80 or HTTPS:443). Once a request matches the listener criteria, it’s routed based on defined rules.
Target Groups 🎯
Targets (like EC2 instances, containers, or Lambda functions) are organized into target groups. Target groups allow load balancers to forward requests to specific backend services based on listener rules.
Health Checks ✅
Load balancers use health checks to monitor the status of each registered target. A healthy target receives traffic, while an unhealthy one is automatically bypassed until it recovers. Health checks can be customized based on protocol, path, interval, and other parameters.
Connection Draining (Deregistration Delay) 🕒
Connection draining (known as deregistration delay in some load balancers) allows in-flight requests to complete before deregistering an instance or shutting it down. Here’s why it’s important:
Graceful Handling: Prevents existing sessions from dropping abruptly when you remove or de-register an instance from the target group.
Maintenance: Useful during scheduled maintenance or scaling down operations, ensuring that no active connections are interrupted.
Customization: You can set the timeout duration (up to a certain limit) for connection draining in both ALB and NLB, allowing existing sessions to complete gracefully.
Session Stickiness (Session Persistence) 📌
Session stickiness (or sticky sessions) is a feature that binds a user’s session to a specific target for a given duration:
Use Case: Essential for applications where the server needs to maintain user data or session state, like e-commerce websites, to ensure the shopping cart persists across requests.
Mechanism: The load balancer creates a cookie that identifies the session and sends subsequent requests from the same user to the same target.
Configuration: For ALB, stickiness can be configured at the target group level, while for CLB, you set it at the load balancer level using session cookies.
Global Accelerator 🌍
AWS Global Accelerator improves the availability and performance of your applications with static IP addresses that route traffic to your endpoints in multiple AWS Regions. Unlike traditional DNS-based routing, Global Accelerator leverages the AWS global network, offering robust routing with low latency.
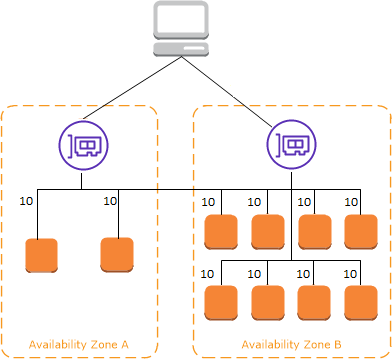
Cross-Zone Load Balancing 🌐
Cross-Zone Load Balancing enables even traffic distribution across targets in multiple Availability Zones, regardless of how many targets are registered in each zone:
Improved Load Distribution: Without Cross-Zone Load Balancing, traffic is routed based on the number of targets in each Availability Zone, which can lead to uneven load distribution if one zone has more targets than another.
Enhanced Availability: Ensures that each target receives an even share of traffic, regardless of the number of instances in a particular Availability Zone.
Configuration:
For ALB, Cross-Zone Load Balancing is enabled by default.
For NLB and CLB, it can be enabled or disabled according to your requirements.
Cost Considerations: With Cross-Zone Load Balancing enabled, you may incur additional data transfer costs for traffic routed across zones, so it's important to understand the pricing implications.
Server Name Indication (SNI) for SSL/TLS 🛡️
SNI is an extension of the TLS protocol that allows multiple SSL/TLS certificates to be associated with the same IP address and port:
Multiple Domain Support: Ideal for hosting multiple secure websites (HTTPS) on the same load balancer, without the need for a unique IP address per domain.
How It Works: During the SSL/TLS handshake, the client specifies the hostname it’s trying to reach. The load balancer uses this information to select the appropriate SSL/TLS certificate for the requested domain.
Use Case: ALB and NLB support SNI, making it easier to manage multiple domains securely under a single load balancer. This is particularly beneficial for scenarios like multi-tenant applications or serving distinct SSL certificates for different domains.
Setup: In AWS, you can upload multiple SSL certificates to the load balancer and specify the default certificate along with domain-specific ones using SNI.

Monitoring and Logging for Load Balancers 📊
Monitoring and logging are crucial for maintaining an efficient load-balancing setup. Here are key aspects to consider:
Access Logs 📝
Access Logs provide detailed records of requests processed by the load balancer.
Storage: Can be sent to Amazon S3 for long-term storage or CloudWatch Logs for real-time monitoring and alerting.
Setup: Enable Access Logs via the load balancer’s settings in the AWS Console, specifying the target S3 bucket or CloudWatch log group.
Use Case: Ideal for security audits, analyzing user behavior, and understanding traffic patterns.
Monitoring with AWS CloudWatch 📈
Use CloudWatch Metrics to monitor the health and performance of your load balancer.
Metrics include request count, healthy/unhealthy hosts, latency, and more.
You can create CloudWatch Alarms based on thresholds (e.g., high response latency or increased error rates) to get notified of potential issues.
Tracing with AWS X-Ray 🌐
AWS X-Ray allows you to trace requests as they pass through the load balancer to backend resources.
Benefit: Provides detailed information on response times, bottlenecks, and end-to-end visibility of your application’s architecture.
Common Load Balancing Algorithms

Round Robin 📜
How It Works: The simplest and most common algorithm. It distributes requests evenly across all available backend servers in a cyclic manner.
Pros:
Easy to implement.
Ideal for applications where each backend server has roughly equal processing power and capacity.
Cons:
- Does not take into account server health or load, meaning a heavily loaded server could receive more requests.
Least Connections 💻
How It Works: This algorithm routes traffic to the server with the least number of active connections.
Pros:
More efficient for scenarios where some servers may have long-lasting or resource-intensive connections.
Ensures even distribution based on current load, improving response times.
Cons:
- Can be less effective if servers have different capabilities or if traffic volume is highly variable.
Weighted Round Robin ⚖️
How It Works: An enhanced version of round robin, where each backend server is assigned a weight based on its capacity. Servers with higher weights receive more requests.
Pros:
- Great for situations where backend servers have different capacities (e.g., one server is more powerful than the others).
Cons:
- Requires manual configuration of weights.
Setting Up a CNAME for Custom Domain 📛
To make your load balancer accessible through a friendly URL (e.g., myapp.example.com), follow these steps:
Domain Setup: Ensure you have a registered domain.
DNS Configuration: In your DNS provider (like Route 53 or GoDaddy), create a CNAME record pointing to the DNS name of your load balancer.
SSL/TLS Configuration: If using HTTPS, set up an SSL certificate via AWS Certificate Manager (ACM) and attach it to the load balancer.
Test & Verify: Check DNS propagation and confirm that the CNAME resolves to the load balancer’s DNS name.
Benefits of Using a Load Balancer 📈
Improved Performance: Load balancers optimize resource usage by evenly distributing traffic, which results in faster response times.
Reduced Downtime: By rerouting traffic to healthy instances, load balancers minimize the risk of downtime during server failures.
Enhanced Security: Load balancers act as a front line of defense, managing SSL/TLS termination, integrating with WAF, and filtering out malicious traffic.
Scalable Infrastructure: They allow infrastructure to scale up or down dynamically, depending on the demand, without impacting the end-users.
Simplified Maintenance: Load balancers can take servers offline for maintenance without disrupting service availability.
Load Balancer Use Cases 🎯
E-commerce Websites: Handle millions of requests daily, ensuring customers have a seamless experience even during peak sales.
API Gateways: Route API requests to microservices and manage traffic effectively.
Gaming Platforms: Distribute high-frequency, low-latency traffic among game servers to provide a smooth gaming experience.
Financial Systems: Manage secure transactions and ensure minimal downtime for trading platforms.
Security Best Practices for Load Balancers 🔐
HTTPS/TLS Termination: Terminate SSL/TLS at the load balancer to encrypt traffic, ensuring data is secure between clients and the load balancer.
Use Web Application Firewall (WAF): Integrate AWS WAF with your ALB to protect against common web vulnerabilities (like SQL injection and XSS attacks).
Restrict Access with Security Groups: Use Security Groups to limit access to the load balancer, allowing only trusted IP addresses or networks.
Enable Access Logs: Turn on Access Logs to capture details about every request processed by the load balancer, useful for security auditing.
DDoS Protection: Utilize AWS Shield (standard or advanced) to safeguard against DDoS attacks.
Private Load Balancers: Use internal load balancers for apps that don’t need to be accessed over the internet, limiting exposure.
Route Traffic Through VPC Endpoints: Use VPC endpoints for private communication between load balancers and backend services within AWS, bypassing the public internet.
Choosing the Right Load Balancer for Your Needs 🏗️
If you need simple load balancing for a legacy app, go with CLB.
For modern web applications needing advanced routing, ALB is the way to go.
When low latency and high throughput are crucial, choose NLB.
For integrating third-party appliances like firewalls, look at GWLB.
Subscribe to my newsletter
Read articles from Venkata Pavan Vishnu Rachapudi directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Venkata Pavan Vishnu Rachapudi
Venkata Pavan Vishnu Rachapudi
I'm Venkata Pavan Vishnu, a cloud enthusiast with a strong passion for sharing knowledge and exploring the latest in cloud technology. With 3 years of hands-on experience in AWS Cloud, I specialize in leveraging cloud services to deliver practical solutions and insights for real-world scenarios. Whether it's through engaging content, cloud security best practices, or deep dives into storage solutions, I'm dedicated to helping others succeed in the ever-evolving world of cloud computing. Let's connect and explore the cloud together!