Petshop Pro Walkthrough
 WalkingEclipse
WalkingEclipse
Flag 0 …
Hints:
Something looks out of place with checkout.
It’s always nice to get stuff free.
To find this flag we have to figure out a way to get a JPEG for free.
As you can see on the homepage there are two JPEGS that can be added to the cart. If you add one to the cart and proceed to check out you will see Payments temporarily disabled message displayed.

So how can we check out and get the JPEG for free?
Let’s start by inspecting the Check Out button located in the Shopping Cart page.
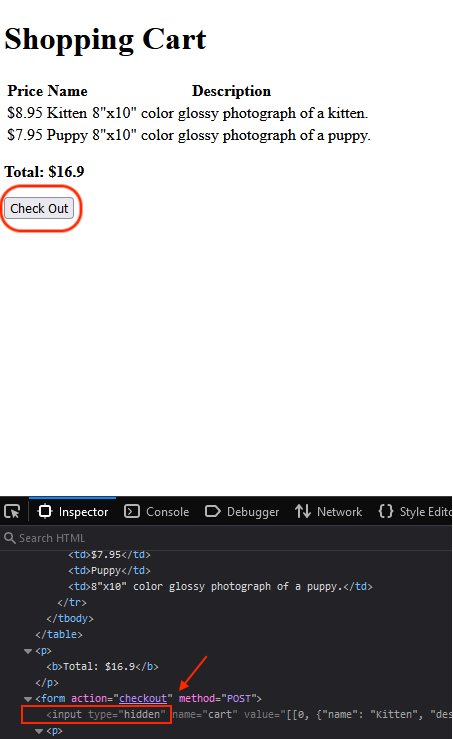
Upon inspection we can see that there is something hidden in the form. To find out what it is we need to erase the text hidden next to type. An input box should pop up on the webpage. The price needs to be changed to zero and this can be done through that box or from the Inspector section.
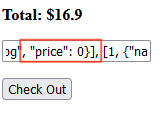
Once the price is set to ZERO go ahead and click on the Check Out button.
Your FLAG should appear!

Flag 1 …
Hints:
There must be a way to administer the app.
Tools may help you find the entry point.
Tools are also great for finding credentials.
It looks like we need to find a way to login as an admin to take control over the webpage.
Note: You must prepare yourself because to find this flag there are several steps to take.
Let’s go back to the Home page. There are no buttons or links to click on to log in so the next step is to try commonly used login paths.
Try using /admin at the end of the URL. Okay, that did not work.
Let’s try /login this time. Bingo, we got us a winner!
Once the login page loads go ahead and try using default admin usernames and passwords. I tried using the following:
Usernames: admin, administrator, user
Password: admin, password, 12345
Each combination produced a Invalid username message. This message is important because it let’s us know which credential is invalid.
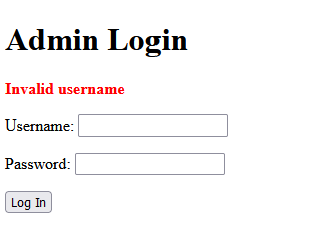
It’s clear that we need help from tools to brute force our way in. I tried using Hydra but it was acting up so I used Burp Suite Community with the Turbo Intruder extension.
Step One:
Open Burp Suite.
* If you already have the Turbo Intruder extension installed skip to Step 2.
To install the Turbo Intruder extension go to Extensions tab > BApp Store > Search bar > type in Turbo Intruder > Click Install
Once it’s done installing the Turbo Intruder tab should populate at the top.
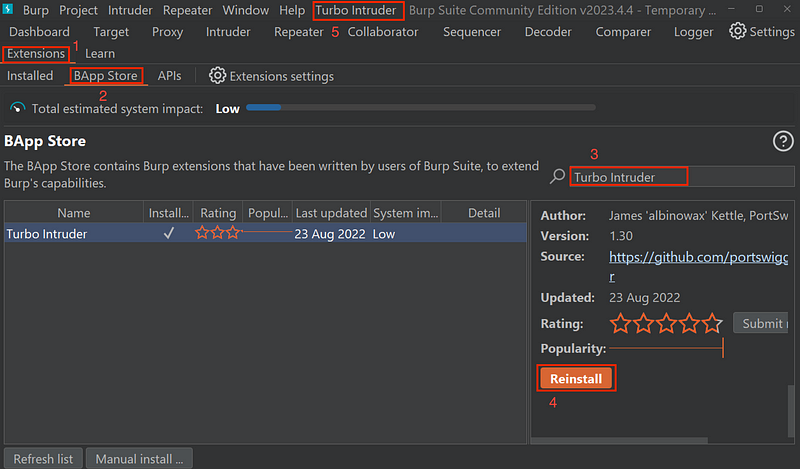
Tutorial: If you are a visual learner here is a step by step video to help you out, Turbo Intruder Tutorial.
Now, the fun part begins …
Step Two:
Go to the Proxy tab in Burp Suite.
Turn on the proxy on the browser.
Go back to Burp Suite and click Intercept is off to turn in on
Go back to the webpage and try to log in using any credentials.
Burp should capture this interaction.
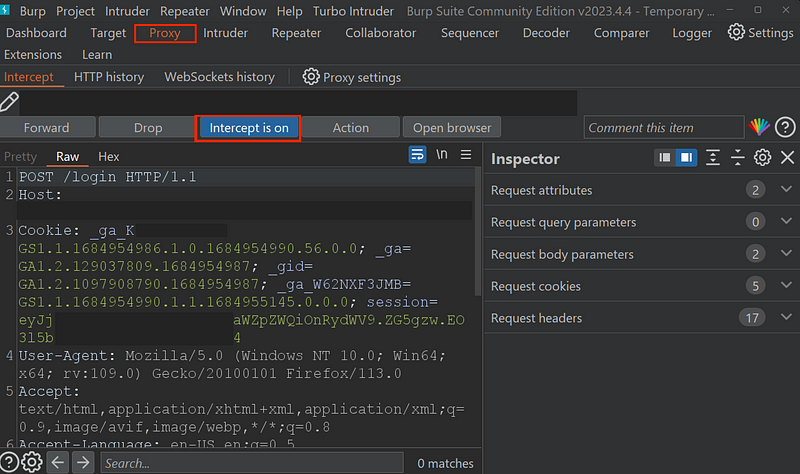
You can turn off the proxy.
Right-click on the Raw capture > Extensions > Turbo Intruder > send to Turbo Intruder
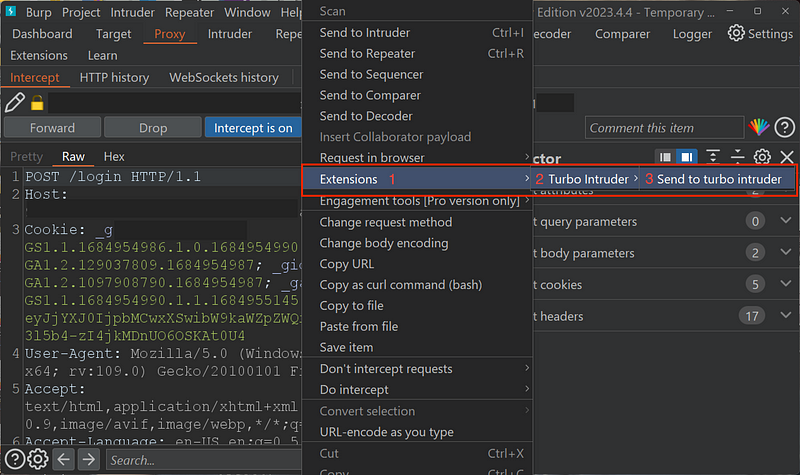
Step Three:
Turbo Intruder pops up and the capture will be on top and the coding section on the bottom.
Click on Last code used drop-down menu > examples/basic.py
Tip: Before we edit the code, first we need to download or create a list of usernames and passwords. I used the rockyou.txt and this can be downloaded here. Note the path you save your file to.
On the code section we will make the following adjustments:
Line 3 & 4
CurrentConnections=200
requestPerConnection=150
Line 8
for word in open('<Your file path goes here>'):
Line 14 & 15
if ('Invalid username' not in req.response):
table.add(req)
Head over to the Raw capture section on top and make the following adjustments:
Line 20
username=%s&password=test
* This tells the code we are only looking for the username.
Click on Attack.
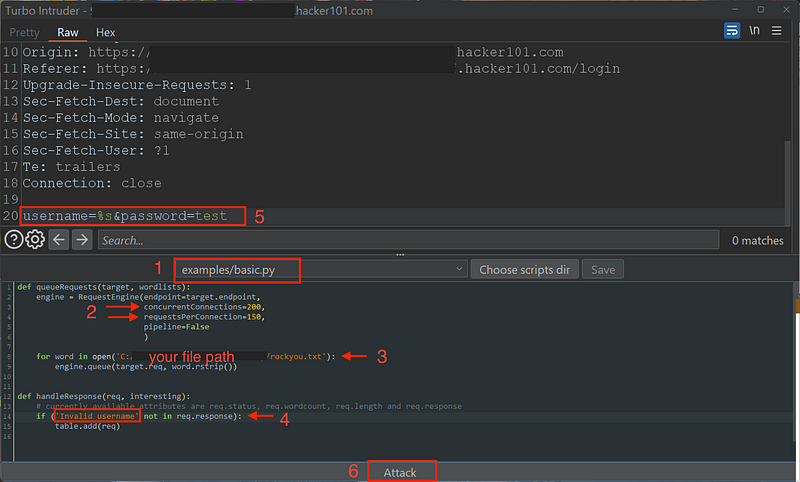
You should see it running. Give it about a minute and then the table above should load up with results.
On the table we are looking at the Status column and looking for code 200. Under the Payload column you’ll find the username.
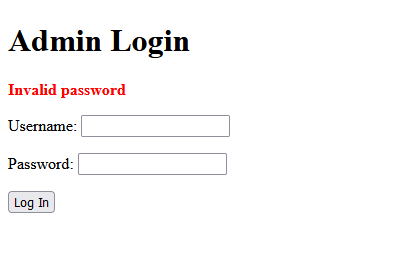
Head over to the webpage and input that username and pair it with a random password.
Click Log In.
The message that should appear is Invalid password.
Congrats you now have a valid username!
Step Four:
Go back to the Turbo Intruder window and click on Configure located at the bottom. It will take you back to the Raw capture and coding window.
Make the following adjustments to the code:
Line 14
if ('Invalid password' not in req.response):
Make the following adjustments to the Raw capture:
Line 20
username=<input valid username here>&password=%s
*Make sure you type the valid username next to username=
Click on Attack.
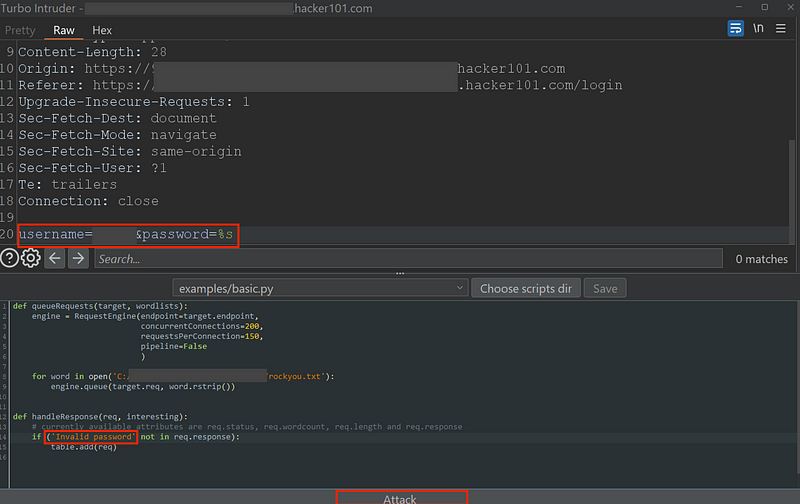
Give it a few minutes and once the table loads up look for Status code 302 and the Payload value is your password.
Go back to the webpage and input the valid username and found password.
Click Log In.
Congrats you have found your FLAG!

Flag 2 …
Hints:
Always test every input.
Bugs don’t always appear in a place where data is entered.
Now that we have admin access we can edit and this flag is pointing us in that direction!
Click on one of the edit buttons. Here we can edit Name, Description, and Price.
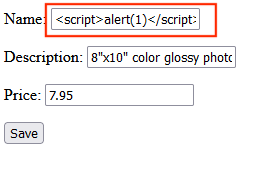
Let’s attempt an XSS payload on the Name field.
Insert the following:
<script>alert(1)</script>
Then click on Save.
Note: I attempted the XSS payload in the two other fields and got an error with one and got no flag with the other. I advise you try it so you can see the outcome for yourself.
Head back to the Home page.
TIP: use the URL path
Click on the link that takes you to the cart.
You should see your FLAG!

Give yourself a hug! You’ve made it to the end and captured all three flags!
Time for a water break …
If you want to learn more about Turbo Intruder and all its uses, check out James Kettle article and video here.
Subscribe to my newsletter
Read articles from WalkingEclipse directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

WalkingEclipse
WalkingEclipse
I’m Mercedez aka WalkingEclipse, a cybersecurity graduate with a B.S. in Cybersecurity and a minor in Penetration Testing. I just earned my Security+ certification and am paving my way into the field by further expanding my knowledge and technical skills. Follow my journey as I share what I’m learning, the projects I tackle, and the cybersecurity challenges I conquer along the way!