Cyber Threat Intelligence: Intro to Cyber Threat Intel (TryHackMe)
 J3bitok
J3bitok
In this article, I will write an Intro to Cyber Threat Intel write-up: The Basics that covers Introduction, Cyber Threat Intelligence, CTI Lifecycle, and CTI Standards & Frameworks.
What does CTI stand for?
Cyber Threat IntelligenceIP addresses, Hashes and other threat artefacts would be found under which Threat Intelligence classification?
Technical IntelAt which phase of the CTI lifecycle is data converted into usable formats through sorting, organising, correlation and presentation?
ProcessingDuring which phase do security analysts get the chance to define the questions to investigate incidents?
DirectionWhat sharing models are supported by TAXII?
Collection and ChannelWhen an adversary has obtained access to a network and is extracting data, what phase of the kill chain are they on?
Actions on ObjectivesWhat was the source email address?
vipivillain@badbank.com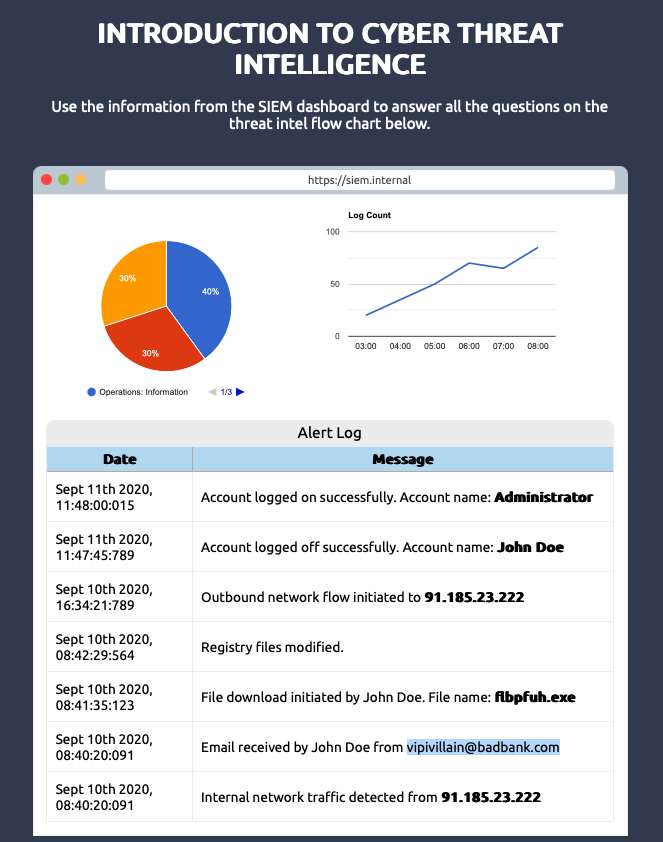
What was the name of the file downloaded?
flbpfuh.exe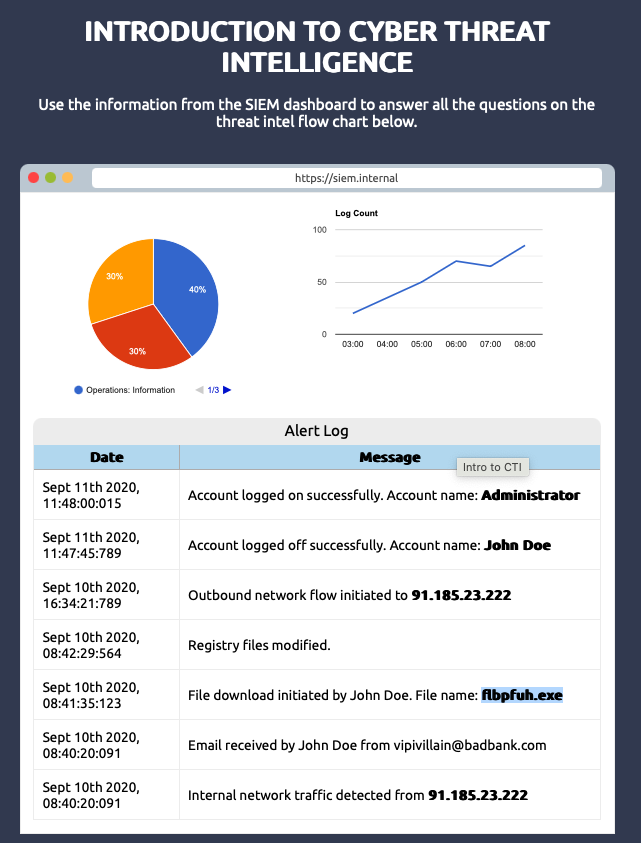
After building the threat profile, what message do you receive?
THM{NOW_I_CAN_CTI}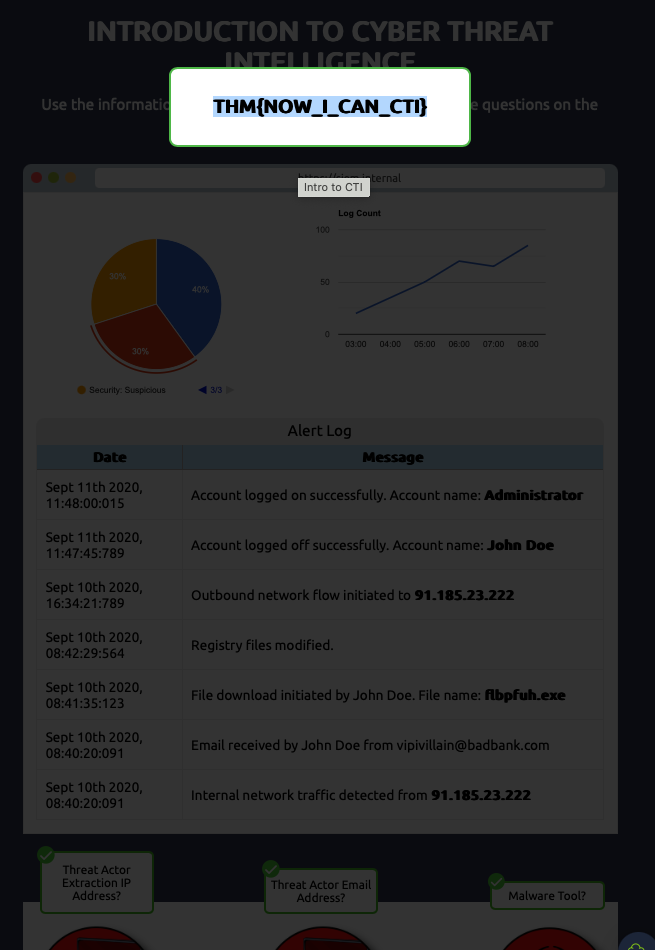
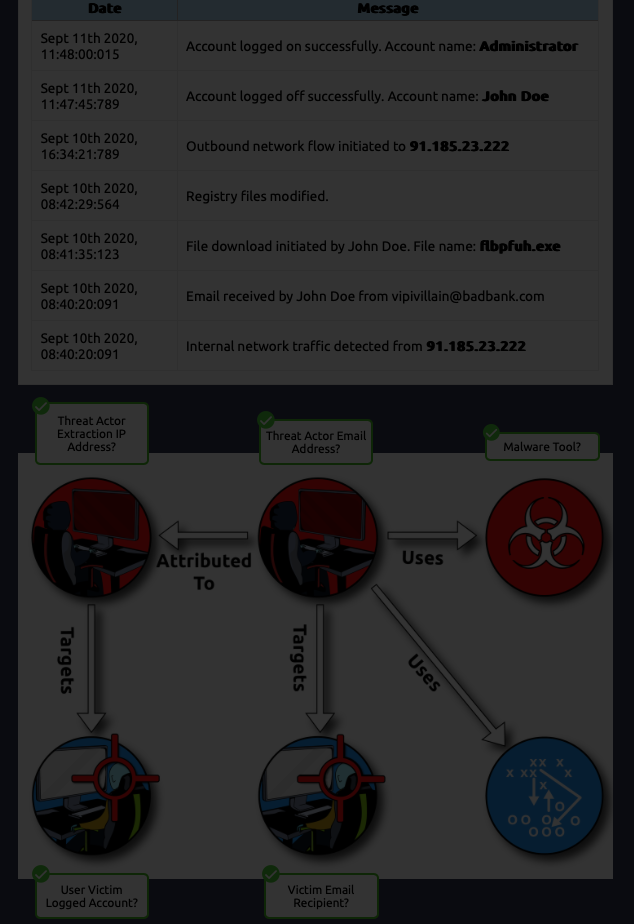
Threat Actor Extraction IP Address:
91.185.23.222Threat Actor Email Address: vipivillain@badbank.com
Malware Tool:
flbpfuh.exeUser Victim Logged Account:
AdministratorVictim Email Recipient:
John Doe
Thank you for reading my article. Please leave any questions or comments on improving my learning journey and the THM challenges. We can also connect more on LinkedIn or X.
Subscribe to my newsletter
Read articles from J3bitok directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

J3bitok
J3bitok
Software Developer Learning Cloud and Cybersecurity Open for roles * If you're in the early stages of your career in software development (student or still looking for an entry-level role) and in need of mentorship you can book a session with me on Mentorlst.com.