Mastering AWS IAM: A Beginner's Guide to Secure Cloud Access
 Shivam Dubey
Shivam Dubey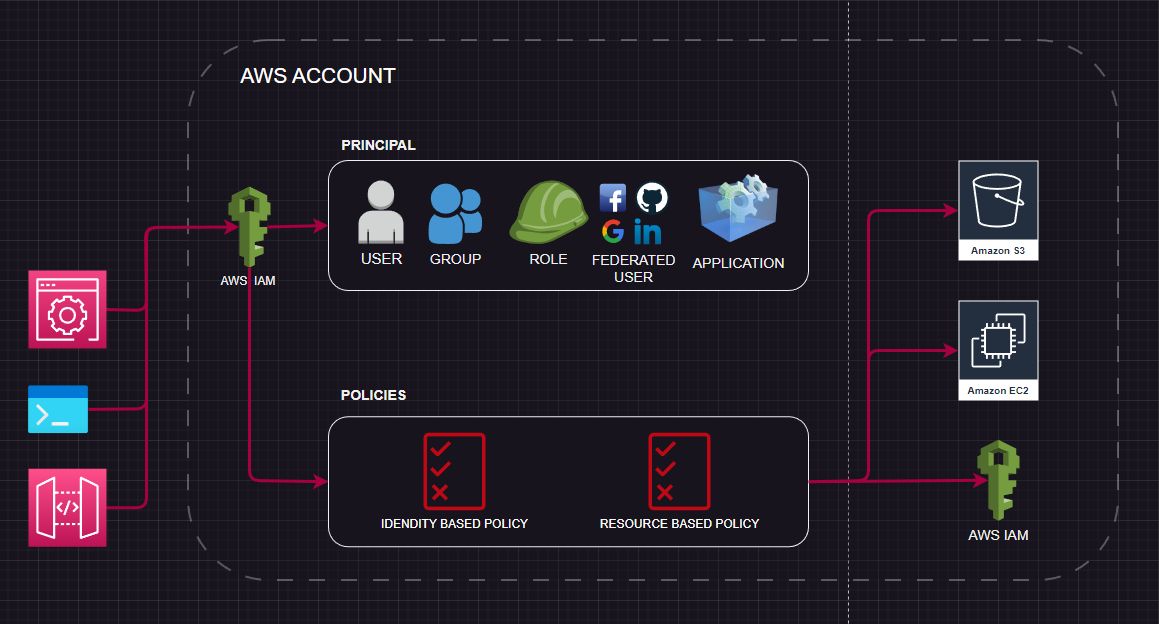
If you’re new to AWS, one of the first services you should learn is AWS Identity and Access Management (IAM). It’s a powerful tool that helps you securely manage access to your AWS resources, ensuring that the right people and services have the right permissions. Let’s dive into IAM step by step, making it simple and easy to understand.
What is AWS IAM?
AWS Identity and Access Management (IAM) is a service that lets you control who can access your AWS resources and what they can do. Think of it as AWS’s security system. You use IAM to define who can access your AWS environment, what actions they can take, and which resources they can interact with.
Why Do You Need IAM?
Without IAM, anyone who has your AWS credentials could access everything in your AWS account. IAM helps you:
Control access to your AWS resources securely.
Protect sensitive data.
Simplify user management.
Key Concepts of IAM
Understanding a few basic terms will help you get started quickly:
1. Users
Users are individual accounts for people who need access to AWS. Each user can have unique permissions.
Example: A user could be a developer, an administrator, or a data analyst who logs into the AWS Console.
2. Groups
Groups are collections of users. Instead of assigning permissions to individual users, you can add users to a group and manage their permissions as a unit.
Example: You can create a "Developers" group and give it permissions to access code repositories and development servers.
3. Roles
Roles are sets of permissions that can be temporarily assumed by users or services. Roles are not tied to a specific user and are often used by applications and AWS services.
Example: An EC2 instance can assume a role to access an S3 bucket without needing permanent credentials.
4. Policies
Policies are documents written in JSON that define permissions. They specify what actions are allowed or denied on specific AWS resources.
Example: A policy might allow users to read files in an S3 bucket but not delete them.
5. Root User
- The root user is the account you create when you first sign up for AWS. It has full access to all AWS services and resources. However, it’s recommended to use the root user only for initial setup and secure it with multi-factor authentication (MFA).
Getting Started with IAM: Step-by-Step
Step 1: Secure Your Root Account
Log in to AWS with your root account.
Set up multi-factor authentication (MFA) to add an extra layer of security.
Create an IAM user for yourself and use it for everyday tasks instead of the root account.
Step 2: Create an IAM User
Go to the AWS Management Console and open the IAM Dashboard.
Click on Users in the left panel, then click Add user.
Enter a username and select the type of access:
Console access: If the user needs to log into the AWS Management Console.
Programmatic access: If the user needs to use AWS CLI or API.
Click Next: Permissions.
Step 3: Set Permissions Using Groups
Instead of giving permissions directly, add the user to a group.
Click Create group, enter a group name (e.g., "Admins"), and choose a predefined policy like AdministratorAccess.
Click Create group, then Next: Tags.
Add optional tags for easier tracking, then click Create user.
Step 4: Enable MFA for IAM Users
Select the IAM user you created.
Go to the Security credentials tab and click Assign MFA device.
Follow the instructions to link an MFA app on your phone.
Step 5: Create an IAM Role for an EC2 Instance
Open the IAM Dashboard and click Roles > Create role.
Select AWS service and choose EC2.
Click Next: Permissions and attach a policy (e.g., AmazonS3ReadOnlyAccess).
Give your role a name and click Create role.
Attach this role to an EC2 instance when launching it, so the instance can access the S3 bucket without storing credentials on the server.
Understanding IAM Policies
IAM policies are the rules that define permissions. Each policy is a JSON document with the following structure:
Effect: Whether the policy allows or denies access.
Action: The specific AWS actions (e.g.,
s3:GetObject) the policy applies to.Resource: The AWS resources (e.g.,
arn:aws:s3:::my-bucket/*) the policy applies to.
Example Policy
This policy allows a user to list the contents of an S3 bucket:
jsonCopy code{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Action": "s3:ListBucket",
"Resource": "arn:aws:s3:::example-bucket"
}
]
}
IAM Best Practices
To make your AWS environment secure and efficient, follow these best practices:
Enable MFA: Add an extra layer of security for all users.
Use Groups for Permissions: Instead of assigning permissions to individual users, use groups.
Follow the Principle of Least Privilege: Only grant the permissions users need to perform their tasks.
Rotate Access Keys Regularly: Change API keys periodically to reduce the risk of unauthorized access.
Monitor Activity with CloudTrail: Use AWS CloudTrail to log and monitor all IAM actions for auditing purposes.
Advanced IAM Features
IAM Access Analyzer
- IAM Access Analyzer helps you identify any resources that are accessible from outside your AWS account. This tool is useful for ensuring that your resources are not unintentionally exposed.
IAM Roles for Cross-Account Access
- You can use roles to grant users in one AWS account access to resources in another account. This is useful for organizations with multiple AWS accounts.
Conclusion
AWS IAM is a powerful and essential tool for managing access to your AWS resources. By understanding users, groups, roles, and policies, you can build a secure environment tailored to your organization’s needs. Start small by creating a few users and groups, then gradually explore advanced features like roles and IAM Access Analyzer.
Remember, IAM is all about security and control. Take your time to set it up correctly, and regularly review your permissions to ensure they align with your needs. For the most up-to-date information, always refer to the official AWS IAM documentation.
Happy cloud computing! ☁️🔒
Subscribe to my newsletter
Read articles from Shivam Dubey directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by
